

By Nadeem Khan
Posted on March 24, 2025 | 9 min read
IP spoofing is a common type of cyber-attack. It tricks computer networks into thinking a request comes from a trusted source. Hackers can change the IP address to gain unauthorized access to a network. This leads to harmful acts like stealing sensitive data or turning computers into zombies. These hijacked devices are then used for attacks, like Denial-of-Service (DoS).
The goal of spoofing is to hide the actual source of the attack. This makes it a popular tool in hacking and network intrusion.
While IP spoofing is a major threat, it shows how crucial strong security is. Solid network security measures can help prevent spoofing. They detect and block unauthorized access. As cybercrime grows, it’s important to know the different types of spoofing. This helps protect sensitive data and keeps networks safe. Let's dive into the article for a better understanding about the IP Spoofing.
IP spoofing is a type of malicious attack. It happens when a threat actor changes IP packets. This lets them impersonate a different computer system. They disguise the sender's identity and change the source IP address in the spoofed packet's header. Attackers use this trick for distributed, denial of service attacks (DDoS) and man-in-the-middle attacks. These attacks target devices and infrastructure while hiding the true source.
In DDoS attacks, the goal is to flood the target with traffic. This makes it harder for mitigation efforts to stop the attack. Spoofed IP addresses let attackers get around security scripts, devices, and services that block known malicious sources. By using shields for hiding their true identity, threat actors can carry out attacks without being traced or stopped.
IP spoofing is a method hackers use to cause harm. They manipulate the IP address to create chaos. One main goal is to launch a Denial of Service (DoS) attack. The hacker uses a fake address to connect to a server and sends many requests. By using open reflectors, like servers running connectionless protocols, the hacker can make the attack stronger. This can overwhelm the system, sometimes reaching hundreds of Gbps.
IP spoofing is also used in man-in-the-middle attacks. Hackers create a trusted connection and reroute packets. They can then read or change the data. While it can be used for harm, IP spoofing isn’t always illegal. For example, server admins might use it to run tests. These tests check a website’s performance under heavy traffic. This helps find problems and improve the site. IP spoofing also helps test security systems. It ensures they can handle threats before going live.
The internet was built with IP packets in mind. These packets are key to how data travels. Spoofing is a trick used by hackers to manipulate the trusted IP address header system. Researchers first noticed it in the 1980s. Early articles warned about IP spoofing, but there was no big concern.
