

By Qasim
Posted on September 04, 2025 | 12 min read
Cyber threats are increasing at a rapid pace and there are clever tricks being used in the daily breach of systems, theft of data, or to disrupt the services, which demonstrate the nature of evolving cyber threats. A good tool of preventing these menaces through proactive threat detection as they happen before they can bring chaos is through one thing referred to as IP Intelligence.
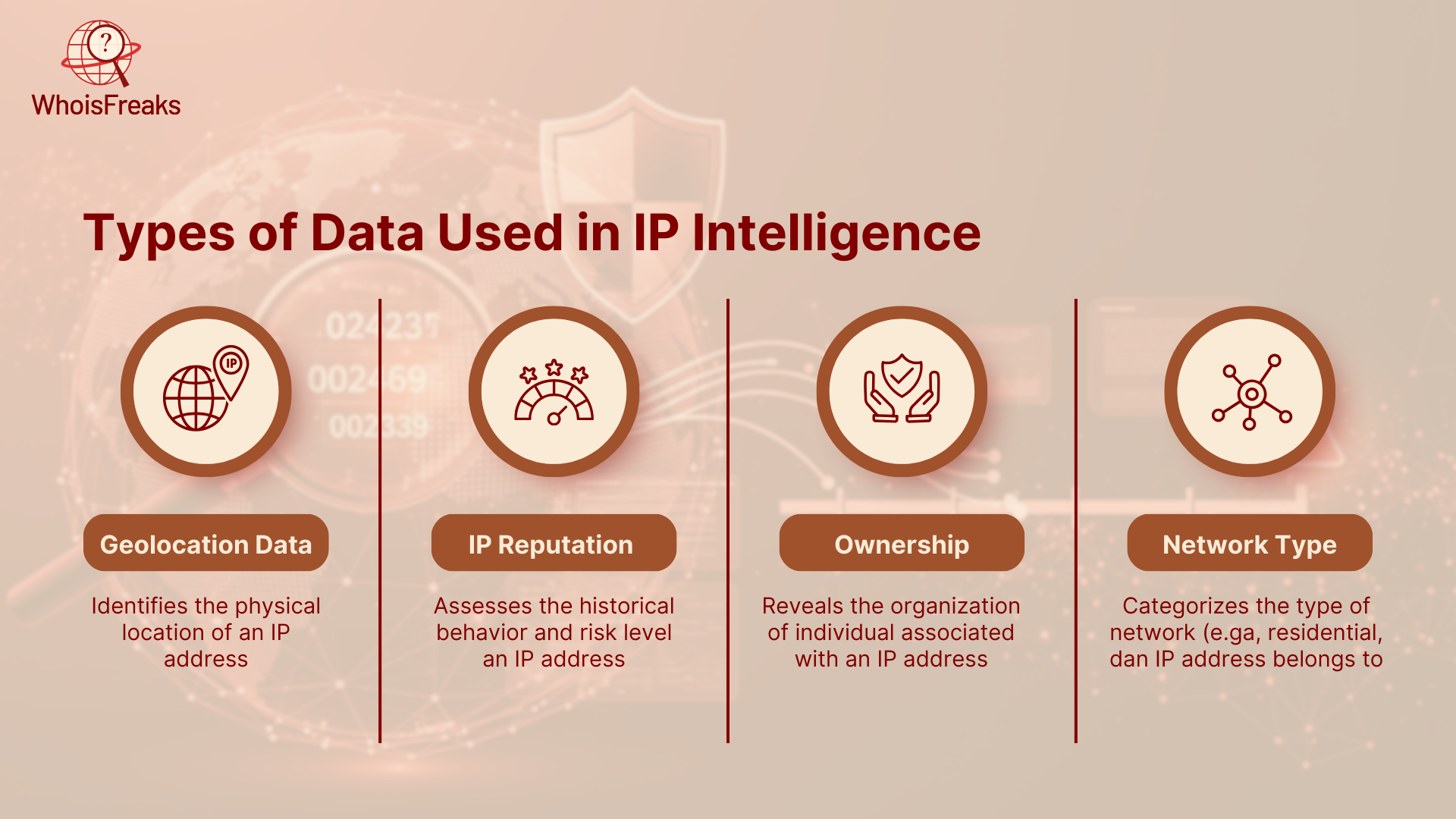
The IP Intelligence refers to gathering actionable intelligence by categorizing information regarding IP addresses, the original numbers that each internet-connected device possesses. Through this information, one can determine the location of an IP, who owns it, the network it uses, and whether it has been used to undertake malicious actions such as hacking or spamming before.
