

By Qasim
Posted on November 10, 2025 | 10 min read
Spear phishing is a very specialized variant of email scam which parades itself as a trusted individual or organization to target people. In contrast to the generic phishing where the attacker sends mass emails to large groups of people, the spear phishing attackers do their research and send individual messages in order to make the scam look genuine.
As an example, a spear phisher can impersonate a company CEO sending an email to a company finance officer or impersonate a reputable service, such as Microsoft or Amazon. Due to the email being seemingly personally targeted, the guard of the recipient is lowered and the spear phishing scams become much more believable, which can lead to identity theft. According to security reports, spear phishing is rampant and expensive: approximately 88% of organizations experience spear phishing every year, and advanced spear phishing attacks caused significant breaches and financial fraud.
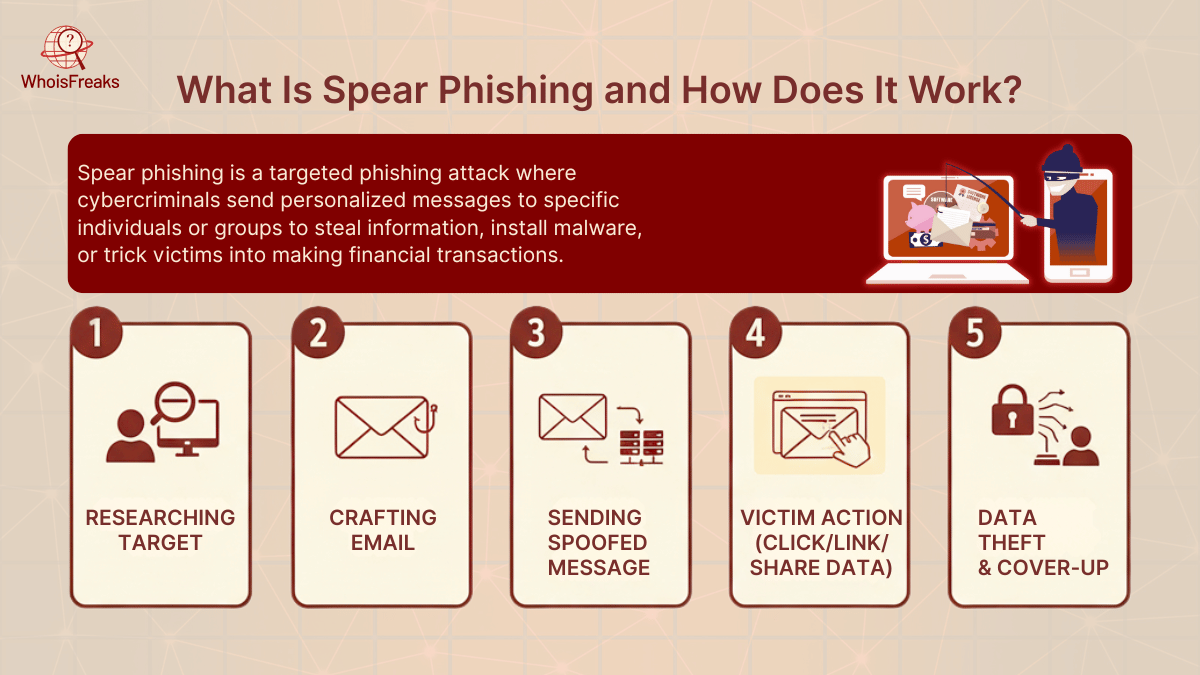
Spear phishing involves a form of targeted cyberattack on individuals or organizations, often revealing sensitive information. The attackers begin gathering sensitive information and personal information like job position, contacts, and interests of a high-value target, like an executive or financier, before collecting their personal information. With such facts, they develop a persuasive email or text that seems to be sent by a reliable individual like a colleague, supplier or a top manager.
Such messages may contain a malicious link or attachment, or it may request the victim to do a sensitive task such as sharing the login credentials or even making a payment. When the target cooperates, the attacker is capable of stealing data, obtaining unauthorized access, or inflicting financial damages, and then overwriting to cover up the tracks.
