

By Qasim
Posted on July 10, 2025 | 10 min read
In today's world of cybersecurity, businesses are always working hard to protect their online systems from growing and increasingly complex attacks. Often, the focus is on securing the main website and its key elements, but the real threats can hide in places that are easy to miss: subdomains, which are associated with a specific domain name. These smaller parts of a website or network can be weak points that attackers use to break in, making them an important area to look at when managing overall security.
Attack surface management means finding, analyzing, and reducing the various ways that attackers could get into your systems. Subdomain enumeration plays a big role in this process. By identifying all the subdomains linked to a main domain, organizations can get a clearer picture of their online presence and spot hidden risks before they become bigger problems, especially with the use of vulnerability scanners.
Even though subdomain enumeration is often ignored, it provides crucial information about your security weaknesses. Many businesses believe that securing their main website is enough, but attackers know how to target subdomains, which are often overlooked and less protected. In this blog, we'll explore why subdomain enumeration is so important, how it fits into attack surface management, and why it should be a priority in your cybersecurity plan.
Subdomain enumeration is a process used to discover all subdomains associated with a particular domain. While a domain name typically represents a primary website or service, it can also have various subdomains for example, blog.screenshotapi.net or support.screenshotapi.net, as well as corresponding CNAME records. These subdomains often correspond to different services, applications, or infrastructure components within an organization’s network.
In cybersecurity, subdomain enumeration is important because it helps uncover hidden parts of a company’s online presence. Attackers often target subdomains that are neglected, poorly managed, or not as secure as the main website. Even if the main domain is well-protected, subdomains can still be vulnerable if they are not given the same attention, potentially exposing sensitive data.
Subdomain enumeration works by finding these subdomains using different methods. This can include checking DNS records, spotting patterns in subdomain names, or using domain registration data. The goal is to create a full list of active subdomains that can be examined for security risks.
By identifying these subdomains, organizations can find weak spots in their network, such as outdated systems or misconfigurations. These overlooked subdomains can be easy targets for attackers, so knowing where they are is the first step to securing your infrastructure and eliminating potential entry points.
