
9 Ways Whois Lookups Can Boost Data Privacy and Security
Few would argue that data privacy and data security are becoming ever-more complex, concerning, and [time-]consuming. The risk of data breaches is as high as it’s ever been, and the impact data privacy regulations have on your organization and industry are becoming ever-more stringent. As a security product leader caught between a rock and a hard place, data collection, secure storage, effective access control, and much more are important in navigating and maintaining the delicate balance between the two. All the while, of course, being subject to scrutiny and challenge from the relevant governing bodies at any time.
However, in what is clearly an unenviable situation, by looking at 9 ways Whois Lookups can boost data privacy and security in your organization, this blog post may help you uncover additional methods to help protect data privacy and maintain regulatory compliance. (Methods outside of what is termed ‘traditional data protection’ and regardless of your particular industry.)
Information privacy and proper handling of data is critical
And many companies are struggling. The speed of technical advancement hasn’t helped. Neither has the continual expansion of the threat landscape (and the number of hackers sensing easy picking). And nor have the changes in regulatory requirements (we’ll touch on this below).
Not quite a Perfect Storm, but all contribute towards what is becoming a severe threat for many organizations: the need to secure and protect sensitive data, including personally identifiable information (PII), to maintain data privacy, and to comply with regulations that govern data privacy and security. It’s hardly a wonder that many security professionals feel they’re losing control.
Whois Lookup can help.
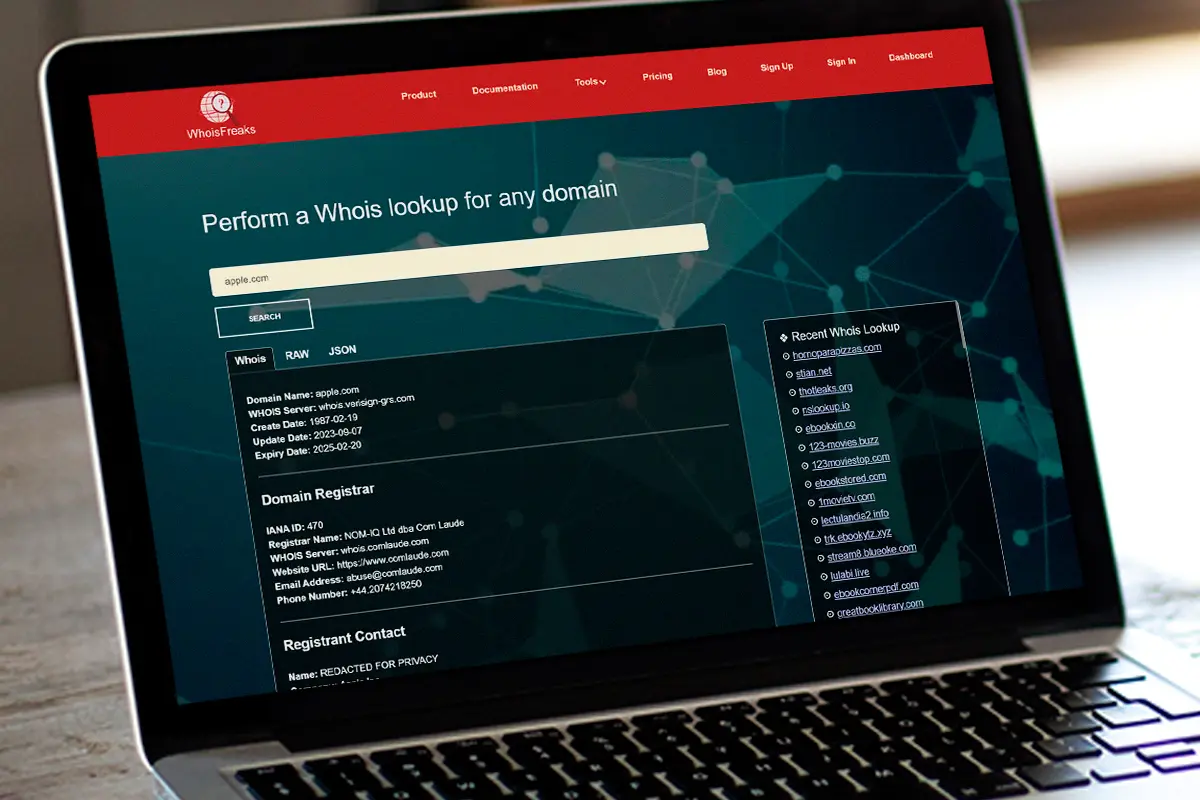
Though an unassumingly simple and easy to use tool, Whois lookups can provide a wealth of insights into who owns what domain, as well as what they’ve been doing with it. And in the same way as negotiating your way through a maze or solving that puzzle can reveal an unexpected treasure or reward at the end, so can Whois Lookups.
