
Essential Strategies to Prevent Subdomain Takeover Vulnerabilities

By Qasim
Posted on November 18, 2025 | 8 min read


By Qasim
Posted on November 18, 2025 | 8 min read
A subdomain takeover occurs when an attacker gains control of a subdomain because its DNS record points to a service that no longer exists. Typically, this happens when a CNAME record or other DNS record remains active but no host is actually serving content at that address. In effect, the DNS entry is like a powered electrical outlet with no appliance plugged in an attacker can “plug in” their own malicious content.
For example, suppose support.screenshotapi.net CNAMEs to screenshot.zendesk.net, but the company stops using Zendesk without removing the DNS entry. Then an attacker could create a new Zendesk account under that name and hijack support.screenshotap.net to host a fake login form. This situation is called a dangling DNS record a DNS entry exists, but no valid host is providing content
Subdomain takeover happens when the subdomain DNS record is pointing to a deactivated or unclaimed resource. To provide an illustration, when survey.uber.com used to point to a Heroku application that Uber deleted, an attacker could make another application with the name survey.uber.com and reclaim it.

The hacker would then be able to put phishing sites or a virus on what appears to be a working Uber URL that can be identified through CNAME records. This occurred in 2017: security researcher Avinash Jain discovered that surveys.uber.com still had a third-party service that was not in use, and that it could be easily leveraged. One of the attackers alleged that a page stealing credentials had been hosted successfully in the domain of service, and that it had duped the users into believing the service.
The danger is severe due to the fact that subdomains tend to be forgotten; hence, it is crucial to identify them regularly . Test sites that are spun up by teams spin down or are abandoned on the cloud with no clean up of DNS. When a subdomain is kept publicly resolvable and it is outdated, an attacker may easily take control of it. To illustrate, hackers will persist in scanning CNAME or A records that target decommissioned cloud services and they will then take over control before anyone realizes.
The first step in prevention is knowing every subdomain your organization controls to access potential vulnerabilities. WhoisFreaks offers a Subdomains Lookup Tool / API that enumerates all known subdomains for a given domain. For example, an API call like
curl -X GET https://api.whoisfreaks.com/v1.0/subdomains?domain=example.com&status=active&apiKey=
returns a JSON list of subdomains. Each entry includes fields like subdomain, first_seen, and last_seen. The “first_seen” and “last_seen” timestamps show when each subdomain was discovered, helping you spot outdated or inactive services.
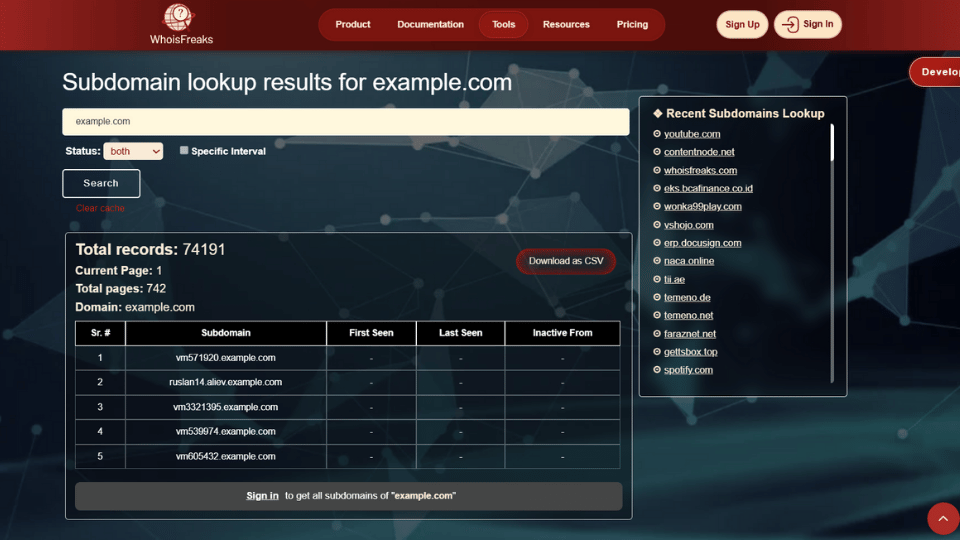
By using this tool, you can map your entire attack surface. As one WhoisFreaks guide explains, you should “scan your domain for newly created, forgotten, or unauthorized subdomains that may be exploited by attackers”. In practice, you’d regularly query the Subdomains Lookup API and compare results. Any unexpected subdomain, which could be a target for phishing campaigns, can be flagged for review. This automated inventory helps prevent blind spots that attackers could slip through.