If an organization uses WhoisFreaks' Subdomains Lookup Tool, they can automatically find and list all subdomains linked to a domain, giving your security team the visibility needed to protect your assets. By regularly using subdomain enumeration with this tool, you can stay ahead of potential threats and address security issues before they become a problem.
In cybersecurity, attack surface management is a key strategy to find, manage, and reduce the various entry points that attackers could use to break into a system. Subdomains, which are often overlooked, are a significant yet hidden part of an organization’s attack surface. If not properly managed, these extra access points can greatly increase the risk of a security breach, highlighting the need for an incident response plan .
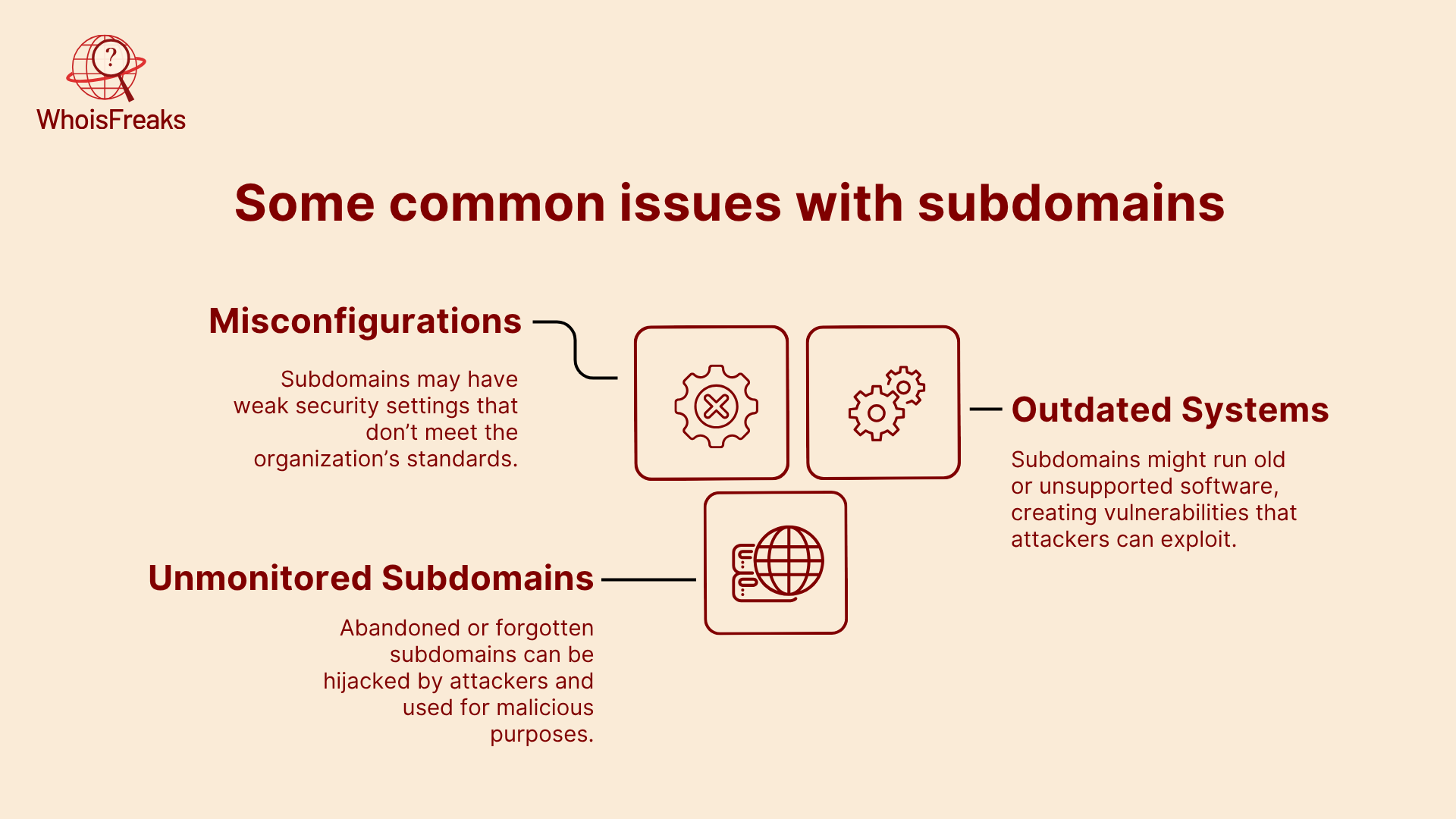
Subdomains expand an organization's digital footprint, giving attackers more potential targets. While the main domain might be well-protected, subdomains can be neglected and left vulnerable. This oversight can lead to attacks like misconfigurations, outdated software, and even subdomain takeovers, where attackers take control of abandoned or unmonitored subdomains.
Subdomain enumeration helps organizations gain visibility into these often-ignored subdomains. By mapping out all subdomains, security teams can identify hidden entry points that might not be detected during regular security checks of the main domain.
Effective attack surface management means continuously identifying and analyzing subdomains. This helps organizations reduce risks, fix vulnerabilities, and prevent unauthorized access to their digital assets, a priority for cybersecurity teams.
In today’s complex digital world, cybersecurity threats don’t only target the main domain of a website or service. Attackers are getting smarter and often find ways to bypass traditional security measures to exploit vulnerabilities in subdomains. This is where subdomain enumeration becomes a crucial part of modern cybersecurity defenses for identifying critical vulnerabilities .
Subdomain enumeration helps reveal hidden or overlooked parts of your digital infrastructure. It’s not just about finding new subdomains, but also understanding how attackers could use these areas to break into your system. While a subdomain might seem insignificant, misconfigurations or poor maintenance can turn it into an easy entry point for attackers. By regularly identifying and securing subdomains, organizations can significantly reduce their risk of being targeted by attackers who seek to extract data.