Because spear phishing is highly personalized, it often relies on social engineering using familiarity or urgency to manipulate victims. Unlike regular phishing, which targets many people at once, spear phishing focuses on a few well-researched victims for greater rewards. This makes it one of the most dangerous and effective cyber threats, emphasizing the need for strong awareness and to prevent spear phishing with effective prevention measures.
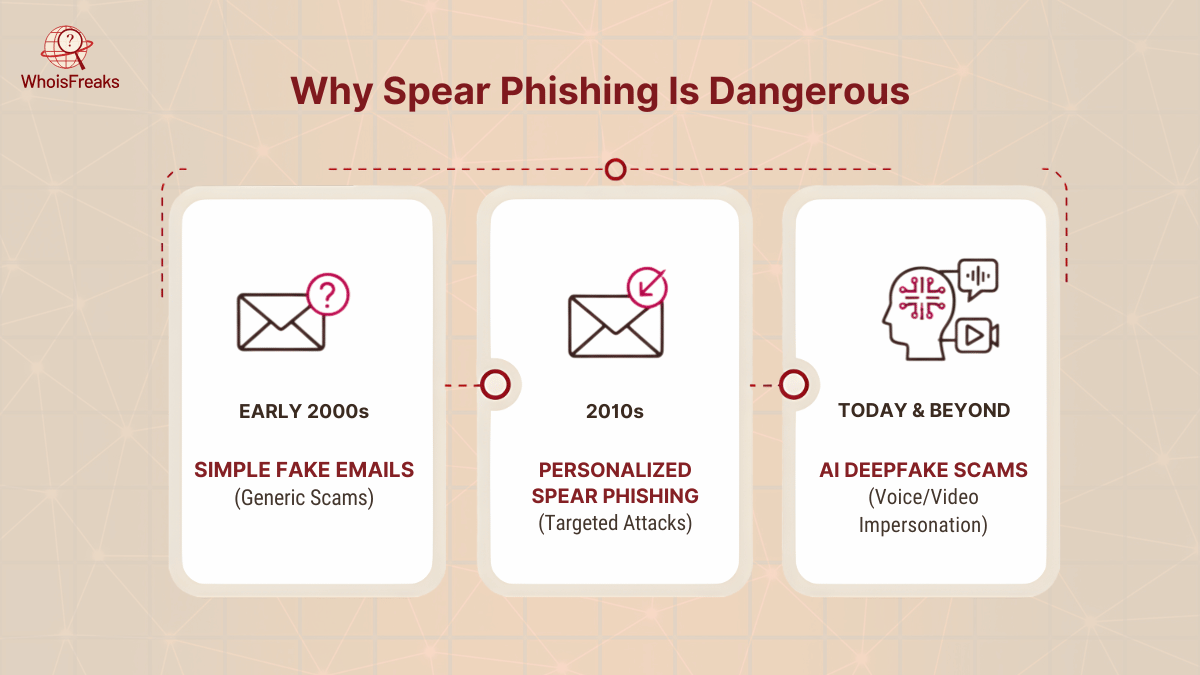
Spear phishing is alarmingly effective and on the rise. Recent threat analyses report that AI-powered spear phishing attacks are increasing, with attackers using machine learning and deepfakes to create highly convincing emails or even voice calls.
