

By Qasim
Posted on August 22, 2025 | 11 min read
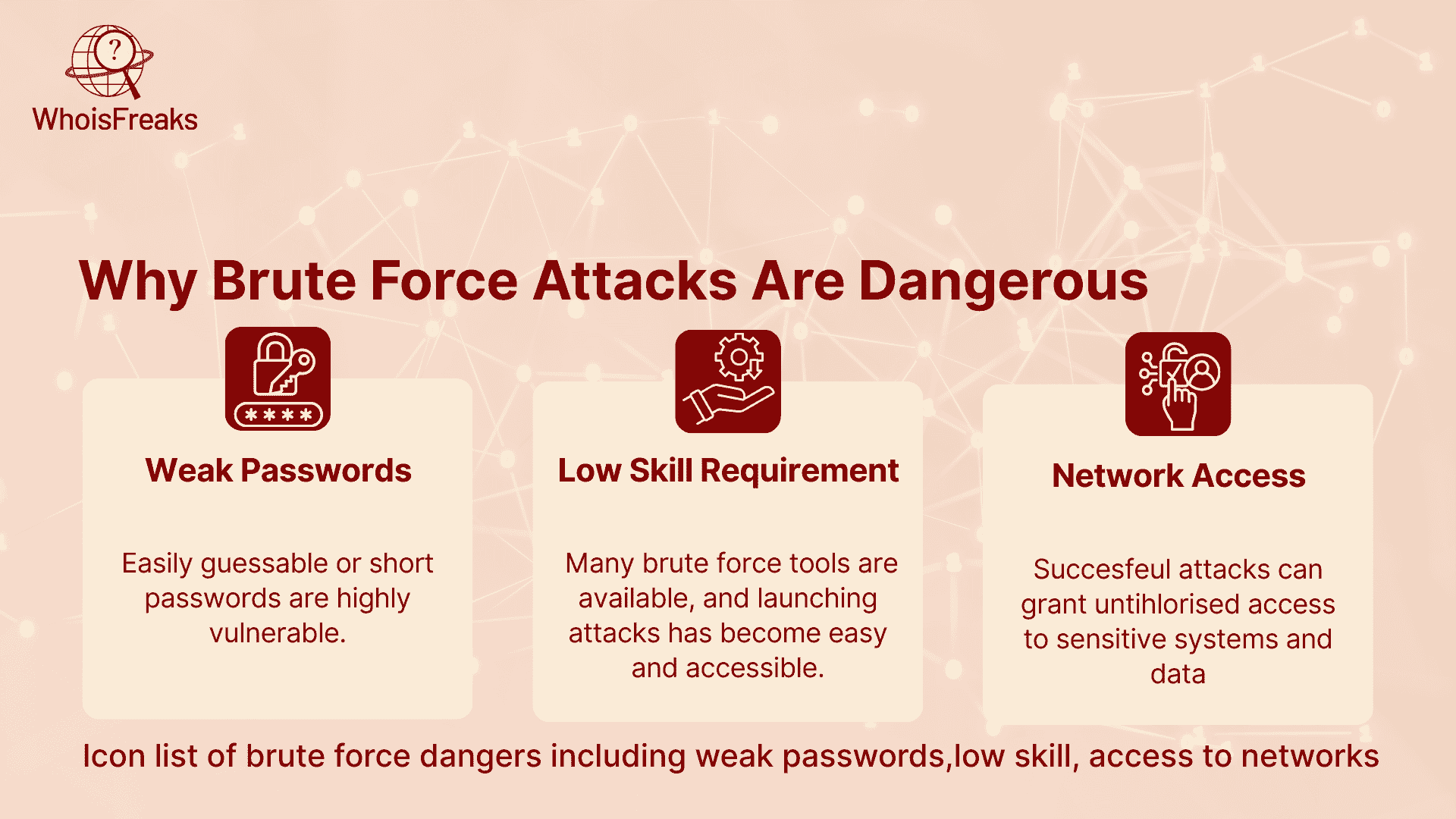
One of the most popular hacking instruments is the Brute force attacks and probably one of the oldest methods of hacking activities used by cyber criminals, including simple brute force attacks. They do so by automatically trying password combinations potentially thousands of times a minute till they get the correct one. Nevertheless, the brute force attacks remain efficient even though simple in nature, when the systems possess vulnerabilities in terms of weak passwords or absence of defensive mechanisms.