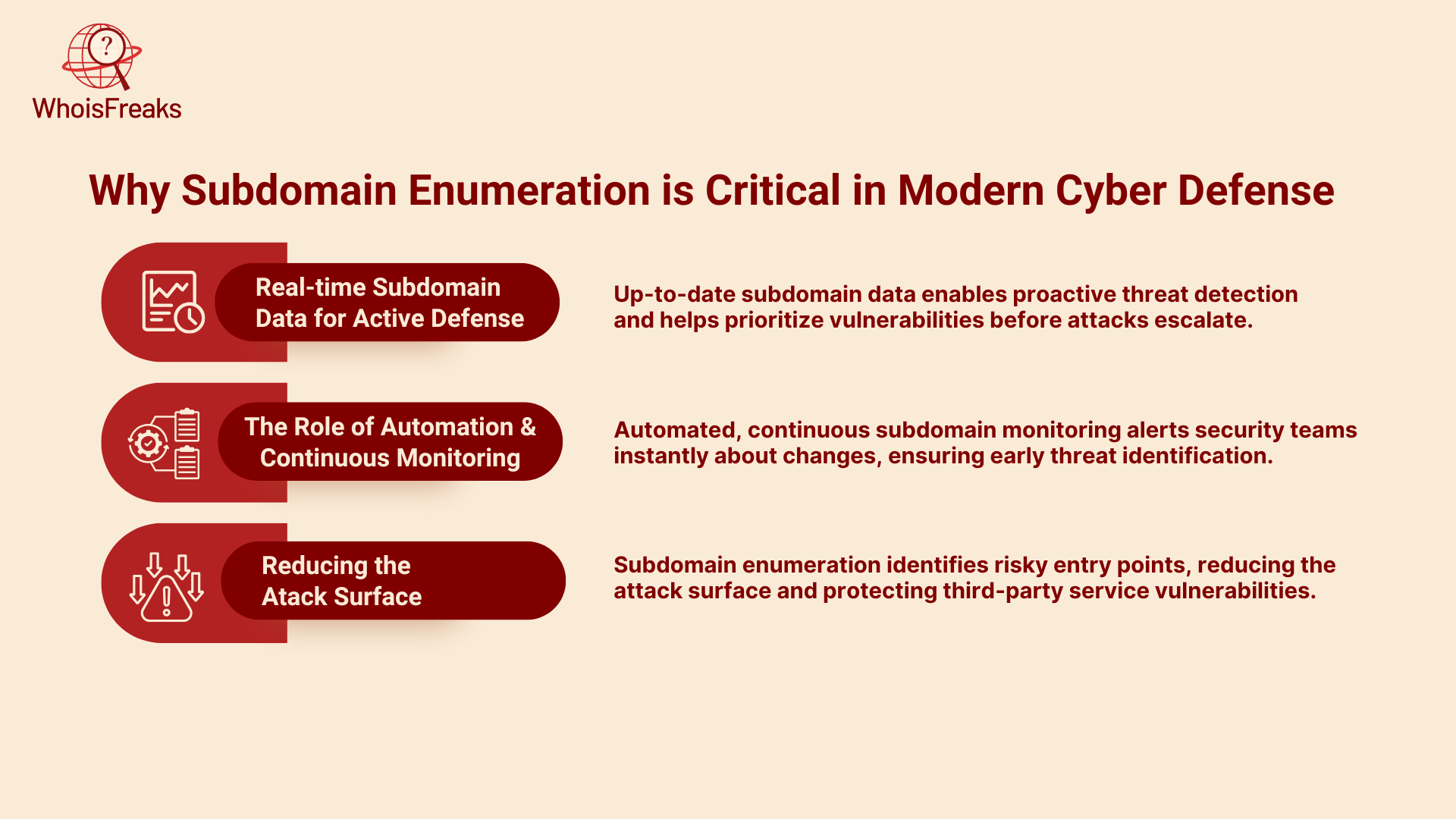
Having access to accurate, up-to-date subdomain data allows security teams to act proactively rather than reactively. As part of a modern defense strategy, subdomain enumeration helps security professionals map out the attack surface and prioritize vulnerabilities that need attention. This proactive approach is essential in identifying potential threats before they escalate into full-blown attacks.
One of the challenges of managing subdomains is that they can constantly change. New subdomains can be created without much notice, while old ones might be abandoned or forgotten. As part of an ongoing security strategy, subdomain enumeration should be an automated, continuous process. This allows security teams to receive alerts and updates as soon as new subdomains appear or if there are significant changes in existing ones. Automated monitoring ensures that subdomains are constantly assessed for potential risks.
