
DNS over HTTPS vs DNS over TLS: What You Need to Know in 2025

By Qasim
Posted on May 22, 2025 | 11 min read
The Domain Name System (DNS) acts like the internet's phonebook, allowing a dns client to translate domain names like www.whoisfreaks.com into IP addresses that computers can understand. Every time you access a website, send an email, or use any online service, DNS is at work, ensuring your request reaches the right place.
However, traditional DNS has security and privacy issues. DNS queries are sent in plaintext, meaning they can be intercepted or altered by attackers. This opens the door for privacy violations and threats like DNS spoofing or man-in-the-middle attacks, especially when recursive DNS servers are involved which can redirect your traffic to dangerous websites.
With privacy concerns growing and cyber threats becoming more advanced, securing DNS traffic is now a top priority. This is where DNS over HTTPS (DoH) and authoritative DNS over TLS (DoT) come in. These protocols encrypt DNS queries, protecting your internet activity from eavesdropping, tampering, and other cyber threats.
In this blog, we’ll explore the differences between DoH and DoT, their benefits, and why they're crucial for online security in 2025.
What is DNS and How Does it Work?
DNS translates human-readable domain names (like whoisfreaks.com) into numeric IP addresses (like "x.x.x.x") that computers use to communicate. Without DNS, we'd have to remember numbers for every website, making browsing much harder.
Here’s how a DNS query works:
Request Initiation
When you type a URL, your browser first checks if it knows the IP address from a previous visit. If not, it sends a DNS request to a resolver (usually managed by your ISP).
Querying the Resolver
The resolver searches for the IP address by querying other DNS servers.
Returning the Response
Once the correct IP address is found, it’s sent back to your browser, which then connects to the website.
DNS Security Challenges and the Need for Encryption
DNS Caching and Its Risks
DNS caching helps speed up browsing by storing IP addresses from previously visited websites. While this improves performance, understanding how DNS work is critical as it can also introduce security risks.
- Cache Poisoning: This happens when hackers insert false DNS data into the cache, causing the resolver to send wrong IP addresses. Users might be redirected to fake websites for phishing or malware.
- Stale DNS Records: Cached records can become outdated, leading users to incorrect or unavailable sites, especially if a website changes its IP address or goes offline.

Why DNS Encryption is Important
DNS queries are usually sent in plaintext, making them easy for anyone to intercept and read, creating security vulnerabilities.
- Eavesdropping: Without encryption, attackers can see which websites users visit, particularly on public Wi-Fi networks, which puts users at risk of being tracked or attacked.
- Man-in-the-Middle Attacks: Hackers can intercept and alter DNS requests, redirecting users to malicious sites that seem real. This could lead to phishing or malware attacks.
- Privacy Concerns: DNS queries can reveal sensitive user information, such as interests or health details. Encrypting DNS traffic helps protect user privacy.
DNS Lookup Vulnerabilities
Traditional DNS lookups have several vulnerabilities that can cause issues:
- Spoofed Responses: Without encryption, attackers can send fake DNS responses, tricking users into visiting harmful websites. Using DNS over HTTPS (DoH) or DNS over TLS (DoT) ensures data integrity and prevents this.
- DNS Query Manipulation: Attackers can change DNS queries during transmission, leading users to fake sites. Both DoH and DoT protect against this by encrypting the queries, ensuring the correct site is reached.
DNS Over HTTPS (DoH) vs DNS Over TLS (DoT)
What is DNS Over HTTPS (DoH)?
DNS over HTTPS (DoH) encrypts DNS queries by sending them over HTTPS (the secure protocol used for web traffic). This makes DNS queries private and prevents them from being intercepted or altered.
How It Works
When you make a DNS query using DoH, the request is sent as an HTTPS request to a DoH-enabled DNS server. The server responds with the DNS data, also over HTTPS, ensuring privacy and security.