Strong passwords and limitation of logins, especially when users rely on the same password, might not suffice to stop such attacks which are increasingly becoming automated and targeted. that is where IP and domain intelligence plays its part.
By analyzing the source of failed login attempts such as the IP address or domain used, organizations can detect suspicious behavior early, identify known bad actors, and stop brute force attempts before they succeed.
In this blog, we’ll break down how brute force attacks work, the different types of these attacks, and how tools like IP geolocation and domain data can be used to build a stronger, smarter defense strategy.
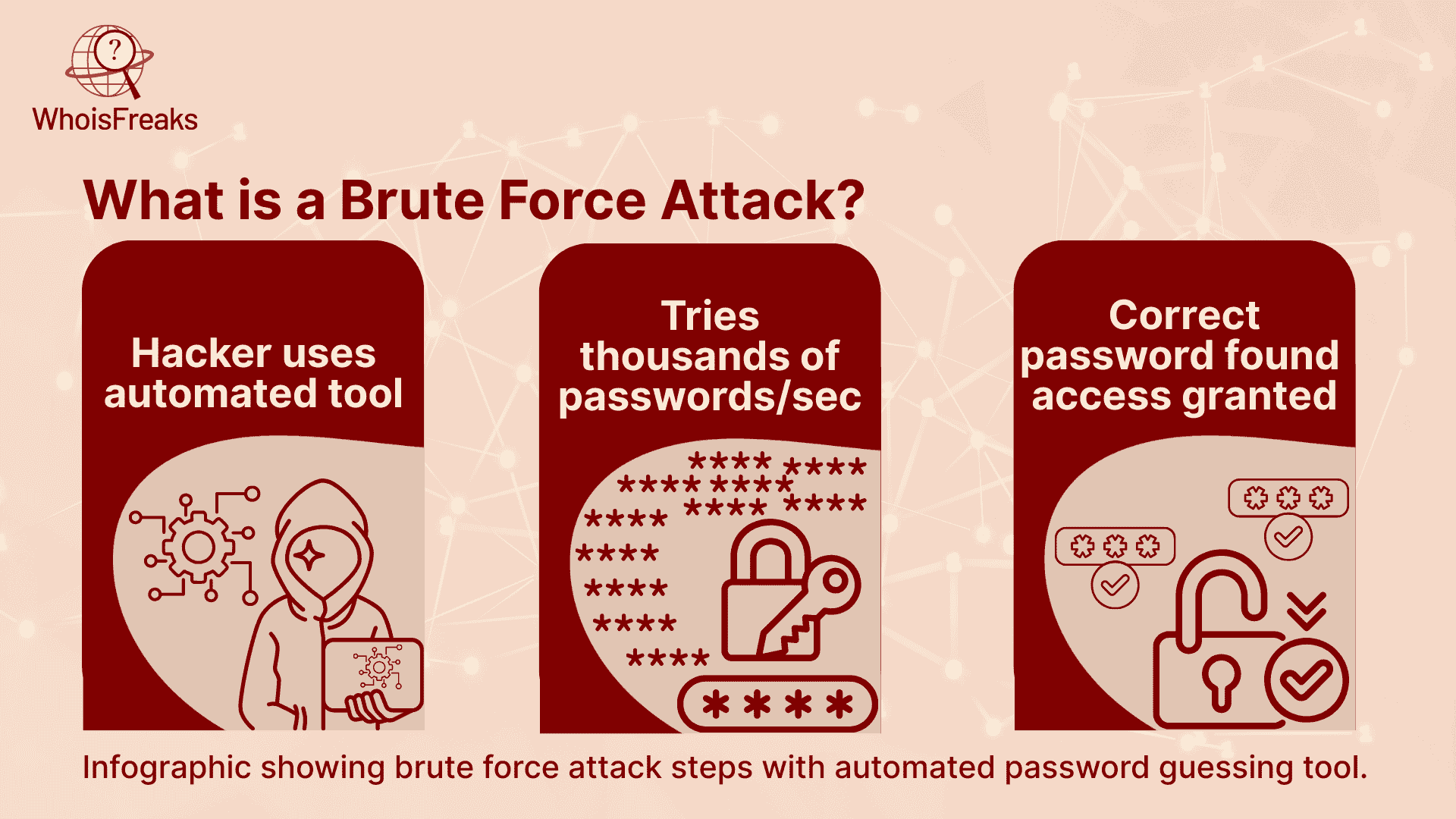
Brute force attack is one of the methods employed by hackers to crack passwords and gain full access into the account or system by attaching all the possible combinations of passwords until the right one is discovered. It is simply a matter of trial and error using all the keys on a keyring until you finally get a key that unlocks the lock.
