
Defending Against DNS Flood Attacks: Leveraging WhoisFreaks Tools for Security

By Qasim
Posted on October 27, 2025 | 10 min read
Domain Name System (DNS) is the phone book of the Internet. Every time we enter a domain name in a browser, DNS servers translate the human‑readable address to a numerical IP. Because of its central role, DNS is a tempting target for attackers, especially when legitimate requests cannot be distinguished from malicious traffic. One particularly disruptive method is the DNS flood attack a form of Distributed Denial of Service (DDoS) that overwhelms DNS infrastructure so legitimate queries cannot be resolved. These attacks can leave websites unreachable, degrade performance for entire networks, and act as smokescreens for other malicious activities.
This blog illustrates DNS flood attacks, explains common variants such as reflection, amplification, and “water torture,” and provides concrete mitigation strategies. It also showcases how WhoisFreaks, a provider of domain and IP intelligence services, can empower defenders with real‑time data monitoring and threat classification tools. By combining general best practices with WhoisFreaks' APIs and monitoring services, cybersecurity professionals and general readers can gain actionable knowledge to detect and combat DNS floods.
Understanding DNS Flood Attacks
DNS is similar to a hierarchical directory: when a user queries screenshotapi.net, the query will go through recursive resolvers and authoritative servers to get an IP address. DNS is fast and reliable but being stateless and UDP-based makes it an easy target of abuse. Attackers take advantage of this by flooding server resources with waves of queries that exhaust server resources, overload network links or caches with useless responses.
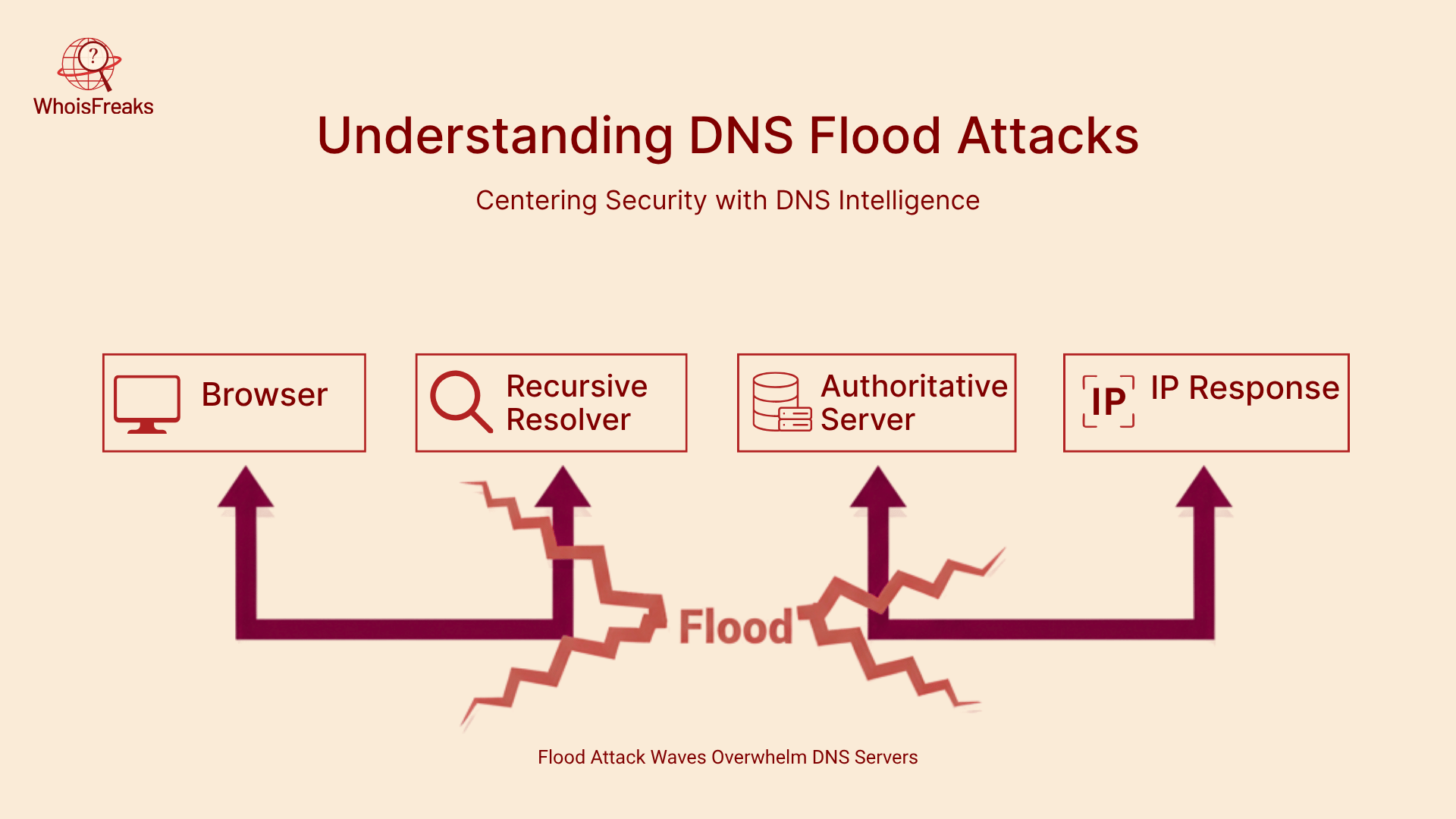
What Is a DNS Flood Attack?
