

By Qasim
Posted on May 09, 2025 | 9 min read
Phishing emails have become one of the most frequent online dangers. They are crafted to deceive you into sharing personal information, such as passwords, bank details, or other sensitive data. These emails can seem legitimate and trustworthy, making it tricky to figure out whether they’re genuine or not. But don’t worry with some basic knowledge and awareness, you can easily spot them. In this blog, we’ll share six simple tips to help you recognize phishing emails and browse the internet more safely.
Phishing is a type of online scam where attackers pretend to be trusted people or organizations to trick you into clicking dangerous links or downloading harmful attachments. Their main goal is to steal your personal info, like login credentials, passwords, bank details, or other sensitive stuff. Phishing emails are made to look real, so they can be tricky to spot without knowing what to look for.
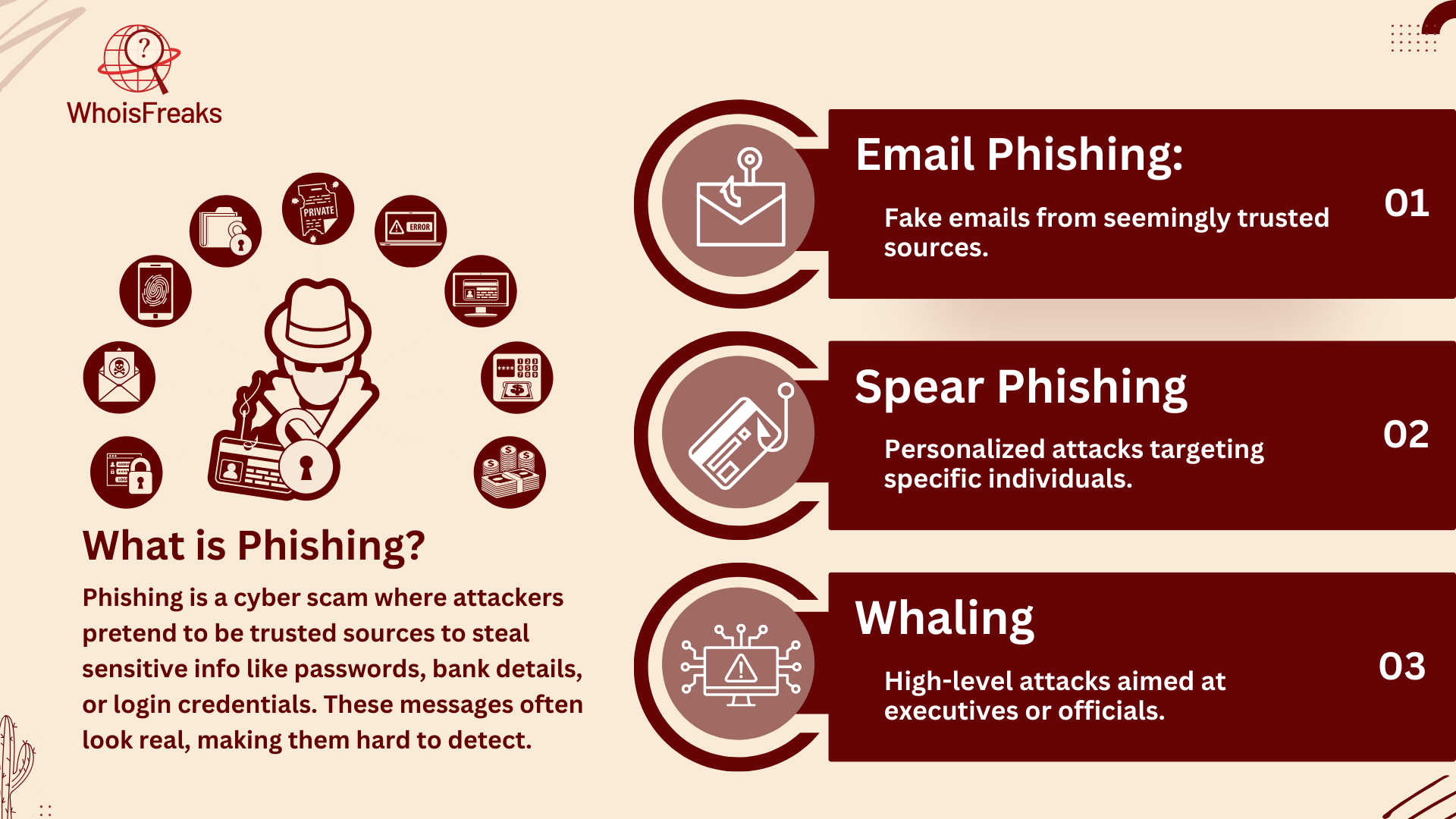
Phishing can show up in different ways:
Phishing attacks, especially phishing emails, are becoming more common these days. With billions of emails being sent and received every day, it’s getting harder to tell which ones are real and which ones might be trying to trick you. Phishing emails are getting smarter, making it tough for people to figure out which emails are safe, and which ones could steal your personal information. This makes it even more important to stay alert and know how to spot these suspicious emails and fake emails in your inbox.