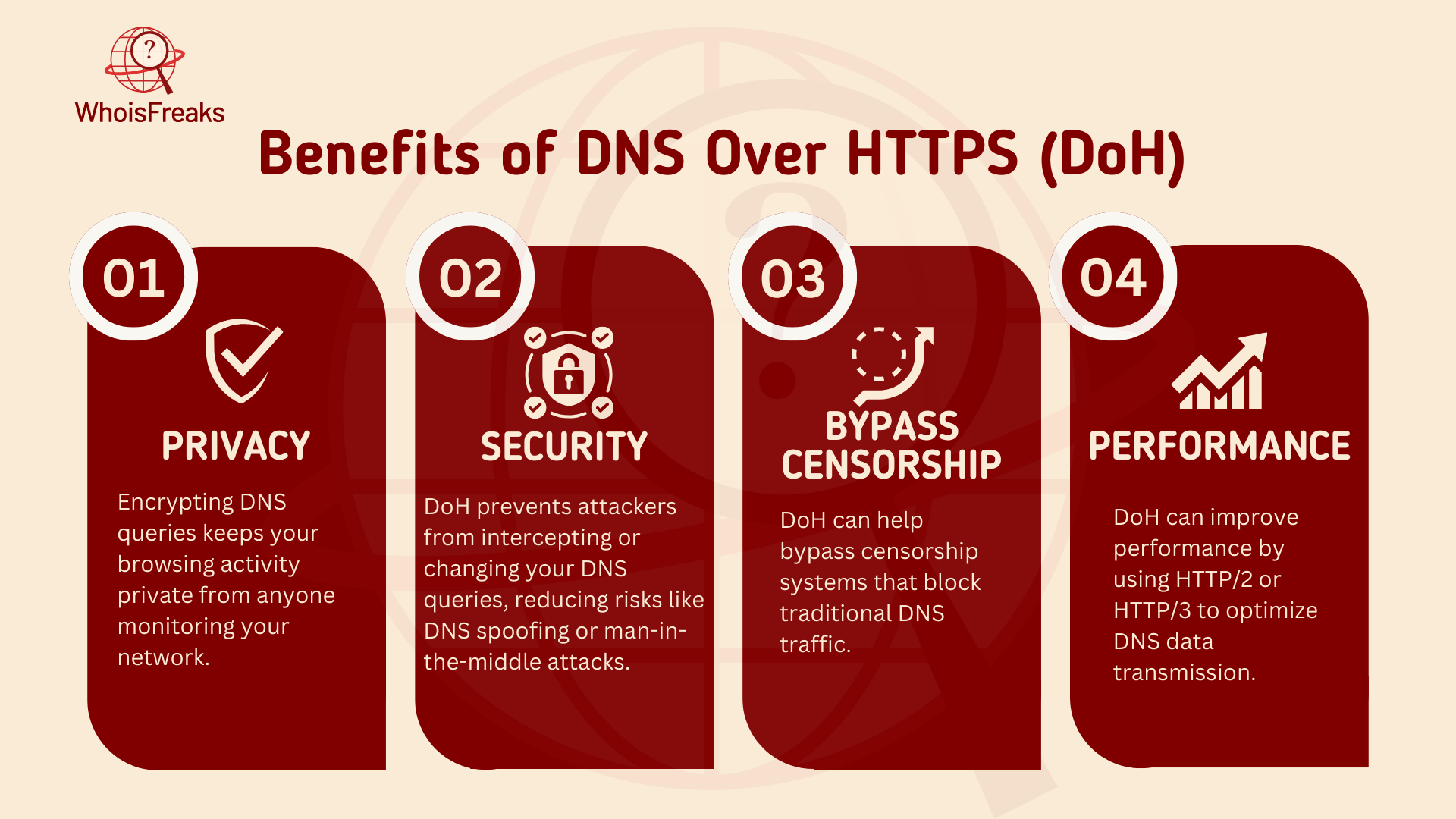
- Privacy: Encrypting DNS queries keeps your browsing activity private from anyone monitoring your network.
- Security: DoH prevents attackers from intercepting or changing your DNS queries, reducing risks like DNS spoofing or man-in-the-middle attacks.
- Bypass Censorship: DoH can help bypass censorship systems that block traditional DNS traffic.
- Performance: DoH can improve performance by using HTTP/2 or HTTP/3 to optimize DNS data transmission.
Benefits of DoH:
What is DNS Over TLS (DoT)?
DNS over TLS (DoT) also encrypts DNS traffic but uses Transport Layer Security (TLS), the same encryption protocol used for emails, to secure DNS queries.
How It Works
In DoT, DNS queries are sent over a dedicated TLS connection, usually on port 853, to a DoT-enabled DNS server. This keeps the DNS traffic encrypted and safe from interception.