In addition to active enumeration, WhoisFreaks includes historical data. The Subdomains API can also list inactive subdomains (if you set status=inactive), revealing records that once existed but are now down. This is critical: an inactive subdomain often means the linked service was removed, making it a takeover risk. The API’s “first_seen”/“last_seen” fields mean you can detect if a service linked to the target domain stopped responding at a certain point. As WhoisFreaks notes, such timeline data gives historical visibility into the presence and potential removal of services.
Key Feature: Subdomain Enumeration fetches all known subdomains for a given domain. This lets you discover hidden endpoints. Doing this regularly ensures no subdomain is forgotten.
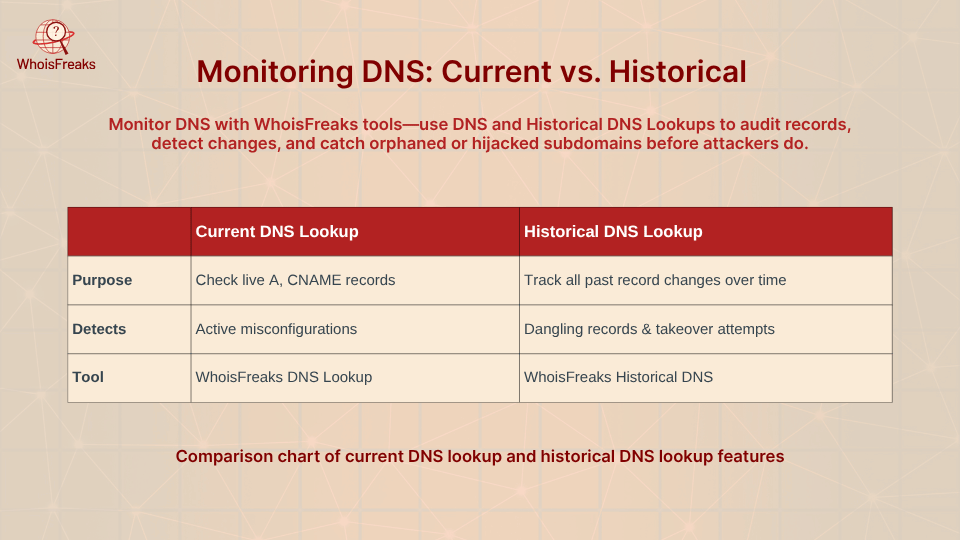
Once you have a list of subdomains, the next step is to check their DNS records. WhoisFreaks provides DNS tools to do this: the DNS Lookup Tool / API and Historical DNS Lookup Tool. These let you verify what each subdomain points to and how it has changed over time.
Using the DNS Lookup API, you can programmatically query any subdomain to see its current A, CNAME, or other records. For instance, if it unexpectedly points to an unfamiliar IP or external domain, that’s a red flag. WhoisFreaks also offers bulk DNS lookups, which can check many hosts at once.
For a deeper audit, the Historical DNS tool is invaluable. In one real-world scenario, a security team saw a suspicious URL in a phishing email (auth-login.screenshotapi.net) and used WhoisFreaks tools to investigate. They ran a Subdomains Lookup and saw auth-login.screenshotapi.net was active.
