

By Qasim
Posted on November 05, 2025 | 8 min read
DNS cache poisoning also called DNS spoofing or pharming is an attack where false information is inserted into a DNS resolver’s cache. Because DNS acts like the internet’s phonebook (turning domain names into IP addresses), poisoning the cache sends users to the wrong sites. In a poisoned cache, a resolver will give an incorrect IP address to visitors, often directing them to fake or malicious sites instead of the intended ones. Since most DNS servers trust their cache entries and have no built-in verification, bad entries can remain until their time-to-live (TTL) expires or they are manually cleared.
Below the blog will explain how web cache poisoning works, what risks it poses, and how to prevent it including how WhoisFreaks' domain and DNS tools can help detect or avoid these attacks.
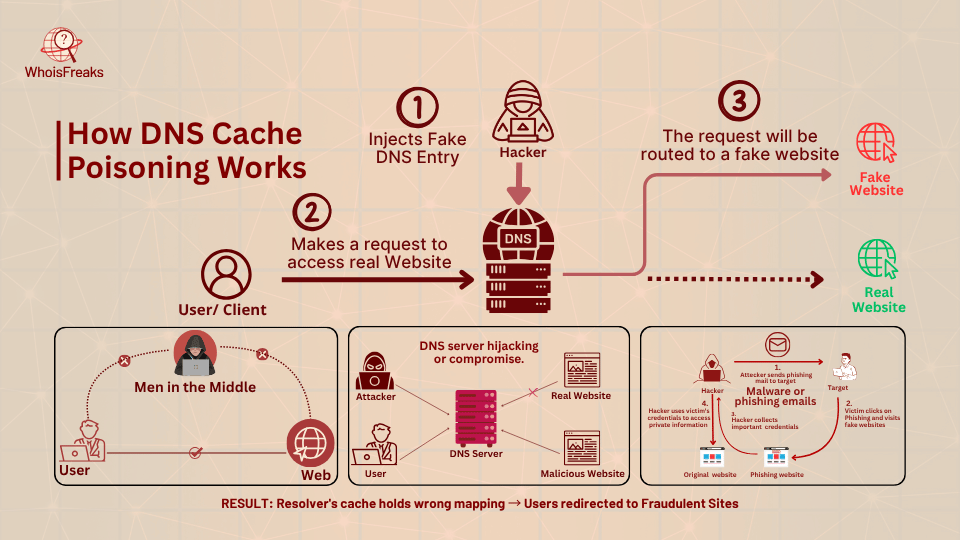
Under normal operation, DNS resolvers interrogate authoritative servers and store the appropriate responses (IP addresses of domain names) so that they can be used to handle DNS requests more efficiently. However, hackers may use the vulnerabilities of the DNS to inject false records into this cache. Common methods include:
In each case, the result is that the resolver’s cache now holds a wrong "domain → IP" mapping. Subsequent queries for that domain will return the attacker’s IP, redirecting users to fraudulent sites.
Cache poisoning can have serious consequences for individuals and organizations. Key risks include:
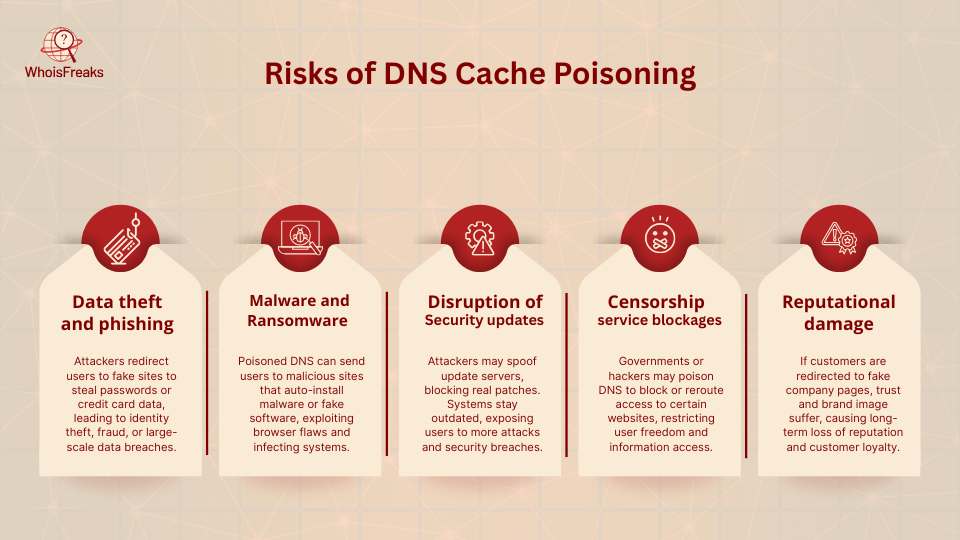
Defending against DNS cache poisoning requires multiple layers of protection, including the implementation of intrusion detection systems. Below are key strategies:
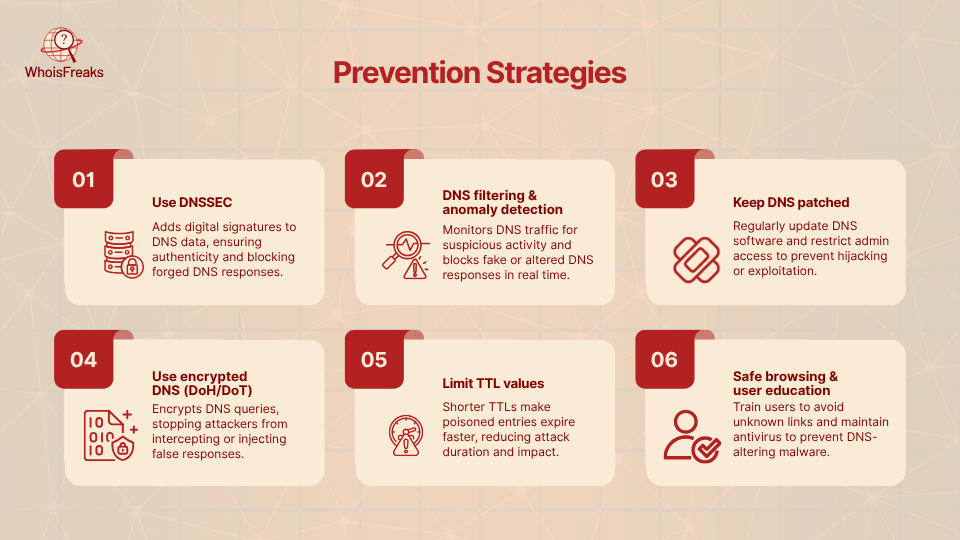
Together, these measures greatly reduce the chances of successful DNS cache poisoning. For example, a company can use DNSSEC on its domains and employ third-party DNS monitoring to cross-check that its domain’s IP addresses stay correct. If a mismatch is detected (indicating possible spoofing), teams can be alerted immediately.