A DNS flood attack is a DDoS attack in which the attacker sends a large amount of DNS queries to the target servers. Rather than having one host, the opponents organize botnets networks of infected computer systems that create millions of queries in distributed sources. Since every request appears to be good, the server tries to serve them, overloading the CPU, memory and bandwidth. Legitimate users receives slow response or no response at all. Attackers can also spoof IP addresses, and it is hard to block traffic on the basis of the source alone.
Types of DNS Flood Attacks
DNS floods encompass several sub‑attacks. Understanding these variants aids detection and informs mitigation.
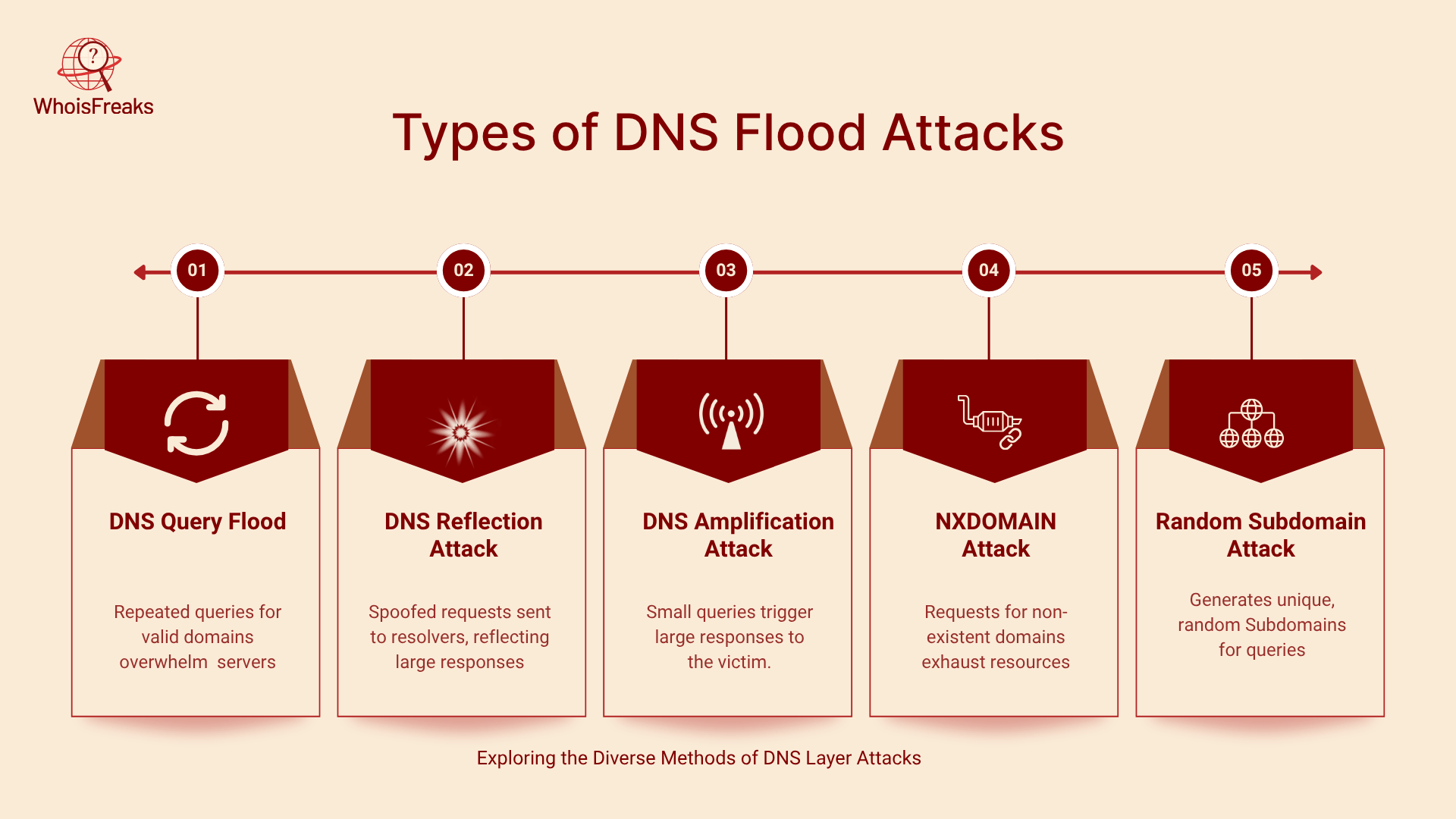
- DNS Query Flood: Attacker sends normal DNS requests to the authoritative servers. The requests are directed to valid or random domains; the enormous volume of requests blocks the server from responding.