Understanding Whois Lookups
Whois Lookup is a tool that provides detailed information about domain registrations.
In effect, a Whois Lookup involves querying the Whois database–a repository containing the registration details of internet domain names—and the query results lay out a website’s identity. Information can include who created it, when it was first created, where it’s hosted, the expiration date, and so forth…
And therein lies the problem!
Though the “If you’ve got nothing to hide”-brigade might advocate such transparency as being commendable, from a data guardian and security perspective, managing confidential data of this nature can be a nightmare.
A nightmare that serves to not only reiterate and reinforce why maintaining a delicate balance between the two is so important—especially when major fines and other non-compliance penalties are in play—but also how you need to use every available and useful tool at your disposal to the best of its ability.
Here are 9 ways in Whois Lookups can help you do just that…
Domain Ownership Verification
“Excuse me, sir, does your dog bite?”
“No.”
Man goes to stroke the dog and gets bitten… “I thought you said your dog doesn’t bite?”
“That’s not my dog!”
Ownership, and understanding who owns what, is critical. Especially with domain names and from a data and a security standpoint.
You know full well that effective cyber-security today requires both a proactive approach and stance: the days of sitting back and waiting for the attacker to strike are long gone. Where possible, the savvy security-oriented organizations are taking the fight to the enemy.

In this regard, Whois Lookups allow you to step quickly, quietly, and confidently onto the front foot and quickly discover information about the domain without getting bitten. This information includes the registrant's name, email address, physical address, and contact numbers.
For data integrity purposes, this information must be up-to-date and accurate. For security purposes, you should only be permitted to access and collect information that’s permitted in the public domain. When either are compromised, then it raises questions about legitimacy, lowers trust, and is ultimately unfit for purpose.
From your security perspective, if the information is flawed, then domain ownership clearly cannot be established. In such cases, it would be foolhardy to consider the domain as anything other than a threat.
API vs Manual Lookups
Note: To be truly proactive, your organization must use automated/API lookups. You’ll get no arguments from us that manual searches are also proactive, it’s just our experience shows they’re too slow to be of anything but limited use or value for today’s organizational cyber-security.)
Identifying Malicious Actors
Have you heard of Guy Goma?
In 2006, Mr. Goma went to the UK’s BBC for a job interview for an IT position but somehow ended up being interviewed live on air as an IT expert.