The hackers normally undertake these attacks with automated tools that can find thousands or even more chances of a password combination in a very short period.
Although brute force attacks are quite straightforward, they are very successful when no precautions have been taken. This is the reason why the knowledge of their mechanism of action is the initial protection against them.
Brute force attacks are of many varieties. There is a possibility that threat actors may select one depending on their mode of execution and the target to be attacked. So, some typical varieties of brute force attacks look as follows:
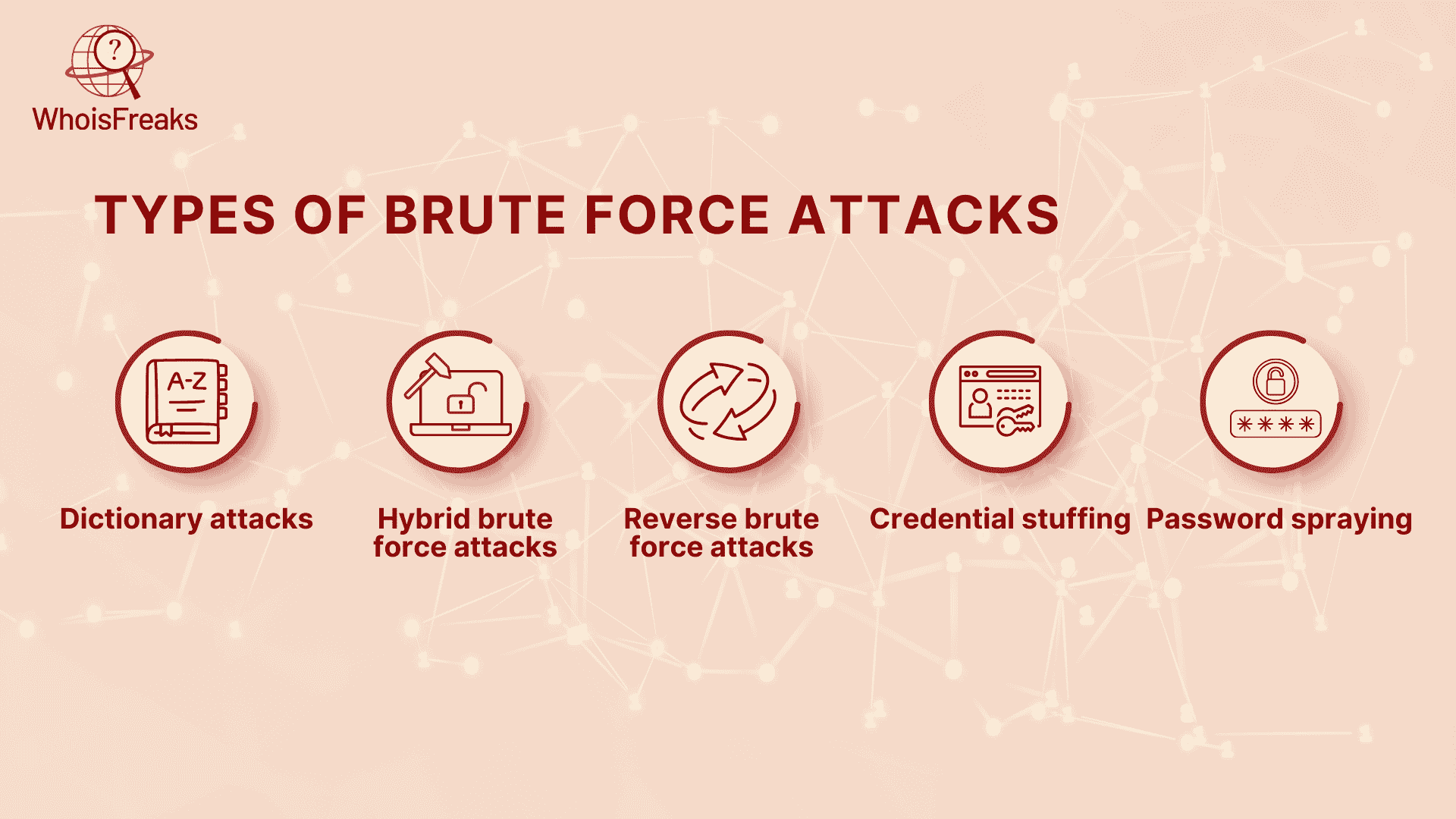
A dictionary attack characterizes an attempt to enter various possible passwords in a sequence with the use of a pre-selected collection of words, often a dictionary, against a username. The attacker shall have a program, which shall be making different combinations of words and phrases to ultimately get the right password. Attackers can also supplement the words with numbers and special characters to make them their passwords, aside from using unabridged dictionaries or special ones. Further, attackers are also in a position to exploit details of previously leaked passwords to make dictionary attacks.
Dictionary attacks are feasible since most people use passwords which are just words or phrases. These types of passwords can be guessed by the program of attacker with ease.
Hybrid brute force attack is a new way of combining a dictionary attack and a brute force attack. In a hybrid attack, the attacker will do a combination of using a set of random characters as he would do in a typical brute force attack and running a program to attempt a list of common work and phrases as in a dictionary attack.
A combination of the two techniques can succeed in creating a hybrid attack with more success compared to the one done using a dictionary or ordinary brute force attack. This is because it will enable the attacker to work with both familiar and less familiar password choices.