- DNS Reflection Attack: It's a type of attack where the attackers spoof the IP address of the victim when requesting to open DNS resolvers. The spoofed address is responded to by the resolver, which sends traffic back to the victim. DNS attacks are also amplification attacks, as the response in DNS is frequently larger than the query. The incident with Spamhaus in 2013 was based on DNS reflection to 300 Gbps.
- DNS Amplification Attack: Attackers use open resolvers and misconfigured servers that send large payloads to small queries. Attackers increase their bandwidth by making large responses (like requests to DNSSEC keys or ANY queries) which are caused by the request. A query is capable of producing tens of times more data, clogging the connection of the victim.
- NXDOMAIN Attack: Sometimes referred to as pseudo-random subdomain attacks or water torture, where queries are sent to non-existent domains or randomly selected subdomains of a valid domain. DNS servers are required to search recursively for each subdomain and eventually give an NXDOMAIN (non-existent domain) response. The flood of fake queries drains the server resources and contaminates caches. Since the queries appear randomly and at a low rate, one by one, they are more difficult to detect.
- Random Subdomain Attack: Similar to NXDOMAIN, but instead of flooding the authoritative server with requests to various subdomains of the target domain, it floods the authoritative server with requests to different subdomains of the target domain. The query for each subdomain does not use a cache since the subdomain has not been encountered before. This is both CPU and memory-intensive, and may also overstretch upstream recursive resolvers.
Why Attackers Use DNS Floods
DNS floods are attractive because they require minimal resources relative to the damage they inflict. Attackers may use them to generate malicious traffic that overwhelms defenses.
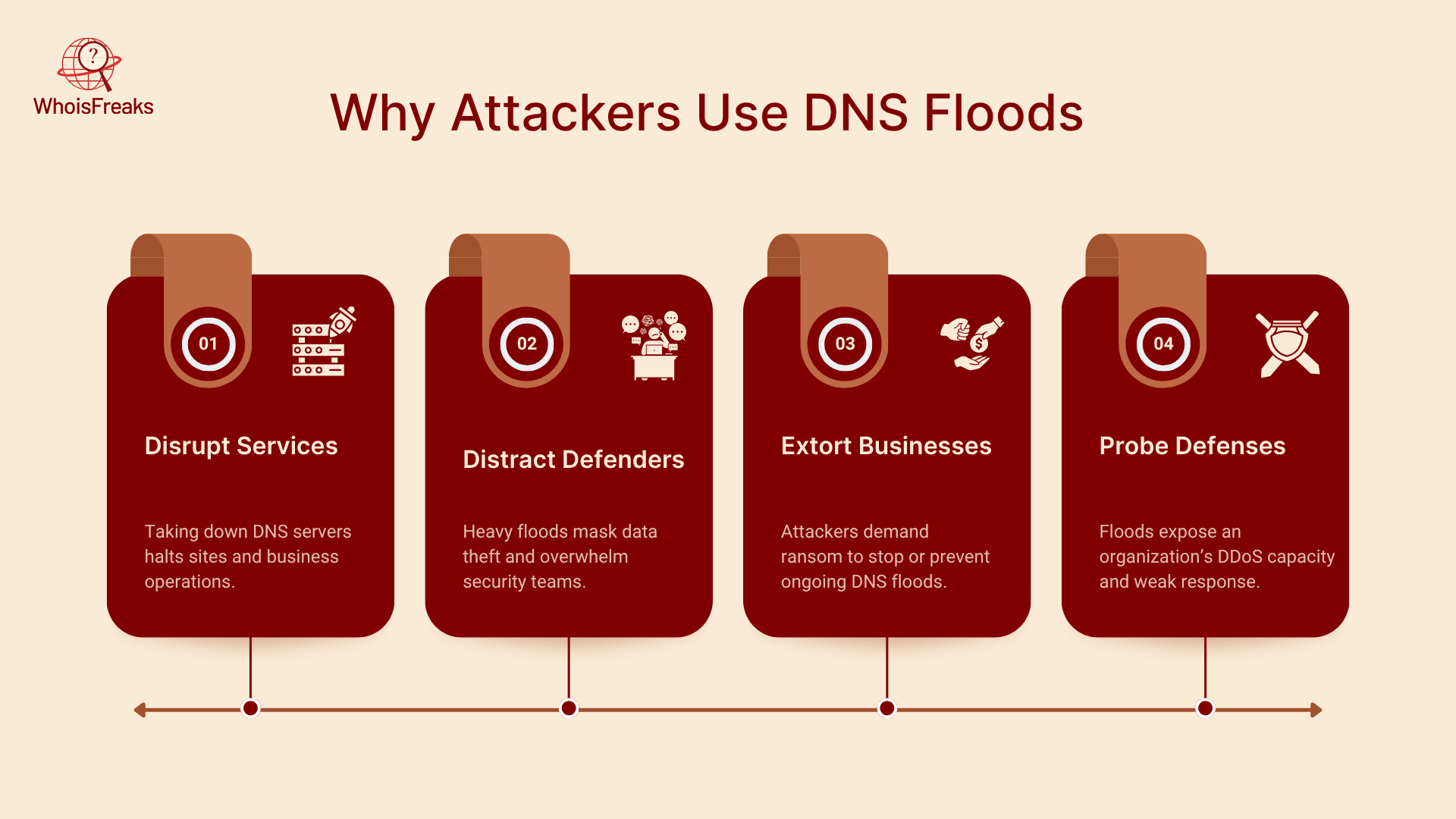
- Disrupt Services: Taking down DNS servers makes websites inaccessible and can cripple business operations.