Phishing is dangerous because it takes advantage of how we think and react, often leading to identity theft. These emails often make you feel like you need to act fast or get curious, pushing you to make quick decisions without fully thinking through the risks. Some phishing emails might include:
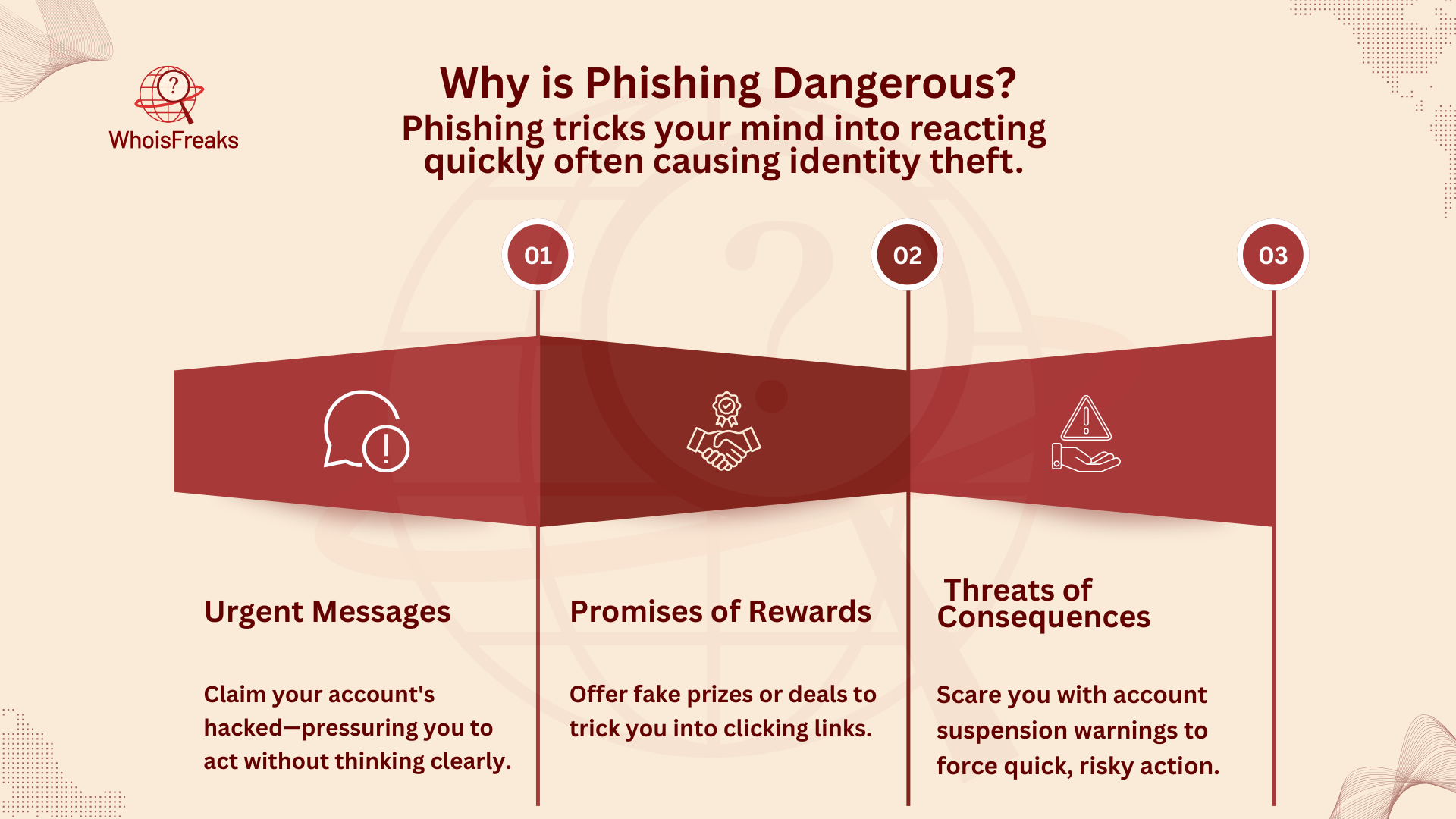
These tricks work well because they trigger emotional reactions, making you more likely to make hasty decisions that could expose your personal information.
