
Mastering WHOIS OSINT for Effective Domain and IP Investigations

By Qasim
Posted on May 17, 2025 | 12 min read


By Qasim
Posted on May 17, 2025 | 12 min read
In the world of cybersecurity and research, Open-Source Intelligence (OSINT) is a valuable tool. One of the key OSINT methods used in domain and IP investigations is WHOIS. WHOIS is a protocol that lets investigators access important details about domain names and IP addresses, such as ownership, registration, and history. Knowing how to use WHOIS is essential for anyone in cybersecurity, digital forensics, or investigative research, as it helps identify malicious actors, uncover threats, and trace suspicious online activity.
For digital forensics experts, penetration testers, or security professionals, tracking down the person or organization behind a domain or IP address is often the first step in solving a security issue or identifying weaknesses. In this blog, we’ll cover the basics of WHOIS, its role in OSINT investigations, and how to use WHOIS data effectively for domain and IP research. Whether dealing with cybercrime, fraud, or malware, understanding WHOIS will help you be more efficient and accurate in your investigations.
WHOIS OSINT (Open-Source Intelligence) is a smart way to gather information that’s open and easy to access. This information is about domain names and IP addresses, and it comes from Whois databases. It helps uncover important details about who owns a domain, when it was registered, and the setup behind it. WHOIS OSINT is especially useful in cybersecurity, where it helps investigators follow up on suspicious activities and find possible online threats linked to a domain or IP address.
WHOIS data is important because it helps us learn about domain ownership and registration. It shows who owns a domain, when it was registered, and where it is hosted. This helps track down the start of suspicious online actions. WHOIS data also helps in cyber threat intelligence by finding harmful actors and their work, giving us more insight into their online presence. On top of that, WHOIS OSINT is key for legal and compliance purposes, as it can provide valuable statistics about domain ownership and activity. It helps businesses make sure the domains they work with in transactions, partnerships, or legal matters are safe and real.
WHOIS OSINT works by using WHOIS databases. Investigators use special lookup tools to search for details about domain names and IP addresses. These tools give back important information, like who owns a domain, when it was registered, and where it’s hosted. By using this data and analyzing the results, people and organizations can better understand who owns a domain, track its history, and find any cyber threats or harmful activities linked to it.
WHOIS OSINT, or Open-Source Intelligence, is a powerful tool that helps make domain and IP investigations better. It uses WHOIS data, which gives important details about domain ownership, history, and activity. This data is key in tracking down cybercrimes, fraud, and bad online behavior. WHOIS OSINT helps find the real identity behind a domain or IP address on the web, even when fake details or privacy protection services try to hide it. By looking at WHOIS records, investigators can track IP addresses, watch for changes in DNS, and check past data to find helpful clues.
Tracking IP addresses linked to domains gives useful information that can lead to finding new people or groups involved in bad activities. Checking past ownership and contact details can show patterns that link the domain to other suspicious groups or people. Also, noticing changes in DNS records can show if someone is trying to hide bad actions, which is important for detecting crime. WHOIS OSINT also helps investigators see how a domain or IP address changes over time. By finding out who first owned the domain, they can learn what it was used for or if it is part of a bigger group of cybercriminals that connect to other malicious activities. Watching for changes in domain ownership and hosting providers can point to suspicious activity, helping to uncover fraud or harmful intentions.