For example, attackers might use AI to generate a fake video or voice message from an executive demanding payment. According to a 2025 industry report, “highly targeted, AI-enabled spear phishing attacks are on the rise” and attackers are constantly developing new social engineering tactics
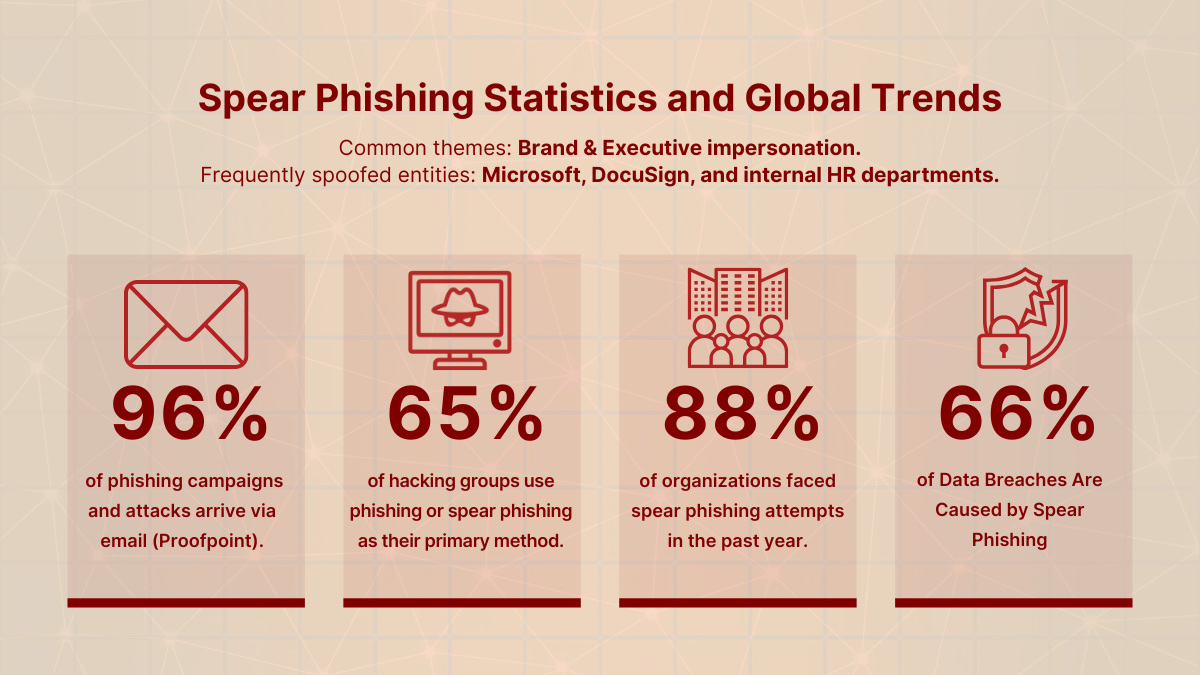
Statistics show that almost every organization will face spear phishing. Proofpoint notes that about 96% of phishing campaigns and phishing attacks arrive via email, and one study found that 65% of known hacking groups employ phishing and spear phishing as their favored attack vector. In fact, nearly 88% of organizations reported encountering spear phishing attempts in the past year.
According to the words of security experts, spear phishing is one of the major reasons of data breach and monetary loss. One study has determined that spear campaigns are infrequent (approximately 0.1 percent of phishing email messages), but 66% of all breaches are due to their accuracy and effectiveness. Most popular spear phishing themes are brand and executive impersonation. Popular services are frequently spoofed by attackers in order to trick victims into believing them. As an illustration, Microsoft, DocuSign, and even the internal departments such as HR are some of the best entities that have been spoofed by spear phishers.
