

By Qasim
Posted on November 07, 2025 | 10 min read
The Domain Name System (DNS) is the internet phonebook critical to the DNS infrastructure. It converts human-understandable domain names (such as that of google.com) into numerical IP addresses, which is used by computers. When you enter a name of a website, your computer requests a DNS resolver to provide the IP address of the same. The resolver caches answers in a time limit (the TTL) so as to make lookups faster. This is like a local address book: once an entry is saved, it can be reused until it expires, making browsing faster.
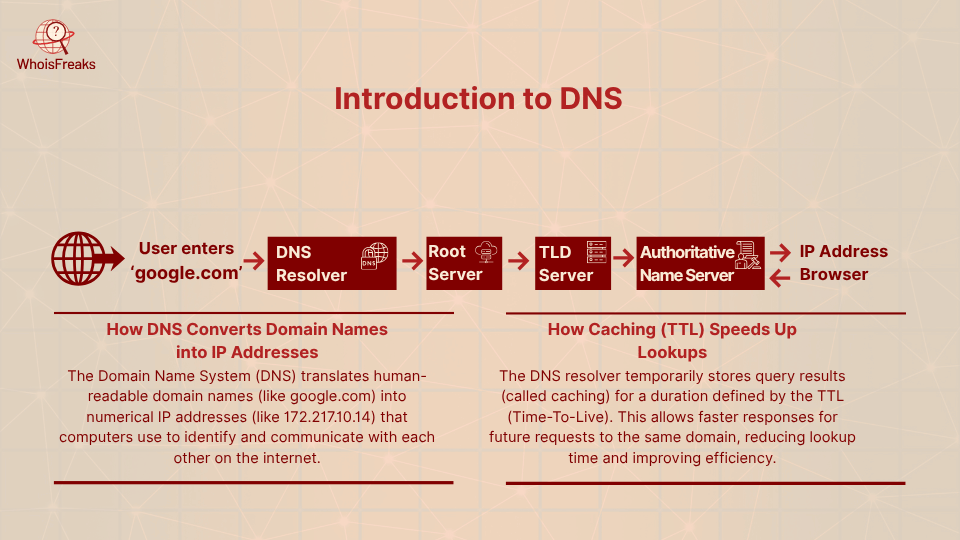
If the resolver doesn’t have the answer cached, it will query DNS root servers and follow the chain of authority (top-level domain servers, then the domain’s own name servers) to find the IP. Each step’s result can then be cached for subsequent queries. Caching makes DNS efficient, but it also means that if a wrong answer is inserted, it will stay in place until its TTL runs out. Normally there is no built-in verification of cache data, so a bogus response can go unnoticed until it is either overwritten or expired
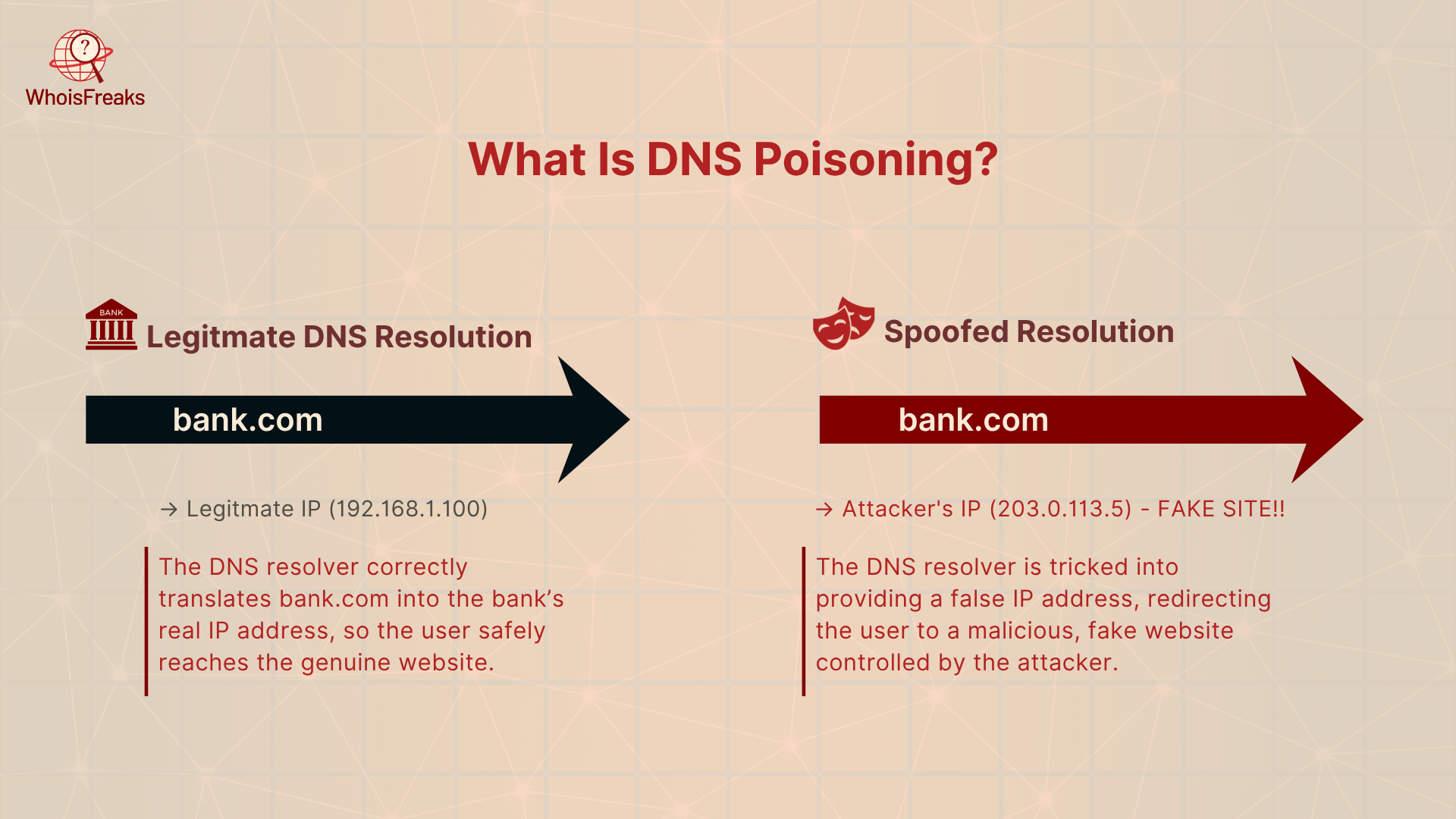
DNS poisoning (also called DNS spoofing or cache poisoning) is an attack that includes DNS spoofing attacks which corrupt the information in a DNS cache so that queries return the wrong IP address. In other words, attackers inject false DNS records into a resolver’s cache. Cloudflare describes this as “entering false information into a DNS cache” so that users are directed to the wrong websites. In effect, DNS poisoning tricks the system into treating a malicious IP as the legitimate address for a real domain.
For example, you might think you’re visiting your bank’s website, but end up on a fake site designed to steal your login details. In this scenario the attacker has forced the DNS resolver to cache an incorrect A record (the bank’s site IP). From then on, anyone querying the bank’s domain is sent to the attacker’s server instead of the real bank’s. In effect, people innocently following the usual URL are secretly connected to the attacker’s server.
DNS poisoning is particularly dangerous since it is many times undetected. The browsers can still display the right URL and the page can appear normal with some minor differences, which may conceal spoofing attacks . The fraud may be identified only through close inspection or through warnings of the browsers (SSL certificate is not valid). When a victim realizes that something is amiss, the attacker can have stolen credentials or even planted malware.