WhoisFreaks provides domain and DNS intelligence services that help detect and prevent cache poisoning by verifying DNS data and monitoring for anomalies. WhoisFreaks boasts over 12 billion DNS records across 1,500+ top-level domains (TLDs). Key offerings include:
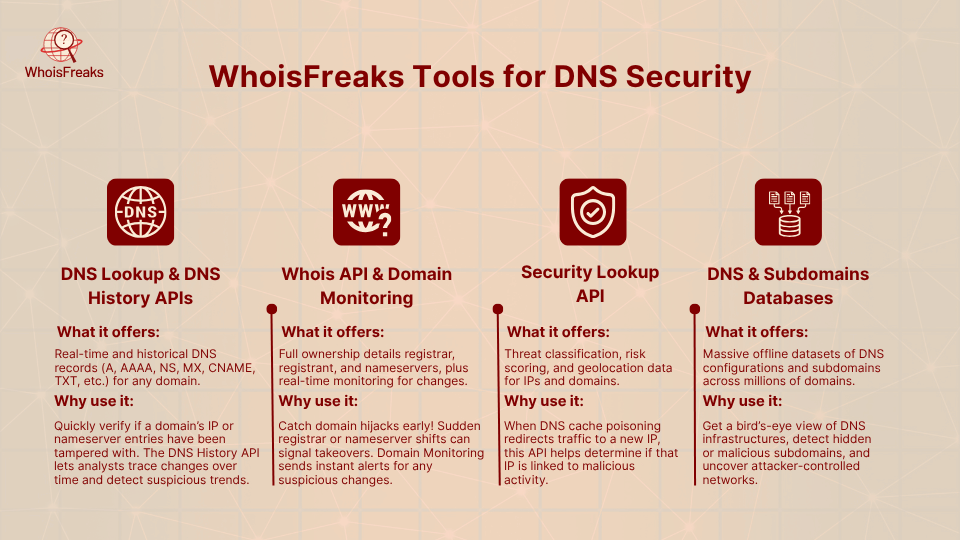
These tools can retrieve real time and historical DNS records (A, AAAA, NS, MX, CNAME, TXT, etc.) of any domain. Through the DNS API, a security team can write programs to check whether the current values of a domain in IP and nameserver entries are as expected. In case an attacker has inserted a counterfeit IP into the DNS server cache, the API will display a non-familiar address, which leads to the investigation. The DNS History API enables analysts to travel in time and identify trends.
WHOIS API gets ownership information (registrar, name servers, registrant information, etc.) of any domain. The transition of the registrar or nameserver without prior warning may be a sign of a takeover or hijack attempt that may be followed by DNS manipulation. The Domain Monitoring service of WhoisFreaks monitors the domains on the fly and sends an alert in the event of a change of ownership or status.
It is an API that categorizes IP addresses and domains in terms of threats and includes risk and geolocation information. When a cache poisoning attack causes the redirecting of a traffic to an unfamiliar IP, the Security Lookup may determine whether the unfamiliar IP correlates with malicious activity or not.
WhoisFreaks makes large DNS databases available to off-line examination. The DNS database allows security teams to query it in order to have a big picture view of DNS configurations (A, AAAA, MX, etc.) across a large number of domains. Subdomains Database is also available to monitor all familiar subdomains of a domain. In some instances, attackers use hidden sub domains when perpetrating attacks; by observing these sub domains, one can be able to detect related malicious infrastructures.
DNS cache poisoning continues to be one of the most deceptive yet dangerous cyber threats capable of redirecting users in the domain name system, stealing data, and damaging brand trust. Preventing it requires layered protection: using DNSSEC, secure DNS channels, regular monitoring, and continuous verification of DNS records.
With WhoisFreaks, you can take a proactive approach. Their DNS Lookup, DNS History, and Domain Monitoring APIs let you instantly verify DNS integrity, track suspicious changes, and identify potential hijacking before it causes harm.
Stay ahead of attackers and protect your web application by starting to monitor your domains and DNS data today with WhoisFreaks to protect your brand, users, and infrastructure from cache poisoning threats.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Learn how to prevent subdomain takeover with essential strategies and best practices. Protect your online assets—read the full guide now!
8 min read