Phishing attacks are getting smarter as hackers use better tricks to fool people. One way they do this is by spoofing email addresses, making them look like they come from trusted sources. This makes it harder to spot fake emails and recognize suspicious activity. Hackers also use social engineering, which means they craft emails that mention personal details, like recent purchases or public information, to make the message seem real. Some even pretend to be important people, like government agencies or law enforcement, to scare people into responding. Social media has made it even easier for attackers to get information, helping them make their emails more convincing. Because of all these tricks, it’s becoming harder to tell the difference between real and fake emails, so we need to stay extra careful.

Phishing emails usually have at least one of these warning signs:
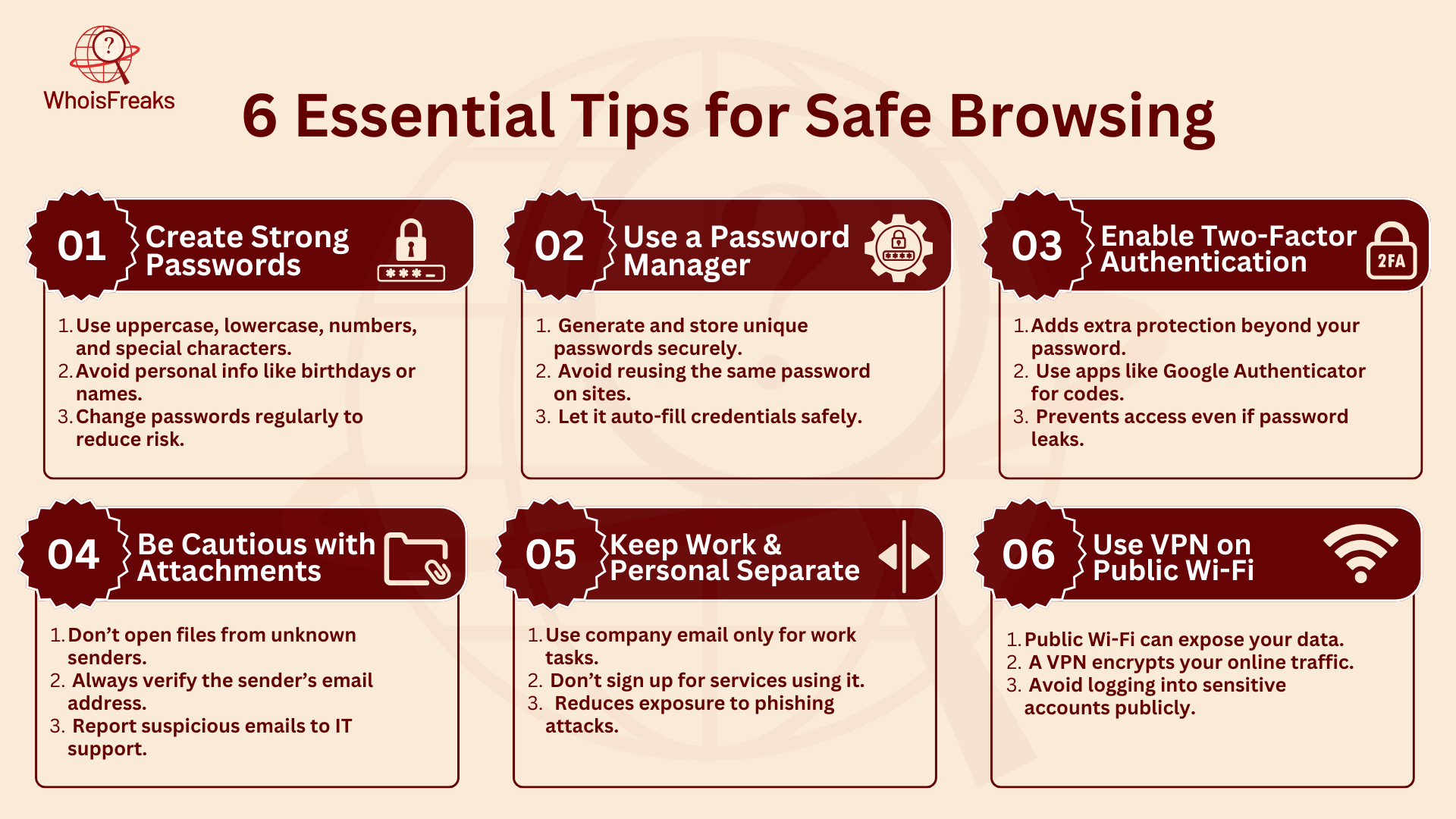
When it comes to email security, a strong password is essential for keeping your account safe. A weak password won't protect your email or sensitive company data. Make sure your password includes a mix of upper-case and lower-case letters, numbers, and special characters. Avoid using common words from a dictionary or personal details, such as payment information, phone numbers, birth dates, anniversaries, pets’ names, or home addresses, as they can be easily guessed. Also, avoid using simple letter/number swaps, like replacing "o" with "0." Instead, use longer phrases that are harder to guess. Make sure to update your password regularly to reduce the chances of a security breach.