In normal BF attack, the attackers are not aware of the password which they are guessing. A reverse BF attack as the name depicts works in reverse. In another instance, say the attacker has the PIN or the password he is seeking, he will search through millions of usernames to get the corresponding username.
In this method, the attackers normally access the passwords that have previously been leaked by prior data breaches, and they access it online. The attack can also be automated in order to be fast.
The same credentials can be used by many users on several user accounts. Credential stuffing: Re-use of a stolen list of usernames and passwords to use in unauthorized access of other accounts. The hackers can automatically test such stolen login credentials using bots on different websites. When they succeed, they would have a chance to obtain confidential personal and financial data.
Beware: these attacks can go undetected hackers are using legitimate login credentials.
The credential stuffing attacks are also harmful when the attackers carry malicious acts in a long term without the knowledge and understanding of the user. There can be major damage that the user could not repair easily by the time he has noticed it.
Password spraying is the usage of a common password on excessive accounts. In this case, the malicious user first attempts some used passwords on a large number of accounts instead of attempting all the possible characters combination. The success of password sprays lies in the fact that lots of individuals share passwords across their accounts. They give access to attackers to numerous accounts with comparatively little effort as they simply attempt a few predictable passwords with numerous accounts
This method also allows the attackers to get out of lockout policies which limit the number of password attempts. This kind of attack is usually directed to single sign-on (SSO) and cloud-based applications that implement federated authentication.
Cybercriminals don’t run brute force attacks just for fun they’re after something valuable. Understanding their motives can help you design smarter defenses and prioritize what needs protection against successful brute force attacks .