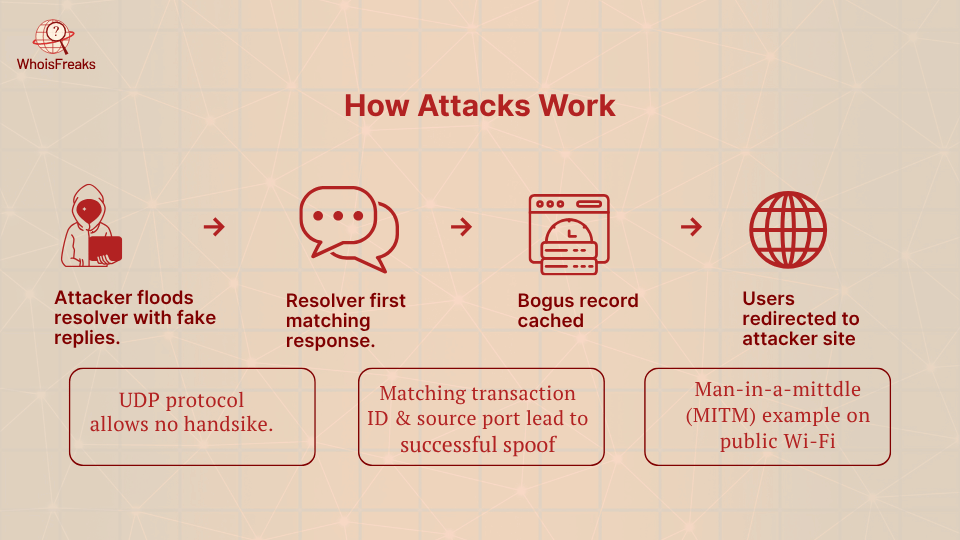
There are different ways through which attackers poison DNS caches. One of the widely used methods is to overwhelm DNS server software by flooding a resolver with bogus DNS responses when it issues a query. The attacker remodels the response to appear as one that was sent by an authentic DNS server. DNS queries normally operate over the UDP protocol without a handshake, and therefore the resolver can accept the first matching answer that it gets. When the spoofed response has the incorrect IP and corresponds to the query transaction ID and source port, the resolver will store the bogus record.
The other technique is a man-in-the-middle attack. As an illustration, an attacker can spoof a DNS query on an open Wi-Fi hotspot and respond instantly with a spoofed response. Instead, the attackers can use the bugs or the compromised DNS servers to inject the bad records. Whichever way, when a fake entry has been logged in the DNS cache, it will stay there until the TTL has expired or the cache is cleared by hand. All customers accessing the resolver that is poisoned will be redirected to the rogue site at that time, allowing attackers to redirect traffic .
In practice, this can affect many users at once without any change to the domain’s official settings. Modern DNS servers randomize source ports and use large transaction IDs to make spoofing harder, but resolvers and network caches (including those on home routers or at ISPs) can still be targets if not properly protected.
The consequences of DNS poisoning are severe. Victims may be sent to fake websites that steal credentials or deliver malware. Traffic can be diverted for phishing, man-in-the-middle eavesdropping, or drive-by downloads. In short, a DNS poisoning attack enables credential theft, malware infections, and a loss of user trust. Even well-known brands can suffer if their customer traffic is hijacked.