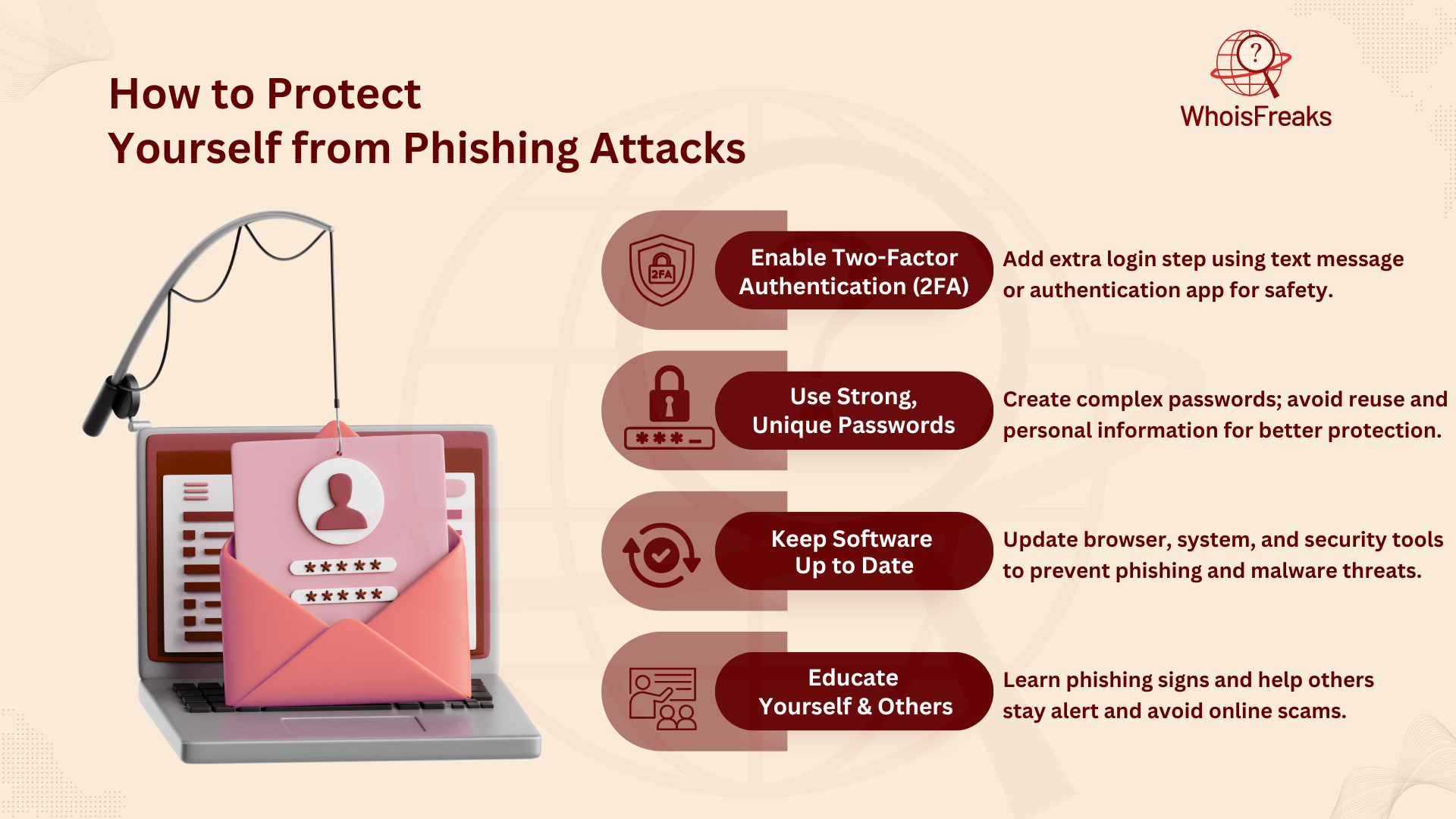
A password manager can make it easier to create and store strong, unique passwords for each account. This tool helps you avoid the temptation to use weak passwords or reuse the same password across different sites, which makes your accounts more vulnerable to attacks. By using a password manager, you can store all your passwords securely and let the tool generate complex passwords for you. This ensures that your sensitive company data remains protected without having to remember every password yourself.