Spear phishers use a variety of tactics, including spear phishing messages, to entice victims. Some of the most frequent techniques include:
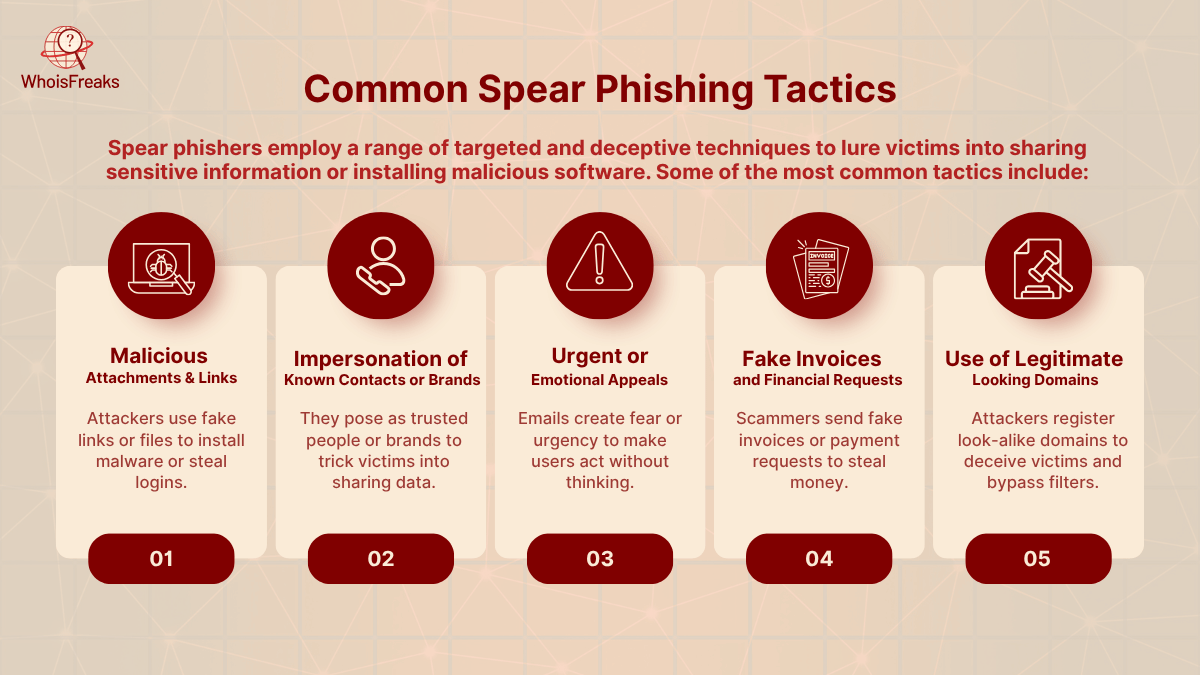
These tactics make spear phishing a versatile threat. Attackers will tailor their approach to the target. For example, tech-savvy employees might be targeted with highly sophisticated emails and fake login pages, while others might be lured by promises of financial gain or administrative requests.
Combating spear phishing requires a multi-layered approach that combines technology, policies, and user education. No single solution, including antivirus software, will stop all attacks, but together they can dramatically reduce risk. Key strategies include:
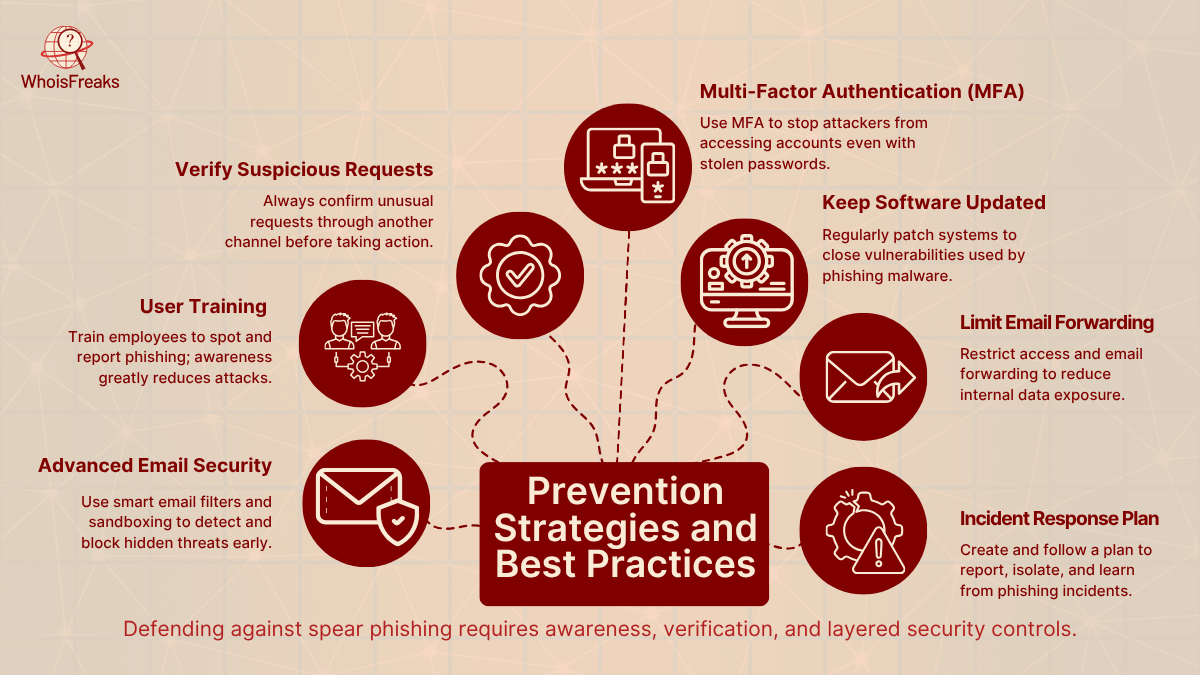
One powerful but often overlooked defense against spear phishing is domain and IP intelligence. Since attackers rely on fake or malicious domains, tracking and analyzing them can reveal early warning signs. WhoisFreaks offers a range of tools to detect, verify, and block such threats in real time. Security teams can use these tools to check suspicious domains, catch brand impersonations, and identify risky infrastructure before damage occurs.