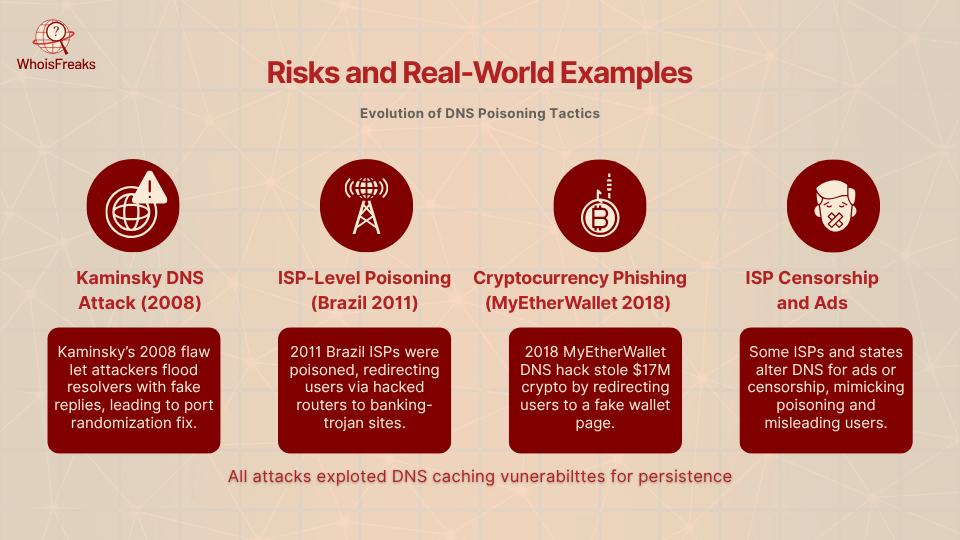
Security vulnerability in the DNS presented by a security researcher called Dan Kaminsky resulted in a disastrous ease in poisoning. With a large scalability, an attacker could add spoofed replies to the cache by flooding a resolver with spoofed replies. The discovery by Kaminsky provoked the need to fix (such as randomization of ports) the problem urgently but demonstrated that core DNS assumptions were vulnerable.
In late 2011, Kaspersky found massive DNS cache poisoning of Brazilian ISPs. Attackers hijacked DNS queries so users were sent to malicious sites. One campaign tricked users into downloading a banking Trojan disguised as a “Google Defense” tool. Alarmingly, attackers even hacked routers or modems to change their DNS settings. As a result, when employees tried to visit normal websites, the compromised routers redirected them to malware-laden pages.
DNS poisoning was used on the Ethereum wallet MyEtherWallet. The visitors visiting the site were automatically redirected into a fake page where their keys were stolen. The fraud went undetected and over 17$ million cryptocurrency was stolen. As it is demonstrated in this case, even the high-value services and tech-savvy users can fall victim to the attack provided that the DNS records are altered.
Some ISPs and governments have deliberately altered DNS records for censorship or advertising. While not criminal attacks in the traditional sense, these actions function exactly like poisoning. In each case, users end up on unintended sites. Such examples underline that any unexpected DNS change must be watched, even “legitimate” alterations can disrupt users.
In all these examples, legitimate domain names were mapped to malicious IP addresses without users realizing it. By the time any warning appears (like a certificate alert or an anomalous pop-up), the attackers may already have captured data or installed malware.