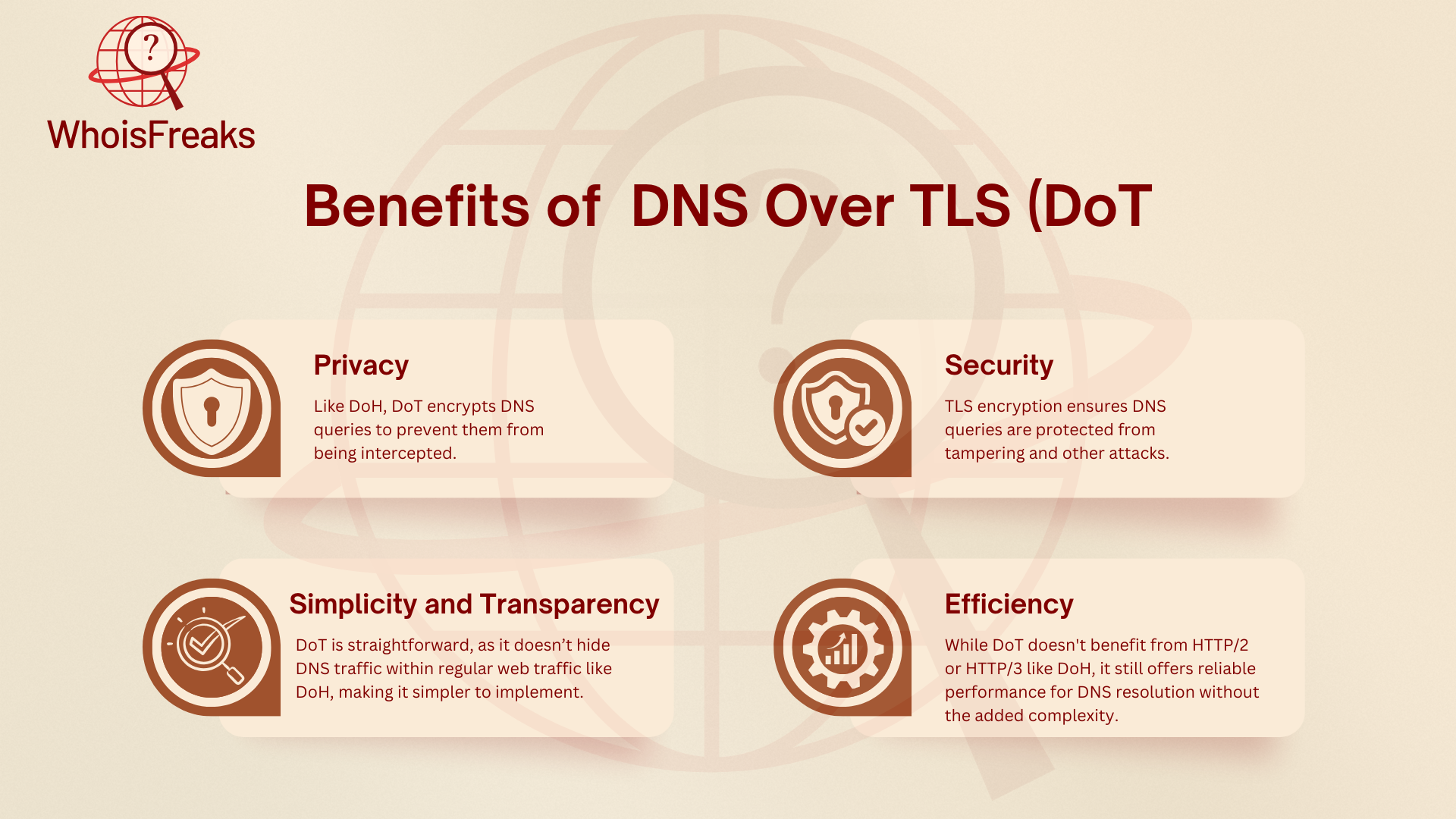
- Privacy: Like DoH, DoT encrypts DNS queries to prevent them from being intercepted.
- Security: TLS encryption ensures DNS queries are protected from tampering and other attacks.
- Simplicity and Transparency: DoT is straightforward, as it doesn’t hide DNS traffic within regular web traffic like DoH, making it simpler to implement.