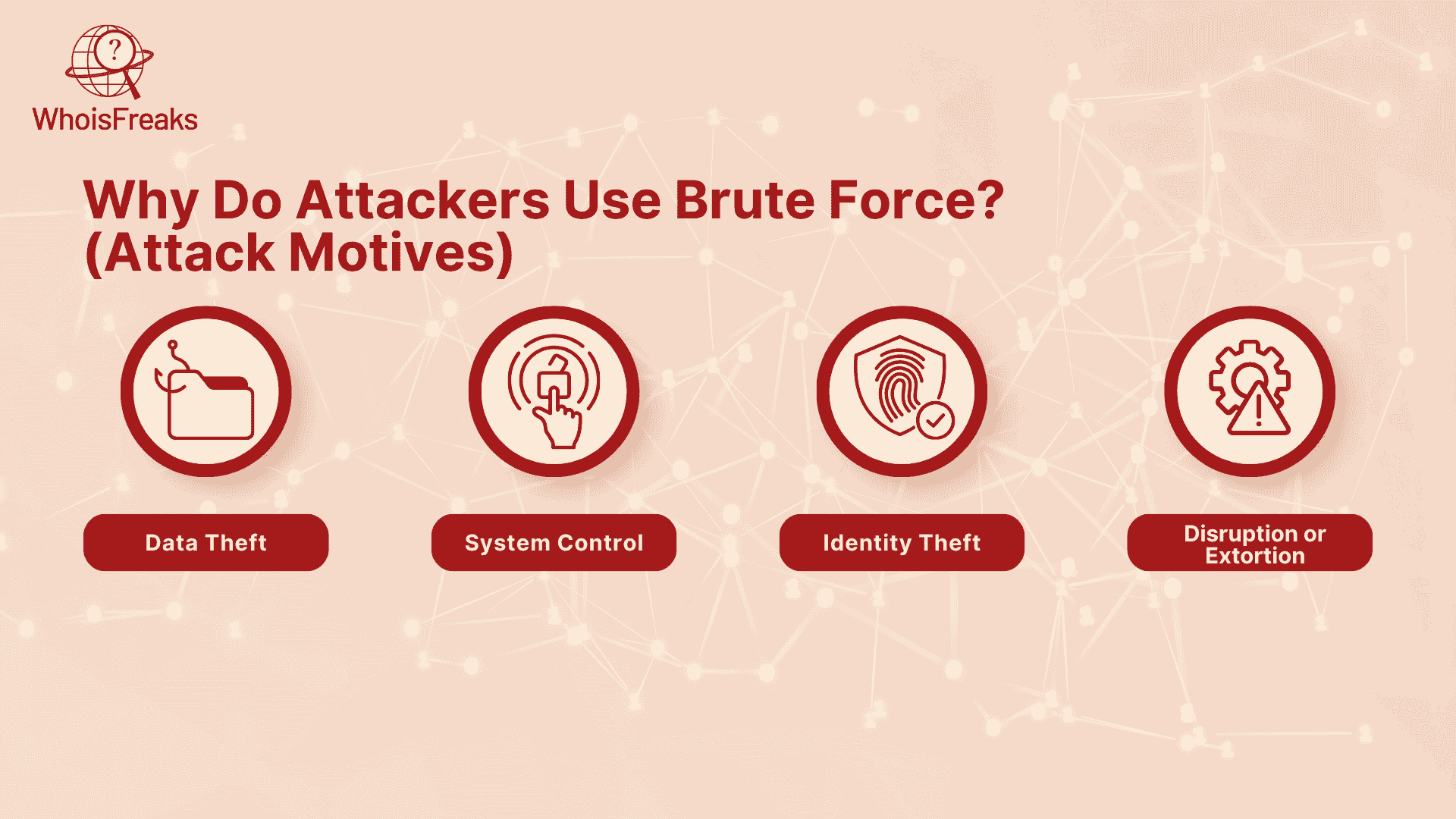
Here are the most common reasons attackers use brute force methods:
The first reason behind brute force attacks is to steal sensitive information, such as:
Once they get in, they can sell the data on the dark web or use it for blackmail.
By gaining access to admin accounts or cloud platforms, attackers can:
This gives them power to spy, steal, or disrupt operations.
If they break into personal accounts, hackers can:
Identity theft can lead to long-term financial and legal damage.
Some attackers just want to cause chaos or demand ransom after gaining access.
Knowing the “why” behind brute force attacks helps organizations:
Blocking brute force attacks isn’t just about passwords, it’s also about knowing who’s trying to get in and implementing strategies such as limit login attempts. That’s where IP and domain intelligence becomes a powerful line of defense.
This type of intelligence helps you analyze the source of traffic and determine whether it’s trusted, suspicious, or outright malicious.