A key objective of subdomain enumeration is to reduce the attack surface by identifying areas of potential risk. The attack surface includes all the points an attacker can use to enter and exploit an organization’s network. By identifying and securing subdomains, you reduce the number of entry points available to attackers. This makes it harder for malicious actors to find vulnerabilities in your infrastructure, especially those that involve third party services.
Here’s a simplified version of your content: To effectively manage and secure the attack surface, organizations need to use the right tools and techniques for subdomain enumeration. Automated solutions help security teams quickly identify and track subdomains, ensuring no hidden entry points are missed. Subdomain enumeration involves both passive and active methods, each offering unique benefits.
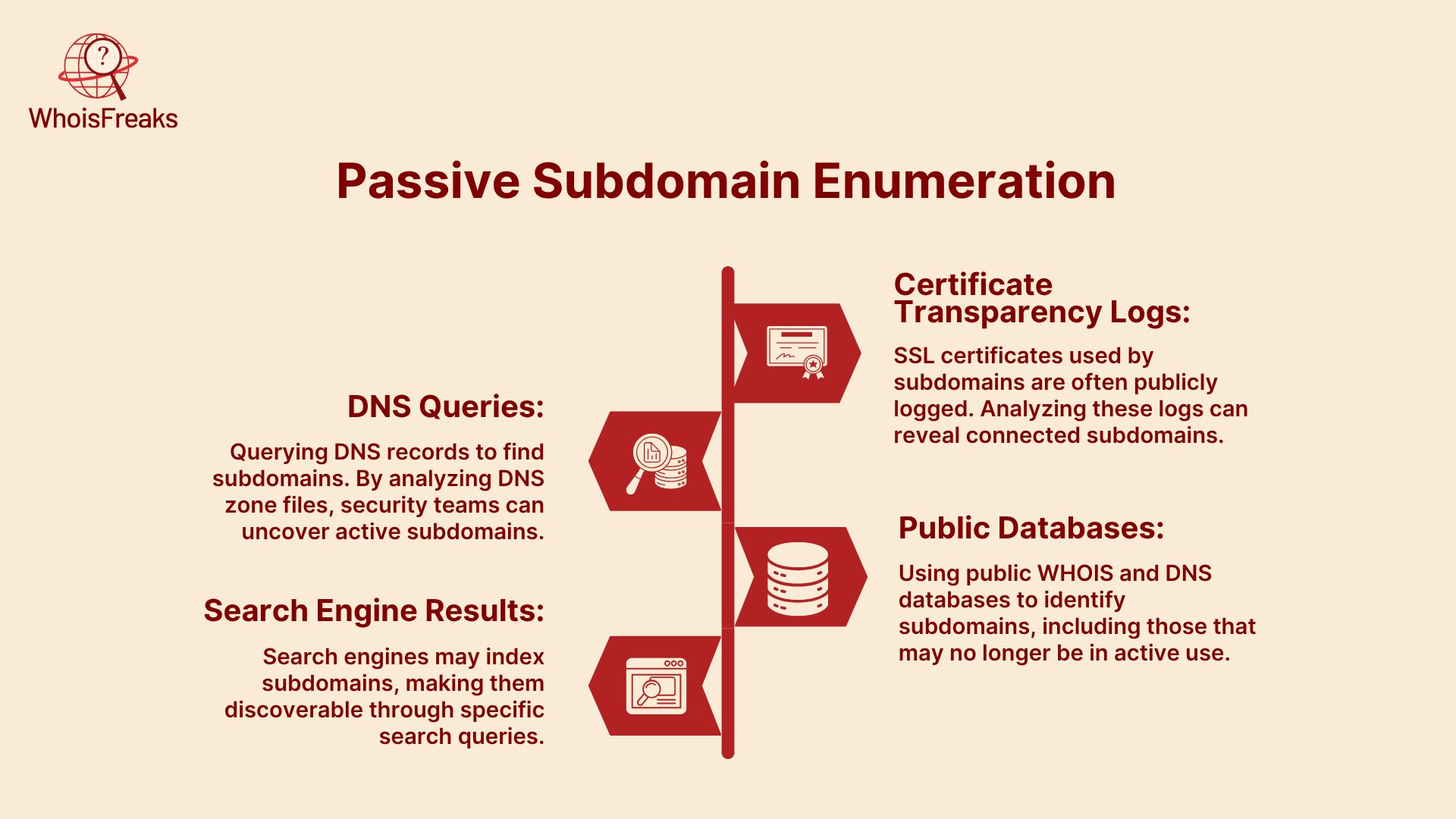
Passive subdomain enumeration uses publicly available information to find subdomains. This method does not directly interact with the target domain, making it a safe way to gather data without alerting the domain owner. Some common passive techniques include:
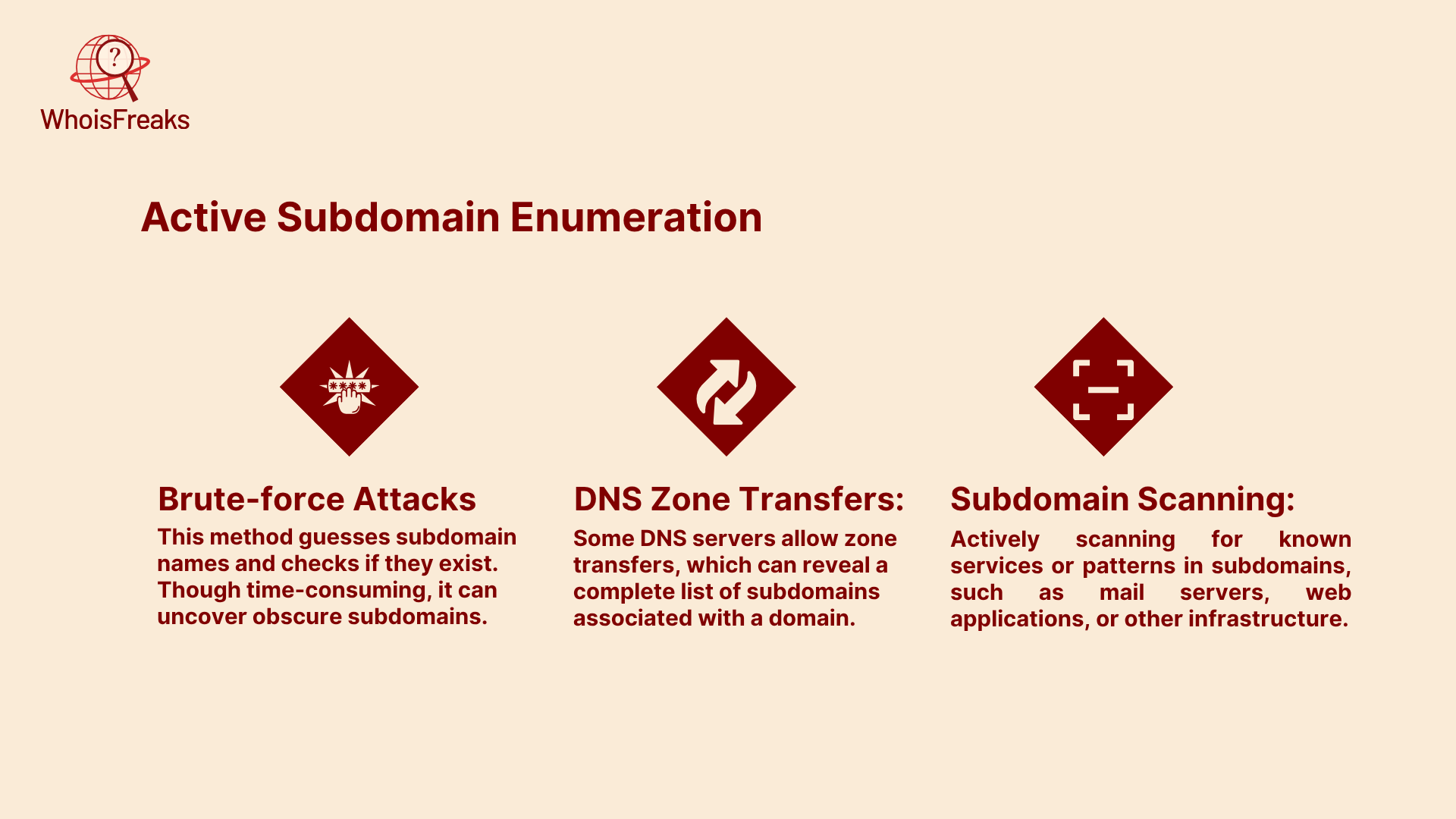
Active subdomain enumeration, in contrast, involves direct interaction with the target system. This method is more aggressive and typically requires scanning or probing the domain’s infrastructure. Some active techniques include:
By combining both passive and active techniques, organizations can perform thorough subdomain enumeration, ensuring all potential vulnerabilities are identified. Since this process can be time-consuming and complex, using automated tools is essential for efficiency, allowing teams to perform extensive reconnaissance.
