

By Qasim
Posted on May 05, 2025 | 11 min read
DNS, also called the Domain Name System, consists of various name servers that function like the internet's phone book. It turns domain names into IP addresses. This helps websites and users connect easily. Good DNS settings are key to keeping your browser safe. They protect you from cyber threats like spoofing and other bad activities. But sometimes, hackers change DNS settings without you knowing. This leads to DNS hijacking. Hackers reroute you to dangerous websites. It’s a serious problem. It can harm your browser's security and stop you from reaching the websites you want.
In this article, we'll dive into DNS hijacking. You’ll learn how DNS settings track, catalog, and manage web traffic. You’ll also see how strong DNS protection can keep you safe online. By understanding these threats, you can protect your digital life from attacks.
DNS Hijacking is a serious cyber threat. It happens when an attacker changes DNS settings without permission. They can find weak spots in your network, like router settings or devices. These weaknesses let attackers' control how your internet traffic is directed.
Normally, when you browse the web, your DNS server turns a domain name into an IP address. But with DNS Hijacking, this process is interrupted. Instead of going to a real website, you're sent to a fake one. These fake sites look just like the real ones. They copy the design, branding, and features.
On these fake websites, attackers try to get you to enter login details or personal info. This information, including your login details, is sent straight to the attacker’s server to steal login credentials. They can use it for identity theft, fraud, or stealing access to your accounts.
Knowing about DNS Hijacking is important. It helps protect your data and keeps you safe online from these sneaky attacks.
DNS hijacking is a type of attack where cybercriminals change the settings of your DNS (Domain Name System). The DNS is like a phone book for the internet. It helps translate website names (like google.com) into IP addresses, which computers use to find websites.
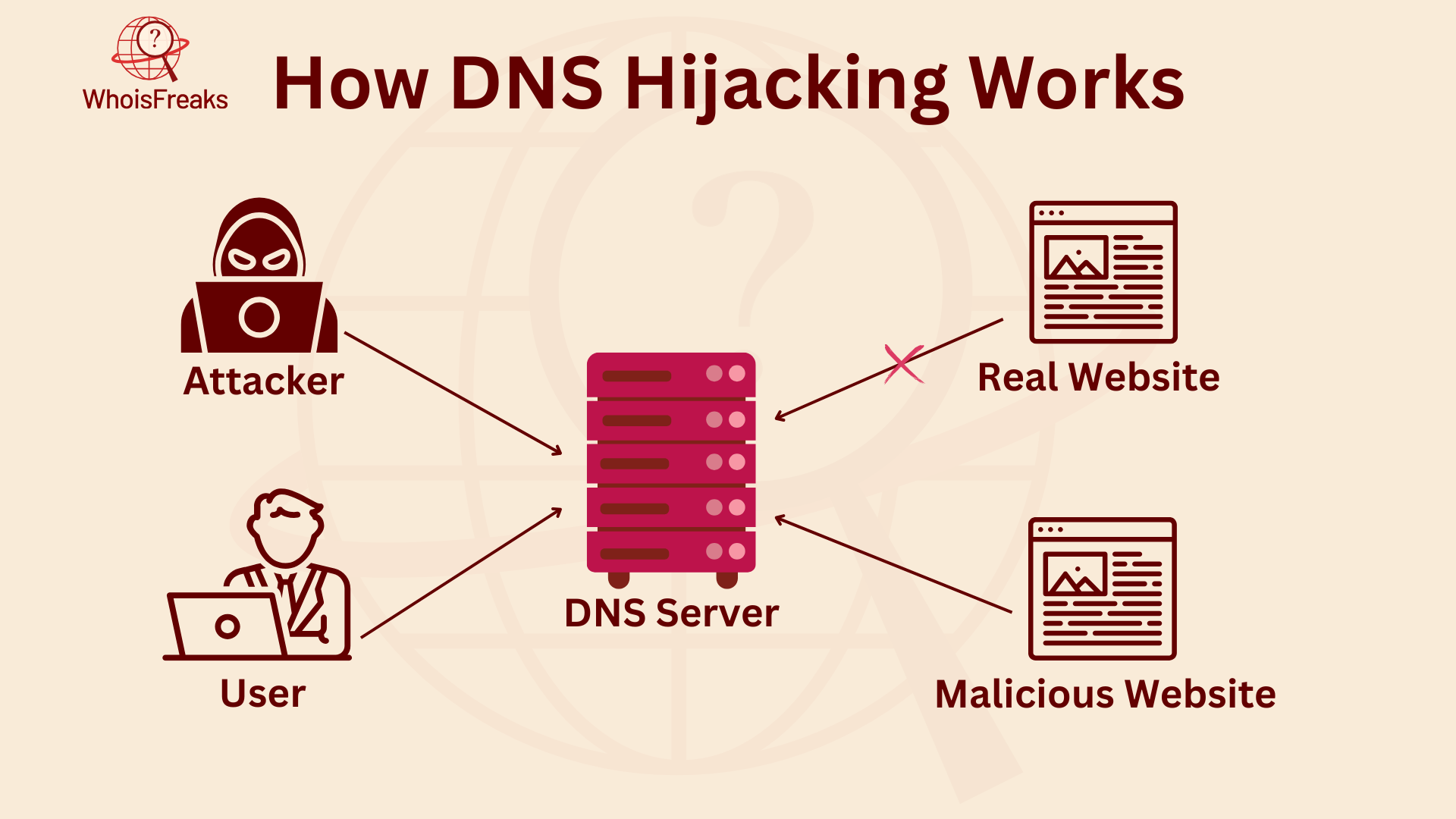
In a DNS hijacking attack, hackers can redirect you to fake or dangerous websites without you knowing. Here's how it usually happens:
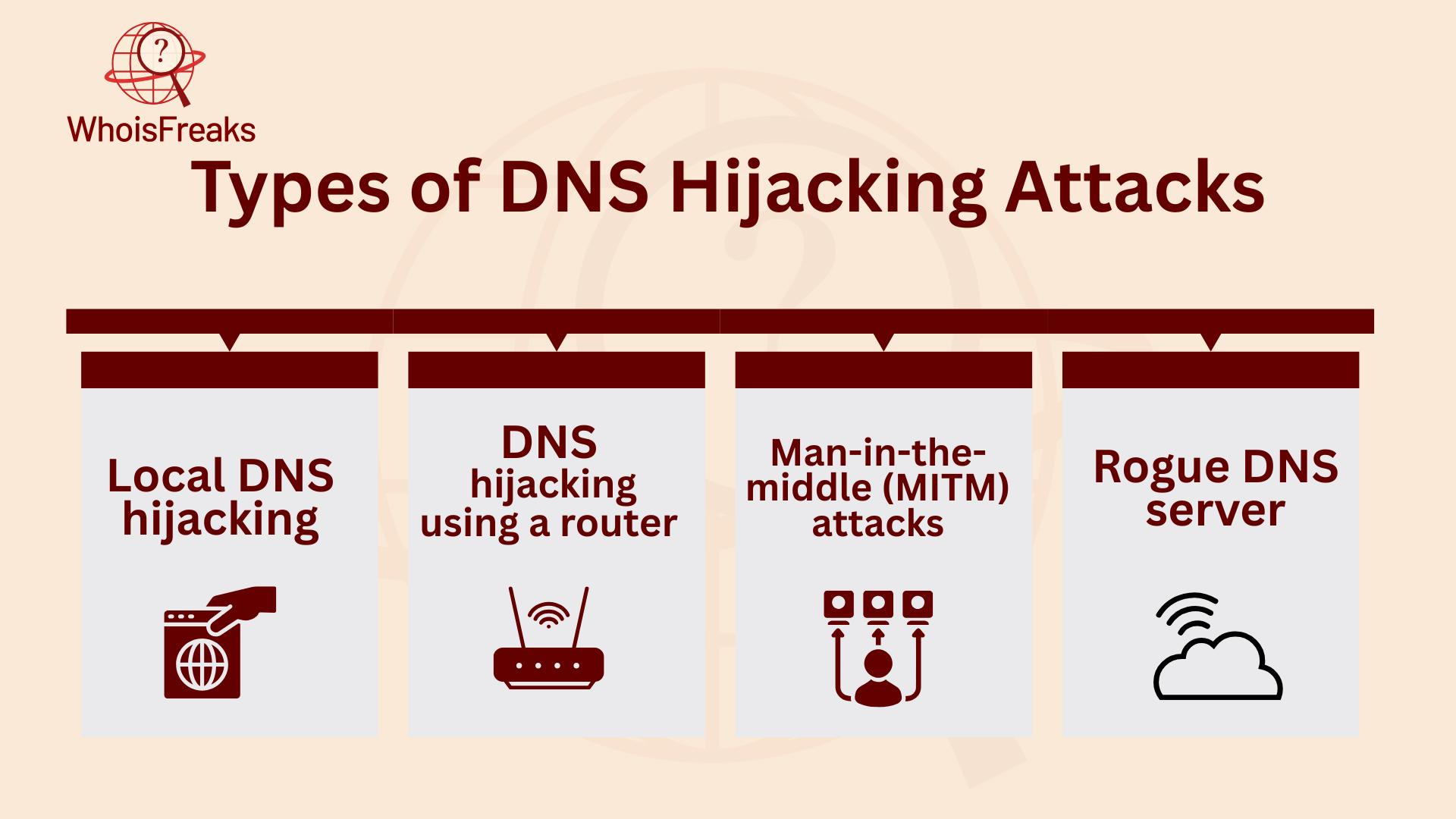
To prevent DNS hijacking, first, you have to know the different kinds of attacks. DNS hijacking can take four different forms:
Local DNS hijacking is a type of cyberattack. In this attack, an attacker uses bad software, like Trojan software, to target your computer. This software infects your device, allowing the attacker to change your DNS settings. By changing these settings, the attacker can send you to harmful websites. These fake sites can put your cybersecurity at risk.
Knowing how local DNS hijacking works helps you avoid these threats. It can protect you from being sent to malicious websites and keep your online activities safe.
DNS hijacking using a router is a big cyber threat. Attackers often target home routers. These routers may have weak firmware or default passwords. Attackers use these flaws to break in. Once inside, they change DNS settings. This sends users to harmful sites.
Router hijacking risks every device on the network. Malicious activity, often targeting a malicious domain, can harm devices and cause more problems. To stop DNS hijacking, improve password security and fix firmware issues.
Man-in-the-middle (MITM) attacks are a type of DNS hijacking. They are a serious cyber threat. In these attacks, attackers get in the middle of DNS communication. They intercept the talks between users and the DNS server. This is called DNS interception.
Once inside, attackers change the DNS resolution. This lets them send users to bad or fake sites. They use weak spots in the system to do this. They also use spoofing to look like a trusted source. By sending fake replies to your browser, they can steal data. This can lead to harmful redirects and security risks. These attacks put both users and their devices in danger.
A rogue DNS server is a big part of DNS hijacking. This is a type of cyberattack. Hackers change DNS records on a trusted DNS server. This lets them reroute DNS requests. Users end up on a bad site, not the real one. The rogue DNS server sends them to harmful sites. It uses spoofing tricks to make the fake site look real. Since DNS resolution works as usual, users may not know they’ve been tricked.
These DNS attacks use redirect steps and domain spoofing. They aim to fool users fast. Strong network security helps stop these attacks. It protects against DNS changes and builds trust in DNS servers. This reduces the chance of falling for a rogue DNS server.