By using this data, you can spot unusual login attempts even if the password is correct.
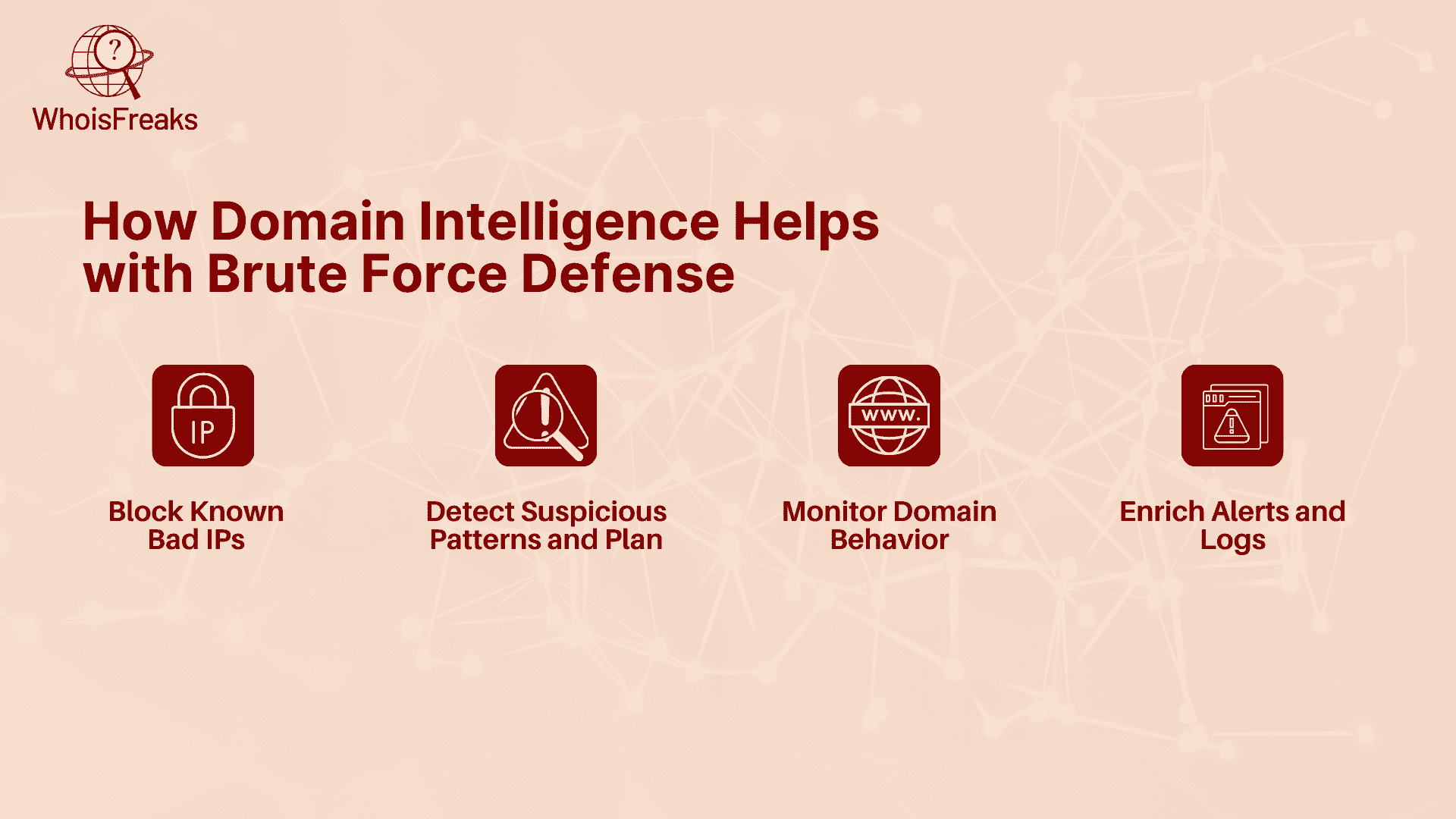
Platforms like WhoisFreaks offer easy-to-use APIs that let you:
You don’t need a complex setup just call the API when a login attempt is made and decide whether to block, alert, or allow it based on the IP/domain reputation.
