

By Nadeem Khan
Posted on March 25, 2025 | 10 min read
DNS spoofing is a growing concern for anyone who values online security and privacy. It’s a method used by hackers and cybercriminals to trick users and compromise sensitive information. The Domain Name System (DNS), which helps map domain names to IP addresses, is often at the heart of these attacks. Understanding DNS spoofing and how to protect yourself is crucial to keeping your online activities safe. Let’s dive into what DNS spoofing is, how it works, and how you can prevent it.
DNS spoofing is a type of man-in-the-middle attack. It targets the Domain Name System (DNS), which is key to network security. In this attack, the hacker intercepts DNS queries and responses. They can then send users to a fake or harmful website. This puts personal data at risk. Things like passwords, credit card numbers, and other details can be stolen.
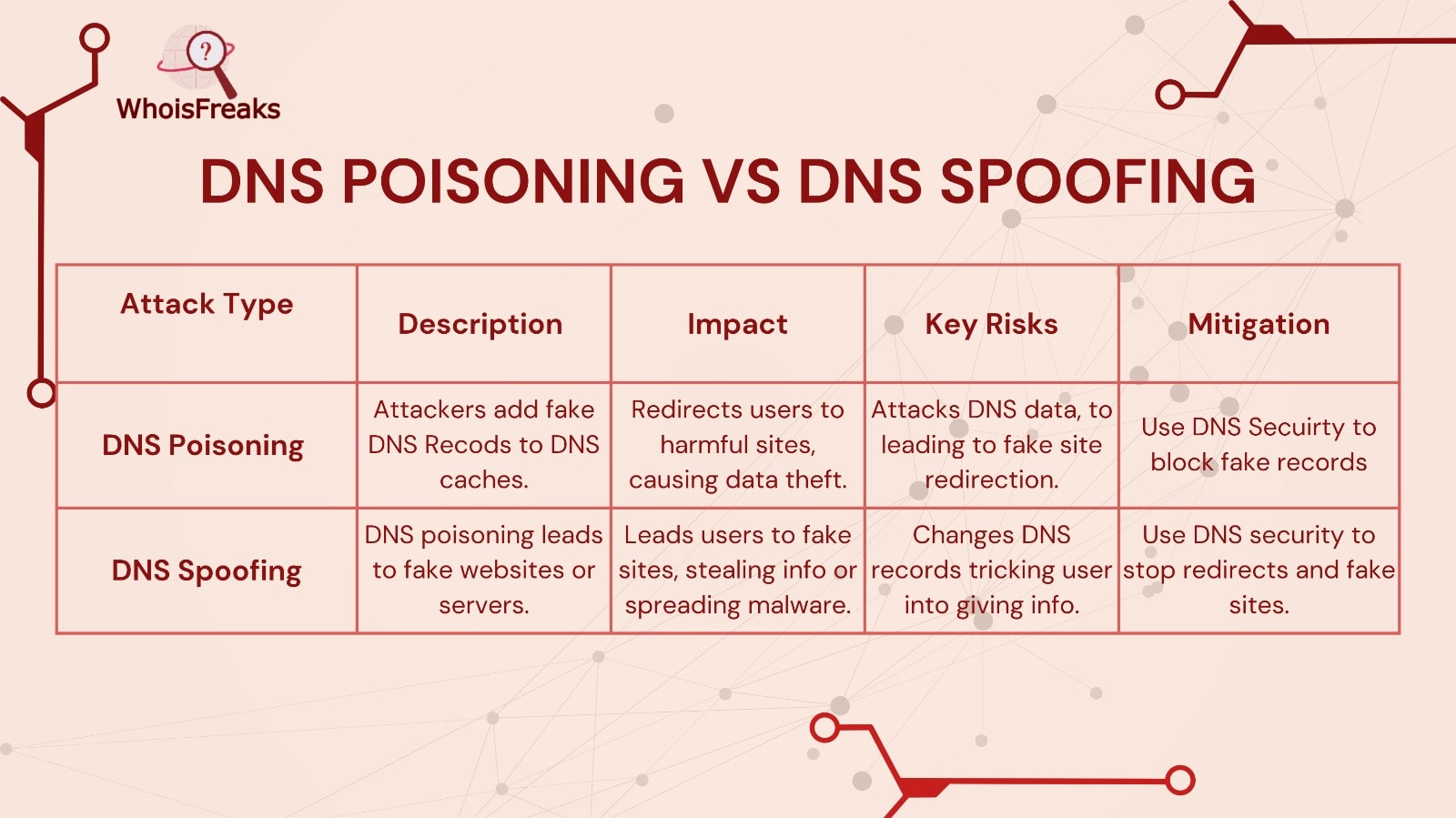
DNS spoofing is a serious cyber threat that compromises online safety, leading to identity theft, fraud, and malware infections. To stop it, we need strong methods and protections. Securing online data and using solid network security is key. By understanding DNS spoofing, you can keep your data safe. This helps protect personal and financial info from bad actors.