- Distract Defenders: A flood can conceal data theft or malware distribution by overwhelming security teams.
- Extort Businesses: Some attackers threaten sustained DNS floods unless victims pay ransoms.
- Probe Defenses: Floods help adversaries learn about an organization’s DDoS protection, capacity and response.
The distributed nature of these attacks means organizations need layered defenses combining network, DNS, and application‑level measures.
Effects of DNS Flood Attacks
A successful DNS flood has cascading consequences:
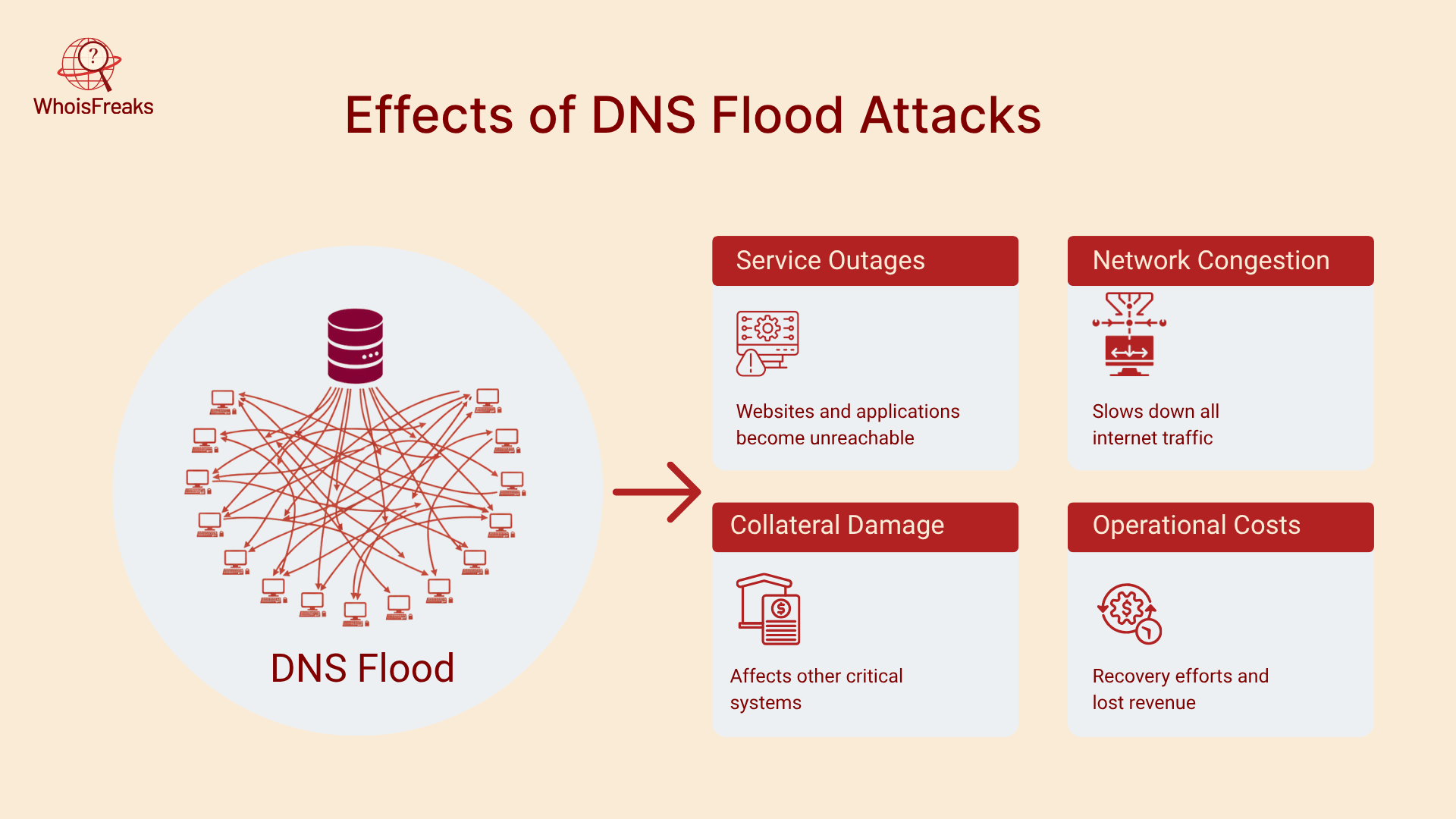
- Service Outages: Websites and services become unreachable, leading to downtime and lost revenue. Check Point notes that slow loading times, disrupted services, and reputational damage are common outcomes.
