
7 Ways Historical Whois Lookups Can Help Your Organization with Cyber-security, Threat Response, and Continuous Improvement
Together with Whois Lookups and Reverse Whois Lookups tool-trilogy, Historical Whois Lookups make up the 3 key components of the WhoIsFreaks Whois Lookups Tool Trilogy (WWLTT). Together, the WWLTT will provide you with an extremely powerful, useful, and versatile toolkit to manage your organization’s online presence, improve its cyber-security, and remediate threats.
However, because this is a vast topic, this post will focus on the benefits of Historical Whois Lookups (covering Whois Lookup and Reverse Whois Lookups in their own posts). Though there are many more ways this lookup can help, we’ll take a quick look at 7 ways Historical Whois Lookup data can help your organization with cyber-security, threat response, and continuous improvement (and others).
First, a quick reminder of Historical Whois Lookups, what they are, why we use them, etc.
What are Historical Whois Lookups and why do we use them?
Historical Whois Lookups are used to query the Whois database for your search term and to retrieve the relevant Historical Whois records, assigned names, and other information related to the domains entered.
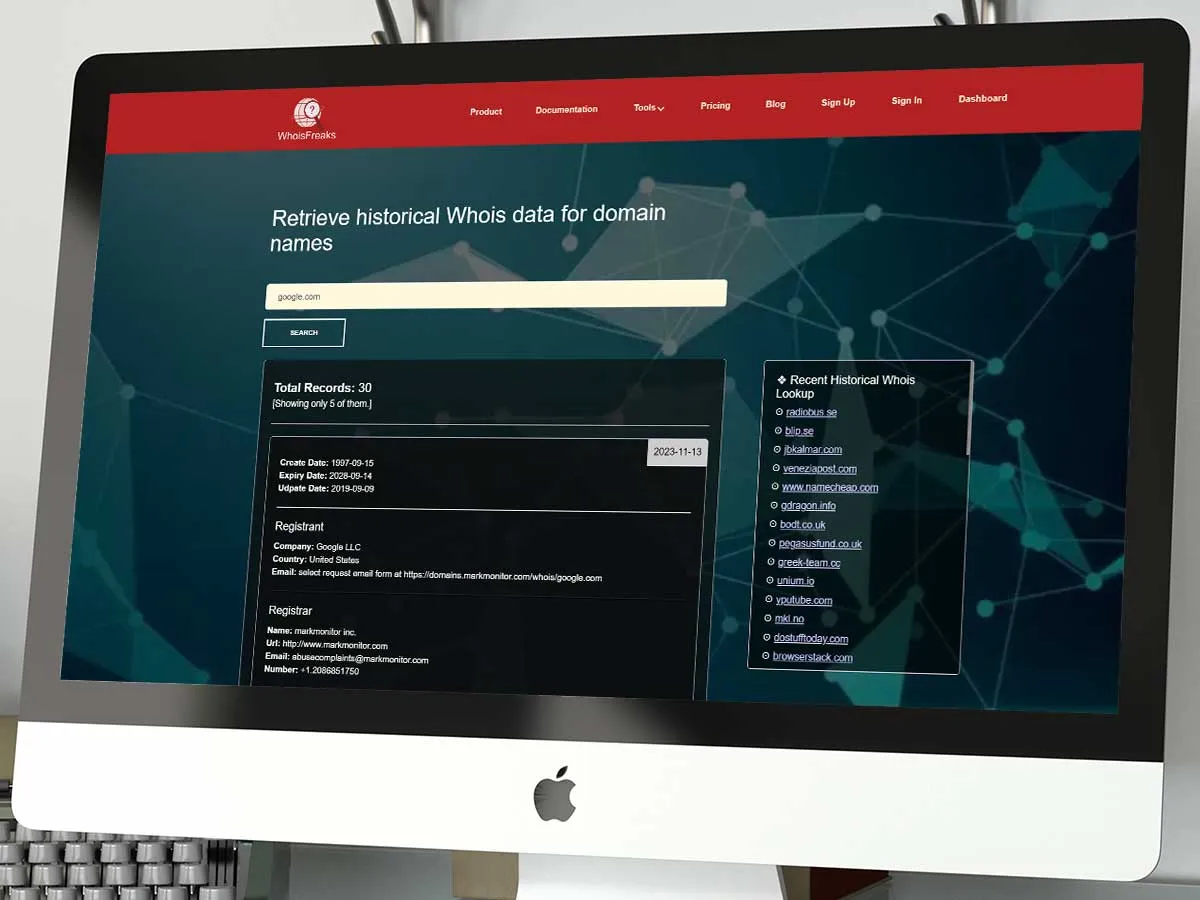
The results display the Whois history, including a high-level overview of the domain name's journey to date, including the domain's owners, registrant name(s), and other relevant results. For example, as shown in above figure, we can see the create date, expiry date, update date, who the registrant is, their country, what their nameservers are, etc.
A Historical Whois Lookup provides a wealth of information that can help you in multiple areas of your business, including threat intelligence and attribution.
Threat intelligence and attribution
As shown in the above figure, a quick domain name search will reveal information related to that domain. Armed with this paper trail, your security team can carry out their investigation and identify and attribute malicious activities such as malicious emails or malware to specific entities or threat actors.

