
WHOIS History as Evidence: Incident Response Use Cases and Chain of Custody Tips

By Qasim
Posted on January 12, 2026 | 10 min read
WHOIS information resembles the domain name directory, with all the differences being who registered a site, when it was registered and who was the registrar. Such information can be stored in the public WHOIS databases and expert systems such as WhoisFreaks archive the records with time. Domain names play a crucial role in cybercrime investigation and digital forensics, as analyzing their WHOIS history can uncover malicious activity and ownership changes. A Historical WHOIS query can provide the whole history of a domain: its creation and expiry dates, previous registrant names and name-server transitions.
One of the first sources of any domain investigation is usually WHOIS. An analysis of WhoisFreaks points out that most internet frauds and scams are conducted using domains registered and even changed by threat actors, indicating that the attacker often forces new domains to carry out phishing and then changes or disregards them. By retrieving the historical WHOIS information about a suspicious domain, detectives will be able to retrace every action made by the adversary, although the domain might have later moved to a privacy service or moved to different ownership. Since WHOIS is an open source, it is regarded as good evidence, yet the most important thing is to write how it has been received and maintained.
Understanding Domain Ownership
Domain ownership is a cornerstone of digital investigations, offering crucial insights into who controls a website and their potential intentions. By examining historical WHOIS data, investigators can verify a domain’s registration history, track ownership changes, and detect signs of malicious activities. WHOIS records typically include important information such as the registration date, registration details, and contact information for the registrant, providing a detailed snapshot of a domain’s background.
However, privacy laws and data redaction practices can sometimes obscure these details, making it challenging to access the full picture of domain ownership. In such cases, specialized tools and techniques become essential for uncovering the necessary data. Historical WHOIS data can help bridge these gaps by revealing previous ownership information and registration changes that may no longer be visible in current WHOIS records.
For digital investigations, understanding domain ownership is key to identifying patterns of abuse, linking domains to specific individuals or organizations, and verifying the legitimacy of a website. By analyzing domain registration history and ownership changes, investigators can uncover connections between domains, spot potential red flags, and gather important information to support legal or regulatory actions. Ultimately, the ability to access and interpret WHOIS data empowers organizations to verify domain ownership, detect malicious activities, and respond effectively to emerging threats.
Incident Response Use Cases
Incident response has numerous uses of historical WHOIS data. It assists the investigators to assign attacks by correlating domains with the threat actors. An example is when two or more malicious domains had identical registrant email addresses or organization names, WHOIS history would show that identical identifiers linked those domains to the same assailant. Cybercriminals often operate various domains with similar registration details, which helps in tracing and analyzing cyberattacks. Another suspicious transfer that is monitored by the analysts is an abrupt change of the domain registrant or registrar: the attacker may have sold the domain to another organization to avoid being tracked. The history of WHOIS will then record the time that transfer occurred and the new registrant.
Historical WHOIS is also useful for threat hunting and proactive defense. If a new attack is detected, analysts might search a known malicious email or name in the Reverse WHOIS tool to uncover the attacker’s entire domain portfolio. Likewise, organizations often use Domain Monitoring to watch their own brand names and related domains. For example, a security team might add all spellings of yourcompany to a monitoring list. If an attacker registers screenshotapi-security[.]com, the monitoring service immediately alerts them, revealing the WHOIS details so they can act quickly. In this way, WHOIS history and monitoring become part of an organization’s "cybersecurity radar."
Key incident response use cases for historical WHOIS include:

- Threat Attribution: Link seemingly unrelated malicious domains by shared WHOIS details. Investigators search past WHOIS records for common registrant emails or names to tie separate incidents to a single actor. This quickly reveals, for example, that three separate phishing URLs were controlled by the same cybercriminal.
- Phishing & Malware Investigations: Map an attacker’s infrastructure. Performing a Reverse WHOIS lookup on an email or name found in a phishing email can reveal all domains that attacker registered. Then a Bulk WHOIS lookup retrieves the registration history for each domain at once. This bulk view often uncovers patterns (same DNS servers, similar registrar names, etc.) that point to the attacker’s network.
