

Posted on August 07, 2025 | 11 min read
In today’s interconnected world, understanding how data travels across the internet is key to both performance and security. One of the building blocks that make this possible is the Autonomous System Number (ASN). In this guide, you’ll learn about the role of the internet assigned numbers authority :
Whether you’re a network operator, IT professional, or simply curious about how the internet works, this article will give you clear, easy‑to‑follow information about understanding ASNs. Let’s get started!
ASN stands for an Autonomous System Number. It is a special number, a special number assigned to large networks that are connected to the internet such as internet providers, big companies or cloud services.
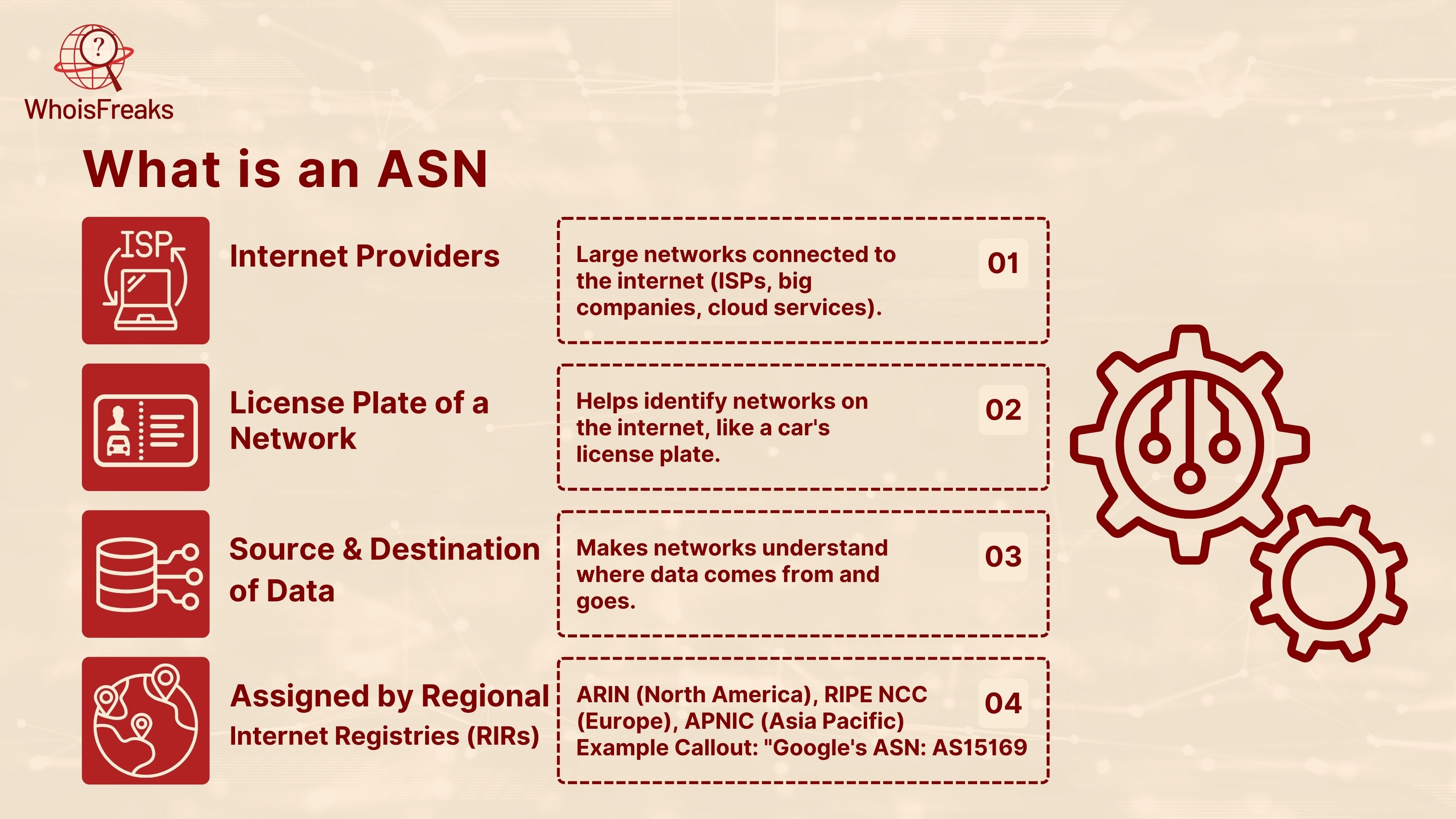
An autonomous system ASN is a bit like a license plate of a network. In the same trend, cars have license plates that help to identify vehicles on the road, networks have ASNs to lead to the identification of networks on the internet.
An ASN makes such networks understand the source and destination of data. It is particularly efficient in routing on the internet such as identifying the destination ip address, that is how internet traffic is carried across various locations. This network is coordinated by an entity known as BGP, which is simply abbreviated to Border Gateway Protocol and which is a sort of map of internet traffic.