With the IP Intelligence, companies and cybersecurity teams will be able to improve their overall security posture by detecting threats much earlier before they result in any form of damage. To use an example, when a login request transpires based on an IP address that has already been flagged as an attacker, the system can halt it instantly.
Whether you’re a security analyst, a business owner, or someone interested in protecting your data, understanding IP Intelligence can give you a big advantage in staying safe online.
No matter what device is connected to the internet, whether the computer, phone, server, or any smart device, an IP address is assigned. It is just like an online address which tells where that device is on the internet. IP Intelligence refers to the job of gathering and interpreting the raw data on these IP addresses to determine the level of trustworthiness or riskiness of the aforementioned.

IP Intelligence is not about the simple location of an IP. It can tell you answers to such questions as:
The information can be of high use in cybersecurity, particularly when determining the possible threat actors. It allows security teams to consider trusting some IPs, or block them, particularly when things are undertaken such as at log in, on-line shopping or when a person gains access to sensitive systems.
There are many tools offered by WhoisFreaks that can help you gather many types of useful IP data, such as:
Cybercriminals often leave behind one key clue during their attacks their IP address. Even if they try to hide it using tricks like VPNs or proxies, smart tools can still help track and analyze their digital footprints. Let’s explore some common types of cyber threats where IP Intelligence, a crucial part of cyber threat intelligence, plays a major role.
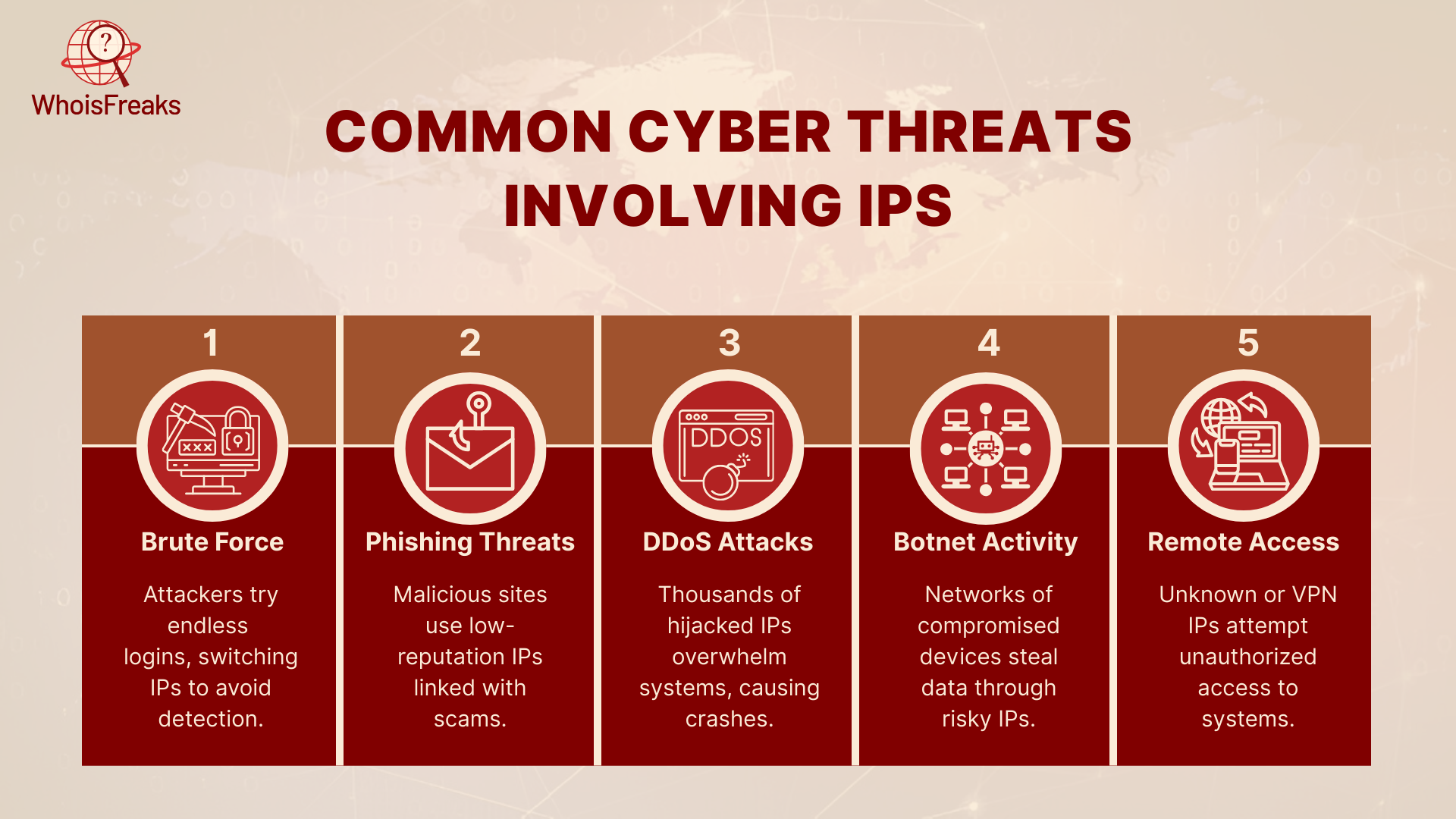
Under brute force attacks, malicious users attempt numerous username and password combinations to crack into an account. They tend to use scripts and change the IP addresses in order not to get noticed. IP Intelligence can also allow easy detection and blocking of suspicious IPs who might log in more than once and fail.