- Network Congestion: Flooding saturates network links, causing latency and packet loss not only for DNS but for all services using the same infrastructure.
- Collateral Damage: Floods can degrade performance for upstream resolvers and networks, harming third parties.
- Operational Costs: Organizations may need to over‑provision resources, purchase DDoS mitigation services, or suffer revenue loss due to downtime.
Mitigation Strategies
There is no single silver bullet to stop DNS floods. Effective defense layers several techniques across the network and DNS infrastructure.
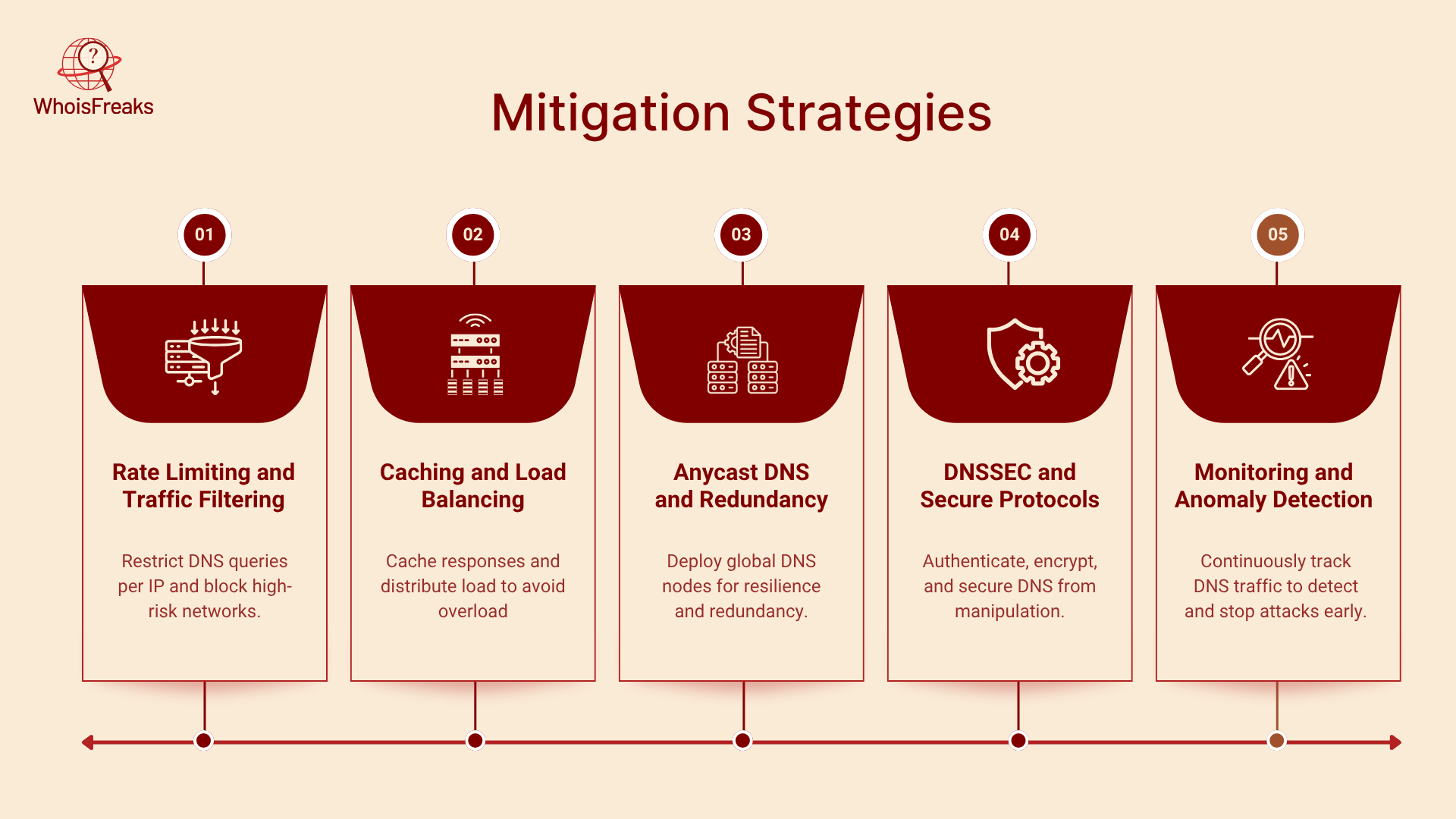
1. Rate Limiting and Traffic Filtering
Introduce DNS rate limiting in order to limit the number of queries served to a single IP or a subnet within a time frame. Water torture attacks can be reduced through rate limiting, which will drop too many queries. The use of rate limiting together with Access Control Lists (ACLs) can serve to prevent traffic in high-risk areas or bad networks. DNS firewalls and intrusion detection systems are capable of filtering suspicious patterns like repeated requests on non-existent domains.