ASNs are assigned by official groups known as Regional Internet Registries (RIRs), such as:
Google has its own ASN -> ASN 15169, which helps manage its massive network traffic around the world.
The internet is made up of thousands of different networks. These networks need a way to talk to each other safely and correctly. That’s exactly what ASNs help with.
Here’s why we need ASNs:
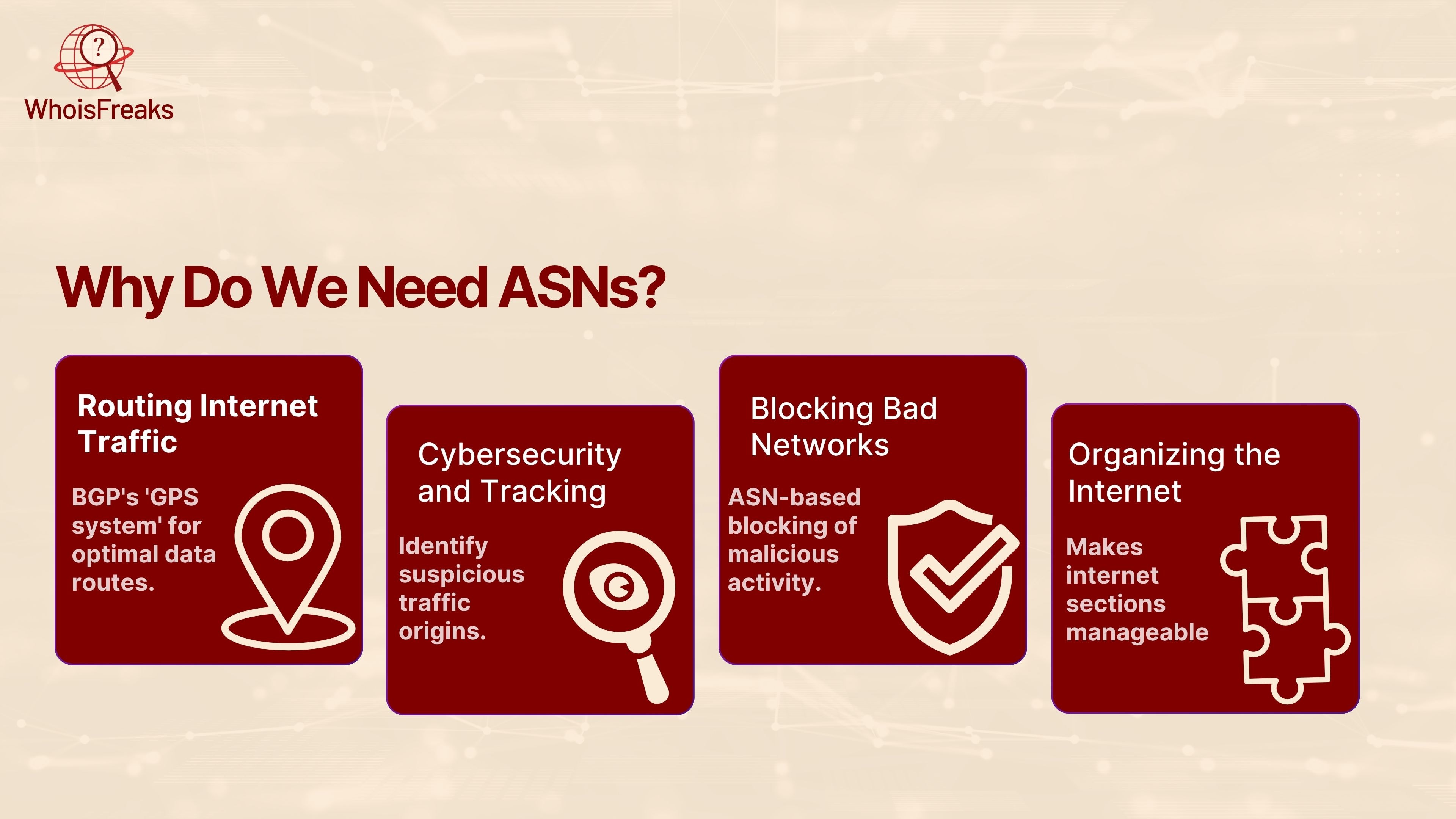
BGP (Border Gateway Protocol) involves the use of ASNs, which is a form of the GPS system of the internet. It aids in providing data through the optimal route amid networks.
Using ASNs, one can understand where network traffic was launched. It can be of great help in cybersecurity. Having suspicious traffic or dangerous traffic, with the knowledge of the ASN number, we can establish the source of traffic.
If a certain ASN is known for hosting malicious activity (like phishing domains or attacks) security teams can block it. This is called ASN based blocking.