The phishing sites are usually set up in servers that have low-reputation or newly registered IP addresses. Such IPs are also related to prior scams, spam or phony mails.
Through IP WHOIS Lookup you can get the history of the IP and thus be able to confirm whether the IP has been used to carry out phishing or the IP is part of a suspicious network. This assists in the elimination of bogus sites or rather blocking of unsafe mails.
When your system is flooded with traffic by thousands of incoming devices in a DDoS attack, it can either get crashed or become slow. Such attacks are typically initiated by numerous IPs usually by hijacked devices or botnets.
You can group IP by region or ISP using IP Geolocation API to filter a suspect traffic. The IP Security Lookup can be used too to automatically block all IPs which participated in earlier attacks.
Botnets may be defined as networks of compromised devices, and attackers control them. They do such activities as stealing data or scanning weak places on other systems. You can prevent their access by following their IP activity and knowing risky or known bot IPs.
Sometimes, even trusted systems are accessed from unknown IPs. This can be a remote hacker or even an insider threat using a VPN.
IP Intelligence lets you catch this by alerting when access comes from an IP that:
Using this insight, security teams can require extra verification or block access entirely.
It is easier to prevent a threat the earlier you notice it. This is why the early identification of the threats is one of the most significant elements of the effective cybersecurity strategy, as it gives the incident response teams enough time to respond. IP Intelligence will help organizations to identify warning signs in the event of an attack before it occurs. Systems can determine that a bad packet is received by looking at the IP origin behind the incoming connection and act accordingly before damage is made.