When conducting a WHOIS OSINT investigation, there are several key data points you should focus on. These data points provide essential information about the ownership, registration, and activity of a domain or IP address. Below are the most important elements to investigate:
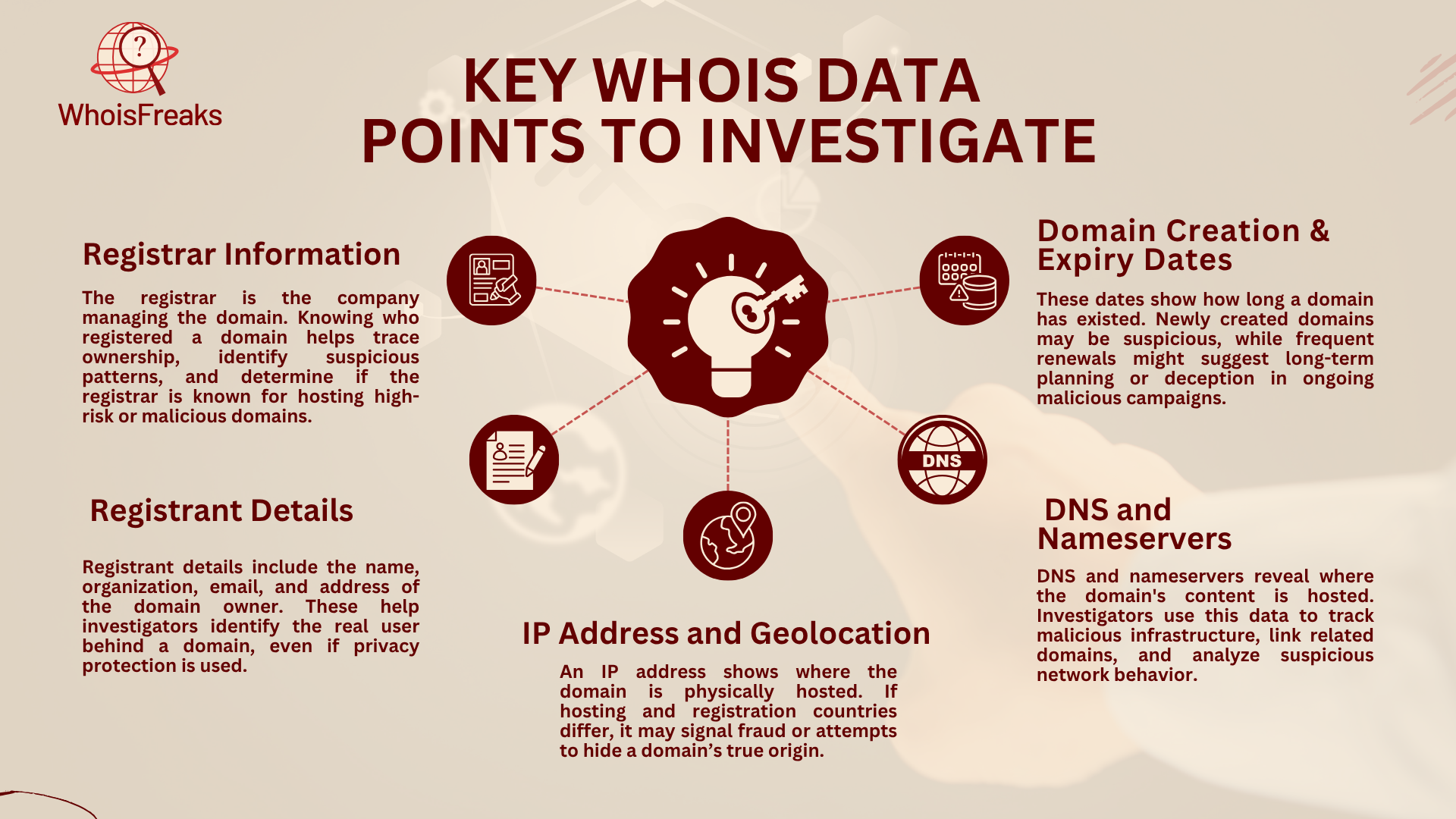
When looking into domain-related activities, the registrar is key. The registrar is the company or organization that manages domain name registration. Their details can give important insights, especially if the domain shows suspicious or harmful behavior. In these cases, the registrar can help take the domain down to stop more damage. Some registrars are known for handling high-risk domains. Knowing which registrar is linked to a domain can show patterns and risks. By checking registrar details, investigators can learn about the domain's past and reputation. This helps find links to fraud or other bad activities.
Registrant details are key for investigators. They help link a domain or IP to a person or company. These details include the owner’s name, organization, email, phone, and address, which are crucial for ensuring the accuracy of the investigation. This helps find the true owner. Sometimes, registrants use privacy protection to hide these details. This makes it harder to find the owner. In these cases, reverse WHOIS lookups or past WHOIS data can help. These tools give investigators the clues needed to uncover the real owner.