- Efficiency: While DoT doesn't benefit from HTTP/2 or HTTP/3 like DoH, it still offers reliable performance for DNS resolution without the added complexity.
Benefits of DoT:
Comparison of DoH and DoT
| Feature | DNS over HTTPS (DoH) | DNS over TLS (DoT) |
|---|---|---|
| Encryption Protocol | Uses HTTPS (Hypertext Transfer Protocol Secure) | Uses TLS (Transport Layer Security) |
| Port | Uses standard port 443 (the same as HTTPS) | Uses dedicated port 853 |
| Traffic Visibility | DNS traffic is hidden inside regular HTTPS traffic | DNS traffic is sent over a dedicated TLS connection |
| Privacy | Offers higher privacy by embedding DNS queries inside HTTPS traffic, making it harder to detect | Provides privacy but may be more easily detected due to a dedicated port |
| Security | Protects against eavesdropping, man-in-the-middle attacks, and DNS spoofing | Also protects against eavesdropping, man-in-the-middle attacks, and DNS spoofing |
| Performance | Can leverage HTTP/2 and HTTP/3 for faster transmission | May not benefit from the same HTTP performance optimizations but still offers good performance |
| Compatibility | Supported by modern browsers (Firefox, Chrome, etc.) | Requires more manual configuration on devices or servers |
| Network Filtering | Less likely to be blocked due to using port 443 (common for HTTPS) | More likely to be blocked by firewalls or network filters due to dedicated port 853 |
| Centralization and Trust | May centralize traffic with third-party servers (e.g., Cloudflare, Google) | More transparent and easier for network administrators to manage |
| Ease of Configuration | Easier for end-users, especially in modern browsers | More complex to configure, especially for individual users |
DNS Over HTTPS vs DNS Over TLS in 2025
1. Adoption Trends and Industry Support
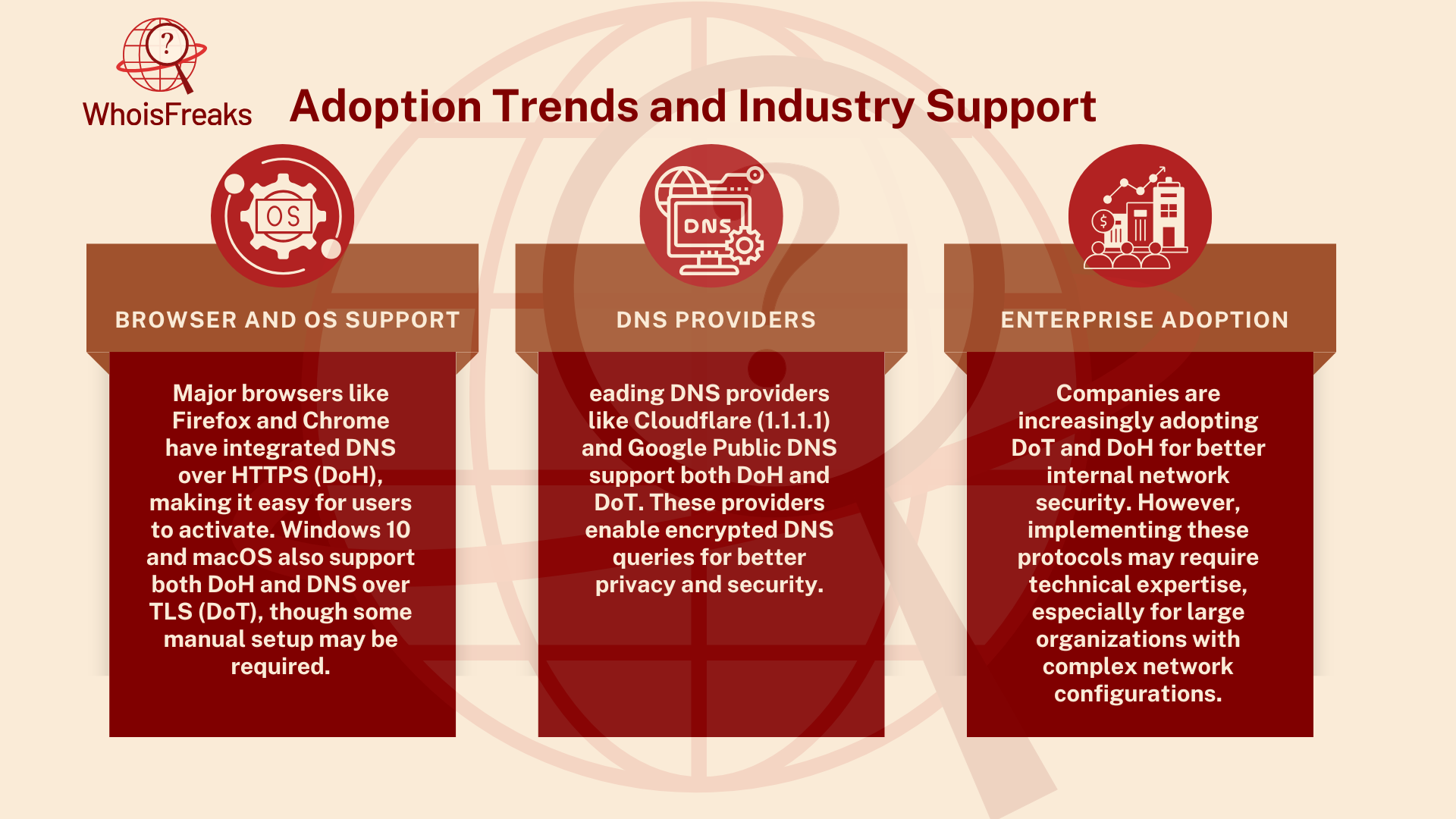
- Browser and OS Support:
Major browsers like Firefox and Chrome have integrated DNS over HTTPS (DoH), making it easy for users to activate. Windows 10 and macOS also support both DoH and DNS over TLS (DoT), though some manual setup may be required. - DNS Providers:
Leading DNS providers like Cloudflare (1.1.1.1) and Google Public DNS support both DoH and DoT. These providers enable encrypted DNS queries for better privacy and security. - Enterprise Adoption:
Companies are increasingly adopting DoT and DoH for better internal network security. However, implementing these protocols may require technical expertise, especially for large organizations with complex network configurations.
2. Performance Considerations
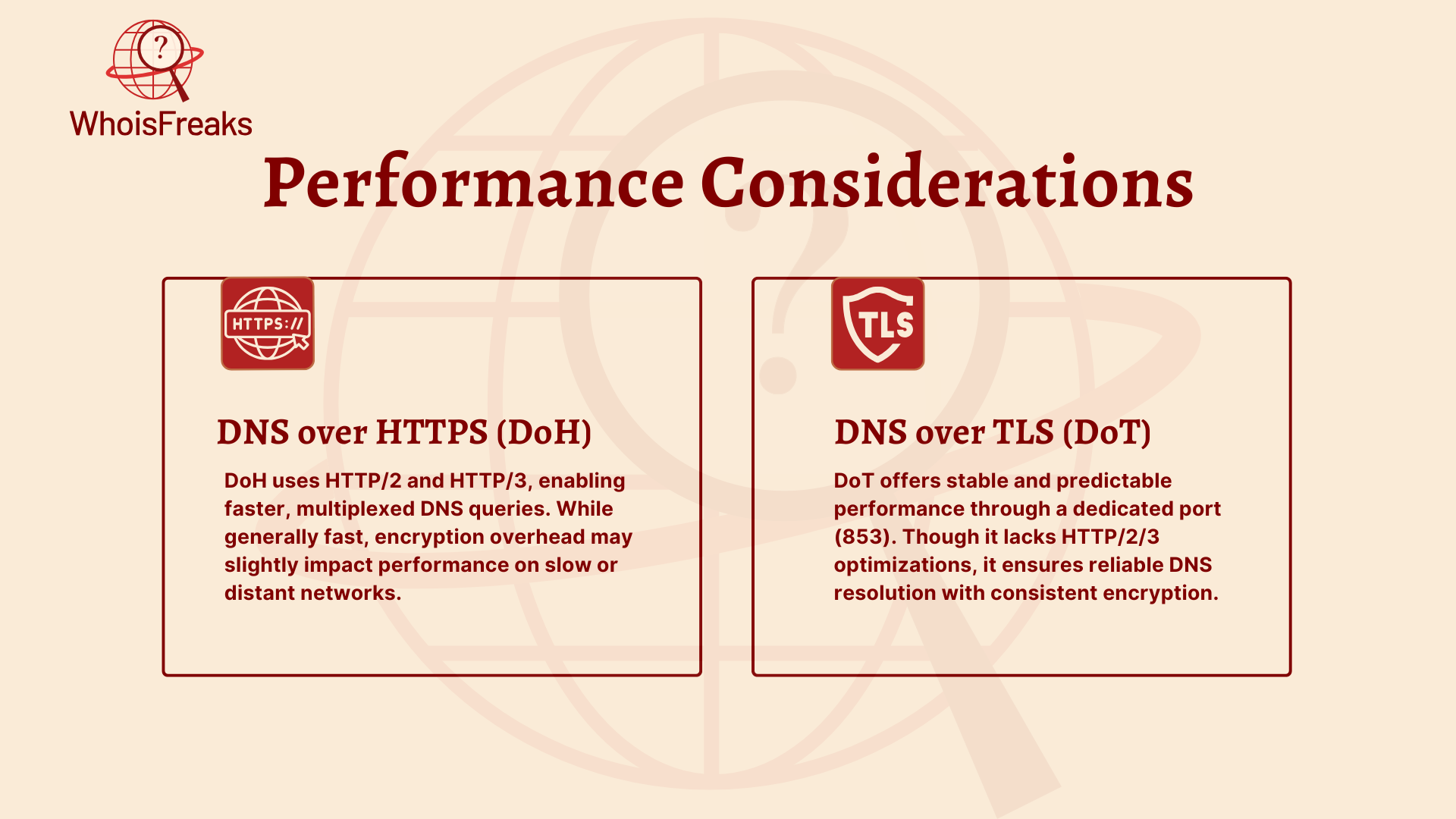
DNS over HTTPS (DoH):
One of the advantages of DNS over HTTPS (DoH) is that it uses HTTP/2 and HTTP/3 protocols, which help speed up the transmission of data and allow the handling of multiple requests at the same time. This can improve browsing performance, especially in environments with high traffic. However, a downside of DoH is the potential for slight delays due to the encryption process. This overhead can become more noticeable when connecting to distant DNS servers or when networks are under heavy load.
DNS over TLS (DoT):
DNS over TLS (DoT) provides more consistent performance by using a dedicated port (port 853) specifically for DNS traffic, which reduces the likelihood of interference from other types of network activity. This results in more predictable and stable DNS resolution. On the other hand, DoT does not benefit from the optimizations of HTTP/2 and HTTP/3, meaning it may not be as fast as DoH in some situations. However, it still offers reliable and efficient DNS resolution.
3. Impact on Privacy and Security in 2025
Protection Against Eavesdropping:
Both DoH and DoT encrypt DNS queries, making it impossible for third parties to see which websites you're visiting.