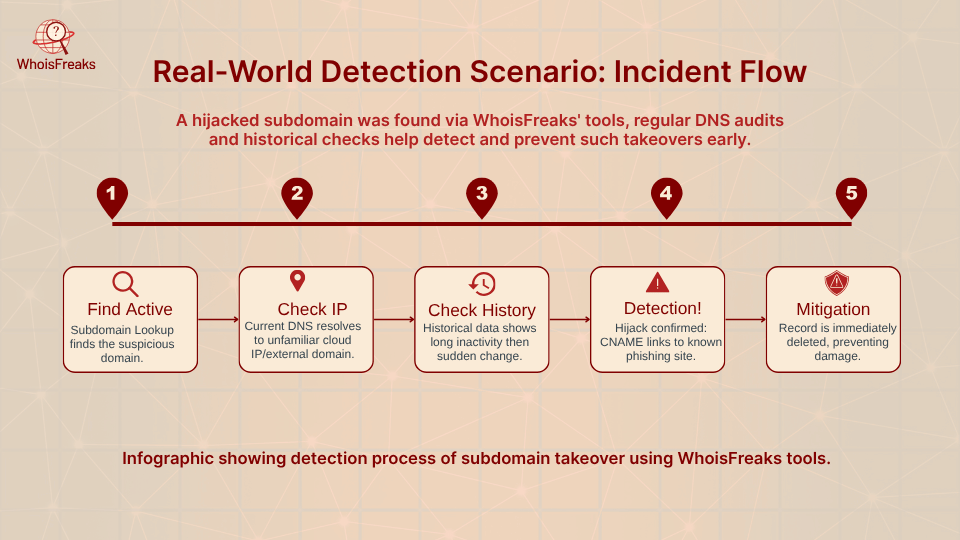
Then, using DNS Lookup, they saw it resolved to a cloud IP that their company doesn’t use. A Historical DNS query revealed that this subdomain had been inactive for months, then suddenly pointed to a third-party IP, with a CNAME linking to a known phishing site. That sequence of DNS queries showed it was a hijacked subdomain takeover/impersonation in progress, allowing them to act before damage.
This example illustrates two strategies in the process of preventing subdomain takeover :
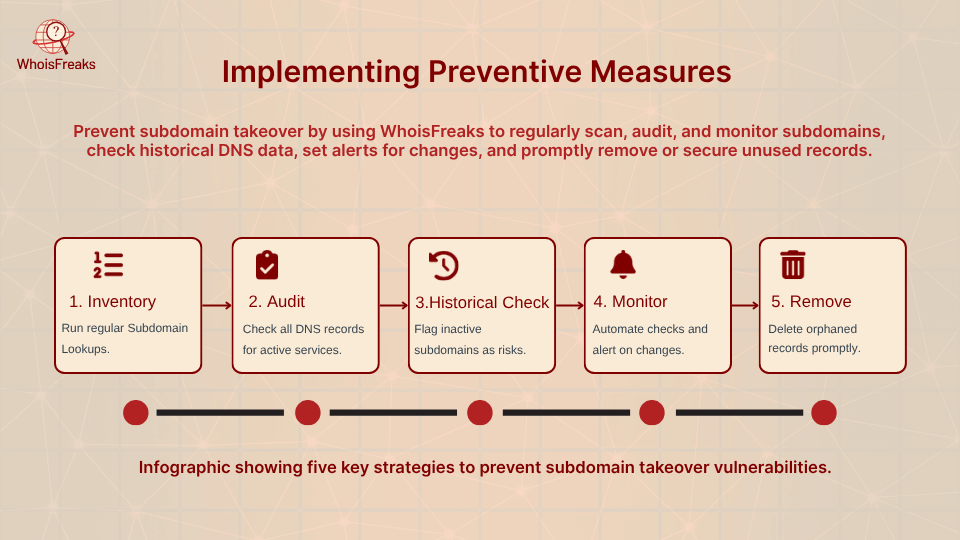
Having the right tools is only half the battle; you also need disciplined procedures. Based on industry best practices, here are the steps you can implement with WhoisFreaks:

A real example illustrates the danger. In 2017, Uber had a subdomain surveys.uber.com that was supposed to point to a third-party surveys service. When Uber stopped using that service, they failed to remove or update the DNS record. Security researcher Avinash Jain noticed that the CNAME still pointed to a Heroku host that no longer belonged to Uber. An attacker could have quickly claimed that Heroku app name and hosted malicious content at surveys.uber.com. Because the URL looked like an official Uber subdomain, users would trust it perhaps entering login credentials or personal data. Fortunately, this issue was discovered and reported, but it highlights the risk: forgotten subdomains are as good as open invitations to attackers.