In absence of the ASNs, various kinds of networks within internet would be chaotic and difficult to control. Every ASN creates a section of the internet manageable and simple to administer.
In short, ASN security is about using these unique numbers to keep the internet running smoothly — and more importantly safely.
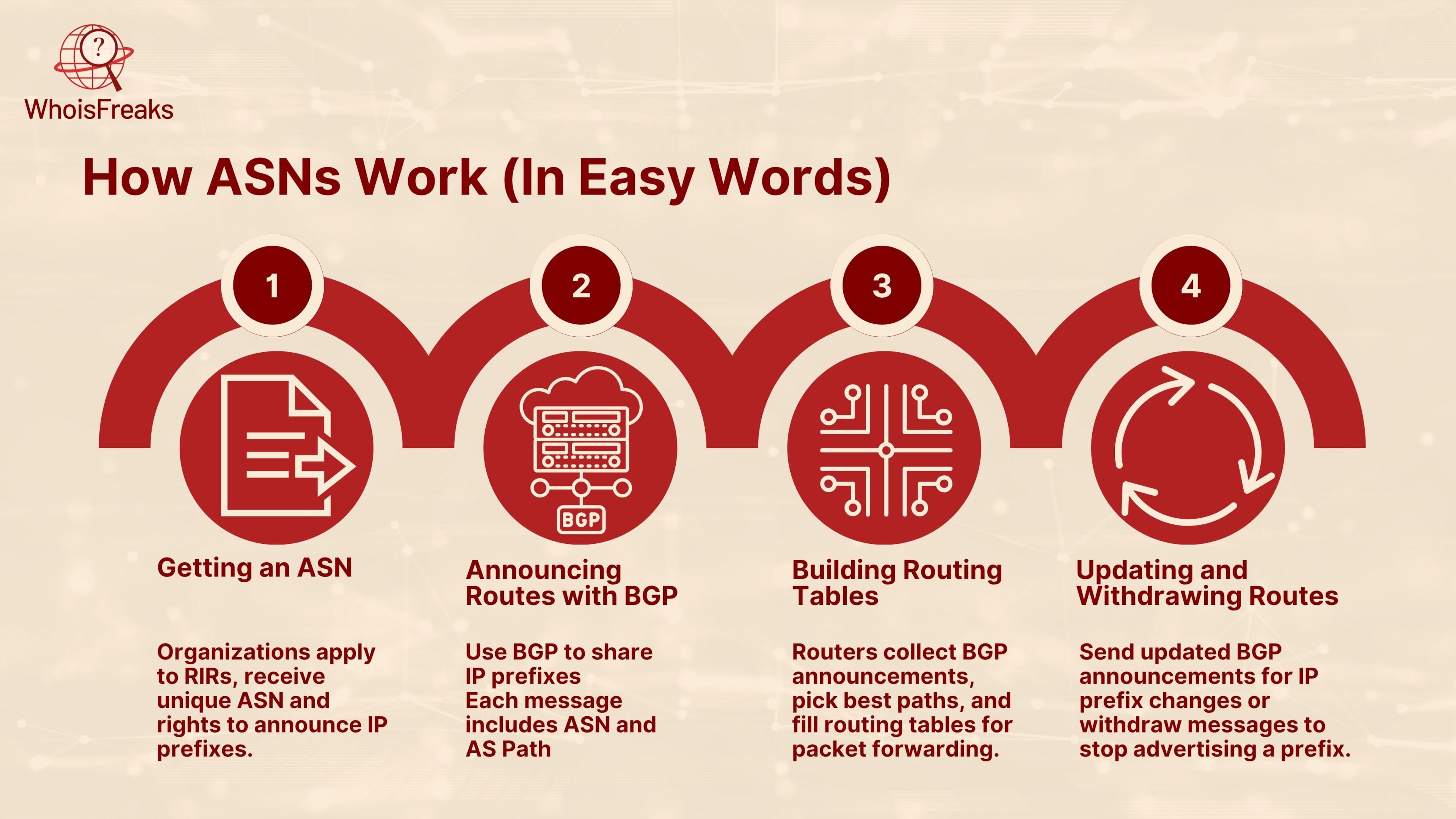
Each BGP message includes your ASN and the path it will take (the AS path). For example:
Prefix: 203.0.113.0/24AS Path: 64500 → 64510 → 12345
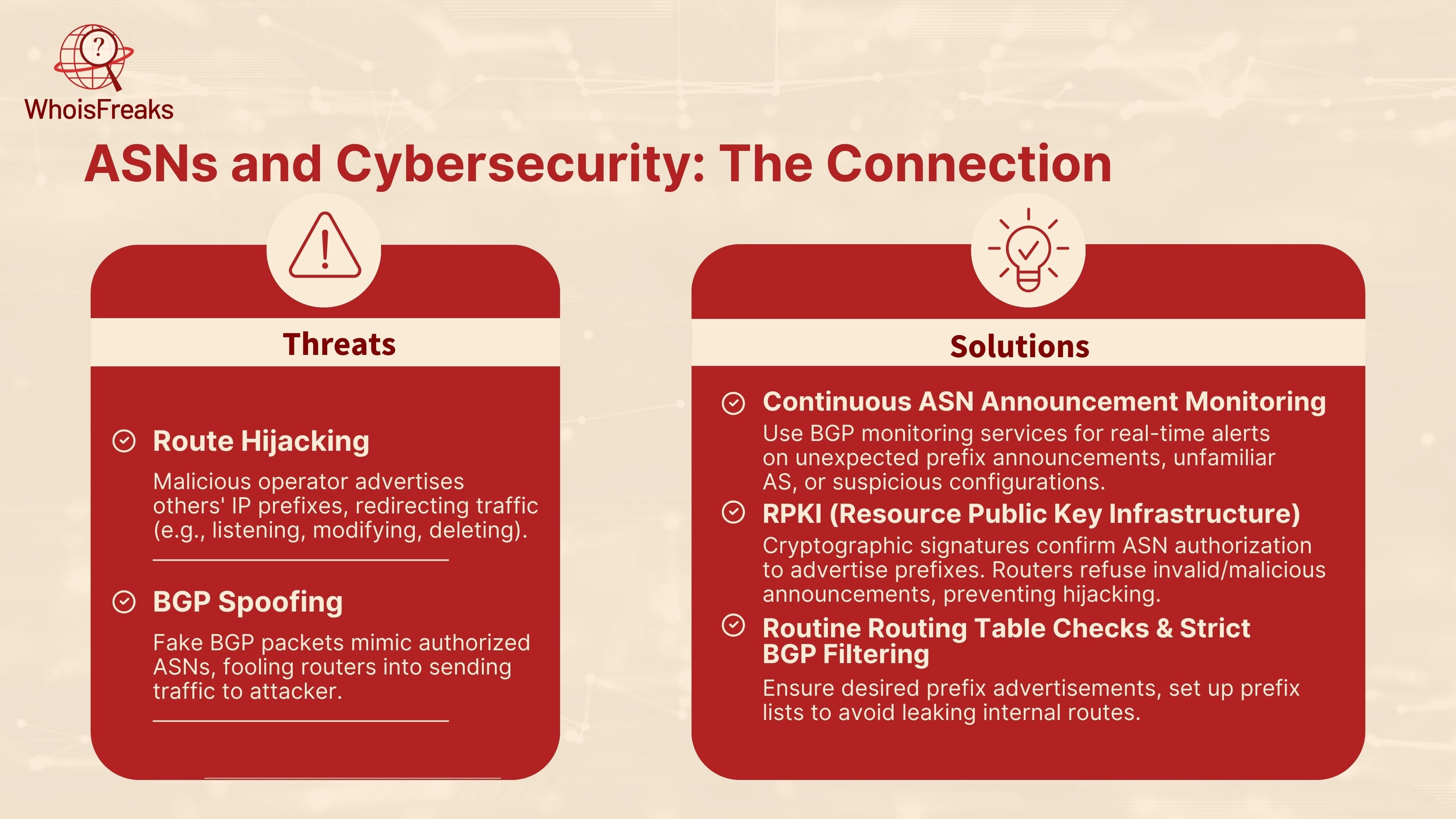
Autonomous System Numbers (ASNs) play a vital role in directing the traffic on the internet, yet they serve the potential of being exploited by hackers, which institute high cyber threats. One of the most severe threats is a route hijacking when an evil network operator advertises the IP prefixes belonging to other people using his own ASN and enjoying malicious behavior . Consequently, the encrypted information that was intended for the legitimate network ends up being redirected to the attacker who then has the opportunity of listening, modifying, or even deleting the traffic. BGP spoofing, where fake Border Gateway Protocol packets are created to mimic an authorized ASN, and by doing so fool routers into sending traffic of interest across the attacker network, is closely related
In order to protect yourself against these threats, your ASNs announcements must be monitored continuously. The use of BGP monitoring services is a common activity by network operators and they notify on real time whenever there is an unexpected prefix announcement or when there is an unfamiliar AS or a suspicious AS configuration on the AS path. Early detection enables you to collaborate with the upstream providers in withdrawing the unauthorized routes before serious damages occur.
One of the strongest methods to fortify the confidence in your routing info is the use of RPKI (Resource Public Key Infrastructure) and the publication of ROAs (Route Origin Authorization). RPKI uses cryptographic key signatures to confirm that ASN is indeed authorized to advertise a given IP prefix. And in case the routers apply RPKI checks, they can automatically refuse to accept invalid or malicious announcements and prevent a large number of hijacking attempts at the network edge.