DNS Spoofing & MitM Attacks:
Both protocols prevent DNS spoofing and man-in-the-middle attacks by ensuring that DNS queries and responses are not altered or intercepted.
Adoption for Enhanced Security:
As cyber threats become more advanced, adopting DoH or DoT is becoming essential for securing DNS traffic and protecting sensitive information.
Choosing Between DNS Over HTTPS (DoH) and DNS Over TLS (DoT)
When deciding between DNS over HTTPS (DoH) and DNS over TLS (DoT), especially for a top-level domain the best choice depends on your security needs, ease of use, and system compatibility.
DoH (DNS over HTTPS)
For most individual users, DoH is the simpler option. It's already built into browsers like Firefox and Chrome, making it easy to enable directly in the settings. DoH uses the same port (443) as regular HTTPS traffic, making it harder for third parties to detect or block. This is ideal for users who want private and encrypted browsing without much setup.
DoT (DNS over TLS)
DoT requires more configuration, as it operates on a dedicated port (853). While this makes it more transparent, it also allows for easier monitoring and management. For users who prefer a more straightforward and visible approach to DNS traffic, DoT might be the better choice.
For Businesses and Organizations
DoT is often preferred, as it’s easier to manage at a network level. It provides clearer visibility of DNS traffic, which is important for monitoring and controlling DNS queries. DoH, while useful for bypassing network restrictions, can be more challenging to implement on a larger scale and might require more configuration.
Ease of Setup
DoH is typically easier for end-users, as its integrated into browsers and can be enabled by selecting a DNS provider like Cloudflare or Google DNS. DoT, on the other hand, often requires configuration at the system or router level, which can be more technical.