Two-factor authentication (2FA) adds an important extra layer of security to your email account. With 2FA, after you enter your password, you'll be asked to provide a second form of identification, usually a one-time code sent to your phone or an app like Google Authenticator. This makes it much harder for cybercriminals to access your account, even if they manage to guess or steal your password. If a hacker tries to break into your account, they will need your phone or access to the authentication app to bypass it, making it crucial to report phishing attempts.
Whenever you receive an email with an attachment that you weren't expecting, pause and double-check the sender's email address. Hackers often send phishing emails that appear to be from someone you know but are actually trying to trick you into opening malicious files. If the email looks suspicious or comes from an unfamiliar source, don’t open any suspicious attachments. Your email program may have virus scanning tools that help block spam and known harmful files, but it’s always wise to have your IT department ensure that your email settings are optimized for the best protection.
To avoid putting your company’s email security at risk, keep your company email strictly for work-related matters. Using your work email for personal reasons, such as online shopping, signing up for subscriptions, or communicating with friends, can expose your email account to unnecessary risks. By limiting the use of your company email to business purposes only, you help reduce the chances of cybercriminals gaining access to your sensitive information. Make sure everyone in your organization, from the newest hire to the CEO, follows this policy to ensure the safety of the entire company's email system.
Public Wi-Fi networks, like those found in airports, coffee shops, or other public spaces, are often not encrypted, making it easy for cybercriminals to intercept your data. When you connect to these networks, hackers can access the information you send and receive, including your sensitive emails and personal data. To stay safe, always use a Virtual Private Network (VPN) when connected to public Wi-Fi. A VPN encrypts your internet connection, making it much harder for attackers, who may have access to your social media posts, to see your data. Using a VPN ensures that your company’s sensitive information remains private, even when you’re working in a public space.
To protect yourself from phishing attacks, here are some simple steps you can take:
Phishing attacks can have serious and far-reaching effects, as shown by the 2016 hack of the U.S. Democratic National Committee (DNC). In this high-profile case, Russian intelligence operatives used spear phishing to break into the DNC’s internal email system, leading to the leak of sensitive emails that had a major impact on the U.S. presidential election.
The attackers sent a carefully designed phishing email that tricked DNC staff into clicking on a harmful link. The email looked like a legitimate message from Google, telling users their accounts were compromised and urging them to change their passwords. When staff clicked the link, they were sent to a fake Google login page where they unknowingly entered their login details. This gave the hackers access to the DNC’s network, where they spent months stealing sensitive data.
The breach was revealed when the hackers began leaking the stolen emails to the public, causing major political and reputational damage. This incident highlighted how effective phishing can be in political contexts and showed the urgent need for stronger cybersecurity measures, like multi-factor authentication, better email filters, and more user education, to prevent such breaches.
Phishing attacks remain one of the most widespread and harmful forms of cybercrime. As technology keeps evolving, cybercriminals are finding new ways to trick people, making it harder to tell the difference between real and fake emails. However, by staying alert, carefully verifying unsolicited messages, and learning how to identify phishing emails, you can greatly lower the risk of falling victim to phishing.
At the end of the day, awareness and education are your best defense. Phishing emails are designed to take advantage of human mistakes, and while the techniques used can be high-tech, many attacks still rely on simple tricks like playing on emotions such as urgency and fear. Recognizing the signs of phishing and knowing what to do can make all the difference in keeping your personal and financial information safe.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Learn how to prevent subdomain takeover with essential strategies and best practices. Protect your online assets—read the full guide now!
8 min read