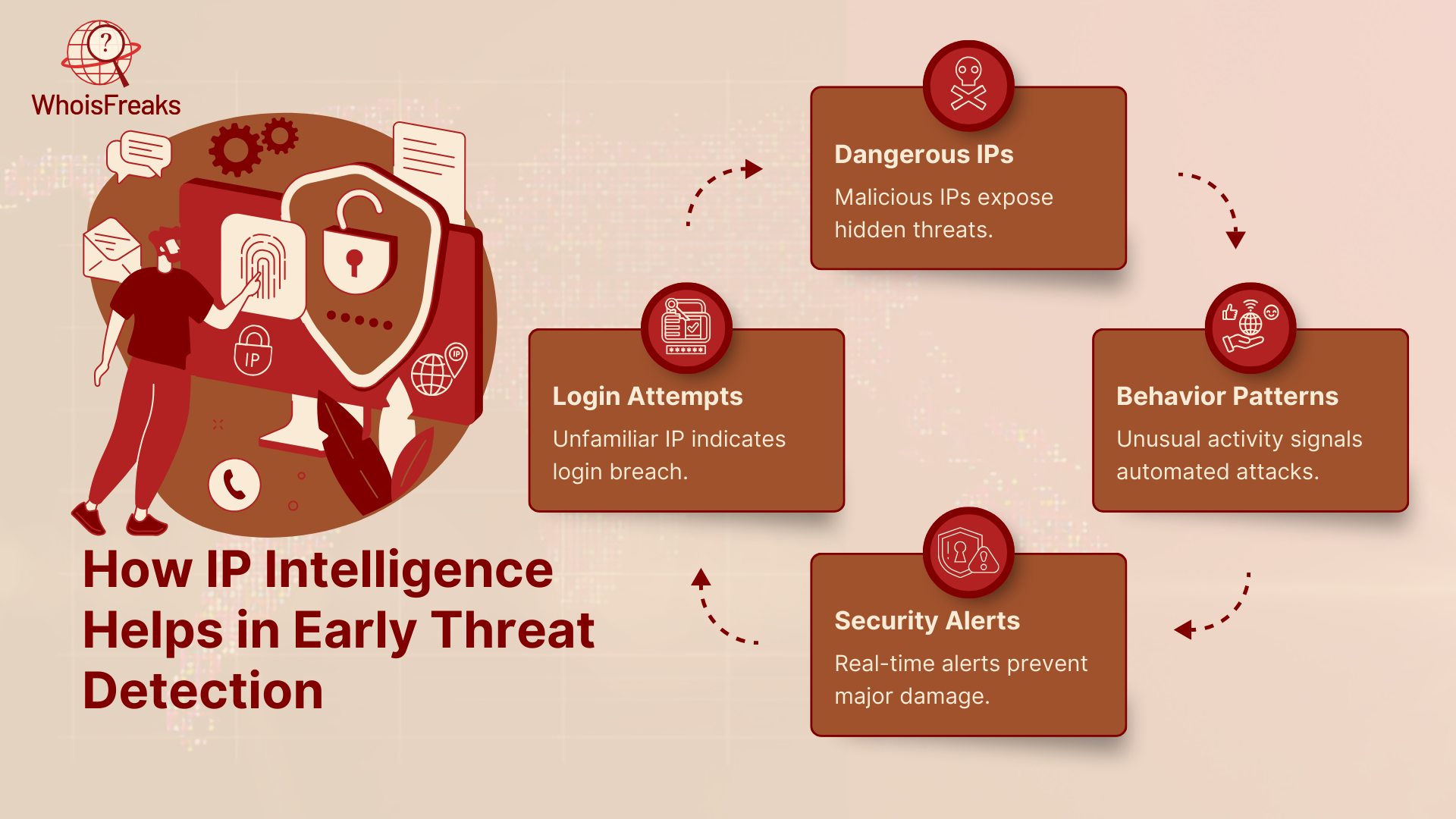
An unfamiliar IP address of login is one of the earliest indicators of the potential breach, particularly when the IP address belongs to another nation or a recognized VPN. Imagine a user who is known to log in most of the time in Pakistan and wakes up one morning to see an Eastern European trying to log in at 2 AM trying to get access.
With the help of IP Geolocation API, you will know the location of the IP and its network immediately. Unless it is consistent with the common behavior of its user, your system can automatically prevent the log in or activate the multi-factor authentication to provide additional security.
There are some IPs that are already known to be harmful. They could have been part of phishing, spam, brute force as well as botnets. Its appearance in your traffic is a good indicator to identify potentially malicious activity and a possible source of security threat when this kind of IP appears in your traffic.
Using the WhoisFreaks IP Security Lookup tool you will have the ability to look up an IP history and risk score. In case it is in the list of dangerous or related to known threats, your system can instantly prevent its communication on the network and interfere with the attack before it occurs.
The one-time log in is not the only thing one should care about. It is the suspicious patterns that are usually more suggestive. As an example, when an IP attempts to connect to many systems within a short period, or a user sends multiple login attempts, or acts unusually, then it can be a sign of an automated attack, a reason why incident response processes and technical threat intelligence are needed.
A combination of IP Security Lookup, Geolocation, and IP WHOIS Lookup allows creating a profile of each IP and tracking its activities. In case of any anomaly such as linkage with unsuspected areas or familiar proxy networks your system can trigger an alert.
What matters the most is the speed at which you prevent threats. The farther a dangerous IP is identified, the more harm it can do- which is why sound security is a necessity. This is the reason why real-time alerts would be crucial.
