

By Qasim
Posted on October 22, 2025 | 9 min read
Phishing remains one of the most widespread attack vectors on the Internet. Cybercriminals continuously register look‑alike phishing sites, hide behind anonymity services, spin up malicious sub‑domains, and spoof legitimate certificates to lure victims into divulging credentials or installing malware. For security teams and even general tech users, staying ahead of this dynamic threat landscape requires a combination of domain intelligence, continuous monitoring and fast response. WhoisFreaks an extensive platform offering domain‑related APIs, data feeds and monitoring services provides the building blocks needed to build a robust anti‑phishing solution.
This guide explores how phishing campaigns work, then shows how to combine WhoisFreaks' tools to detect suspicious domain registrations, verify SSL certificates, identify malicious IPs, track brand misuse and automate proactive defenses. Whether you are a cybersecurity professional looking to enrich threat intelligence or a general tech reader wanting to protect a digital brand, the article will help you build an anti‑phishing strategy using real‑time data, automated monitoring, and anti-phishing tools.
Phishing attacks generally follow a predictable lifecycle:
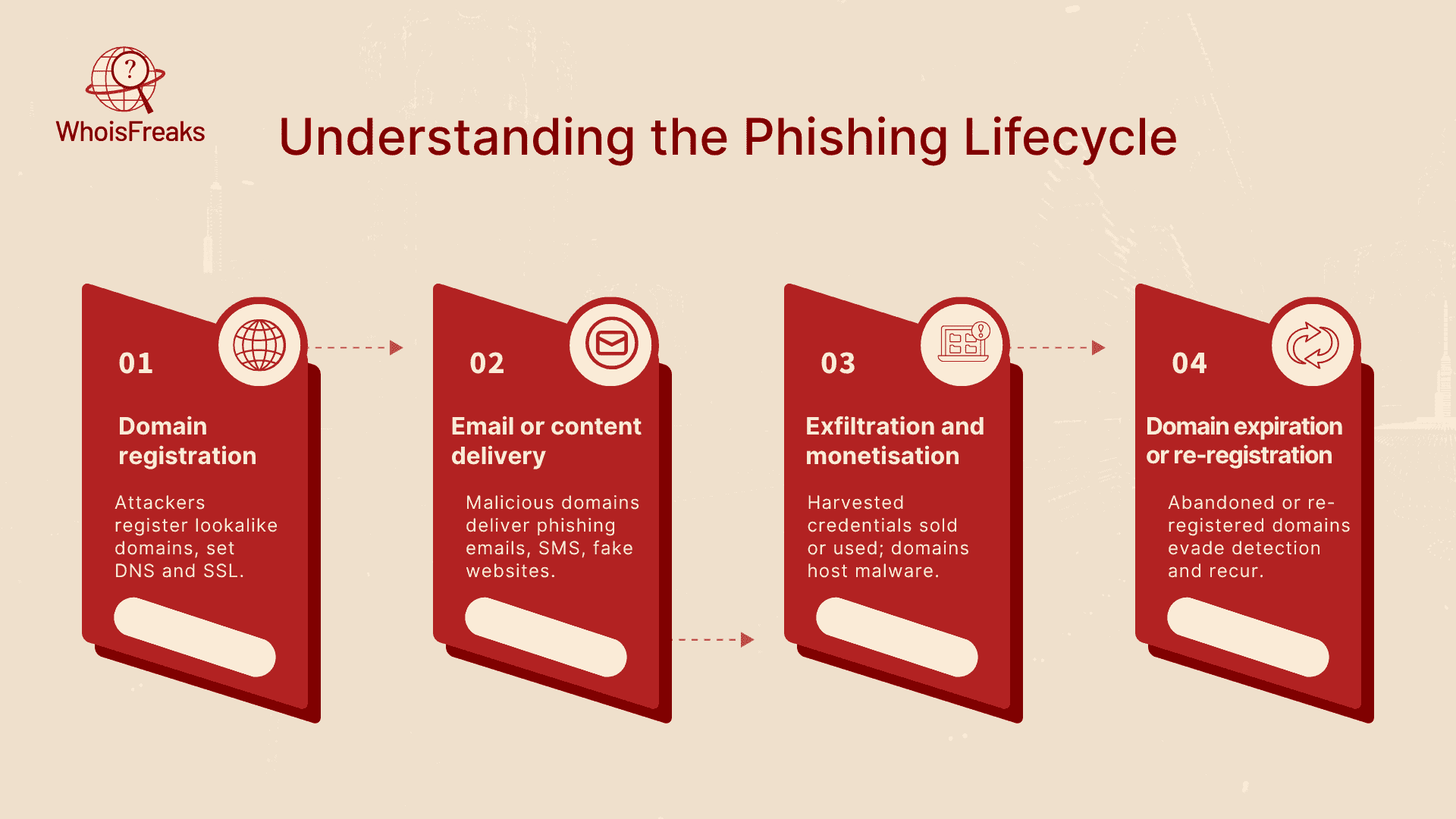
Traditional anti‑phishing measures, such as spam filters or URL block lists, often react after a campaign has caused damage. Domain intelligence provides the context behind a domain: who owns it, when it was registered, where its nameservers and IP addresses reside, whether it uses privacy services or appears on blacklists. Combining these signals reveals patterns that are hard to fake. For example, if a domain claiming to represent a global bank was registered only yesterday using a privacy proxy in an unrelated country, its legitimacy is questionable due to the tactics often employed in social engineering . Real‑time data about newly registered domains, sub‑domain enumeration, SSL certificate chains and IP geolocation can expose malicious infrastructure before phishing emails are sent.