The domain creation date is important for checking how active the domain is. A newly created domain might be suspicious, especially if linked to fraud. Looking at the expiry dates can show the owner’s plans. If the domain is about to expire or has been renewed, it may signal a change in the owner’s intentions. This is helpful in investigations. By checking both creation and expiry dates, investigators can learn more about the domain’s history and any risks.
DNS records and Nameservers show where a domain’s website and services are hosted. Investigators use DNS data to find the hosting provider and track linked IP addresses. This helps when looking into the infrastructure behind a malicious website. By checking DNS and nameserver details, investigators can find patterns across many domains. They can also link domains or IPs that may seem unrelated at first.
The IP address of a domain gives useful clues about its location and network. WHOIS databases usually show the IP address of the server that hosts the domain. By looking at the geolocation of this IP, you can find out which region or country hosts the domain. This helps uncover details about the domain's activities or jurisdiction. If a domain is registered in one country but hosted in another, it may seem suspicious. This can raise doubts about the domain's legitimacy and purpose.
When conducting WHOIS OSINT (Open-Source Intelligence) investigations, using the right tools is crucial to uncover valuable insights about domains, IP addresses, and their ownership history. Below are some of the most effective tools and resources for performing WHOIS lookups and related investigations.
Whoisfreak offers a powerful suite of tools tailored for domain investigators, threat analysts, and cybersecurity professionals. It provides fast, accurate, and up-to-date WHOIS data including registrant details, domain status, and key timestamps all accessible via an easy-to-integrate API.
Whether you're conducting bulk WHOIS lookups, tracking domain ownership changes, or uncovering hidden connections between digital assets, Whoisfreak supports both real-time queries and historical WHOIS data. Its flexibility allows seamless integration into automated workflows and custom investigation tools.
Use cases include fraud detection, threat intelligence, digital asset tracking, and more.
As the global authority overseeing domain name registration, ICANN provides a free WHOIS lookup tool that allows users to retrieve publicly available domain registration information. While this service is ideal for simple lookups of top-level domains (TLDs), the data may be limited in cases where domain privacy protection is enabled or for complex investigations.
Reverse WHOIS search allows you to find all domains registered using a particular email address, phone number, or other identifying contact information. This is a vital technique in OSINT investigations, especially when identifying networks of connected domains or tracking suspicious behavior.
Whoisfreak's Reverse WHOIS functionality offers precision and depth, helping analysts identify patterns and relationships across large domain datasets even when WHOIS privacy shields are present in some cases.
Conducting a successful WHOIS OSINT investigation involves more than just using the right tools—it's about following a systematic process to gather the most relevant and accurate information. By sticking to best practices and conducting a thorough review, you can make your WHOIS investigations more effective and uncover valuable insights quickly. Here are some key tips:

The first step is to perform a basic WHOIS lookup. This will give you essential details about the domain or IP address, like the registrar, registrant, and registration dates. If privacy protection is on, check the registrar’s contact info, as they may provide more details about the domain owner.
Don’t rely on just WHOIS data. Use other sources like DNS records, IP lookup tools, and reverse WHOIS searches to verify the information. This can help confirm the accuracy of the data and uncover hidden connections between domains or IPs.
Look at the domain’s historical WHOIS records to find deeper insights. Tools like DomainTools or WhoisXML API show past ownership and registration details. This can help you spot patterns or track down the real identity behind a domain, especially if it’s been involved in suspicious activities.
Keep an eye on domain expiry dates and renewal histories. A domain that’s about to expire or has been recently renewed might indicate a change in ownership or malicious intent. Tracking these dates helps you identify suspicious activities or changes in domain status.
Always stay within legal boundaries. Follow privacy laws like GDPR, which may limit access to certain WHOIS data. Be mindful of ethical considerations, especially when dealing with private individuals or sensitive data. Don't try to bypass privacy protection unless you have a valid legal reason.
Make sure to document everything you find in an organized way. This is crucial if your investigation could be used for legal purposes. Keeping clear records of your findings and the context around them ensures you can track your process and provide evidence if needed.
WHOIS data is a valuable resource for investigators, but it has some limitations that can affect the success of OSINT investigations. It's important to note that being aware of these challenges can keep your investigation accurate and effective.