Lastly, you should have routine checks on your routing tables and ensure that there are harsh BGP filtering policies. Ensure that the prefix advertisements are those desired, and ensure that prefix lists are set up to avoid leaking internal routes. Coupling the diligent observation, cryptography-based authorization, and ultra-code, you can diminish considerably the threat of ASN-based attacks and ensure that the traffic in the network under your control remains safe.
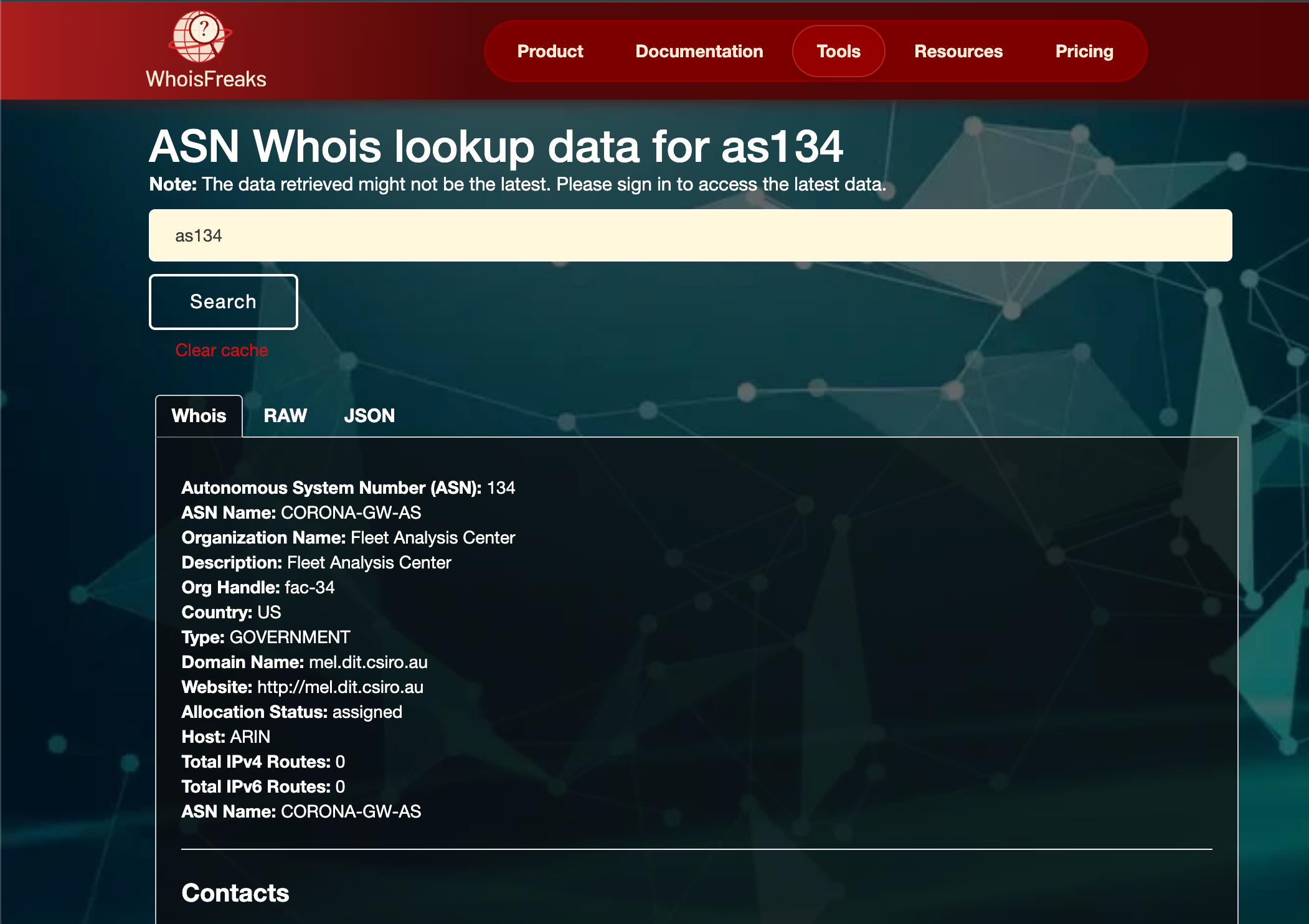
If you need a quick, web‑based ASN lookup no setup required check out the ASN Whois Lookup Tool from WhoisFreaks. Here’s what you get and how to use it for retrieving ASN information:
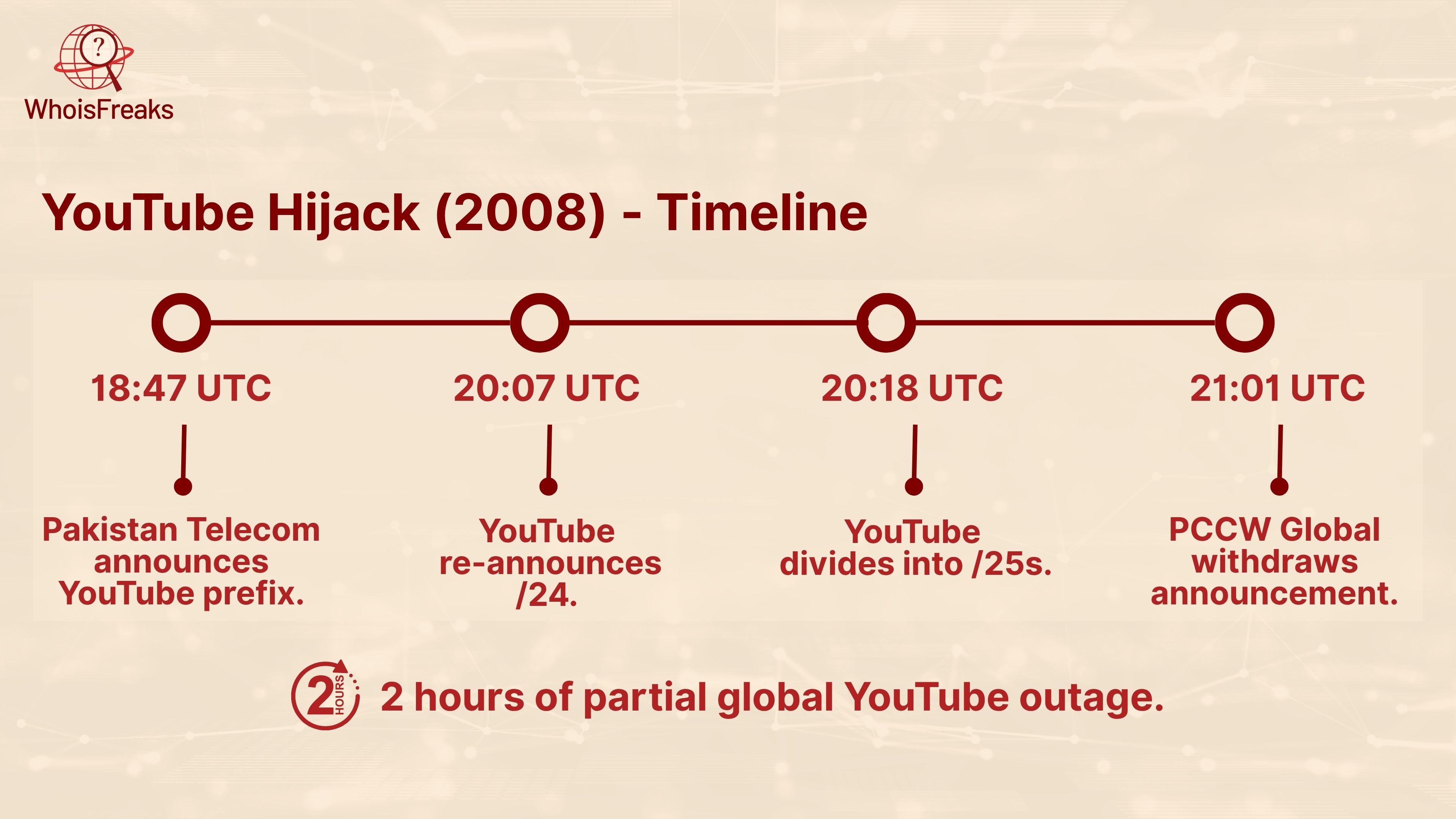
Pakistan Telecom (ASN 17557) unintentionally assigned the IP prefix of YouTube (208.65.153.0/24) as their own and all YouTube access throughout the world was then routed through Pakistan Telecom rather than Google network.