While subdomain enumeration is essential for identifying vulnerabilities in an organization’s digital infrastructure, it does come with its challenges. The complexity of today’s digital environments and the large number of subdomains many organizations manage can make the process difficult. Understanding these challenges is important when developing a comprehensive attack surface management strategy.
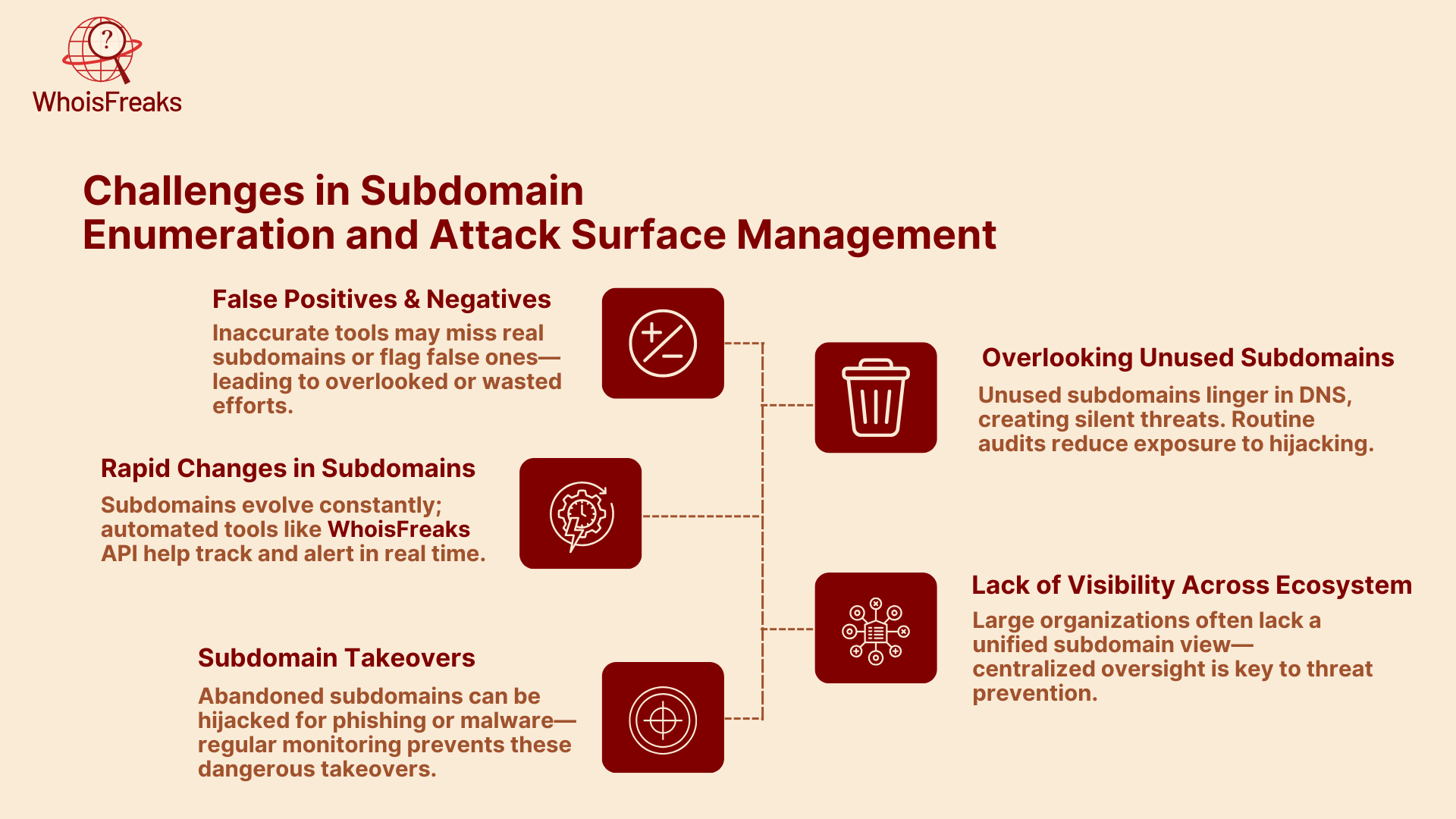
One challenge in subdomain enumeration is accuracy. Tools can sometimes produce false positives (identifying a non-existent subdomain) or false negatives (failing to identify an existing subdomain). These inaccuracies can lead to missing vulnerabilities or wasting resources chasing incorrect information.