Using WhoisFreaks tools, you can establish a system of automatic notifications in case there is suspicious IP. You can pass these warning messages on to your security staff, you can log them on your systems or even act on them by taking a defensive measure like blocking access or isolating the infected systems.
Threat mitigation is the process of reducing or preventing the attack once the attack has been identified. Truth be told, it is not about early identification but about the speed at which you can respond. An important part of it is an IP Intelligence working towards assisting organizations in leveraging operational threat intelligence to respond swiftly and defend themselves.

When system blocks an IP address, it turns out to be suspicious either in terms of reputation or those the IP addresses are involved in cyberattacks. This will ensure that unauthorized access is mitigated even before actual damage can be inflicted. Using solid IP information, the systems are capable of identifying and blocking known malicious connections instantly.
Cyber threats usually emanate in certain areas or networks. In case your organization is not serving users in those places, exposure can be limited by installing filters to block traffic. The filter will not only keep threats at bay, location-based filtering will also assist you in targeting your resources on users which are important to your business.
The IP addresses that display abnormal activities do not all require complete blocking. Others may just need more extra efforts such as multi-factor verification, or human review. If a user signs in with a different IP address or a connection is made using a masking service such as a VPN, your system will adapt to such a change.
The IP addresses that display abnormal activities do not all require complete blocking. Others may just need more extra efforts such as multi-factor verification, or human review. If a user signs in with a different IP address or a connection is made using a masking service such as a VPN, your system will adapt to such a change.