DNS hijacking can cause your web pages to load slowly, show unwanted pop-up ads on websites, or display pop-ups saying your computer has malware. If you notice these problems, there are simple ways to check if your DNS has been hijacked:
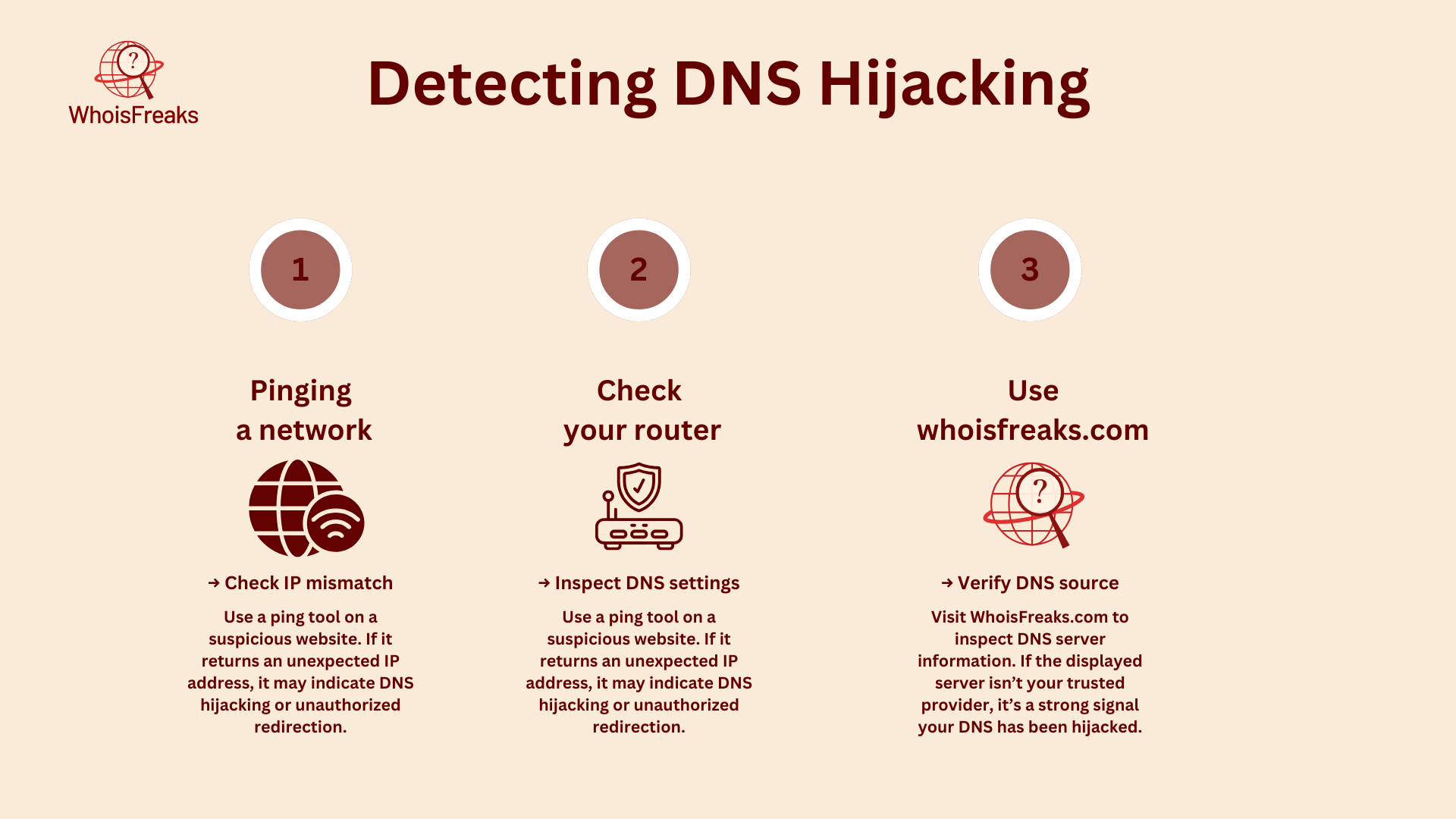
A simple but powerful way to protect against DNS hijacking is to use a trusted DNS provider with added security features. Public DNS services like AWS Route 53 have tools like threat detection, encrypted DNS queries, and DNS filtering to block harmful websites.