Organizations constantly create, modify, and remove subdomains, making it hard to keep track of them. Some subdomains may appear and disappear quickly, and outdated subdomains can pose security risks if not regularly monitored. Automated tracking is necessary to stay on top of these changes.
Using tools like WhoisFreaks' Subdomains Lookup API can help automate the tracking of new subdomains and alert security teams to any changes in real time.
Subdomain takeovers happen when a subdomain is abandoned or no longer in use. Attackers can hijack these subdomains if they point to unused resources, such as cloud services or hosting platforms. This can lead to phishing attacks, malware distribution, or further breaches where attackers gain unauthorized access . Regular monitoring and quick action are crucial to prevent these takeovers.
Many organizations fail to regularly check or clean up unused subdomains. These forgotten subdomains can still exist in DNS records and may be hijacked by attackers. Consistent audits and cleanup of inactive subdomains are important to reduce the risk of exposure.
In large organizations, it can be hard to keep track of every subdomain, especially if different teams manage them for different projects, sometimes linked to specific IP addresses. Without a clear strategy to monitor all subdomains, security teams may miss vulnerabilities. A complete and centralized view of all subdomains is essential for effective security management and for the security community to share best practices.
To effectively manage subdomains and reduce security risks, follow these best practices:
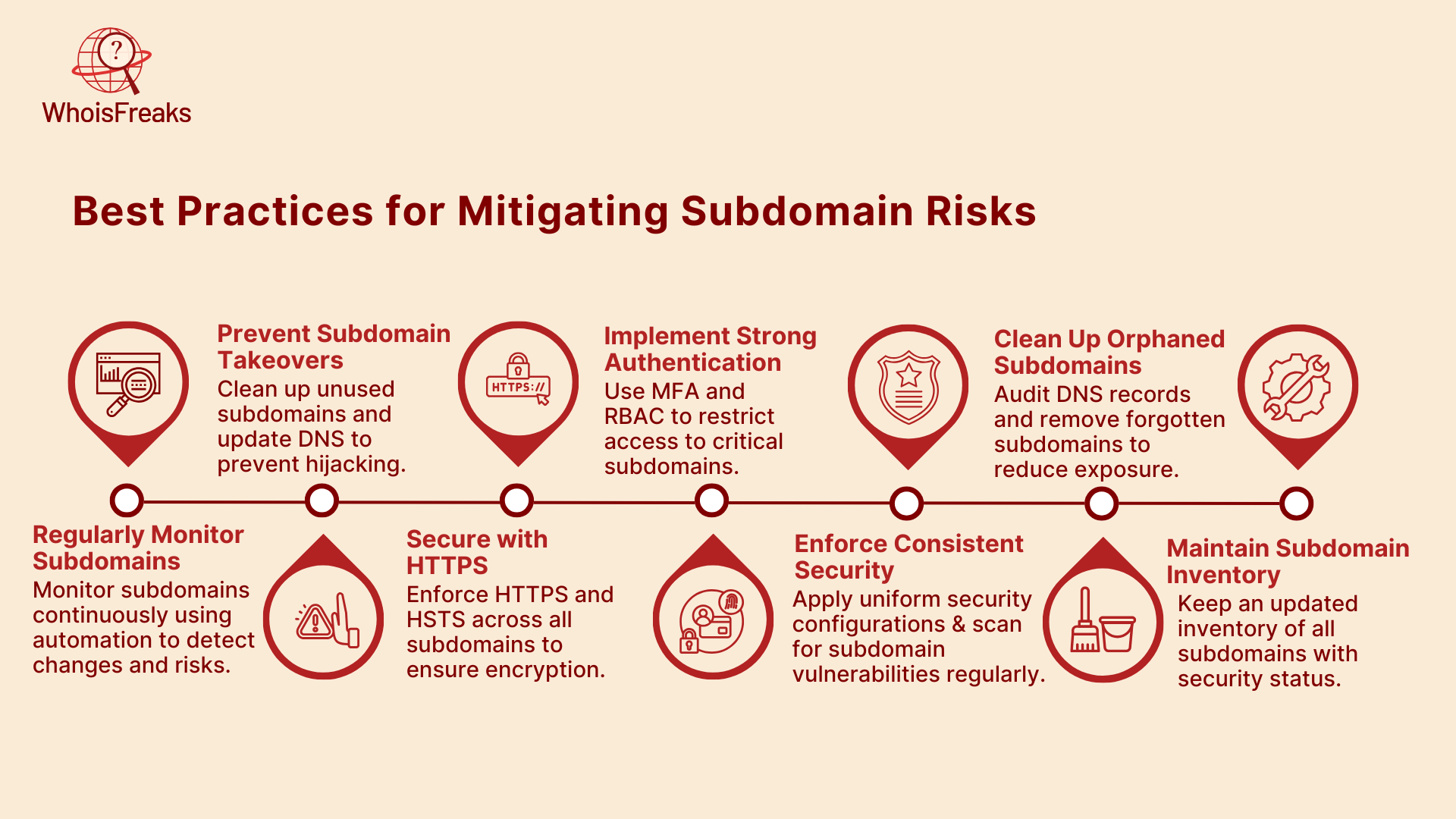
Continuously monitor subdomains to track new, modified, or abandoned entries. Automated tools like WhoisFreaks' Subdomains Lookup API can help with real-time updates and prevent missed vulnerabilities.
Regularly clean up unused subdomains and ensure DNS records are updated when services are decommissioned. Secure all subdomains and avoid leaving them orphaned or unmanaged.
Ensure all subdomains are protected with HTTPS and implement HSTS to prevent man-in-the-middle attacks.