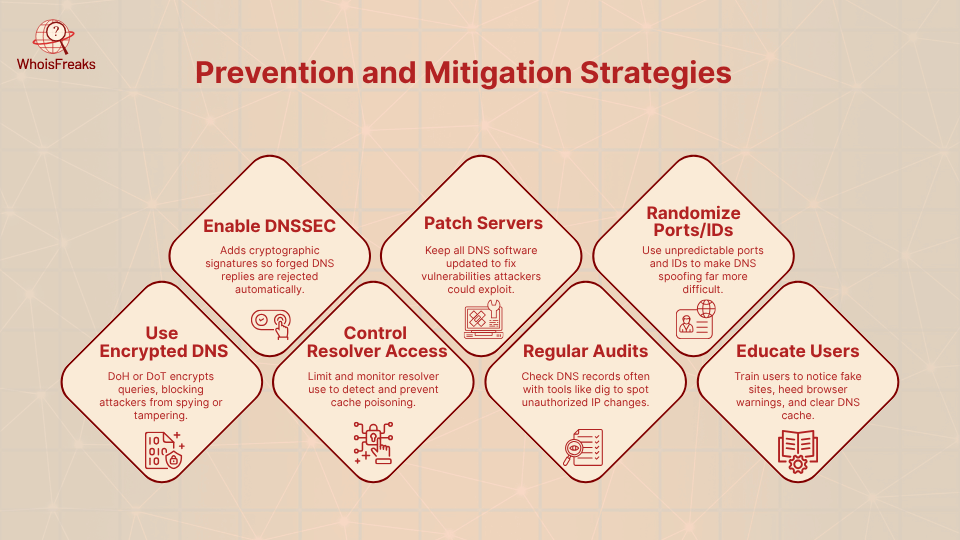
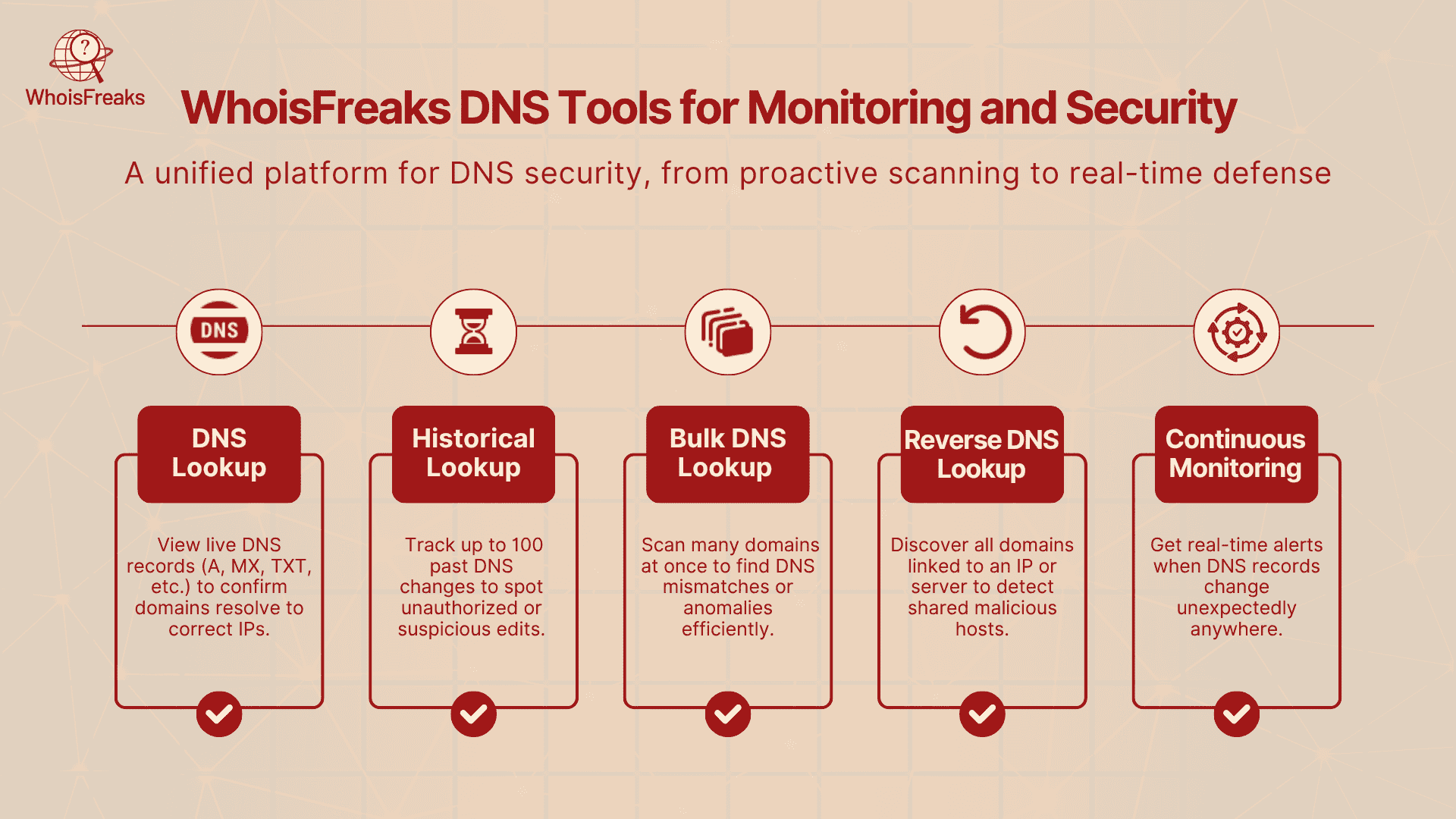
WhoisFreaks boasts over 12 billion DNS records across 1,500+ top-level domains (TLDs). WhoisFreaks offers domain and DNS intelligence tools to help detect or prevent DNS issues:
DNS poisoning is one of those silent attacks that can cause serious damage before anyone even notices. To counter this threat, measures to prevent DNS poisoning are essential as it allows hackers to secretly redirect users to fake or harmful websites putting data, reputation, and trust at risk. Real-world incidents like the MyEtherWallet breach and large-scale ISP attacks show how dangerous this threat can be.
The positive side of the situation is that these attacks on domain name system security are preventable through the appropriate awareness and equipment. With DNSSEC, periodically verifying your DNS records, maintaining systems and tracking DNS activity are viable methods of ensuring that you have not been compromised.