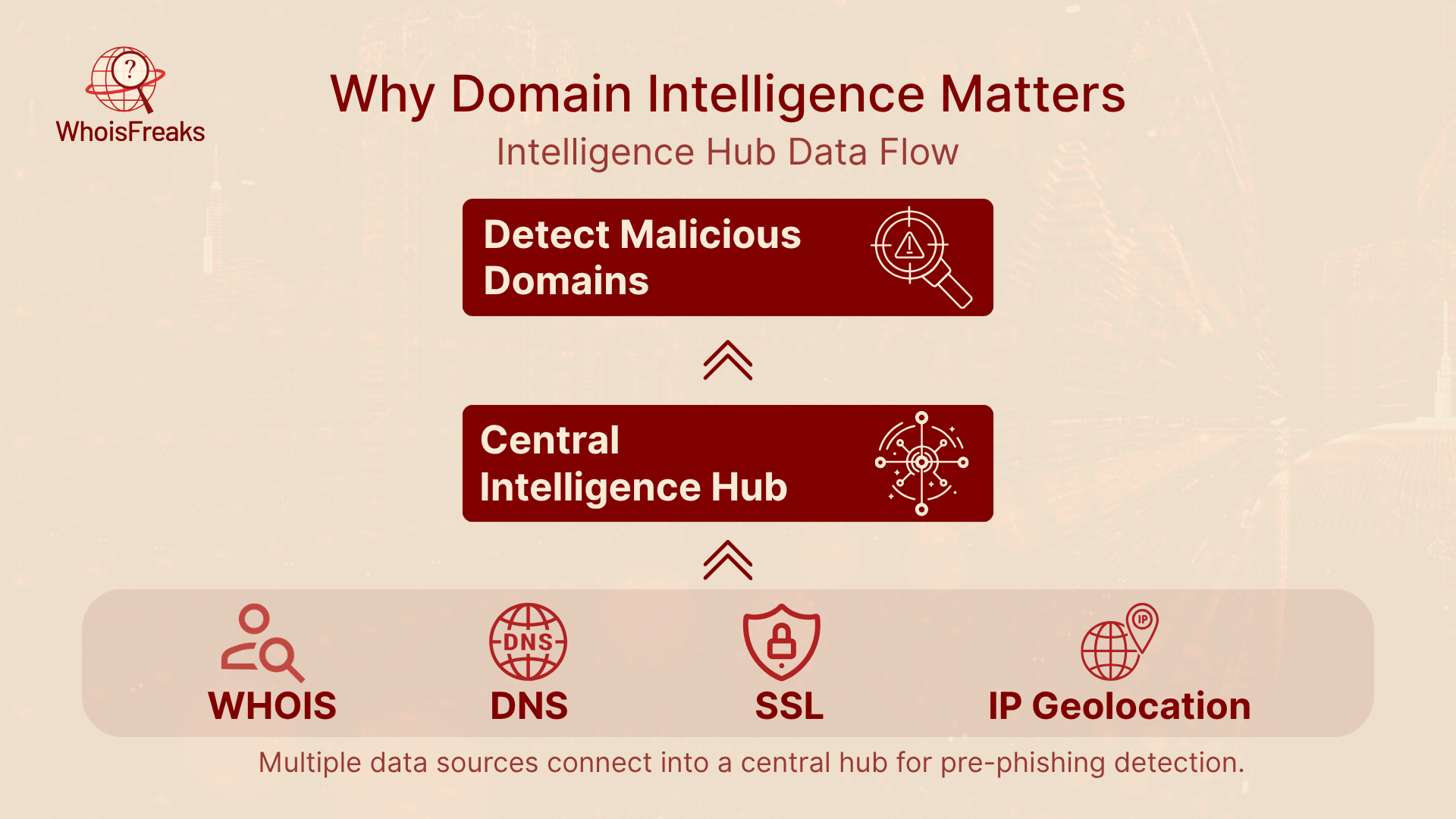
WhoisFreaks offers a diverse set of API solutions, data feeds and monitoring services. The home page lists several APIs for domain intelligence, DNS records, IP geolocation, SSL information and threat lookup, alongside data feeds such as newly registered domains and monitoring services for domains, brands and registrants. These capabilities span the entire domain lifecycle, enabling