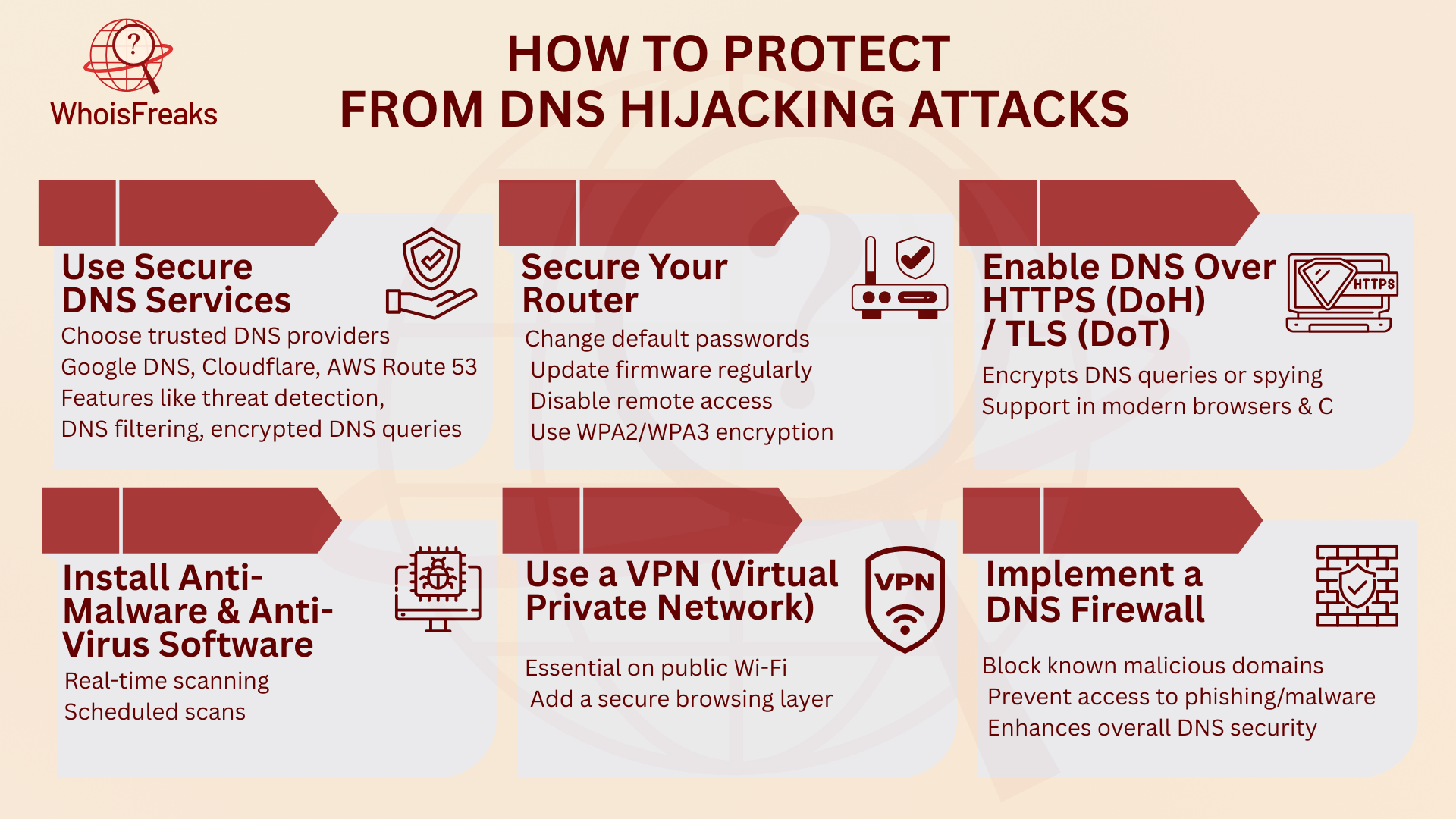
Routers are often targeted for DNS hijacking, especially at home. Attackers may use weak router settings or default passwords to change your DNS settings. To secure your router, follow these steps:
DNS Over HTTPS (DoH) and DNS Over TLS (DoT) are modern protocols that encrypt your DNS requests. This stops attackers from changing or intercepting your DNS queries and ensures that no one can tamper with the websites you're visiting.
Malware can alter your DNS settings, leading to DNS hijacking. Install good anti-malware and anti-virus software to protect your devices.
A VPN encrypts your internet traffic, including DNS queries, and sends it through a secure server. This adds extra protection, especially when using public Wi-Fi, which is vulnerable to DNS hijacking and other attacks.