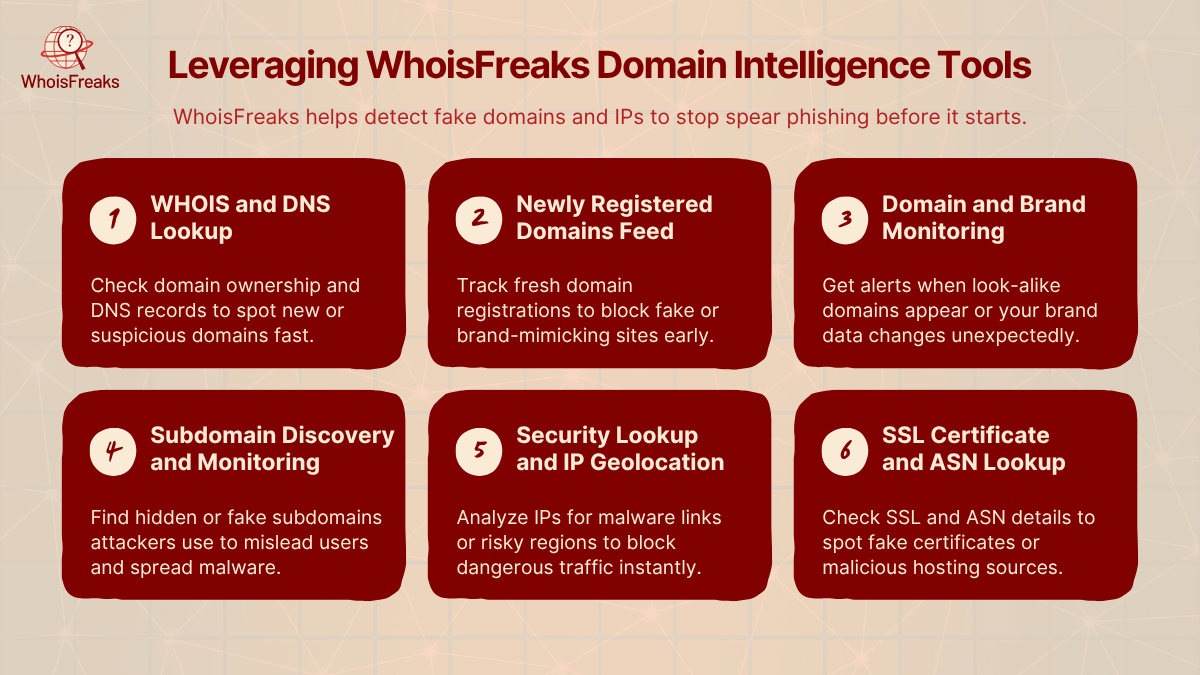
These tools show who owns a domain and how it’s set up. A domain with a recent registration date or hidden owner can be suspicious. DNS Lookup also reveals live records like IPs or mail servers if they point to known bad sources or look unusual, that’s a red flag. Analysts can quickly check if an email or domain is legitimate or newly created.
Attackers often use new domains to avoid detection. WhoisFreaks provides a daily list of recently registered domains with their WHOIS and DNS info. Monitoring for domains that mimic your brand helps catch threats early and block them before they’re used in attacks.
These tools automatically watch for domains or websites using your brand name or trademarks. Alerts trigger when suspicious lookalike domains appear. They also track changes to your own domains like unexpected DNS updates that could signal tampering.