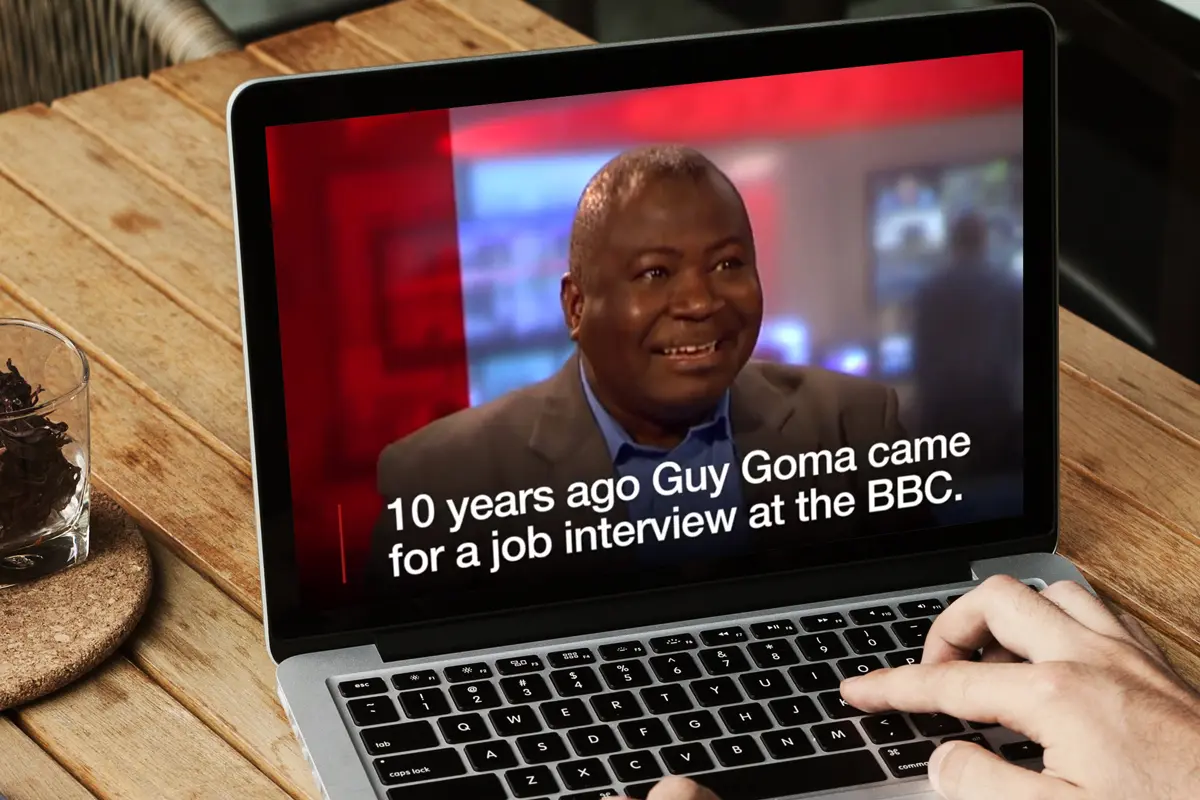
It just goes to show that mistakes do happen, but it also emphasizes the importance of understanding who is genuine and who is not. From a security point of view, knowing who you’re dealing with is vital, and being able to filter out real from malicious actors is vital to minimizing risk, maximizing security, and thwarting potential threats.
Red flags for malicious actors include fake addresses, frequent changes of ownership, generic email use, etc. Identifying such patterns and anomalies are part-and-parcel for your security team, and Whois Lookups make this task much easier.
Forearmed, you can then take the necessary steps to implement security measures, fortify your defenses, and defuse any cyber threats. Moreover, Whois Lookups can also be used to investigate and learn from cybersecurity incidents.
Investigating Cyber-security Incidents
Anyone involved in a cyber-security incident knows firsthand how time is of the essence in mitigating damage. Whois Lookups play an essential role in investigating such incidents by providing your investigators with information that can be used to trace the attack source.
For example, in scenarios where a compromised network led to a data breach, or in a ransomware or distributed denial-of-service (DDoS) attack, Whois Lookups are one of the first tools of choice by investigators. In such cases, these lookups can identify both the origins of the malicious activity and who the orchestrators are.
Naturally, when you have solid information that can be attributed to a specific entity, it enables your organization to take legal action, collaborate with law enforcement, and to improve defenses.
Enhancing Incident Response
Again, the faster your organization can understand and contain a threat, the lower the potential impact.
Imagine your organization is bearing the brunt of an active phishing campaign targeting your employees and contractors. Using a Whois Lookup, your security team swiftly identifies the domains associated with the malicious emails as well as the registrant details and registration history. Now you understand the scope of the attack, you can make better decisions faster, and can formulate both an effective response strategy and minimize damage.
Detecting Phishing Attempts
“Phishing attacks are still the biggest threat to internet users.”