DNS spoofing takes advantage of flaws in DNS and its protocols.
DNS caching helps DNS servers and resolvers store data. This speeds up the resolution process and lowers network traffic. When you ask for a domain, the DNS server checks its cache for the corresponding IP address. If the data is cached, the server sends back the response fast. It doesn't need to contact authoritative DNS servers. But if the cache is tampered with, it can lead to DNS spoofing attacks. This causes the wrong IP addresses to be stored on servers. As a result, users may face security risks and malicious activities.
DNS spoofing is a big problem for data privacy. Phishing helps attackers trick users into giving away sensitive info. Attackers may want to steal banking information. To do this, they find a popular banking site, copy the code and styling files, then upload them to a malicious machine. This machine hijacks connections and sends users to fake sites.
These spoofed sites look real, but they often have small mistakes. One common issue is that they lack an encryption certificate. The connection is cleartext, meaning it is not encrypted. Browsers do alert users when the connection isn’t secure, but many ignore the warning. Users then enter their username, password, social security number, and private contact details into malicious site. All this information goes straight to the attacker. With enough stolen data, the attacker can open new accounts in the victim’s name. They can also access real accounts to steal more money and sensitive information.
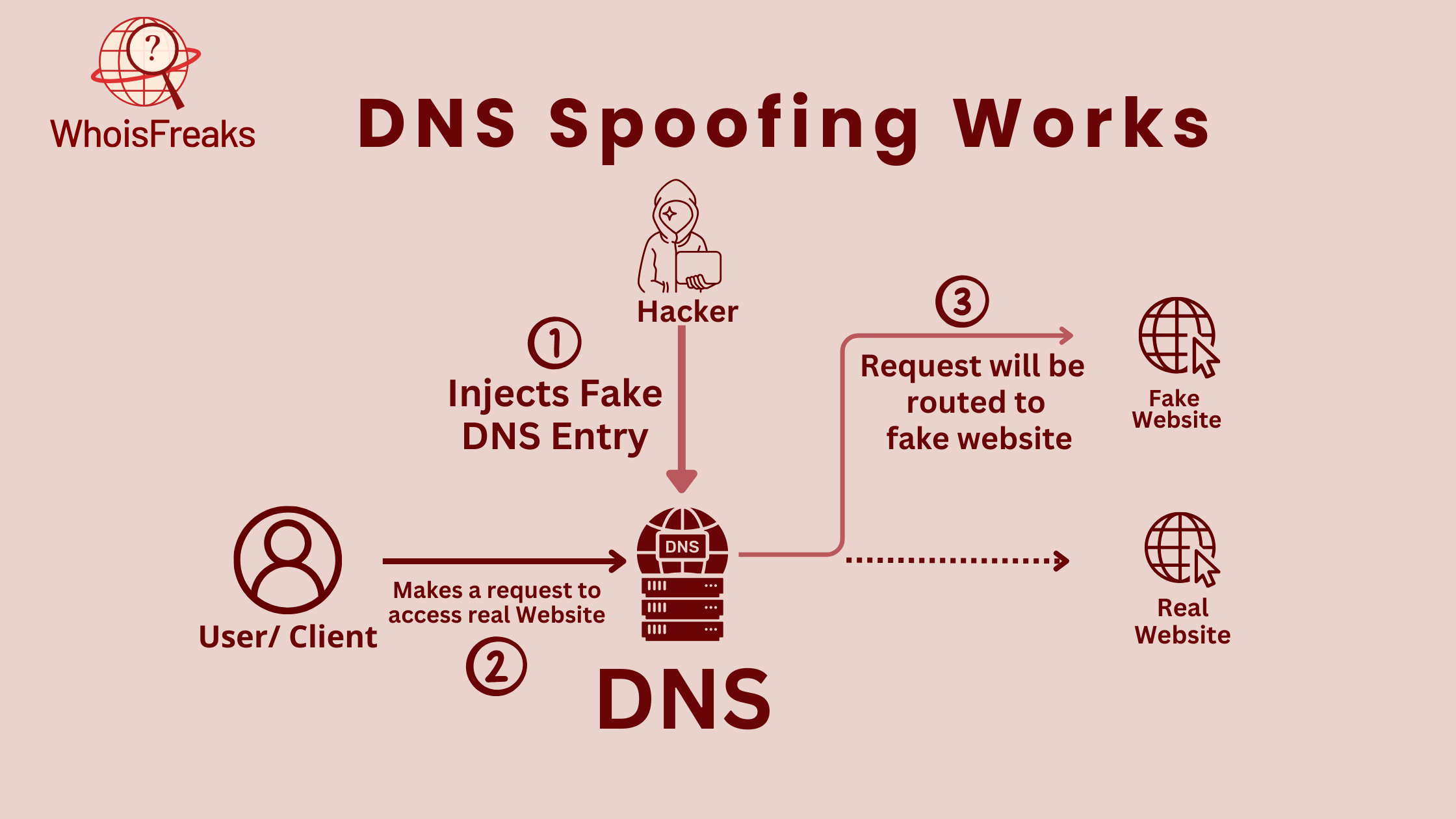