Such investigations can help with:
- Pinpointing the source of attacks allows you to both mount a more effective and targeted response and helps you to minimize any impact on your system(s) or service(s).
- Enhancing threat intelligence by understanding the historical context of cyber incidents provides you with a deeper understanding and allows you to develop your policies and continuous improvement methods based on practical experiences and real-world challenges.
- Strengthening incident attribution for legal and enforcement purposes provides you with solid evidence and a clear understanding of the historical context to support any legal actions/enforcement efforts against threat actors.
Incident Response Planning
- Learning from past incidents to enhance response strategies allows you to adapt and improve your incident response plans/processes to be more effective, agile and capable in responding to any future incidents.
- Identifying weaknesses in previous responses enables you to address vulnerabilities and improve your overall incident response capabilities as part of continual improvement/your continuous improvement model.
- Streamlining incident recovery processes based on historical insights equips you to optimize your incident recovery procedures, reduce downtime, and improve recovery efforts.

Risk Assessment
Assessing risk is a vital element in prioritizing security measures and allocating requisite resources. To do this effectively requires access to accurate and up-to-date historical lookup information that equips your team to analyze and assess past data breaches, vulnerabilities and threats, and to then apply findings to your current situation.
Historical lookups can help with:
- Identifying recurring risks and vulnerabilities enables a better, faster, and more efficient ‘risk-aware’ approach across the organization.
- Prioritizing security measures based on historical threat landscapes helps ensure a focused and effective approach to security implementation across all systems.
- Strengthening risk management strategies and solutions through data-informed decisions fosters a more resilient and adaptive risk management framework throughout your organization
Policy Development
With the threat landscape and legislation and regulation changes in a constant state of flux, your business must adapt accordingly. In such cases, accessing historical data can provide valuable insights and assist with policy decisions, alignment with industry best practices, improving effectiveness, etc. Other benefits include:
- Adapting to evolving threats for proactive defense ensures your policies are dynamic, your overall cyber-security posture is resilient, and you’re effective in responding to emerging threats.
- Incorporating lessons from historical incidents for understanding standards provides you with a deeper understanding of evolving standards and benchmarks and allows you to refine policies based on actual practical experiences and real-world challenges.
- Staying current and competitive through industry best practices helps maintain a robust cyber-security posture, protect your organization, while remaining competitive.
Vendor Risk Management
Having accurate data about your third-party vendors and partners assists in evaluating any risks or baggage they may carry. (Let’s face it, you know they would be evaluating you in the same manner). Historical Whois data can help with your due diligence in creating and maintaining a more robust vendor risk management program and can directly help with the following:
- Evaluating the historical cyber-security performance of vendors makes for better and more informed choices when selecting and managing third-parties.
- Enhancing due diligence in vendor selection and monitoring helps you achieve a comprehensive understanding of the vendor’s cyber-security practices and any associated risks.
- Strengthening overall supply chain security enables you to both identify and address vulnerabilities far faster and create, implement, or foster a more resilient and secure supply chain.
Continuous Improvement
Historical data as a feedback mechanism is an extremely useful component for continuous improvement. We all make mistakes and analyzing and learning from past incidents helps you best refine and improve cyber-security throughout your organization.