proactive detection and continuous surveillance, making it one of the best anti phishing solutions available. Key solutions relevant to anti‑phishing include:
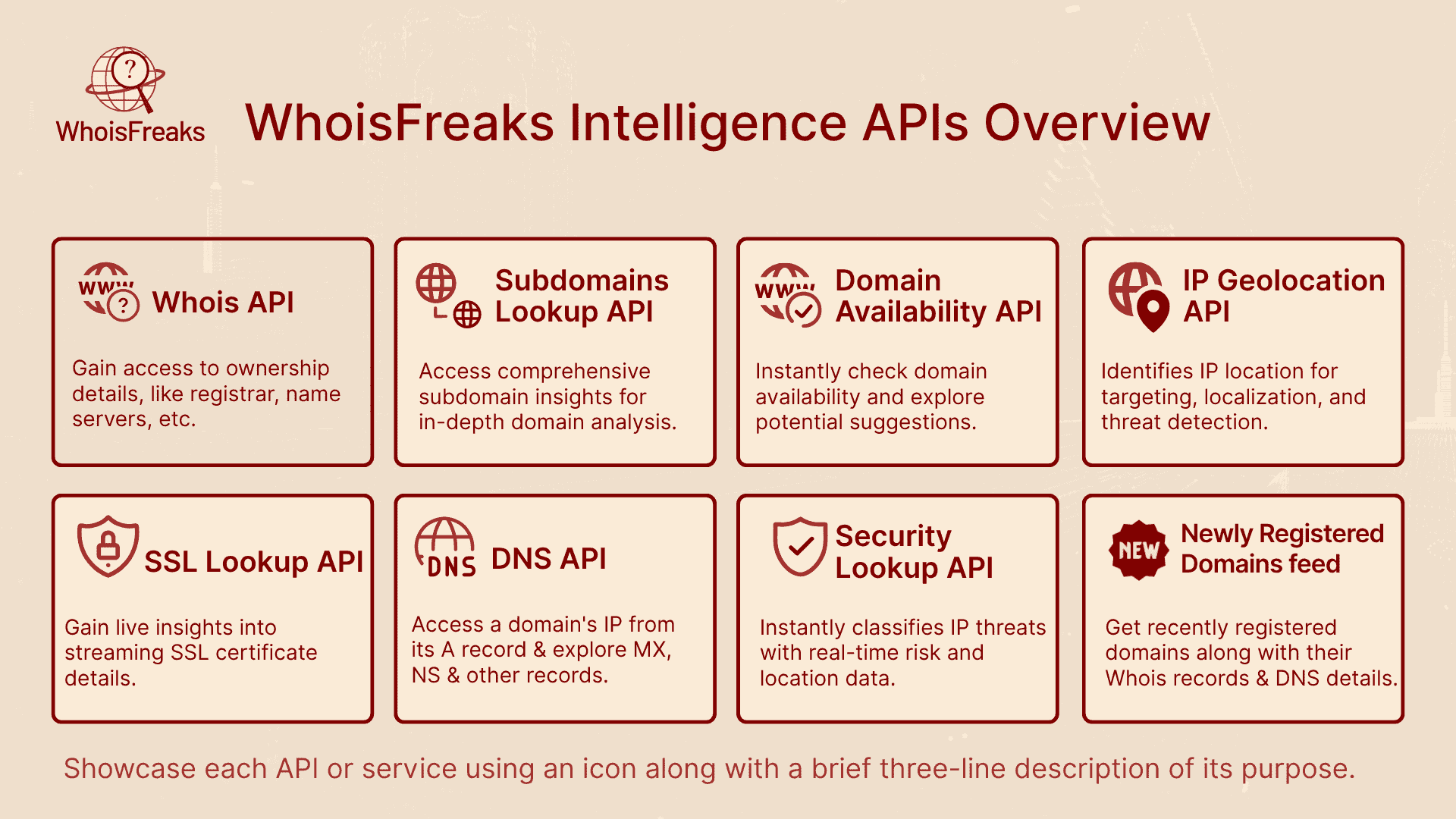
With these tools focused on email security, defenders can automate data collection and detection across the phishing lifecycle. The following sections map each stage of an anti‑phishing solution to specific WhoisFreaks capabilities.