IP Intelligence is a powerful cybersecurity tool that analyzes the behavior, source, and reputation of IP addresses. It helps organizations block risky connections while ensuring trusted traffic flows smoothly.
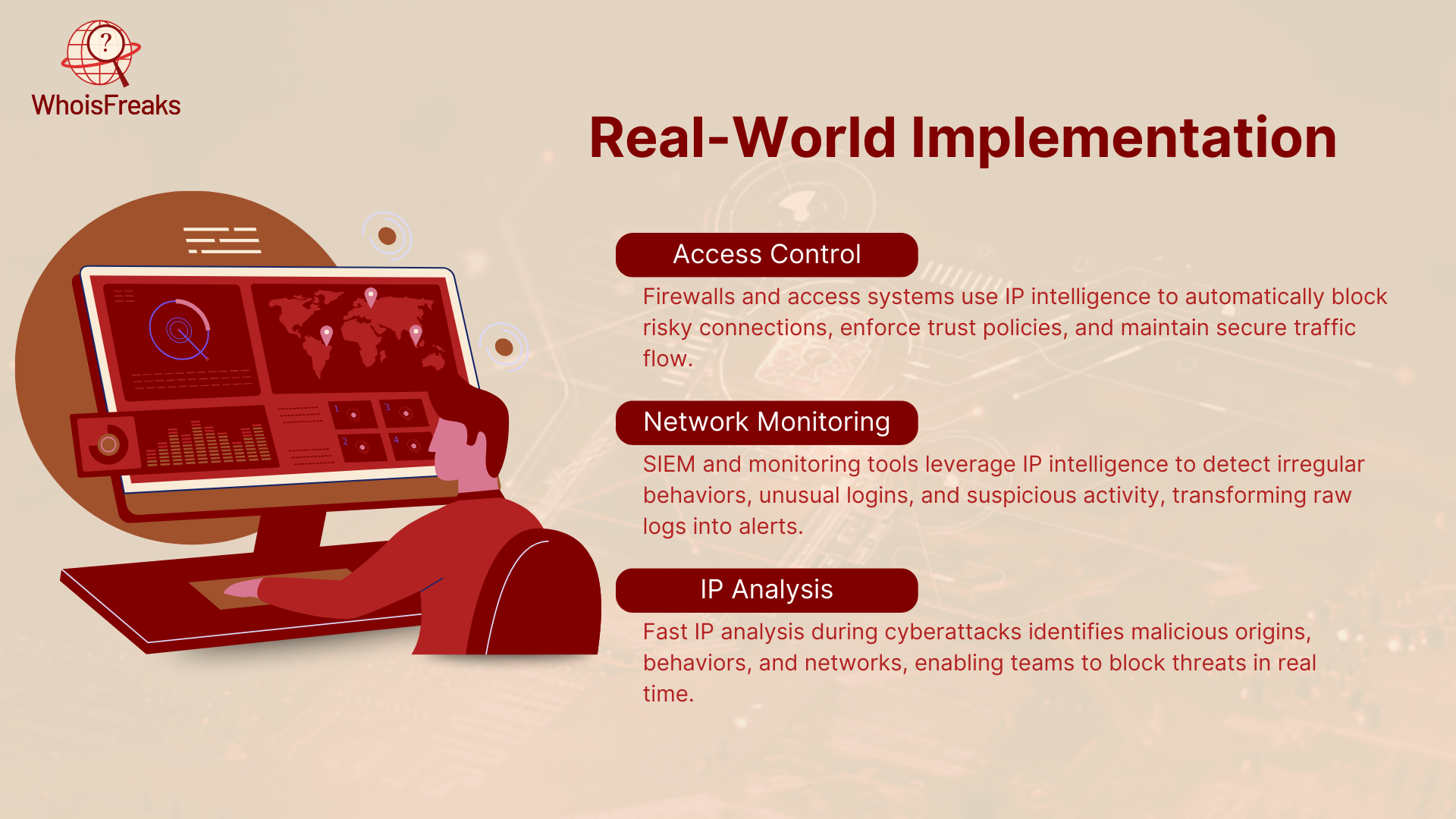
IP Intelligence is really an effective threat intelligence mechanism and practical cybersecurity used within organizations of all varieties. It enhances systems due to an increment of a filter of intelligent decision-making on the basis of behavior, source, and reputation of IP addresses. IP data can be used in firewall and access control systems to automatically block risky connections, adjust traffic on the basis of how or where the traffic is trusted, and keep normal traffic moving without slowing.
IP intelligence also forms a major aspect in network monitoring and analysis. It can be applied to tools, such as SIEM platforms, to assist security teams to detect irregular behaviors, such as logins to unapproved countries or large spikes in unknown access. Such enriched data allows transforming raw traffic logs into significant alerts, which can assist teams to concentrate on the actual threat rather than filtering through noise.
Fast IP analysis is important especially in instances when a cyberattack is already in action like in the case of DDoS attack or botnet connection. Teams can easily identify and block the threat by looking at where the traffic originated, how it has acted, and which networks it is associated with by looking at the traffic path.
When it comes to collecting, analyzing, and acting on IP data, WhoisFreaks offers a complete set of tools designed to support security teams, developers, and businesses. These tools help in both early threat detection and fast mitigation of critical threats, integrating seamlessly with threat intelligence platforms making IP Intelligence much easier and more reliable.
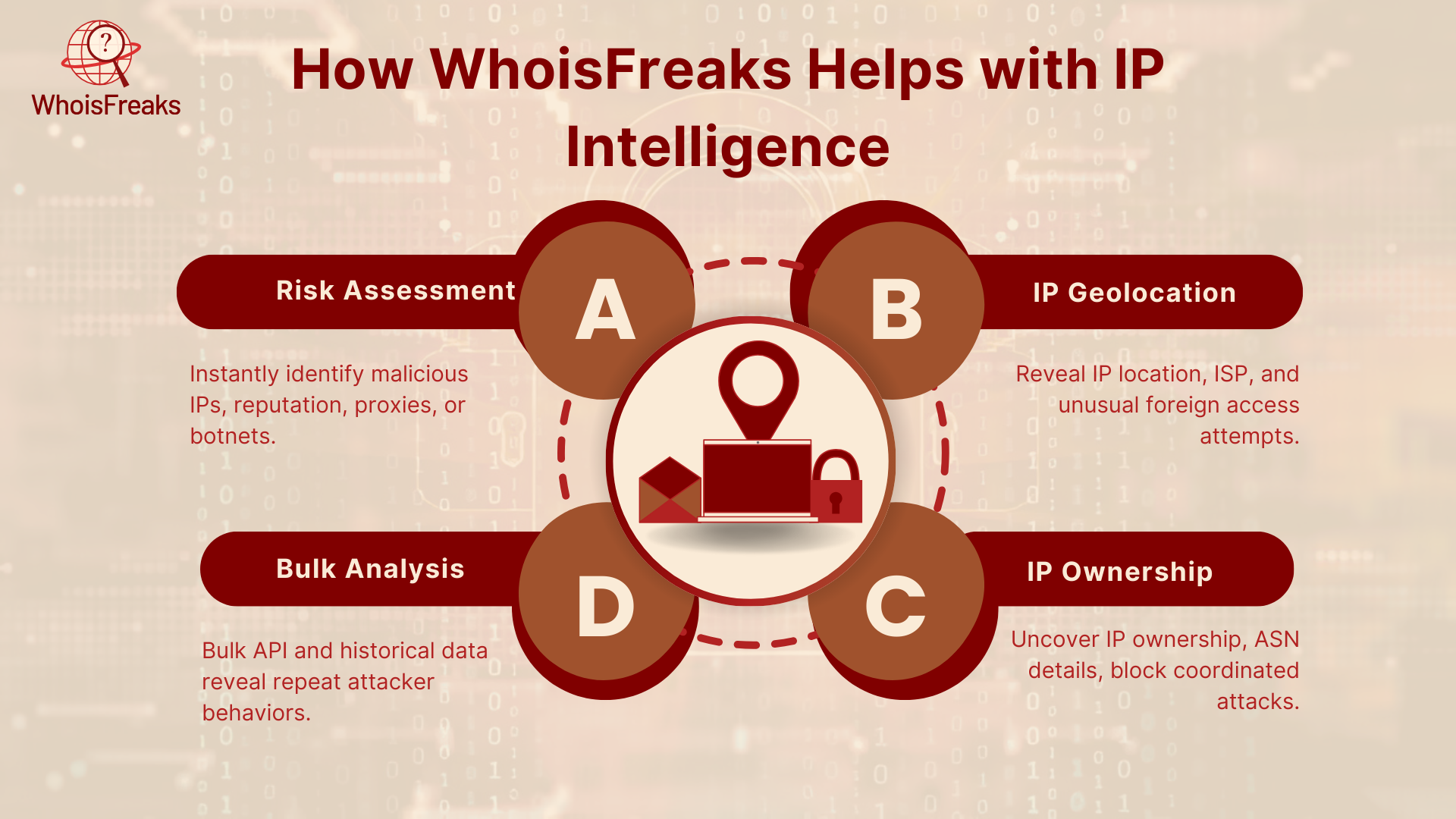
Let’s explore how WhoisFreaks specifically supports each part of the IP Intelligence process.
The IP Security Lookup API is one of WhoisFreaks' most powerful tools for security. It lets you check any IP address and instantly see:
This helps you make quick and automated decisions such as blocking a login attempt or alerting your team based on solid threat data.
