

Posted on September 10, 2025 | 8 min read
In today's digital world, particularly with the rise of newly registered domains cyber threats are growing at an alarming rate. Each and every day, thousands of new sites and domains are being registered. Although most of them are authentic, a great number of them are generated out of ill intentions. Cybercriminals can use these freshly created domains to deliver malware, launch phishing attacks, steal credentials and other sensitive information, or conduct other massive attacks of businesses and individuals.
The largest risk is that new domains are generally not subjected to build up reputation. The trust scores-based security tools are not able to understand them as malicious in many cases until it is too late. This renders newly registered domains, which pose a potential risk, the ideal instrument of the cybercriminals.
Firewalls will be useful in this area. A firewall is a computer protection in the form of a digital gatekeeper. It keeps track of traffic on your network, prohibits dangerous connections and lets only secure communication, protecting sensitive data such as credit card information, into your system. By properly setting a firewall, organizations and individuals will be able to prevent any unwanted domain traffic, eliminate malicious traffic, and significantly decrease chances to become a victim of a cyberattack.
This blog will explain the importance of blocking threats using firewalls, highlight how malicious activities work, and provide insights on how to block newly registered domains using firewall as best practices you can follow to protect yourself from cybercriminals.
Before diving into the details of malicious activities and domain blocking, it’s essential to understand the role of firewalls.
Firewall is like a security gate between the Internet and store or network. It keeps track of the traffic coming to the system and the one going out of the system and judges accordingly to either permit or block it based on the set rules. It curbs unauthorized access, restriction of downloads of malicious files, and protection of sensitive information for the first time ensuring comprehensive security.
In short, a firewall is your first line of defense against the evolving cyber threat landscape.
Cybercriminals exploit newly registered domains for phishing, scams, and malware distribution.
These activities often bypass traditional reputation checks, making detection more difficult.
Newly registered domains are cheap, quick and easy to acquire. Cybercriminals use this by registering domains used by phishing websites, counterfeit online storefront, or servers used to host malware. These domains are new, and, in most cases, they may not be suspicious with the help of the traditional reputation-based mechanisms.
WHOIS data is one of the best methods to detect suspicious domains because it contains the information about the person, who registered this domain, when it was registered and other data. When the information of ownership is suspiciously fake, or when the domain is far too new, it is a warning sign. Security solutions like WHOISFreaks provide valuable data to help organizations monitor and flag risky domains.
Cybercriminals constantly adapt with new domains and attack strategies, making continuous monitoring essential. Firewalls strengthened with threat intelligence feeds, patches, and updates provide real-time defense. Advanced solutions predict and block malicious domains before damage occurs.
Cybercriminals constantly adapt. A given domain that is blocked today may be swapped with another one tomorrow. This renders ongoing observation to be important. Security teams should monitor the processing of domain registrations in real-time and to block those involved in malicious activities.
Current firewalls are able to customize with threat intelligence feeds that will update in-real-time on latest malicious domains, IP addresses, and attack methods. This makes sure that you are constantly ready to block the latest threats with your firewall.
Firewall, just like any other software must be updated on a regular basis. There are outdated security systems that may be used by the cybercriminals. By installing patches and firmware upgrade, you can keep your firewall well-fortified against the latest attack techniques.
Attackers tend to employ strategies such as domain generation algorithms (DGAs), which generate thousands of new domains in a day to evade detection. Security solutions can evaluate trends in newly registered domains and employ machine learning translation to predict domains they suspect are malicious and block them before they can cause damage.
WhoisFreaks offers a suite of domain and IP intelligence tools that directly support firewall-based threat blocking.