To simplify this process, you can use such tools as DNS Lookup, Historical DNS Lookup, and DNS Monitoring by WhoisFreaks that will allow you to monitor any suspicious activity in the DNS records of your domain. Such tools provide visibility to you and early warnings in case anything goes amiss to take an action before it is too late.
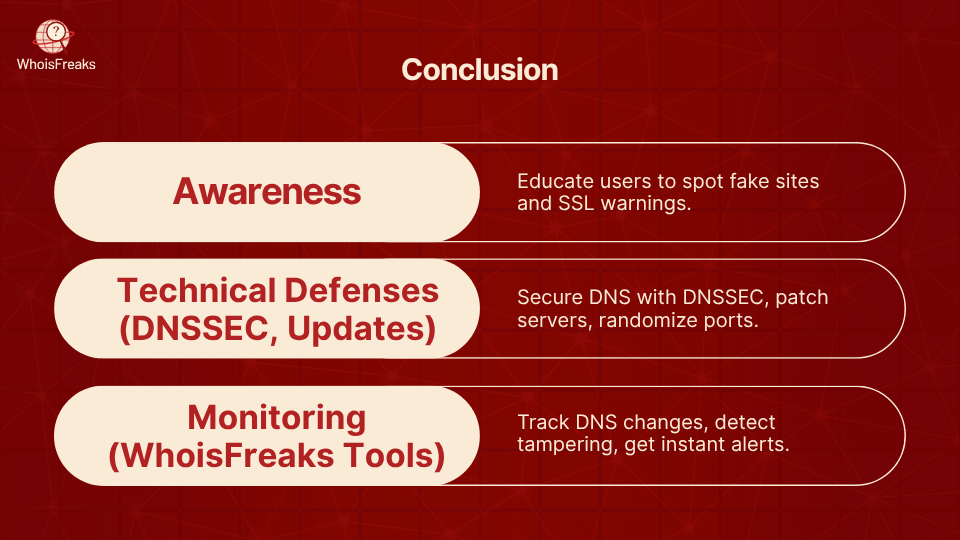
Stay ahead of attackers and secure your domains today with WhoisFreaks' DNS monitoring tools.
Explore WhoisFreaks DNS Tools

Learn how a DNS flooder can threaten your network security and discover practical measures to protect your systems. Read more to safeguard your network.
10 min read

Discover the essential role of DNS servers in internet functionality and learn how they enhance your online experience. Read the article for insights.
9 min read