In normal DNS communication, the user's device sends a query when they want a website. The DNS resolver, managed by the user's ISP, gets the query. If the resolver doesn't have the client's IP address, it forwards the query to a root server. The root server sends the resolver to the right Top-Level Domain (TLD) server, like .com, .org, or .net. The TLD server points the resolver to the domain's name server, which gives the correct IP address. The resolver then sends this IP address to the user's device, letting it connect to the website. This process makes it easy for users to visit websites using simple domain names instead of long numeric IP addresses.
DNS spoofing attacks are used by hackers to carry out harmful actions. They steal sensitive information, launch phishing attacks, and spread malware. By spoofing DNS servers, hackers redirect network traffic to unauthorized sites. This allows them to commit ad fraud or even launch a DDoS attack.
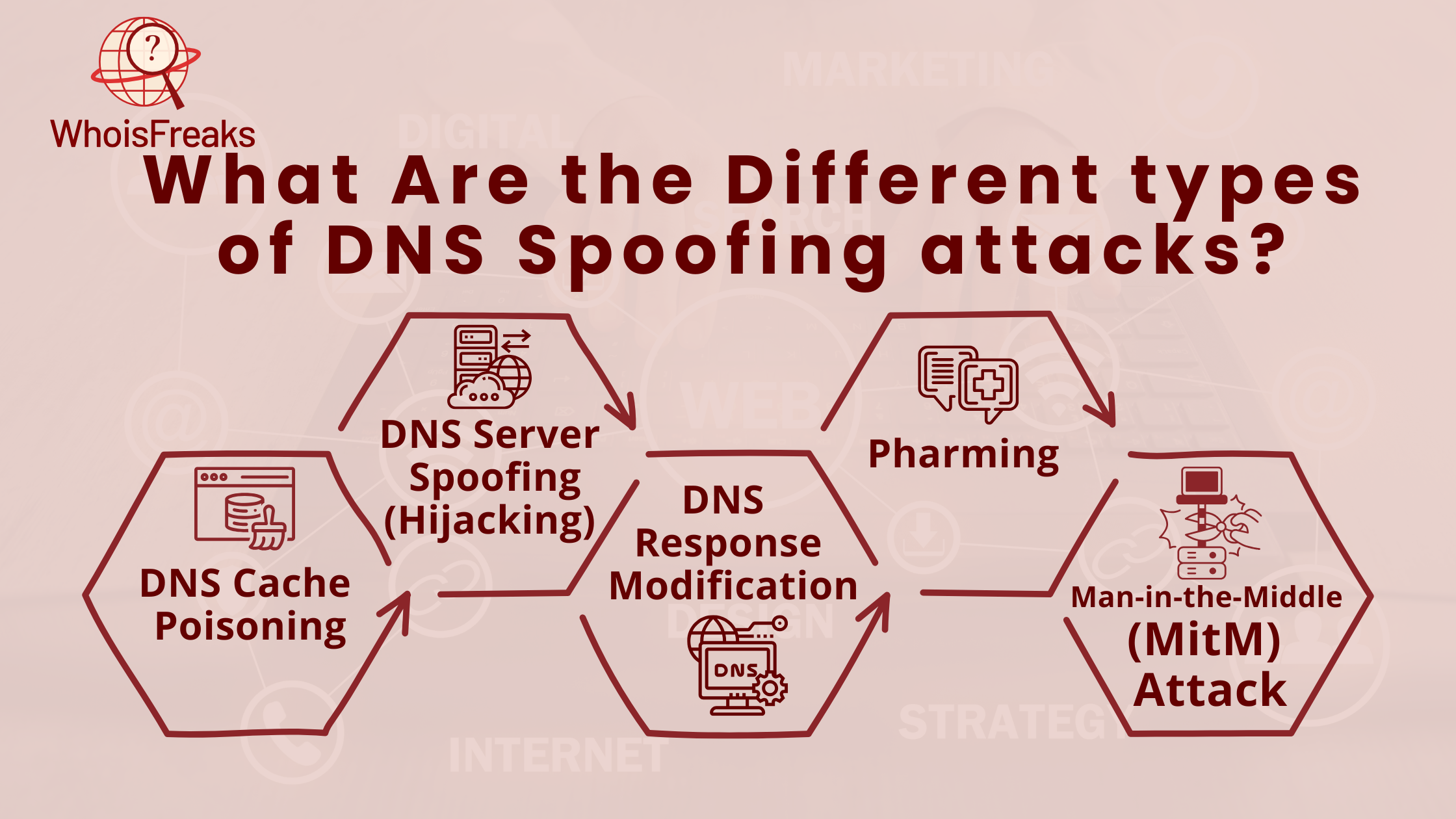
One common attack is DNS cache poisoning. In this attack, hackers add fake DNS records to a DNS resolver or router. This makes valid domain names point to the wrong malicious IP address or addresses. Users are then sent to fake websites where they may unknowingly enter sensitive data, like passwords.
DNS server spoofing, also called DNS hijacking, happens when hackers impersonate a real DNS server. They intercept DNS queries and send back fake DNS responses. This redirects users to unknown sites. Hackers can also use this attack to spy on network traffic or launch other cyberattacks.
DNS server spoofing (DNS hijacking) can happen due to NS record and A record tampering, allowing attackers to control DNS queries and send fake responses.
Another form of attack is DNS response modification. Hackers intercept real DNS responses and change them. This sends users to the malicious domains or websites instead of the correct ones. The attacker manipulates DNS resolution to make users visit fake sites without their knowledge.