DNSSEC is a security protocol that makes sure the responses to DNS queries are authentic and haven’t been altered. It adds a layer of cryptographic validation to DNS records to protect against DNS hijacking.
To use DNSSEC, work with your domain registrar and DNS hosting provider to ensure your DNS zone is signed and verified. Although many organizations haven’t yet implemented DNSSEC, it’s an effective defense against DNS hijacking.
Companies should regularly check their DNS records to make sure they haven't been tampered with. Monitoring DNS traffic can also help detect hijacking attempts early.
A DNS firewall blocks requests to known harmful domains. This stops users from being redirected to fake websites that could be used for phishing or downloading malware.
DNS hijacking has been used in many big attacks. These attacks affected millions of people around the world. Let's look at three of the most famous ones.

In 2011, the DNS Changer Trojan was used by an Estonian cyber group called Rove Digital. This Trojan hijacked DNS settings on infected computers. It redirected users to fake websites. The attack affected over 4 million computers in more than 100 countries. In the U.S., about 500,000 devices were compromised. This included devices used by individuals, businesses, and even government agencies like NASA.
In 2015, hackers attacked Google’s Vietnam site, google.com.vn. These hackers, possibly supported by some internet service providers, were believed to be part of the Lizard Squad group. They changed Google’s nameservers to send users to a defaced page. The page showed an image of a man taking a selfie and a message from Lizard Squad. However, Google Vietnam itself was not compromised.
The MyEtherWallet attack in 2018 shocked the cryptocurrency world. Attackers hijacked the DNS of the popular wallet service. They redirected users to a phishing website. Users entered their login details on the fake site. As a result, the attackers stole over $150,000 worth of Ethereum. This attack showed how vulnerable online wallets can be to DNS hijacking and phishing scams.
DNS hijacking can harm both individuals and businesses. It can lead to data theft. Users may enter sensitive information on fake sites. These sites are controlled by attackers. This puts personal and financial data at risk.
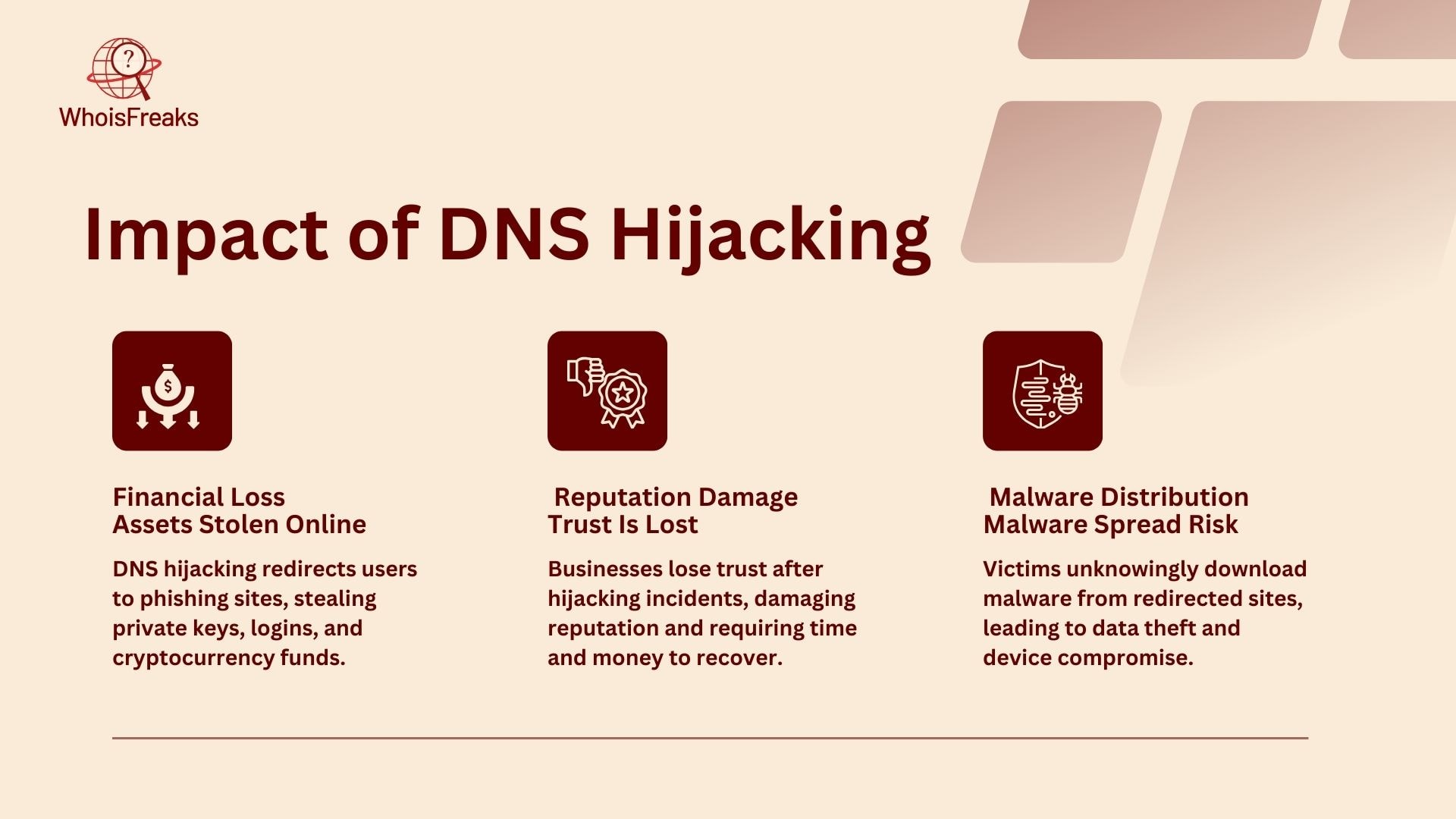
DNS hijacking can also cause financial loss. For example, MyEtherWallet users lost cryptocurrency. They were sent to phishing sites. Phishing sites trick users into giving away private keys and login info. This leads to theft of their assets.