For example:
- Improving incident response iteratively based on historical data lets you refine and enhance your incident response strategies and advance towards a more effective and adaptive approach.
- Enhancing cyber-security policies through continuous feedback helps align and address evolving threats, and with employee involvement, not only keeps everyone in the loop but also helps break down barriers, improve communication and relationships across the board.
- Adopting an adaptive security posture based on lessons learned empowers your organization to proactively adjust its security posture, increase agility, and become more resilient against any emerging threats.
Note: we always advocate implementing a continuous improvement process within your organization. Small improvements are a proven way forward.
Forensic Analysis
Reconstructing events, understanding attack vectors, and conducting post-incident investigations are critical in understanding events around any cyber incidents. Historical Whois data is particularly suited for analysis and can help your investigators in several ways including
- Supporting detailed post-incident investigations via thorough and comprehensive examinations. These examinations can help uncover the root cause of any cyber-security incidents, help with any post-incident response, and also help prevent reoccurrence.
- Reconstructing cyber events for legal and compliance purposes ensures your organization has the necessary information to meet legal and compliance requirements, as well as being able to aid in investigations (where necessary), and maintain regulatory adherence.
- Enhancing incident response by incorporating lessons-learned into your incident response strategies, Organizations that implement this effectively have seen vast improvements in their overall incident handling and mitigation efforts.
In conclusion, accurate historical data can play a pivotal role in improving and fortifying your organization’s cyber-security. From threat intelligence and attribution to incident response planning, risk assessments, continuous improvement, and more.
However, as we’ve touched on here, when applied correctly, this is just a fraction of what Historical Whois Lookups can do. Not only can they provide a wealth of insights and information to help you stay abreast of today’s changes and challenges, but with ongoing effort and incremental improvements, they’re also capable of improving your threat hunting capability, boosting your overall security posture, and helping you to proactively manage and meet any emerging threats. What’s not to like?
Next Steps
As mentioned, WhoIsFreaks’ Historical Whois Lookup tool is but one arm of the WhoIsFreaks’ Whois Lookups Tools Trilogy (WWLTT) . Though fully capable as a stand-alone tool, when it’s combined with Whois Lookups and Reverse Whois Lookups your security teams get full capability to enhance your online presence.

We know we’re biased towards our tools, but if you’re either not using these lookups or aren’t using them to their full capability, we’d thoroughly recommend you checking them out. It only takes a few minutes and when you see what a difference they will make to you and your organization, you’ll be glad to did.
Get started by clicking on the button below:

Software Engineer
A software engineer focused on developing scalable, efficient solutions. Expertise in coding, system optimization, and utilizing advanced technologies for high-performance apps.
Related Posts

Reverse WHOIS by Email: Find All Domains Linked to...
Discover how to use reverse Whois by email to find all domains linked to an email address. Read the article to learn effective techniques today.
Published at: Mar 13, 2025

How to Uncover the Owner of a Privately Registered...
Discover how to find the owner of a privately registered domain using Whois history lookup. Read the article for practical steps and insights.
Published at: Mar 12, 2025

Essential Guide to Domains Lookup: Find Your Domai...
Quickly access and understand domain information with our essential guide. Get the insights you need to manage your online presence effectively. Read ...
Published at: Mar 11, 2025