DNS response modification occurs due to NS record tampering, where attackers alter real DNS responses to mislead users.
Pharming is when hackers manipulate DNS resolution to redirect users from legitimate site to fake websites. Users think they are visiting a real site, but they are sent to fraudulent ones. Hackers use pharming to steal personal data, such as credit card details or login credentials.
Pharming is caused by A record, NS record, and CNAME record tampering, which redirects legitimate website traffic to fraudulent sites.
A more advanced form of DNS spoofing is the Man-in-the-Middle (MitM) attack. In this attack, hackers intercept DNS communication between a client and a server. They can eavesdrop on or change the DNS traffic. The user unknowingly gets a false DNS response, which sends them to a harmful website controlled by the attacker.
Man-in-the-Middle (MitM) attacks on DNS occur due to A record, NS record, and PTR record tampering, allowing attackers to intercept and manipulate DNS communications.
DNS spoofing brings serious risks like data breaches, malware, and ransomware. Attackers can steal sensitive data such as company records, personal details, banking info, credit cards, and passwords. This data theft affects both businesses and individuals. For example, attackers can make a fake banking site. They trick users into entering login details. The attacker can then use these details for financial fraud. Here are the 3 most common risks associated with DNS spoofing:
Malicious websites play a big role in DNS spoofing. They redirect users to harmful sites. This can infect devices with malware or ransomware. Once infected, the device and IT systems are at risk. A single infected device can lead to a larger attack on the whole network.