2. Caching and Load Balancing
Caching solved queries saves the workload on authoritative servers and alleviates the impact of multiple queries. The traffic is spread and no single DNS server is overloaded when load balancing is implemented with more than one DNS server. DNS caching is especially resistant to amplification attacks since the response can be served locally without having to communicate with upstream servers. Nevertheless, caching does not prevent NXDOMAIN floods as queries are sent to random subdomains that are not cached.
3. Anycast DNS and Redundancy
Anycast enables the various DNS servers in different geographic areas to share a common IP address. Traffic routing is automatic to the closest or least congested node, enhancing resilience. It works by implementing DNS infrastructure on more than one provider and network path to provide redundancy and capacity to absorb floods. Having a mixture of DNS providers will also minimize the chances of single-point failure and make the work of an attacker more difficult.
4. DNSSEC and Secure Protocols
DNS Security Extensions (DNSSEC) authenticate DNS responses and prevent cache poisoning. While DNSSEC does not prevent floods directly, it stops attackers from injecting malicious responses and can mitigate some amplification vectors by rejecting unsigned responses. Similarly, protocols like DNS over TLS (DoT) and DNS over HTTPS (DoH) encrypt queries, preventing eavesdropping and tampering. However, encryption may complicate traffic inspection and should be balanced with monitoring needs.
5. Monitoring and Anomaly Detection
Watch DNS traffic constantly to identify abnormal spikes, anomalous query patterns, or spikes in NXDOMAIN responses. Early alert will enable security teams to institute mitigation measures before an attack leads to outages. Logs across the networks can be correlated, and scrubbing or rate limiting can be triggered by logs by DDoS protection services or Security Information and Event Management (SIEM) systems. Catchpoint suggests the distribution of DNS services and software maintenance, yet also notes that monitoring is a crucial component in order to draw the difference between legitimate surges and attacks.
Using WhoisFreaks Tools to Enhance Your DNS Defense
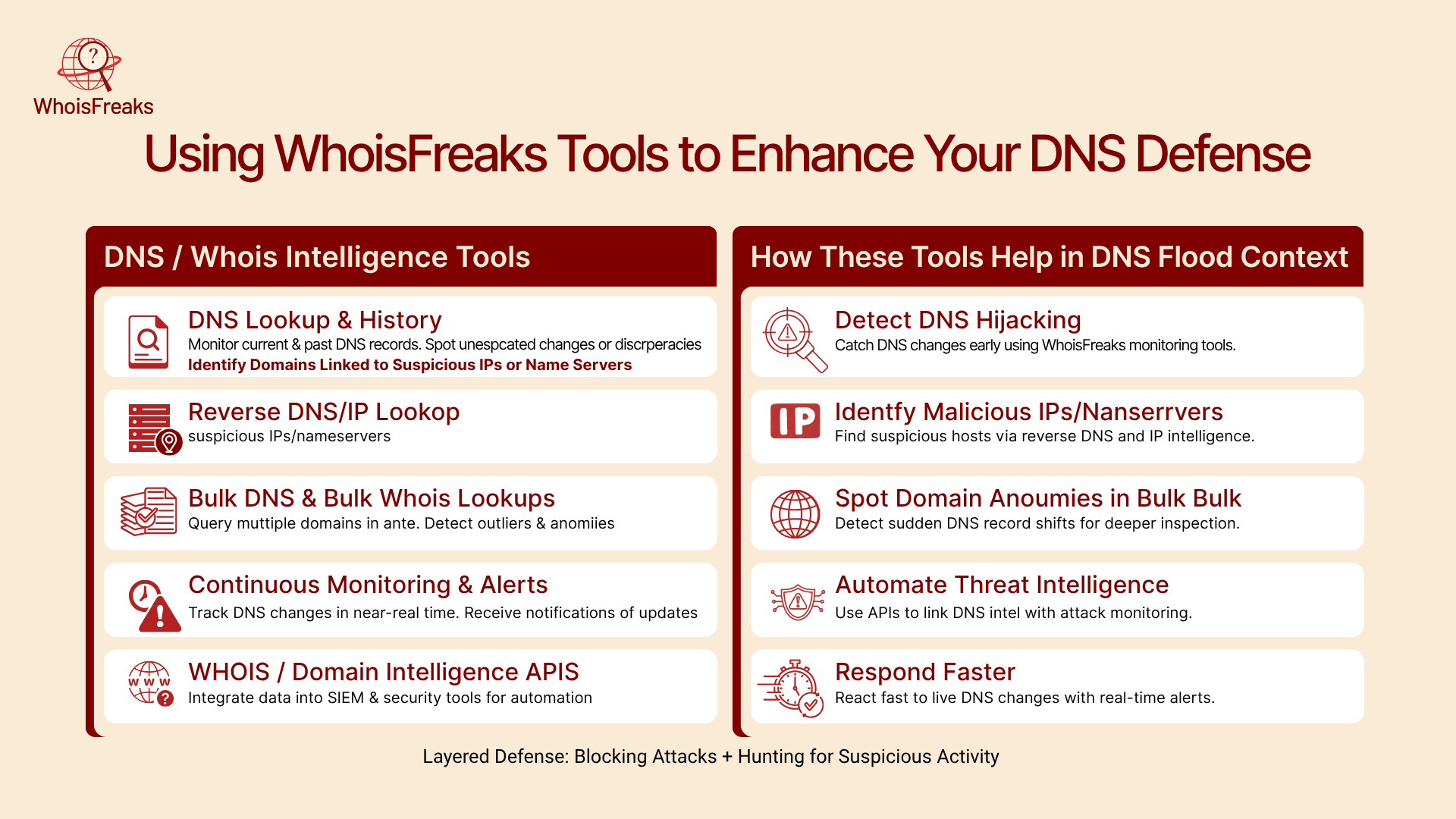
Security is not just about protecting the server; it’s also about visibility and early warning. WhoisFreaks offers domain and DNS intelligence tools that help you monitor, detect anomalies, and respond faster. Below are features that can support your DNS flood defense strategy, especially against threats from compromised devices.