Uber’s case underscores every strategy above. If Uber had had an up-to-date subdomain inventory, surveys.uber.com would have shown as inactive (last seen), triggering review. A DNS audit would have noted that the pointed service was deprecated. Monitoring tools would have flagged the reactivation of that target. Using WhoisFreaks tools would have caught surveys.uber.com as an active subdomain and its dead target, prompting cleanup before an attacker could exploit it.
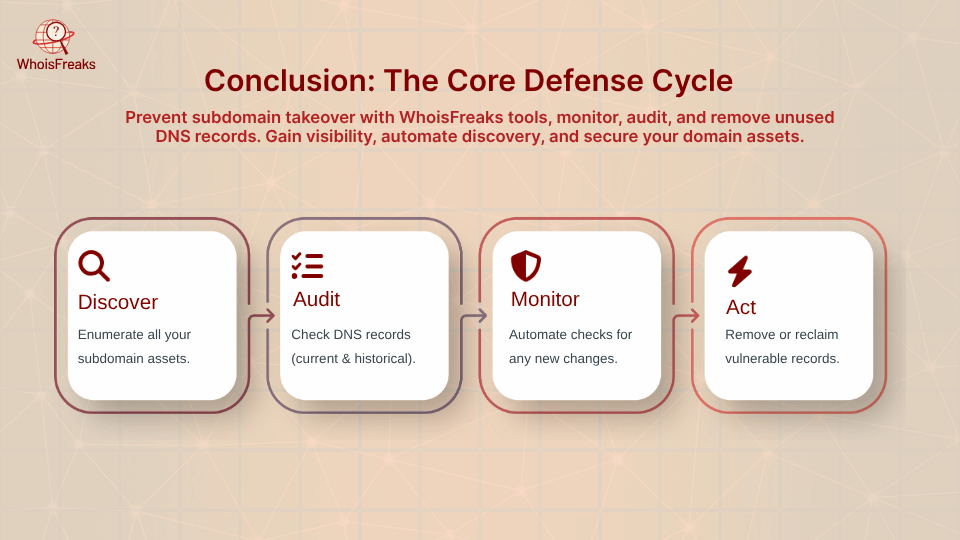
Subdomain takeover is a stealthy but preventable threat. The keys to defense are full visibility and routine hygiene. With the features of WhoisFreaks, organizations gain that visibility: the Subdomains Lookup tool/API finds every subdomain, the DNS Lookup and Historical DNS tools check their targets, and the Subdomains Database provides continuous monitoring. In practice, you should regularly enumerate your domains, audit each DNS record, and use automated alerts for any anomalies. When unused services are retired, remove or claim the corresponding subdomains.
By following these strategies auditing DNS, automating subdomain discovery, and applying best practices you can secure your DNS zone and keep attackers from hijacking your infrastructure. As experts remind us, preventing subdomain takeover is about disciplined asset management and leveraging the right tools. WhoisFreaks makes those tools accessible and easy to integrate, turning what could be blind spots into well-charted territory.

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Discover how to access and utilize daily newly registered domains to enhance your online strategy. Read the article for practical tips and insights.
6 min read