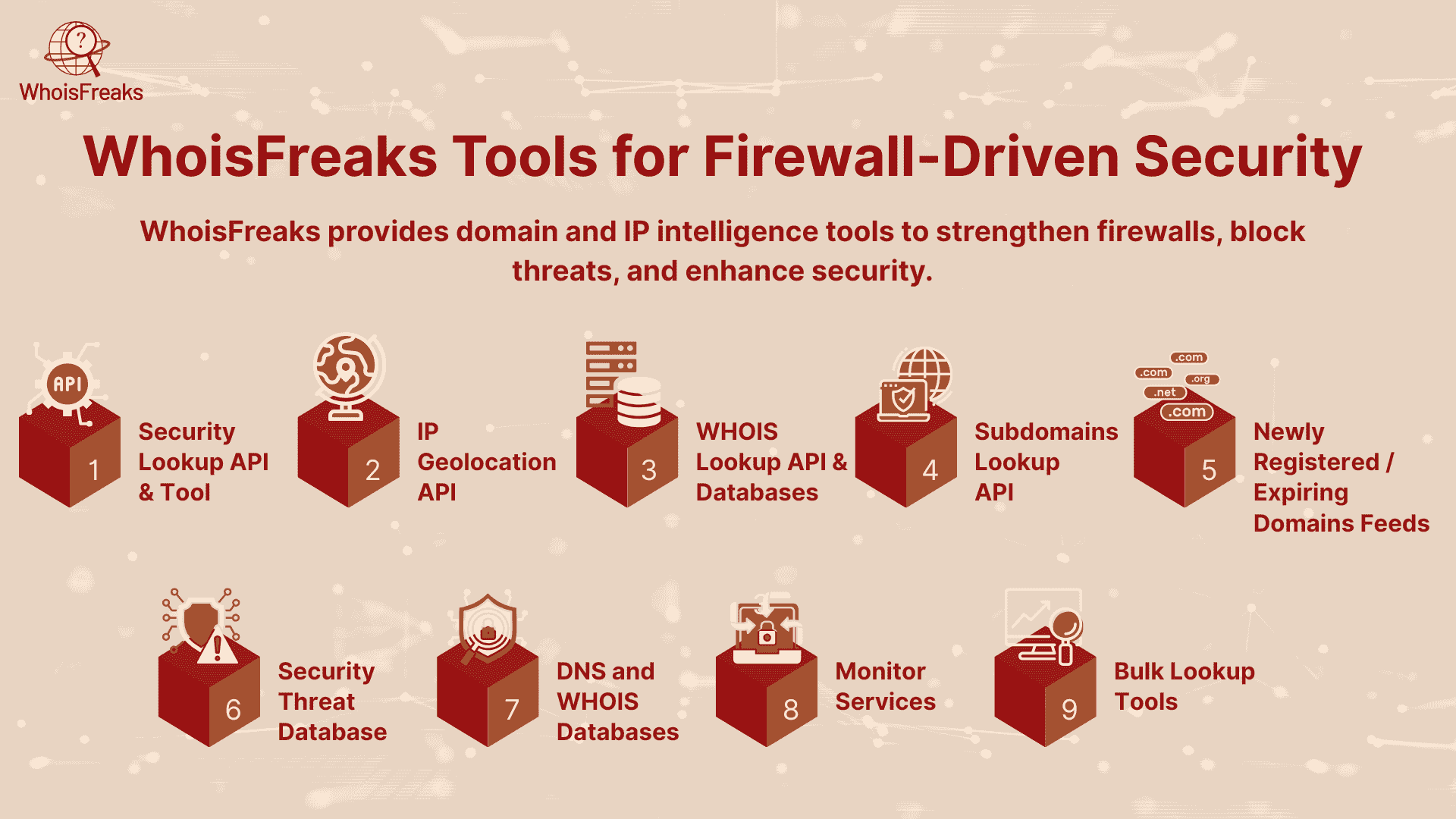
WHOISFreaks can give a domain ownership and registration information to make it easier to know about suspicious domain before they can cause any harm. Integrating the