DNS / WHOIS Intelligence Tools from WhoisFreaks
- DNS Lookup & DNS History Tools: These let you see current and past DNS records for domains. If an attacker hijacks or redirects DNS, these tools help you spot unexpected changes or discrepancies.
- Reverse DNS / Reverse Lookup: You can check which domains are tied to a particular IP or name server. This helps you identify if a flood is linked to suspicious domains.
- Bulk DNS & Bulk WHOIS Lookups: For organizations managing multiple domains, WhoisFreaks lets you query many domains at once. You can compare their DNS records and detect outliers.
- Continuous Monitoring & Alerts: WhoisFreaks constantly crawls DNS and records changes as they occur. You can set alerts to receive notifications of unexpected updates.
- WHOIS / Domain Intelligence APIs: You can integrate WhoisFreaks’ data into your security tools (SIEM, dashboards) and automatically cross-check domain attributes.
How These Tools Help in the DNS Flood Context
- Detect DNS Hijacking Before It’s Used: If attackers plan to combine flood attacks with DNS redirection, WhoisFreaks’ DNS history and monitoring tools can help you catch unauthorized changes quickly.
- Identify Malicious Nameservers or IPs: Reverse DNS and IP intelligence can help you find suspicious hosts participating in an attack, or common infrastructure used by attacking domains
- Spot Domain Anomalies in Bulk: If one domain suddenly shows a change in records while all others remain stable, that’s a red flag worth deeper investigation.
- Automate Threat Intelligence Feeds: With APIs, you can incorporate WhoisFreaks domain intelligence into your monitoring stack and cross-correlate attack events with DNS anomalies.
- Respond Faster: Because WhoisFreaks tracks changes almost in real time, you can be alerted to DNS record changes during an ongoing attack and respond (rollback, reconfigure, block) more quickly.
By combining these domain intelligence capabilities with the technical DDoS defenses listed earlier, you create a layered defense that not only blocks attacks but also hunts for suspicious activity.
Real-World Cases of DNS / DNS-Flood / DDoS Attacks
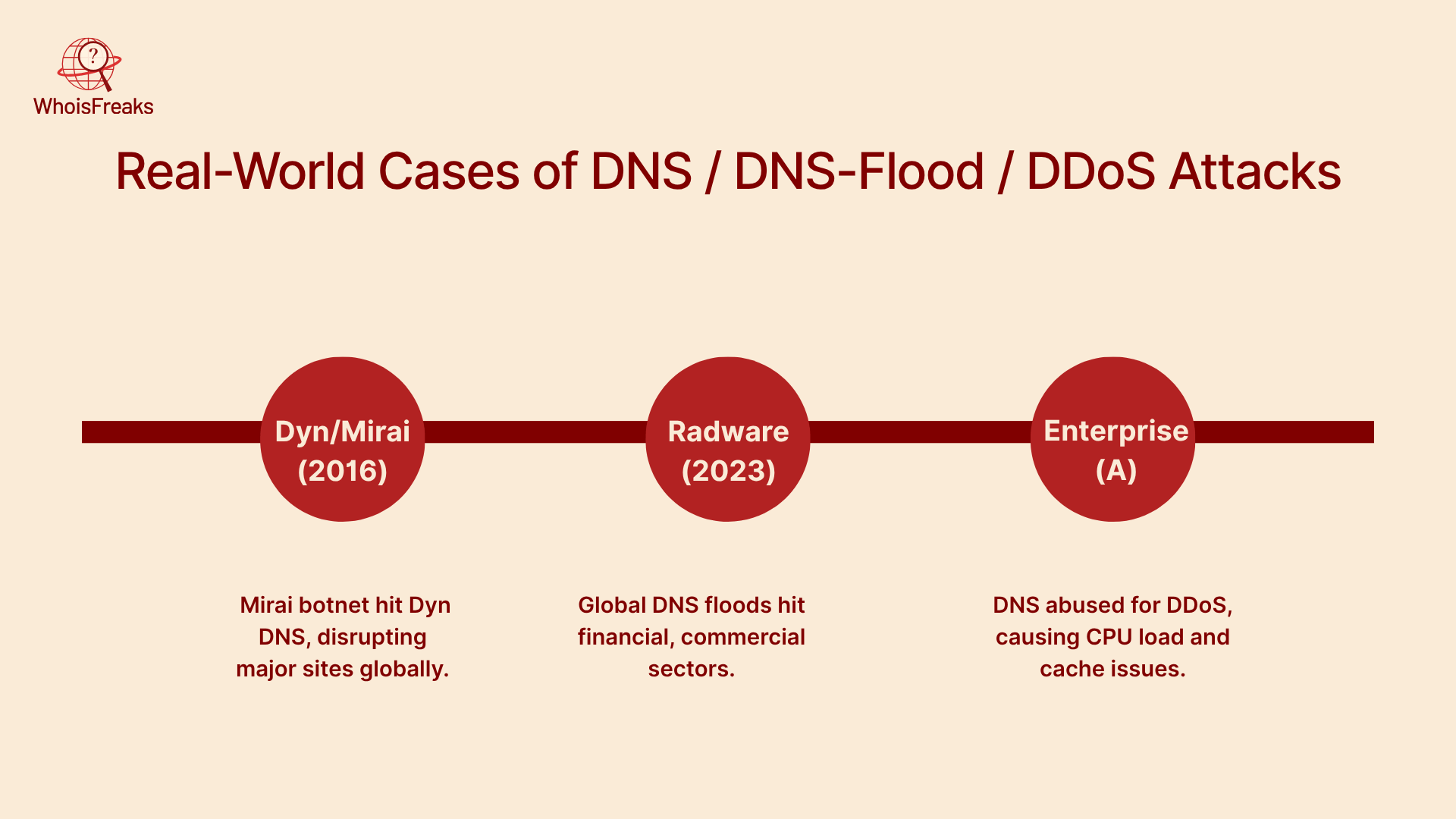
1. Dyn / Mirai DDoS Attack (2016)
It is also one of the most well-known DNS-based attacks. In October of 2016, the Mirai botnet was used to have an enormous DDoS attack on Dyn, a DNS infrastructure. The DNS services of Dyn were crippled by the flood, and dozens of large websites (Twitter, Spotify, Reddit, etc.) were unavailable in parts of North America and Europe for hours.