Because they often rely on deceptive domains that mimic legitimate websites, detecting phishing attacks early is crucial. Warning signs of potential phishing domains include irregularities in registration information such as misspelled names, fake addresses, or suspicious email contacts. If your security teams identify these in advance, you’re better equipped to take preemptive action and respond at the earliest opportunity.
Monitoring Domain Expirations
Expired domains are already established online identities and are often a very attractive target. Not every organization has the right processes in place and is as proactive in monitoring as they should be, and if a cybercriminal can obtain an expired domain and act quickly, the potential for damage before the victim knows what’s hit them is exponential.
Don’t think it’ll ever happen to you?
“The guy who bought Google.com from under Google's nose.”
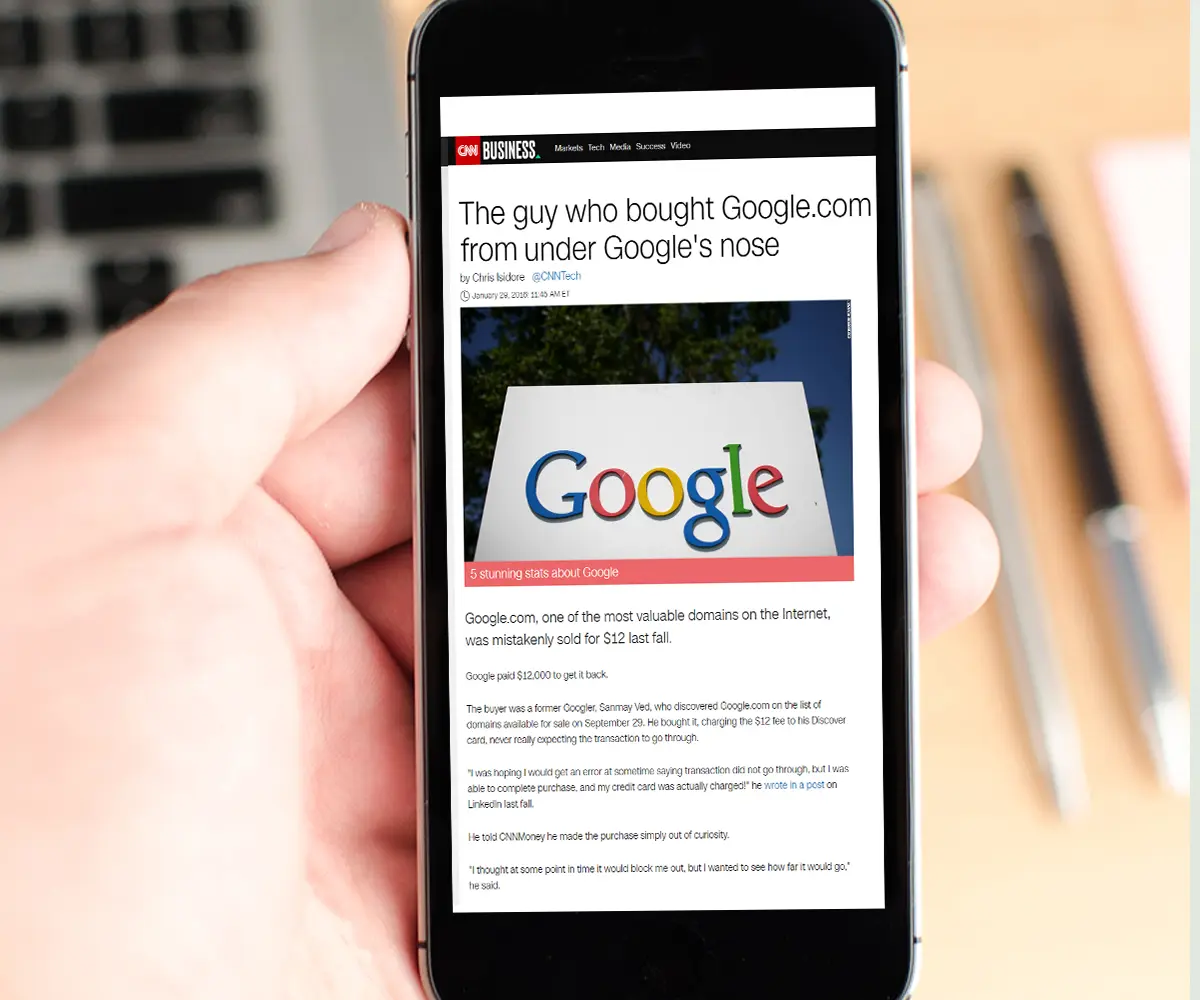
Regularly querying Whois databases allows you to track the status of expired domains as well as those connected to, or associated with, their digital footprint.