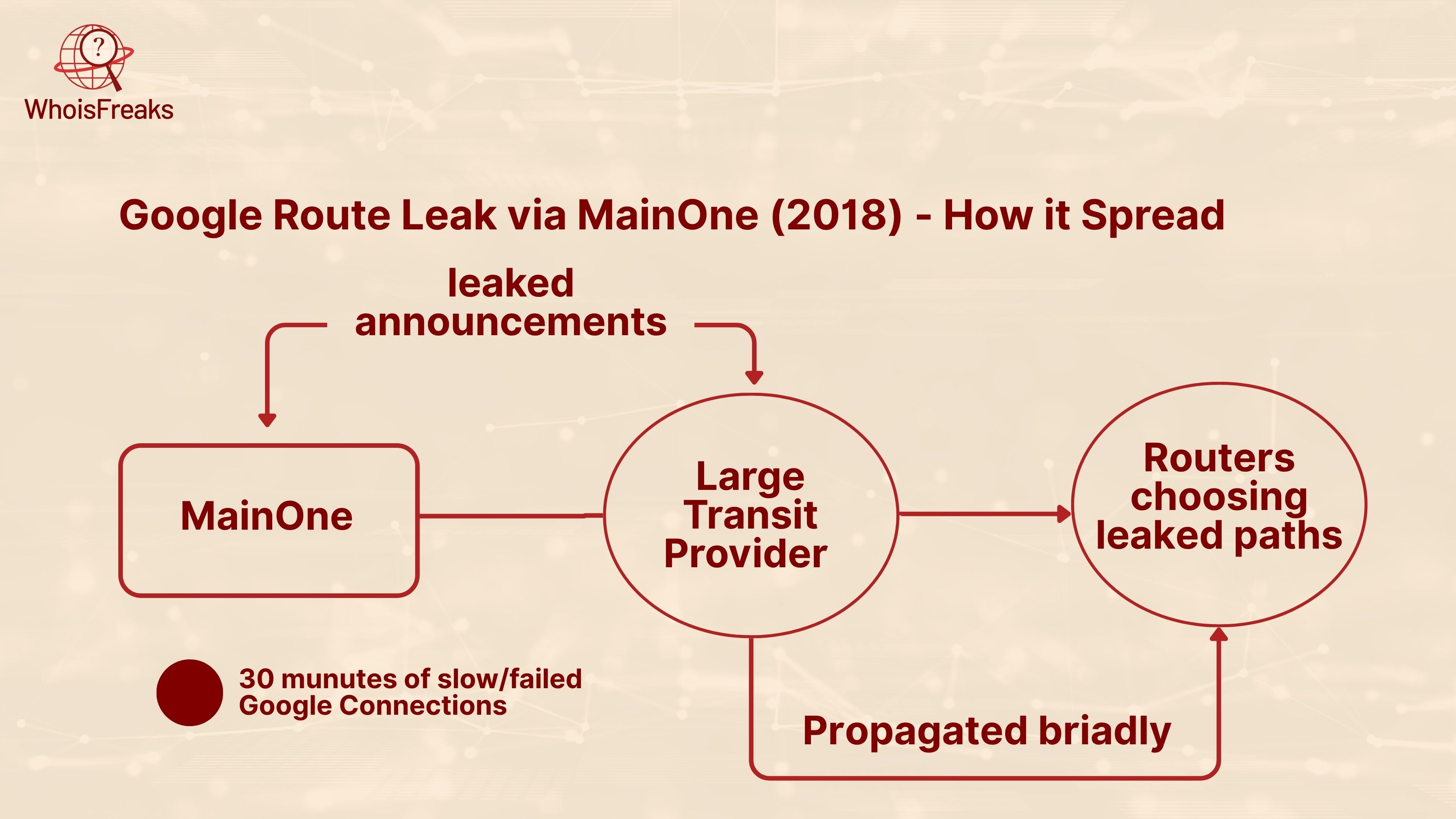
The Nigerian ISP MainOne misconfigured its BGP filters, exposing hundreds of prefixes owned by Google to its upstream providers including China Telecom. The traffic to Google services (Search, G Suite, YouTube) was redirected to the unexpected networks in China and Russia.
WhoisFreaks also provides multiple free, web based searches to verify ASN(s) and IP ownership information without registering and creating user accounts. The most pertinent to ASN-level investigations are the following ones:

Retrieves instant advanced ASN information: the registry, the date of allocation, the name of the organization that received it, the emails of contacts, and all announced address blocks. Ideal in determining river owners of an ASN.
Enter any IP address, to see its ASN, IP block (CIDR), information in registry and technical/admin contacts. You use this when you observe an unusual IP in your AS path and you desire to back track it..
Find out registration information of a domain registrar, creation/expiry dates, name servers, and contact of the registrant. Useful when you have to confirm infrastructure areas connected with an ASN.
Search all the domains registered with a name of email or the name of organization. In case of a certain email being used by an abuse contact of an ASN, other domains that the party controls would be revealed that can also be helpful to find threats.

Ensure that you keep the contact information (email, phone, address) on file by your ASN in your regional registry (ARIN, RIPE, etc.) current at all times. In that manner, you will receive timely notifications such as electrifying and hijacking.
To every block of IP addresses that you have, you ought to form a ROA. One can think of this as a digital signature which means: These addresses only my ASN is allowed to advertise. Request your upstream providers to verify such signatures and any false announcements will be blocked automatically.
On your routers, only allow your exact IP ranges to be advertised. Block any private or unassigned addresses. Also, check that incoming BGP announcements from neighbors match the AS paths and prefixes you expect reject anything that doesn’t fit.
Implement real time notices where you are notified instantly of someone else advertising your prefixes or in case a route goes completely missing. After that, every month, you should put some more attention to analyze your routing table and RPKI status to prevent minor problems that can evolve into major ones.
Write names of whom to call in the upstream providers and registry in case of possible hijack. Do a mock BGP incident exercise every six to twelve months so when pressured your team understands exactly what they should be doing.