To build an effective defense against brute force attacks, you need more than strong passwords you need real-time insights into where login attempts are coming from and how they behave. This is where WhoisFreaks' tools come into play. They provide accurate, actionable IP and domain intelligence that can be integrated directly into your security systems.

The WhoisFreaks IP Geolocation API delivers detailed IP-level information that can be used to make immediate access decisions. It gives you the user’s IP location, including country, city, and time zone, and also provides insights into their ISP, ASN, and whether the connection comes from a data center, VPN, or proxy. This allows you to flag or block login attempts that fall outside of normal behavior such as someone trying to access a user account from a suspicious region or anonymized IP.
Other valuable tools include the Security Lookup Tool, which checks if an IP is associated with malicious activity or anonymized traffic, and the Subdomain Lookup Tool, which can reveal hidden attacker infrastructure. You can also use the IP WHOIS Lookup to understand who owns the IP address, what organization it belongs to, and whether it’s part of a known threat network.
These tools aren’t just useful for manual checks they’re made to be integrated. You can connect WhoisFreaks’ API with your firewall or Web Application Firewall (WAF) to automatically block or filter traffic based on IP reputation or geolocation. In Security Operations Centers (SOCs), the data can be used in SIEM platforms to enrich logs and provide deeper context for login activity, enabling more accurate detection and faster response. You can also enhance login systems by incorporating geolocation logic to alert on unusual access patterns like a login from a foreign IP just minutes after one from a trusted local network.
Defending against brute force attacks isn’t a one-time setup—it’s an ongoing process that involves staying updated, analyzing trends, and combining multiple layers of security. By following a few foundational best practices and addressing weak password policies, you can significantly reduce the risk of a successful attack while improving your team’s response time and system resilience.
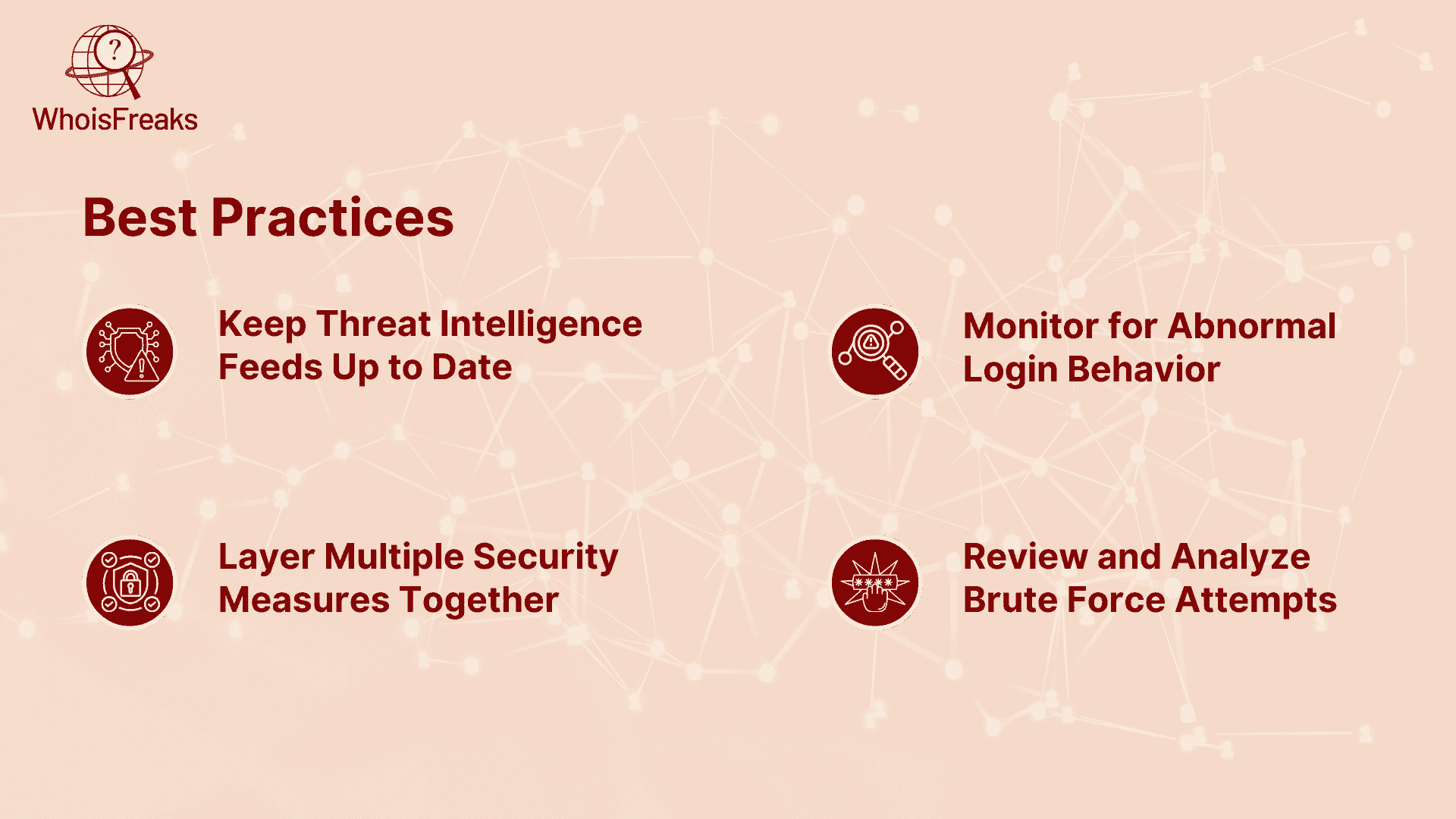
Attackers constantly change their tactics, infrastructure, and IP addresses. That’s why it’s crucial to ensure your threat intelligence feeds are regularly updated. Using WhoisFreaks' API, you can maintain an accurate and real-time view of risky IPs, new subdomains, or suspicious domains that may be involved in brute force attacks. Staying updated allows you to act before attackers even complete their first attempt.