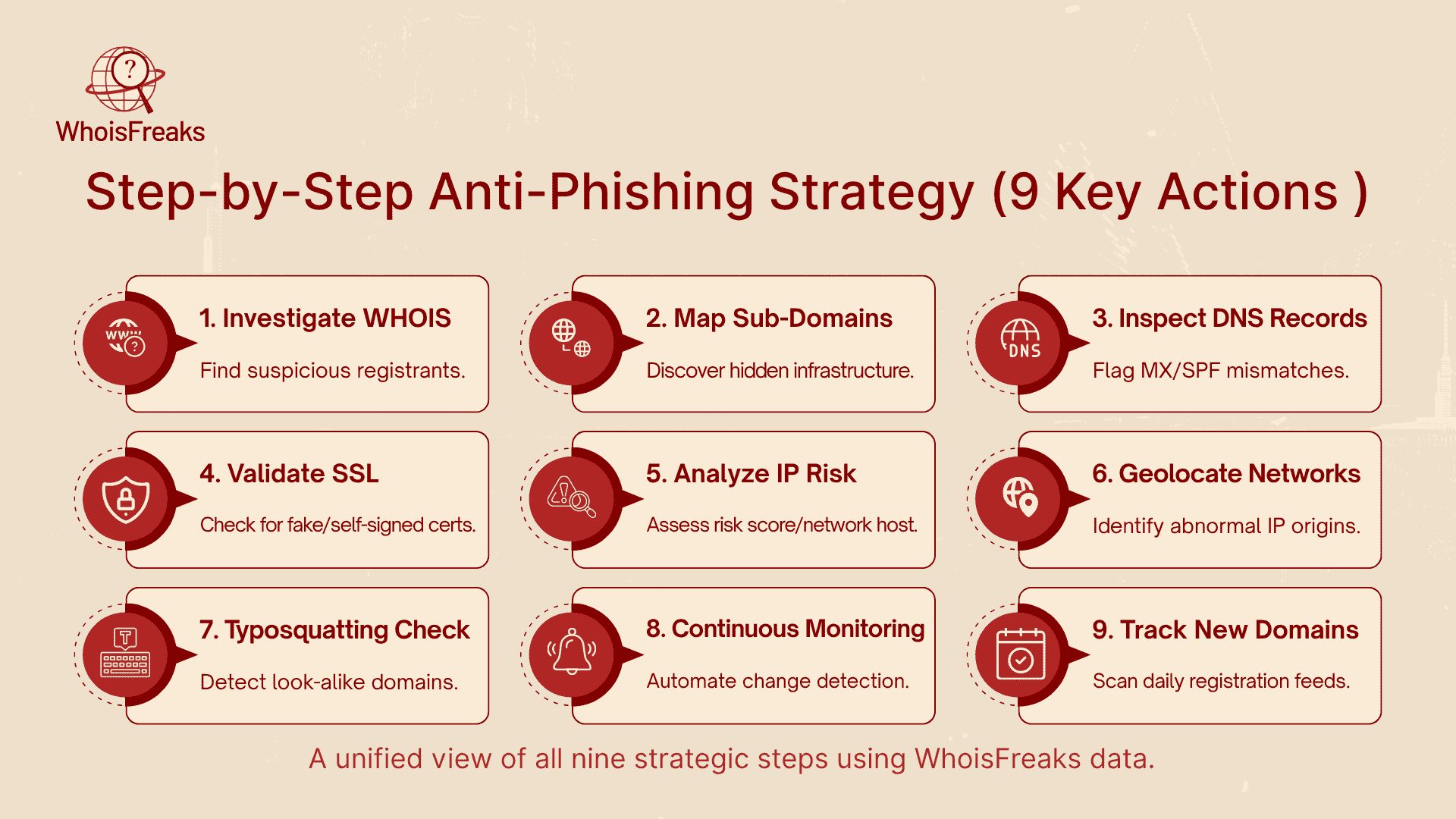
Every anti-phishing process begins by validating suspicious domains found in emails, logs, or alerts. The WHOIS Lookup API from WhoisFreaks helps uncover a domain’s true identity by providing real-time registration data, historical ownership records, and reverse lookups that reveal related domains controlled by the same entity and might be used to reveal personal information.