The effect was far-reaching due to the fact that Dyn did DNS resolution on numerous high-profile domains. This attack demonstrates that it is possible to take down massive parts of the Internet through attacking DNS systems.
2. Massive DNS Floods Detected by Radware
In 2023, security provider Radware reported multiple DNS flood campaigns targeting financial and commercial organizations globally.
These attacks used high volumes of DNS queries to overwhelm DNS servers. Radware’s analysis showed patterns and techniques in those attacks, helping defenders understand how attackers try to disrupt DNS services.
3. Enterprise DNS DDoS / DNS server abuse (Case Study: "Enterprise A")
One case study describes how a large enterprise’s DNS servers were used as part of a DDoS process. Attackers sent high volumes of DNS queries (some for domains not even belonging to the enterprise), causing CPU load and cache eviction in their DNS servers.
This shows how even DNS systems can be misused by attackers to amplify or redirect traffic, adding load and instability to the infrastructure.
Conclusion
DNS flood attacks can bring even large and secure websites to a sudden stop by overwhelming their DNS servers with fake traffic. Real-world incidents like the Dyn DNS attack in 2016 proved how damaging these floods can be taking down major platforms like Twitter, Spotify, and Reddit for hours.
To defend against such attacks, organizations need more than just a firewall. They need visibility, monitoring, and fast intelligence on what’s happening across their DNS infrastructure. Regular monitoring, traffic analysis, and quick threat detection play a key role in keeping services online and reliable.
This is where WhoisFreaks' tools such as DNS Lookup, Historical DNS Lookup, and DNS Monitoring APIs can make a huge difference. They help you keep track of every DNS change, monitor suspicious activity, and quickly identify malicious IPs or domains targeting your servers.
Don’t wait for an attack to expose your weaknesses. Strengthen your DNS defense today with WhoisFreaks' advanced monitoring tools and stay one step ahead of cyber threats.
FAQs
1. How can DNS flooding be prevented?
2 . What are the signs of DNS hijacking?
3. Is DDoS attack illegal?
Related Posts

Understanding DNS Poisoning: Risks and Prevention Strategies
Discover essential insights on DNS poisoning and learn practical steps to safeguard your online presence. Read the article for vital protection tips.
10 min read

What is the Purpose of DNS Server? Understanding Its Role and Benefits
Discover the essential role of DNS servers in internet functionality and learn how they enhance your online experience. Read the article for insights.
9 min read