- Detecting Evasion Techniques: Spot red flags. Rapid WHOIS changes such as turning on privacy protection, swapping registrars, or frequently updating DNS often indicate malicious evasion tactics. WhoisFreaks' Domain Monitoring alerts can immediately notify teams when such changes occur, even if they happen outside normal business hours.
- Timeline Reconstruction: Build a forensic timeline of the attack. By lining up WHOIS updates with other logs, responders can show the exact sequence of events. Forensic teams rely on these records to demonstrate exactly when each domain was under attacker control.
- Brand Protection: Identify counterfeit or abusive domains. WHOIS history can reveal if a suspicious domain was once owned by your company or a legitimate business. It can also show if those domains later moved to a known criminal registrar, helping you flag scam sites impersonating your brand.
Case Study: Tracking the Kelihos Botnet Infrastructure
The Kelihos botnet was a network of criminal, globally located systems that have been utilized in many years to send voluminous spam as well as distribute malware and collect credentials and money laundering schemes. The law enforcement and security researchers in the United States collaborated to challenge and disrupt it and eventually arrested one of the key operators.
Investigation and Evidence
Kelihos was not a single server, but rather a peer-to-peer (p2p) botnet with tens of thousands of infected computers and dozens of command-and-control (C2) nodes all over the world. The domain intelligence and WHOIS records among other data sources (network traffic, email analysis etc.) allowed the investigators to determine the most important elements of the botnet infrastructure and associate them with the criminal actors.
Although the police do not often release comprehensive technical specifications of all their investigation methods, as evidenced by publicly accessible court records and cybersecurity audits, domain data, IP addresses and registration information are being used by the analysis to:
- Identify malicious command‑and‑control domains and patterns of usage.
- Link those domains to email addresses, IP addresses or alias identities connected to the operators.
- Correlate multiple domains or subdomains used by the botnet to a common actor.
- Support legal processes that result in warrants, seizures and arrests.
This form of evidence gathering is accurate since the history of registration of domains (via WHOIS) can reveal the way malicious infrastructure is established and evolves with time. E.g. Correlating frequent registration emails, or similar names of registrants across multiple domains can assist the investigator to draw a full picture of how the infrastructure of an attacker changed, and how various infrastructure items are connected to the same criminal activity.
Outcome
Combining WHOIS history with network intelligence and legal authority, law enforcement succeeded in:
- Disrupting Kelihos' network operations by redirecting malicious domains and isolating infected machines.
- Arresting a key botnet operator, who was extradited to the United States to face charges related to running the criminal network.
The Kelihos case highlights how historical domain data and evidence tracing are essential tools in modern cybercrime investigations. WHOIS history forms part of the cyber trail that connects malicious domains to threat actors even when attackers attempt to hide behind proxies or rapidly change infrastructure.
WhoisFreaks Tools for Evidence Gathering
WhoisFreaks provides a suite of tools to automate each step of WHOIS-based investigation:

- Historical WHOIS Lookup: Retrieves the archived WHOIS records for any domain. It provides a full history of past registrants, registrar transfers, contact changes, and DNS updates. Analysts use it to see who owned the domain at each point in time and what its settings were.
- Reverse WHOIS Lookup: Searches by email address, registrant name, or organization to find all domains that have ever used that information. This automatically links multiple malicious domain names to the same attacker if they reused an email or name.
- Bulk WHOIS Lookup: Lets you upload a list of domain names (via CSV or text file) and retrieve their WHOIS data in one batch. Web administrators can monitor multiple websites or domain names through a single account, making the account essential for managing and analyzing website data. This is invaluable when dealing with large phishing campaigns or botnets: instead of querying each domain manually, you get a combined CSV file of all registration details.