WHOISFreaks information with firewalls, organizations can:
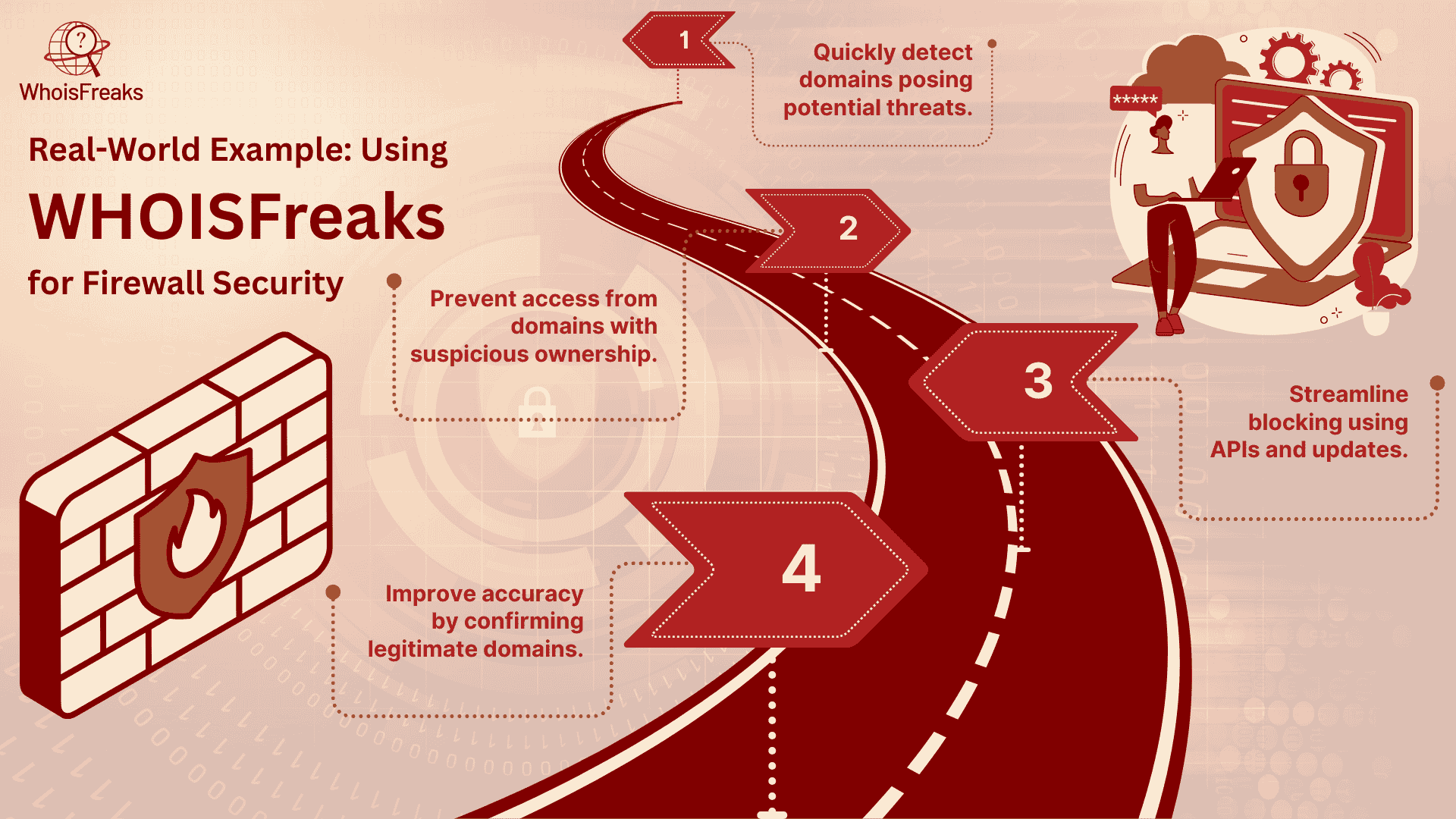
This proactive approach ensures that firewalls aren’t just reactive but actively preventing attacks before they happen.