One major issue is the widespread use of domain privacy protection services. Many domain owners use these services to hide their contact details, replacing them with information from a third-party service. This makes it hard for investigators to identify the true owner of a domain. Although reverse WHOIS searches or older records might help, privacy protection often limits access to important information.
WHOIS data can sometimes be incomplete or outdated. Some domain owners may intentionally provide false or old details, or the data may not have been updated for years. For example, an outdated email or phone number could make it hard to find the actual owner. This is common with domains used in illegal activities, where criminals use fake or outdated data to cover their tracks.
Some WHOIS databases don’t provide full access to all data, especially for certain country-specific domains. The level of transparency varies depending on local laws and regulations. This can leave gaps in the information available to investigators. In some cases, full records may require a formal request to the domain registrar, which can be a lengthy process.
Privacy laws, like the GDPR in Europe, limit access to WHOIS data. These regulations protect personal information, so contact details for individual domain owners may not be visible in public records. Investigators must be cautious in regions with strict privacy laws to avoid legal problems. There are also ethical concerns when dealing with private individuals or sensitive data.
To deal with these challenges, investigators can combine WHOIS data with other OSINT tools like DNS records, IP address lookups, and reverse WHOIS searches. Using multiple sources can help fill in gaps and be essential for completing the investigation by providing a clearer picture of the domain or IP being investigated.
Real-world examples show how WHOIS OSINT helps investigators and cybersecurity experts uncover cybercrimes. Here are three case studies that demonstrate the power of WHOIS data in online investigations:
A cybersecurity team worked to find the source of a large phishing campaign targeting corporate email accounts. The attackers used a fake domain to trick people into revealing sensitive login information. After checking the WHOIS data for the phishing domain, the team found it was registered under privacy protection. However, by analyzing the domain’s IP address, they tracked it to a hosting provider with ties to previous phishing attacks. A reverse WHOIS search revealed other domains registered with the same email address. This led to the discovery of a criminal group in Eastern Europe. Sharing this info with law enforcement led to several arrests.
A bank suffered a DDoS attack that shut down its website and online banking services. The bank’s IT team used WHOIS OSINT to examine the IP addresses involved. By looking up the WHOIS data for these IPs, they identified the hosting provider and linked them to a domain with suspicious activity. Further investigation connected the attack to a well-known hacker group famous for launching DDoS attacks. The team traced the group’s activities to a server farm overseas. This information helped the bank improve its security and supported law enforcement efforts against the hackers.
The IRBIS OSINT Center used WHOIS OSINT techniques to locate Emmanuel Edokpolor, a fugitive wanted by Nigeria’s anti-corruption agency for embezzling government funds. By analyzing domain registration info and IP addresses linked to assigned names, investigators built a detailed profile of Edokpolor's online activities and connections, which led to his capture.
In conclusion, WHOIS OSINT is a valuable tool for digital investigations. It allows investigators to find important information about domain ownership, registration, and hosting numbers, which is crucial for tracing cybercriminals, verifying online entities, and preventing cybercrime. Whether dealing with phishing, DDoS attacks, or fake websites, WHOIS data provides essential insights that guide investigations and help resolve cases.
However, WHOIS OSINT has its limitations. Privacy protection services, incomplete data, and legal restrictions can make investigations harder. But by combining WHOIS data with other sources like DNS records, IP geolocation, and reverse WHOIS searches, investigators can get a clearer, more complete picture.
For those looking to dive deeper into Whois OSINT, it's important to stay up to date with best practices, legal issues, and the latest tools. While WHOIS data might not always tell the whole story, it can be a key part of uncovering hidden networks and tracking down cybercriminals, and to ensure the effectiveness of the investigation.
By mastering WHOIS OSINT and refining investigative skills, you can improve the effectiveness and ethics of your investigations on any site in today’s digital world.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore how WHOIS history aids forensic analysis in cybercrime investigations. Learn effective strategies to enhance your cyber defense. Read more now!
9 min read

Learn how subdomain discovery can enhance phishing prevention and protect against spoofing campaigns. Read the article for practical strategies.
12 min read