- Domain Monitoring Service: Continuously watches specified domain names and sends instant alerts whenever their WHOIS records change (registrant, registrar, expiry date, privacy status, etc.). This ensures analysts immediately notice any suspicious updates, such as an attacker switching the domain to a new registrar or enabling WHOIS privacy protection.
These tools can be integrated into existing systems and applications via API calls. The WHOIS history database is continuously updated with the latest registration occurrences, ensuring analysts have access to the most current data. WHOIS history tools can also help in market research by providing information about domain names related to competitors and customers.
Chain of Custody Best Practices
Chain of custody is used in forensic studies, and it is the record of the way evidence was used, by whom, when, and where it was passed on or analyzed. In the case of digital evidence such as WHOIS data it would imply that there is a clear audit trail between the time data is gathered and when it is presented. To make sure that the WHOIS findings are accurate and admissible, the following best practices should be followed:
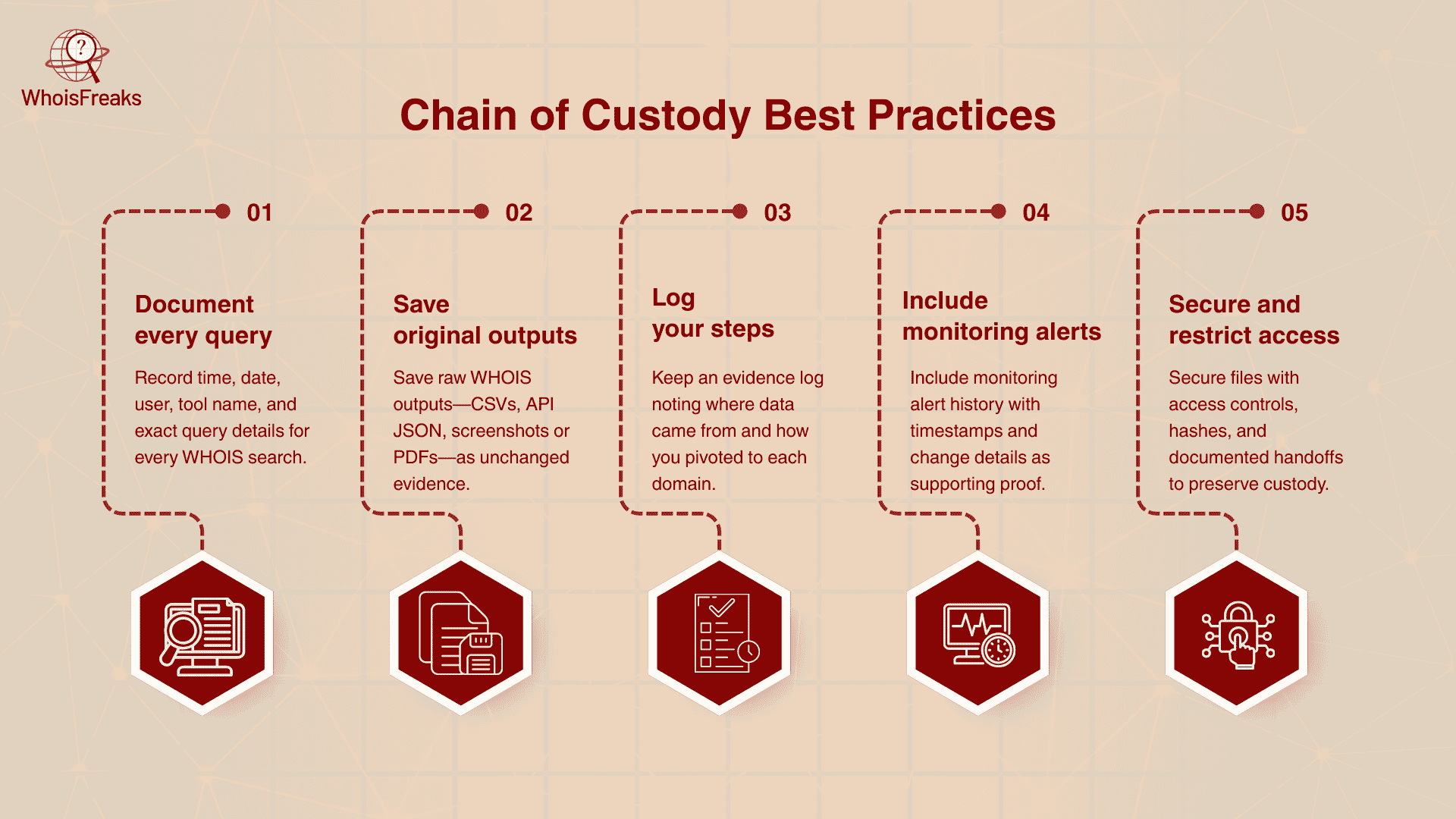
- Document every query: Enter the time and date and user of every WHOIS search or WHOIS export. Provide the name of precisely which tool and query was being used (e.g. record the CSV name or API query details). WHOIS entries contain timestamps so ensure that your notes have been synchronized with the time.