Knowing where an IP is coming from helps detect unusual or suspicious behavior. The IP Geolocation API provides:
This makes it easy to spot risky logins from foreign locations or unusual access patterns. You can also use this data to build geo-filters or detect DDoS hotspots.
Sometimes you need to know who owns an IP address, or what network it belongs to. That’s where the IP WHOIS API and ASN Lookup API come in.
This is especially helpful when you're investigating larger threats like botnets or coordinated attacks.
For security teams that need to analyze large volumes of data or conduct deep research, WhoisFreaks provides:
This helps in threat hunting, forensics, and even identifying repeat attackers who change IPs or domains.
Cyber threats are on the rise, and they are more sophisticated. However, using the appropriate tools and strategies, we can be ahead of these risks. The best manner of achieving this is by doing IP Intelligence to mitigate cyber threats. This is defined as the process of knowing who is at the other end of an IP address, where are they located and is it safe to open their address or not.
This blog provided an overview of how IP Intelligence can be used and the benefits of doing so and also demonstrated that it can provide actionable insights to identify as well as prevent cyberattacks. We also demonstrated how WhoisFreaks has got all that you require in IP reputation scores and geolocation data, ownership data and indefatigable APIs in order to develop a sharp security network.
If you're looking for a reliable, easy-to-use, and powerful IP intelligence solution, WhoisFreaks is a great place to start. Whether you're a security analyst, IT manager, or developer, their tools help you protect your digital assets and take action with confidence.

Discover how IP domain intelligence enhances your brute force defense strategies. Strengthen your cybersecurity—read the article now for practical insights.
11 min read

Discover the fundamentals of IP geolocation and its vital role in enhancing security. Learn practical applications and best practices in our latest article.
11 min read