DNS spoofing can also be used for censorship. Governments like China change DNS caches to block certain IPs, domains legitimate websites, and services. Malicious actors can also control browsing habits by blocking specific websites.
DNS spoofing can bring legal and regulatory risks. If organizations fail to protect sensitive data, they may face fines and legal action. For example, businesses in the EU must follow GDPR rules. In the U.S., healthcare companies must follow HIPAA laws. Not meeting cybersecurity standards can lead to reputational damage.
Detecting a DNS spoofing attack can be challenging, but with the right tools and methods, it becomes easier to spot. By monitoring DNS entries and requests, you can spot irregularities that may indicate an ongoing attack. Below are some key steps to help you detect a DNS spoofing attack.

Detecting a DNS spoofing attack starts with constant monitoring of DNS entries and requests. Setting a baseline DNS behavior is key to spotting any changes. With DNSSEC enabled, it can flag up spoofed responses and DNS responses that lack valid signatures, making attacks easier to detect.
A deep dive into the DNS cache is important. Regular checks on the DNS resolver cache can reveal inconsistencies. Look for mismatched or incorrect IP address and addresses, differences between cached records and authoritative DNS data, or changes in TTL values. These signs help spot potential issues.
Monitoring DNS queries is crucial. Track your DNS resolution patterns for any anomalies. Look out for sudden spikes in queries, slow response times, or repeated queries for non-existent domains. These unusual patterns can be a red flag for a DNS spoofing attack.
DNS spoofing attacks can compromise your online security and expose sensitive information. To protect against these attacks, it’s crucial to implement multiple preventive measures. Using tools like DNSSEC, DNS encryption, VPNs, and secure DNS resolvers can help safeguard DNS traffic, ensuring that your data remains safe from attackers. Below are key strategies to prevent DNS spoofing attacks.
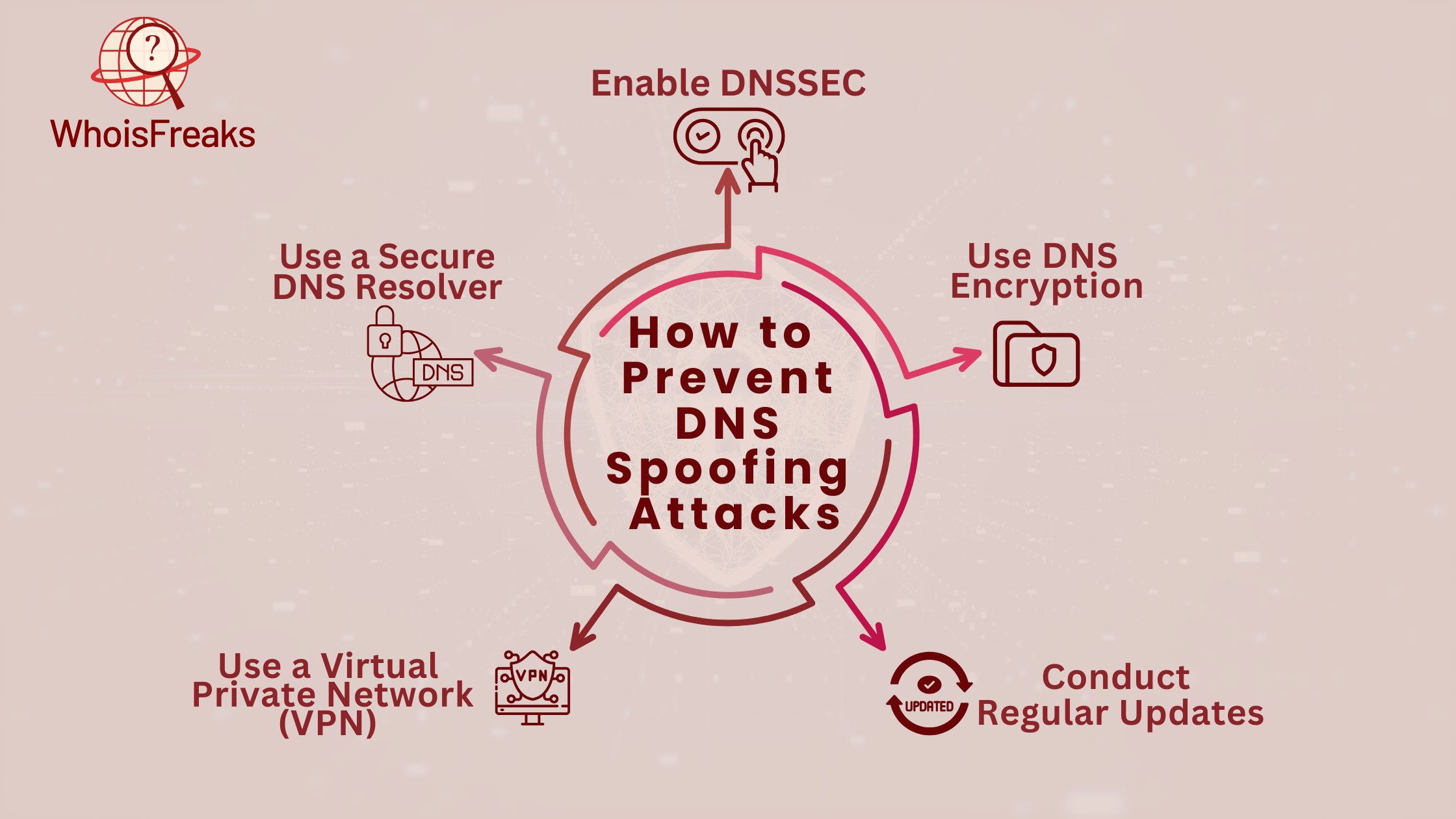
DNSSEC provides cryptographic authentication to ensure the integrity of DNS data. By verifying that DNS queries and responses are not tampered with, DNSSEC prevents manipulated data from being delivered to clients. This means your DNS resolver can block connections to known malicious domains and websites, reducing the risk of a DNS spoofing attack.
DNS encryption, using protocols such as DNS-over-TLS and DNS-over-HTTPS, ensures that DNS queries and responses between clients and resolvers cannot be intercepted or altered by attackers. This encryption safeguards DNS traffic from prying eyes, preventing attackers from hijacking DNS servers or viewing sensitive information.