Keep WhoisFreaks’ ASN Whois Lookup bookmarked. In an emergency, you can quickly find out who owns a suspicious ASN and get the right contact info to report problems.
Make sure everyone who works on your network understands the basics of BGP, how to set up RPKI, and how to read routing tables. Share real‑world hijack stories so they see why these practices matter.
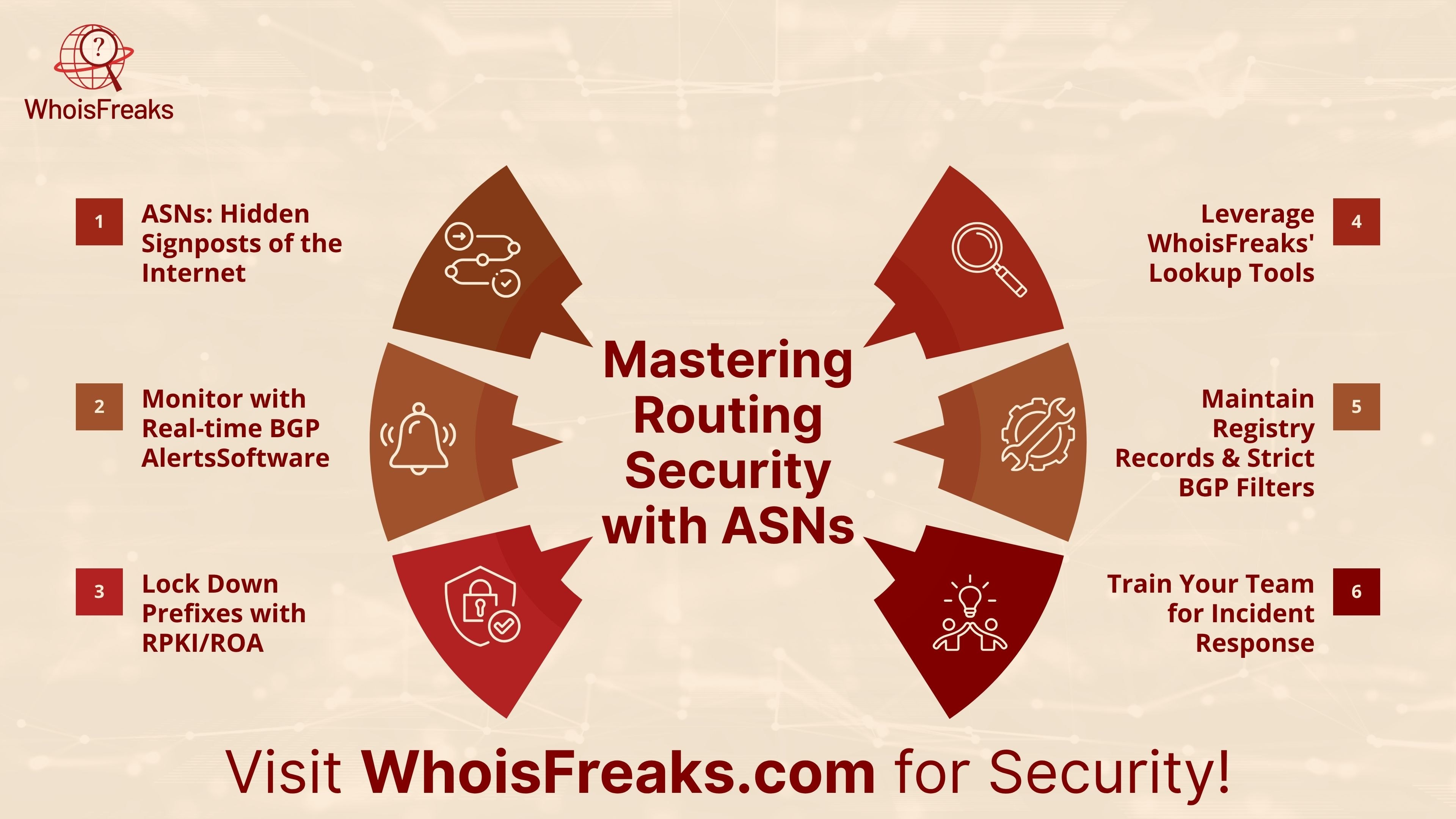
ASNs act like hidden signposts that guide your data across the internet. By watching your ASN with real‑time BGP alerts, using RPKI and ROA to cryptographically lock down prefix announcements, and leveraging WhoisFreaks’ ASN and IP lookup tools for ip intelligence , you can detect and stop route hijacks or spoofing before they impact your network. Keep your registry records up to date, apply strict BGP filters, and train your team on incident response to stay ahead of threats.
Ready to take control of your routing security? Visit WhoisFreaks.com now, look up your ASN, and set up simple BGP alerts today your network (and the wider internet) will thank you.