Some attacks use hidden or fake subdomains to trick users. WhoisFreaks’ tools can list all subdomains linked to a domain, helping analysts spot malicious setups. Regular monitoring also helps detect unauthorized domain use.
These tools analyze IP addresses to see if they’re tied to malware, proxies, or threat networks. They also show the IP’s country and internet provider. If a phishing link or login attempt comes from a high-risk region or flagged IP, it can lead to download malware and be blocked immediately.
Attackers may use fake SSL certificates to appear trustworthy. WhoisFreaks' SSL Lookup reveals certificate details, such as who issued it and when it expires, helping to prevent business email compromise . ASN Lookup identifies the network that owns an IP useful for spotting connections to shady hosting providers or threat actors.
Spear phishing remains a top cyber threat because it exploits human trust and sophisticated social engineering. The attack is effective but also preventable with the right spear phishing prevention defenses in place, ensuring they can differentiate from legitimate emails . The key insights are:
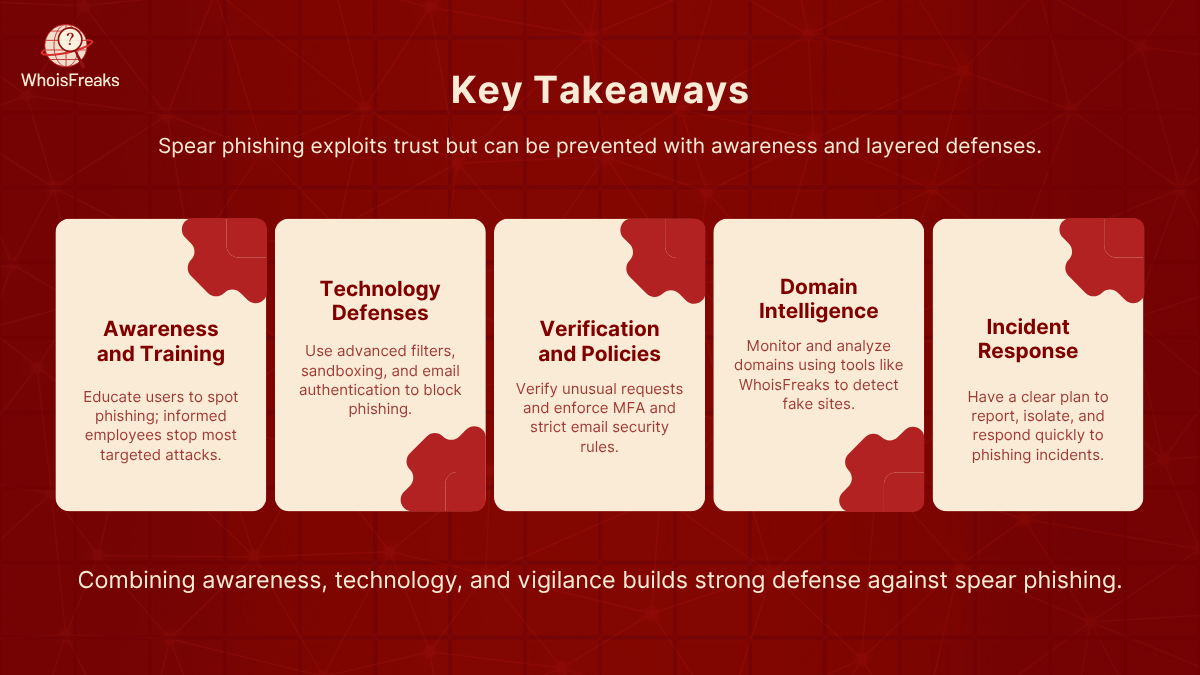
By combining these strategies, organizations and individuals can build a robust defense against spear phishing. In an environment where attacks are continuously evolving, staying informed and proactive is the best protection. Using the latest security tools and maintaining a vigilant mindset will help ensure that spear phishing threats are detected early and neutralized before any security risk or harm is done.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Learn how to prevent subdomain takeover with essential strategies and best practices. Protect your online assets—read the full guide now!
8 min read