Consistent monitoring is one of the most reliable ways to detect brute force activity early. Set up logic in your systems to watch for multiple login attempts that come from unfamiliar locations, devices, or IP ranges. WhoisFreaks' geolocation and security lookup tools make it easy to enrich login logs with IP-based intelligence, helping you spot anomalies that would otherwise go unnoticed.
No single method can stop all brute force attacks. That’s why you should always combine multiple defenses. Use multi-factor authentication to add an extra layer beyond passwords. Implement rate limiting to slow down rapid login attempts. Add CAPTCHAs to stop bots, and integrate IP/domain intelligence to make smarter access decisions. When these measures work together, your overall security posture becomes much stronger.
Finally, take the time to log and review brute force activity on a regular basis. Analyze failed login patterns, repeated IPs, and suspicious behaviors to understand how attackers are targeting your systems. Use WhoisFreaks' historical data and lookup tools to dig deeper into where those IPs are coming from and whether they are part of a larger attack network. This insight helps you refine your security rules and strengthen weak spots before they’re exploited again.
Brute force attacks may be simple in nature, but their impact can be devastating when security systems aren’t prepared. Whether attackers are guessing passwords, reusing stolen credentials, or hiding behind proxies, the goal is always the same to gain unauthorized access and exploit your systems.
Defending against these threats requires more than just strong passwords. It takes a layered strategy that includes prevention, detection, response, and most importantly, real-time intelligence. By understanding where attacks are coming from and how they behave, you gain the power to block threats before they break through.
That’s where tools like WhoisFreaks come in. With IP geolocation, subdomain analysis, security lookups, and WHOIS data, you can strengthen your brute force defense using accurate, actionable insights.
Ready to boost your defenses? Start using the WhoisFreaks IP Geolocation API and explore free tools like the Security Lookup, Subdomain Lookup, and IP WHOIS to identify threats, block bad actors, and secure your applications against brute force attacks before they succeed.

Discover how IP intelligence enhances early threat detection strategies to protect your digital assets. Read the article for insights and practical tips.
12 min read

Discover the fundamentals of IP geolocation and its vital role in enhancing security. Learn practical applications and best practices in our latest article.
11 min read