Regardless, adopting a proactive approach towards expired domains allows for the timely renewal of your own domains and 1) mitigates the risk of security vulnerabilities from lapses in ownership, 2) avoids the embarrassment that Google were subjected to, and 3) helps retain trust (from both customers and other interested parties).
Privacy Concerns and GDPR Compliance
As stated earlier, to strike a balance between data privacy and data security means being mindful of compliance and other legal implications, whether geographical, jurisdictional, industry-specific, etc. Such data protection laws can extend anywhere from corporate security to national security to even multinational security/regulations, such as the General Data Protection Regulation (GDPR) within the European Union.

These legal requirements often mean that information through Whois Lookups is redacted or restricted and, to remain in compliance, your organization must adapt its cyber-security strategies to align with these privacy measures while still extracting as many valuable insights as available.
Integrating Whois Lookups into security protocols
Automating Whois Lookups via API offers several benefits for your organization:
- Proactive Threat Detection: Automation in monitoring domain registration changes enables swift identification of potential risks.
- Enriched Threat Intelligence: Incorporating Whois data helps you make better and more informed decisions around cyber-security threats.
- Consistent Practices: Establishment of standard operating procedures (SOPs) ensures consistent, clearer, and more efficient practices across your security teams.
- Enhanced Collaboration: Access to Whois data fosters collaboration between different teams, helps break down barriers, and promotes a more unified and organized cyber-security strategy.
- Fortified Defenses: Obtaining better and more accurate data faster empowers you to fortify defenses, respond rapidly to incidents, and maintain a proactive stance against emerging threats.
Conclusion
Toeing the line between data privacy and security is an ongoing battle, and appreciating and understanding how Whois Lookups can help is extremely useful. More-so when you consider how beneficial automating lookups via API can be.
In this post, we looked briefly at nine impactful ways that these can help you navigate your daily challenges, proactively enhance your cyber-security measures, and effectively mitigate any associated risks. For most organizations, the need to be proactive in security means monitoring multiple areas including monitoring domain ownership, identifying malicious actors, and investigating cyber-security incidents.
Integrating Whois Lookups into security protocols, promotes such an approach and affords many benefits such as swiftly detecting threats, enriching threat intelligence, ensuring consistent practices, fostering collaboration, and fortifying defenses against emerging threats.
One thing’s definite, if you aren’t using Whois Lookups, or using them to their full effect, we’d recommend you take a look now.

Software Engineer
A software engineer focused on developing scalable, efficient solutions. Expertise in coding, system optimization, and utilizing advanced technologies for high-performance apps.
Related Posts

WHOIS History as Evidence: Incident Response Use C...
Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, ...
Published at: Jan 12, 2026

Forensic Analysis Uncovering Cybercrime with WHOIS...
Explore how WHOIS history aids forensic analysis in cybercrime investigations. Learn effective strategies to enhance your cyber defense. Read more now...
Published at: Jul 25, 2025

Phishing Prevention Using Subdomain Discovery to T...
Learn how subdomain discovery can enhance phishing prevention and protect against spoofing campaigns. Read the article for practical strategies.
Published at: Jul 22, 2025

Unmasking Hidden Threats: The Role of Subdomain En...
Discover how subdomain enumeration enhances attack surface management and helps identify hidden vulnerabilities. Read the article to safeguard your as...
Published at: Jul 10, 2025