Maintaining up-to-date operating systems, software, and servers is essential for defending against DNS spoofing attacks. Regular patches close security gaps that could be exploited by attackers. By keeping your system current, you strengthen your defenses against the latest cyber threats.
A VPN acts as a strong security measure, routing DNS queries through a private DNS server. This ensures that your DNS traffic is encrypted and protected from external threats. By bypassing your ISP or internet service provider's DNS server, a VPN can shield you from DNS server hijacking, offering enhanced protection for your online activities.
A secure DNS resolver is an essential tool for preventing DNS spoofing. Private DNS resolvers provide advanced protection by incorporating DNSSEC, DNS encryption, and malware blocking. They also offer DNS filtering capabilities, allowing you to tailor your security protocol and block harmful domains or services. With a secure resolver, you won't need to worry about manually updating DNS software, as it handles the security updates for you.
DNS spoofing attacks have caused major issues for many companies. In 2015, hackers took over the Malaysia Airlines website with a DNS spoofing attack. This led to reputational harm for the airline, which was already struggling. In 2018, hackers targeted Amazon Web Services. They redirected a cryptocurrency site to one they controlled, stealing over $17 million in Ethereum.
In 2019, a hacker group named Sea Turtle used DNS hijacking. They attacked 40 organizations across multiple countries, including government agencies. These examples show how DNS spoofing can hurt businesses, government groups, and individuals, stressing the need for strong security measures.
DNS spoofing targets a server's DNS registry. It redirects clients to a malicious address during a query. To protect against these spoofing attempts, organizations can use a DNS filtering solution like Heimdal® DNS Security. Heimdal hunts, prevents, detects, and blocks threats at the traffic level. Unlike traditional defenses, Heimdal’s machine learning-driven system offers strong protection. It defends against DNS attacks, providing full DNS protection and malware blocking. This ensures that the organization or user's computer network stays safe from potential risks.

Explore how combining Whois data, DNS, and SSL can enhance your analysis insights. Learn practical strategies to improve your data assessment—read more now!
11 min read

Learn what SSL/TLS certificates are and why they are essential for website security and data protection.
6 min read