Use Multi-Factor Authentication (MFA) and role-based access control (RBAC) to restrict access to sensitive subdomains, limiting exposure.
Maintain uniform security configurations across all subdomains. Use automated tools to scan for vulnerabilities and ensure compliance.
Regularly audit and remove unused subdomains. These can pose a significant security risk if left unmanaged.
Keep an up-to-date inventory of all subdomains, detailing their purpose and security status. This inventory helps ensure comprehensive attack surface management.
Subdomain enumeration plays a critical role in uncovering hidden threats and managing your organization’s attack surface. By identifying and securing all subdomains associated with your domain, you can gain greater visibility into your digital infrastructure, detect vulnerabilities early, and prevent potential attacks by implementing proper CSP headers. Subdomains are often the overlooked entry points that attackers exploit, making it crucial to regularly audit, monitor, and secure them.
As cyber threats evolve, so must your defense strategies. Subdomain enumeration is an ongoing process that should be integrated into your broader attack surface management plan. With tools like WhoisFreaks' Subdomains Lookup API, security teams can automate the discovery and monitoring of subdomains, ensuring they are always aware of any new vulnerabilities or changes to their digital footprint.
By proactively identifying and managing subdomains, organizations can significantly reduce their risk exposure, secure their digital assets, and stay one step ahead of attackers. The more you know about your subdomains, the better equipped you’ll be to protect your organization from hidden threats.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore how WHOIS history aids forensic analysis in cybercrime investigations. Learn effective strategies to enhance your cyber defense. Read more now!
9 min read

Learn how subdomain discovery can enhance phishing prevention and protect against spoofing campaigns. Read the article for practical strategies.
12 min read