- Save original outputs: It is always good to have the raw WHOIS data files. As an example, download a CSV of Bulk WHOIS, store any response of a JSON/API request, or take screenshots/ PDF of lookups. Such unmodified files are your main evidence and you might be required to provide them in audits.
- Log your steps: Keep an independent evidence log of the way and the place that the data was collected. When using API, store the response and request IDs. In web lookups, retain any confirmation email or support tickets containing the WHOIS data. This log must describe the way that you found yourself in the next domain.
- Include monitoring alerts: In case you used Domain Monitoring, add the history of its alerts in your report. The alerts are also time-stamped and display the details of the change (e.g. registrant changed to B on date X) which are additional evidence in events.
- Secure and restrict access: All data and notes collected by the WHOIS shall be stored in a secure setting that is controlled by access (encrypted storage or official evidence repository). Checksum hashes or digital signatures of files are used to demonstrate that they were not changed. To ensure the integrity of evidence whenever evidence is passed to another analyst, follow formal chain-of-custody protocols (e.g. record every handoff) to verify integrity.
The steps above will make sure the evidence of the WHOIS is reliable. An audit trail will record every single step of the data collection process, through to analysis, which can be shown to illustrate how that specific piece of data was acquired.
Conclusion
Historical WHOIS data is not merely the information it is the digital fingerprint of the domain activity. Using such tools as the Historical WHOIS, Reverse WHOIS, Bulk Lookup, and Domain Monitoring of WhoisFreaks, cybersecurity teams can:
- Trace attackers via pattern of domain registration.
- Rebuild schedule on phishing, malware or hijacking attacks.
- Gather and conserve court ready evidence.
- Track important areas of suspicious activity in real time.
This data is credible, dependable and legally justifiable, as proper documentation and chain of custody practices are observed. Through incorporating the WhoisFreaks into your incident response process, you have a clear-cut edge of detecting threats ahead of time and responding promptly.
Call to Action: Start protecting your organization today. Visit WhoisFreaks.com and explore their Historical WHOIS and Domain Monitoring tools to uncover hidden threats, track malicious domains, and strengthen your cybersecurity defenses. Every suspicious domain tells a story make sure you can read it before it’s too late.
FAQs
1. What is the chain of custody in incident response?
2 .What are some situations that may require chain of custody documentation?
3. How to check domain owner history?
4. What are the key steps in chain of custody?
Related Posts

Forensic Analysis Uncovering Cybercrime with WHOIS History Insights
Explore how WHOIS history aids forensic analysis in cybercrime investigations. Learn effective strategies to enhance your cyber defense. Read more now!
9 min read

Phishing Prevention Using Subdomain Discovery to Thwart Spoofing Campaigns
Learn how subdomain discovery can enhance phishing prevention and protect against spoofing campaigns. Read the article for practical strategies.
12 min read