Example: If your company receives a link to screenshotapi.net, a WHOIS check might show it was registered just yesterday under a privacy proxy an instant red flag signaling a possible phishing attempt.
Phishing actors often create multiple sub-domains to host login pages, fake portals, or malware. Identifying these sub-domains reveals the attacker’s entire infrastructure. The Subdomains Lookup API from WhoisFreaks provides an extensive list of all sub-domains associated with a parent domain, along with their discovery timelines.
Example: A query for screenshotapi.net may uncover login.screenshotapi.net and cdn.screenshotapi.net, both registered recently. Such patterns confirm the existence of a coordinated phishing setup.
DNS misconfigurations often expose fraudulent domains. The DNS Lookup API lets you retrieve and inspect A, MX, SPF, TXT, and CNAME records to ensure they match legitimate configurations.
Example: If the MX record points to an unrelated mail server, or the SPF record is missing, it’s a strong sign that the domain is being used for phishing.
Attackers often use short-term or free SSL certificates to make their fake sites look trustworthy. With the SSL Lookup API, analysts can review complete certificate chains, issuers, and expiry dates to validate a domain’s authenticity.
Example: If login.screenshotapi.net has a 90-day certificate from an unrecognized authority, it likely isn’t the real bank website.
Even if the domain looks legitimate, the IP behind it might not be. The Security Lookup API identifies whether an IP address is linked to risky networks such as VPNs, proxies, Tor nodes, or botnets.
Example: If an IP scores 90/100 in threat rating and belongs to a known proxy network, blocking it can prevent future phishing activity.
The IP Geolocation API gives context to network activity by mapping IP addresses to their physical locations. Geolocation mismatches often expose fraudulent access attempts.
Example: If a user’s account shows multiple failed logins from Eastern Europe while the user resides in the US, geolocation data can confirm suspicious behavior.
Phishers frequently register look-alike domains to deceive users. WhoisFreaks' Domain Availability API helps organizations find and register such typo-variants before criminals can use them to trick users via suspicious emails.
Phishing threats change daily, making continuous monitoring essential. WhoisFreaks offers three key monitoring tools Domain Monitoring, Brand Monitoring, and Registrant Monitoring to help detect risks early.
These tools help you act quickly if a domain is hijacked, if someone registers a similar brand domain, or if known attackers appear in your monitoring results.
Early detection is key to identifying and mitigating interactions with known phishing sites. The Newly Registered Domains Feed provides a daily updated list of new domain registrations worldwide, allowing organizations to identify suspicious names before they’re weaponized.
Example: Searching the feed for domains containing "acmewidgets" can reveal typosquatting attempts, letting your team block or report them immediately.
Phishing is one of the biggest threats to any digital environment. To protect against it, organizations need more than just basic security tools they need accurate domain and IP intelligence.
WhoisFreaks provides complete visibility through its WHOIS Lookup, Reverse WHOIS, Subdomains Lookup, DNS and SSL APIs, IP Geolocation, and Security Intelligence tools. These features help detect fake domains, track suspicious IPs, and monitor brand misuse in real time.
By using WhoisFreaks, security teams can identify phishing threats early, take action faster, and keep their systems safe from online fraud.
Visit WhoisFreaks.com to explore the APIs and start building your own anti-phishing solution today.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Learn how to prevent subdomain takeover with essential strategies and best practices. Protect your online assets—read the full guide now!
8 min read