For Larger Networks
DoT offers better control and simplicity for monitoring and configuration, though it requires a more hands-on setup. Businesses may need to install DNS forwarders or upgrade their network to fully support DoT.
Troubleshooting and Common Issues with DoH and DoT
While DNS over HTTPS (DoH) and DNS over TLS (DoT) improve security and privacy, they can introduce some issues. Here are common problems and tips for troubleshooting.
Common Problems with DoH and DoT
Connection Failures
This can happen if the DNS resolver is incorrectly configured or the DNS server is down. Firewalls or routers blocking required ports (port 853 for DoT and port 443 for DoH) can also cause this issue.
Slower DNS Resolution
The encryption in DoH and DoT can sometimes slow down DNS resolution, especially on slower networks or when connecting to distant servers.
Compatibility Issues:
Not all devices or software support DoH or DoT. Older routers or network devices might not handle encrypted DNS traffic, and some DNS resolvers may not fully support both protocols.
Network Configuration Conflicts
In corporate networks, using DoH or DoT might conflict with other DNS configurations, like network filters or security appliances, which might not work properly with encrypted DNS.
Fixing Configuration Issues
Check DNS Server Configuration:
Ensure the DNS resolver is correctly set up. For DoH, verify that the resolver URL is correct (e.g., https://1.1.1.1/dns-query for Cloudflare). For DoT, ensure the server and port are correct (e.g., 1.1.1.1:853 for Cloudflare’s DoT server).
Verify Firewall and Router Settings
DoH (port 443) and DoT (port 853) require specific ports to be open. Make sure your firewall or router is not blocking these ports.
Test DNS Resolution
Use tools like nslookup or dig to test your DoH or DoT configuration. For DoH, you can test using https://1.1.1.1/dns-query or another supported DoH server.
Update Software and Hardware
Make sure your browser, operating system, and network hardware (e.g., routers) are up to date. Updates may fix compatibility issues.
Revert to Unencrypted DNS
If the issue persists, temporarily revert to unencrypted DNS. This can help determine whether the problem is with DoH/DoT or with DNS in general.
By following these steps, you can troubleshoot and resolve common issues with DoH and DoT.
Conclusion: The Importance of DNS Encryption Moving Forward
As we’ve seen, both dot DNS over HTTPS (DoH) and DNS over TLS (DoT) are key technologies in improving internet security and privacy. These protocols ensure that DNS queries are encrypted, protecting users from eavesdropping, tampering, and other cyberattacks.
In 2025, DNS encryption is more critical than ever. With the rise of cyber threats targeting both personal and corporate data, securing the first step in internet communication—DNS—is vital for maintaining privacy and security. DoH and DoT protect user data, improve ip address information browsing privacy, and prevent threats like DNS spoofing and man-in-the-middle attacks.
Choosing between DoH and DoT depends on your DNS settings and needs. Individuals may prefer DoH for its ease of use, while businesses might opt for DoT for greater control and transparency over DNS traffic. As more devices and networks adopt these protocols, DNS security will continue to improve.
Looking ahead, the growing use of DoH and DoT, along with other security measures like DNSSEC, will help create a more secure and private internet. These protocols will play a crucial role in shaping the future of internet security.
In conclusion, if you haven’t already, it’s time to switch to DNS over HTTPS or DNS over TLS. Whether for personal or business use, these protocols are essential for a safer and more secure digital experience. The future of the internet relies on encrypted DNS traffic, especially as users type URLs into the address bar and adopting these protocols is a key step in making that future a reality.
FAQs
1. Which is better, DNS over HTTPS or DNS over TLS?
2. What are the disadvantages of DNS over TLS?
3. What are the risks of DNS over HTTPS?
4. What does DoH stand for?
Related Posts

Understanding DNS Poisoning: Risks and Prevention Strategies
Discover essential insights on DNS poisoning and learn practical steps to safeguard your online presence. Read the article for vital protection tips.
10 min read

Defending Against DNS Flood Attacks: Leveraging WhoisFreaks Tools for Security
Learn how a DNS flooder can threaten your network security and discover practical measures to protect your systems. Read more to safeguard your network.
10 min read

What is the Purpose of DNS Server? Understanding Its Role and Benefits
Discover the essential role of DNS servers in internet functionality and learn how they enhance your online experience. Read the article for insights.
9 min read