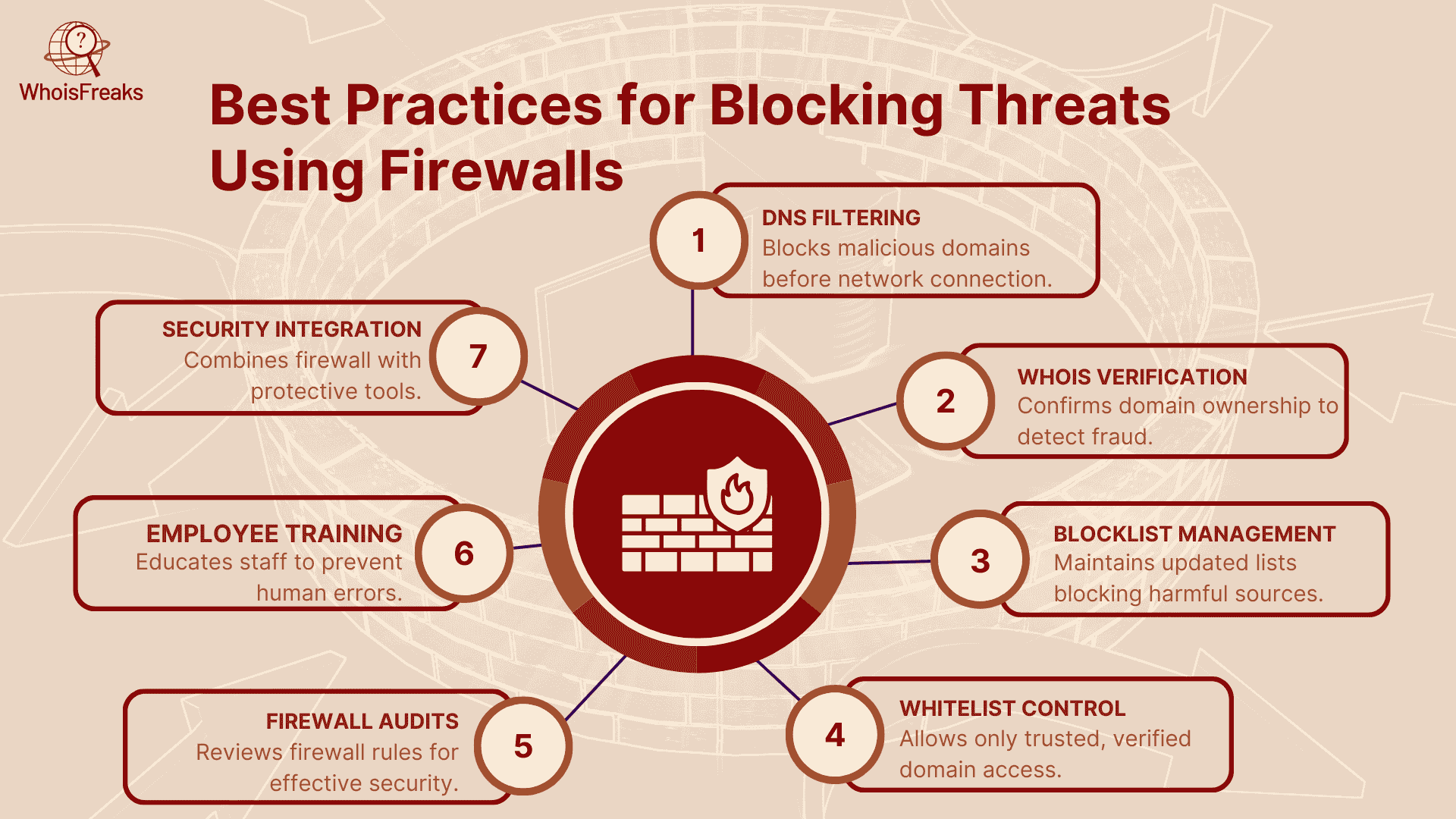
Combining firewalls with DNS filtering, WHOIS checks, and intelligence feeds strengthens protection. These practices help block malicious domains before they cause harm.
Cyber threats are not slowing down in fact; they are becoming more advanced every day. Newly registered domains, often using a new domain name, remain one of the most common tools for cybercriminals to spread malware, launch phishing campaigns, and steal sensitive data.
Firewalls present the initial firewall of security against these attacks and serve to thwart off such attacks. Knowledge of the malicious activities would help you block the registered domains and everman, new threats should be monitored and applied best practices that would go a long way in ensuring that you do not fall victims.
Tools like WHOISFreaks provide an additional layer of security by helping you verify domain ownership, offer suggestions, and identify suspicious domains before they become active threats.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Learn how to prevent subdomain takeover with essential strategies and best practices. Protect your online assets—read the full guide now!
8 min read