Organizations that face DNS hijacking may suffer reputation damage. This is especially true if customer data is stolen. The trust customers have in a business may be lost. This can harm the brand’s image. It may take a long time and money to rebuild trust.
Another effect of DNS hijacking is malware distribution. Users may be sent to harmful websites. They might unknowingly download malware on their devices. This malware can steal data, monitor activity, or cause other problems.
| Attack Type | Description | Key Difference |
|---|---|---|
| DNS Spoofing | The attacker alters DNS information, leading the user to a fake site. | Does not take the site offline; redirects to a fraudulent site. |
| DNS Hijacking | The attacker takes over the session after the user authenticates. | Requires the user to authenticate before the attack. |
| DNS Cache Poisoning | The attacker manipulates a caching DNS server with fake responses. | Targets the DNS cache; difficult to detect without DNSSEC. |
DNS hijacking is a major cybersecurity threat that can have severe consequences for both individuals and businesses. It occurs when attackers gain control of DNS settings and redirect users to fake websites. This can lead to serious issues such as data theft, where users unknowingly provide sensitive information like passwords and credit card details. Financial losses can also occur, especially in cases like the MyEtherWallet attack, where cryptocurrency was stolen.
Additionally, DNS hijacking can damage a company’s reputation, particularly when customer data is compromised. Trust is essential in business and losing it can result in long-term harm to a brand. Malware distribution is another common consequence of DNS hijacking, as malicious websites can infect devices with harmful software.
To protect against these attacks, it's crucial to use secure DNS services, regularly update router passwords, and enable DNSSEC. Monitoring DNS activity, setting up firewalls, and using encryption protocols like DNS over HTTPS (DoH) can also prevent hackers from taking control of your DNS. By staying proactive and implementing these security measures, individuals and businesses can safeguard their online presence from DNS hijacking attacks.

Discover essential insights on DNS poisoning and learn practical steps to safeguard your online presence. Read the article for vital protection tips.
10 min read

Learn how a DNS flooder can threaten your network security and discover practical measures to protect your systems. Read more to safeguard your network.
10 min read

Discover the essential role of DNS servers in internet functionality and learn how they enhance your online experience. Read the article for insights.
9 min read