In 1994, everything changed. Security expert Tsutomu Shimomura was attacked on Christmas Day. This high-profile attack became known as the "Computer Crime of the Year." It caught a lot of attention and made people realize the damage spoofing can cause. After that, experts focused on how to protect systems from these attacks.
Today, much of what we know about IP spoofing prevention comes from discussions after this attack. In the early days of the internet, protection was weak. But over time, we’ve built better defenses for servers. Awareness has helped create stronger protection measures.
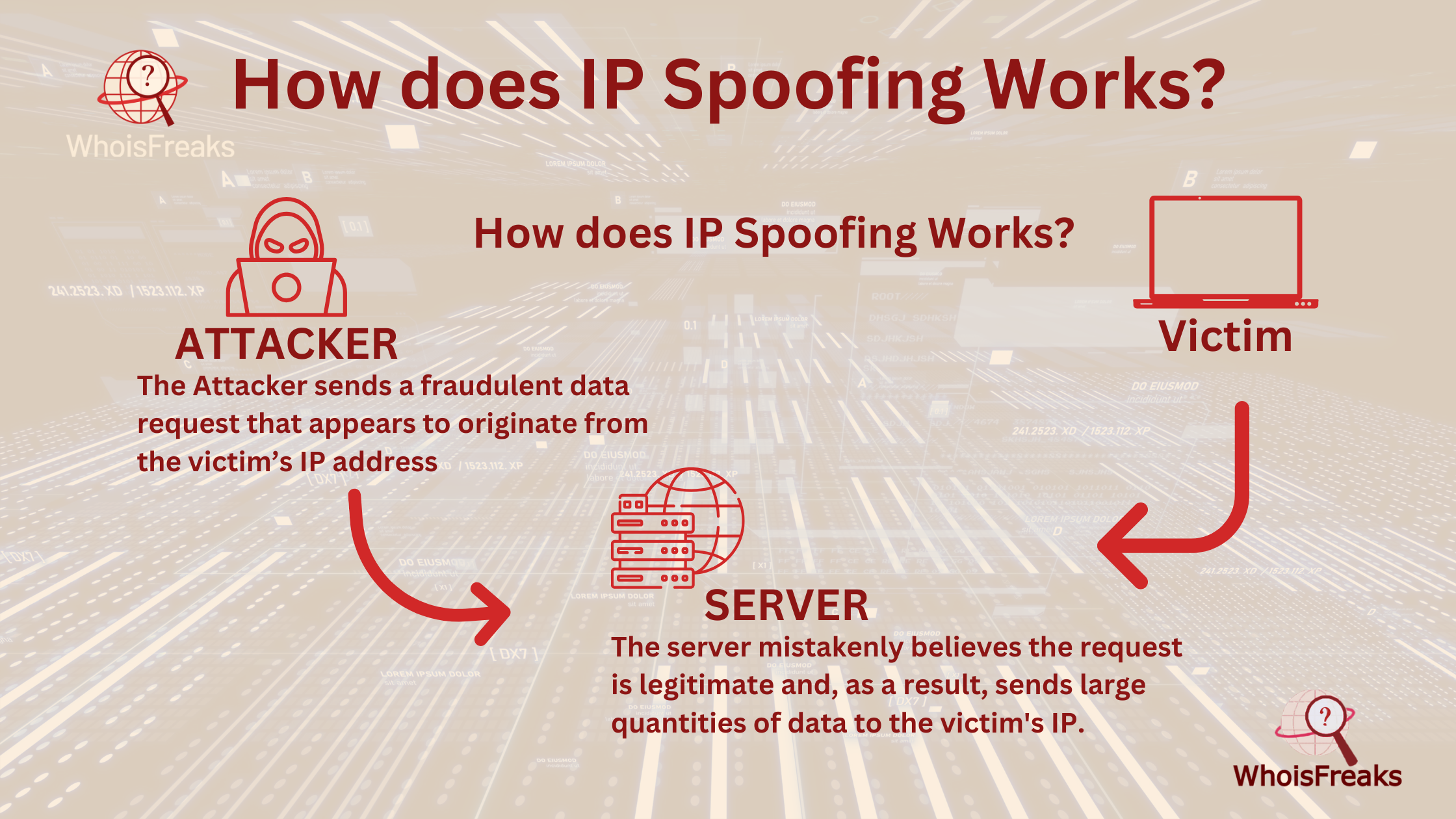
The Internet sends data in packets. Each packet has an Internet Protocol (IP) header. This header contains the source and destination IP addresses. In IP spoofing, a hacker modifies the source intended destination address in the packet header. This trick makes the receiving system think the packet is from a trusted source, like another computer on a real network, potentially leading to the sharing of sensitive information or credentials with spoofed IP address.
IP spoofing happens at the local network call level. Since no clear signs of tampering appear, the hacker stays anonymous. This allows cybercriminals to hide their identity from law enforcement and victims. They can easily bypass firewalls and security checks that would normally flag the packet as malicious.
Spoofed IP addresses can sneak past security systems. This means the targeted systems may not even know they’ve been compromised. No alerts are sent to notify the victim. This makes it harder for systems to detect and block these types of attacks.
IP spoofing is a dangerous attack because it’s hard to spot. Hackers using IP address spoofing and use it to gain system access without the victim knowing. Unlike phishing, IP spoofing has no clear signs. It redirects communication meant for a trusted party to the hacker. The hacker hides their identity with a spoofed IP address.
The ability to stay hidden for so long makes it dangerous. In a secure system, alerts usually go off during an attack. This lets security teams respond. But with IP spoofing, hackers stay in the system, disguised as a trusted source. They can cause damage before anyone notices. On a larger scale, IP spoofing helps hackers bypass firewalls and other security blockers. This lets them flood systems and cause outages. These attacks can shut down services and cause a lot of trouble. This makes the attacks harder to stop.
There are different types of IP spoofing that companies must consider in their internet traffic and security plans. The two main types are blind and non-blind spoofing.
IP spoofing can be used by attackers in many ways to disrupt systems. Some of the common methods are as follow:
DDoS attacks: Attackers send spoofed IP packets to flood servers. These packets look real, so servers respond normally. This overloads the network and causes the target system to go offline.
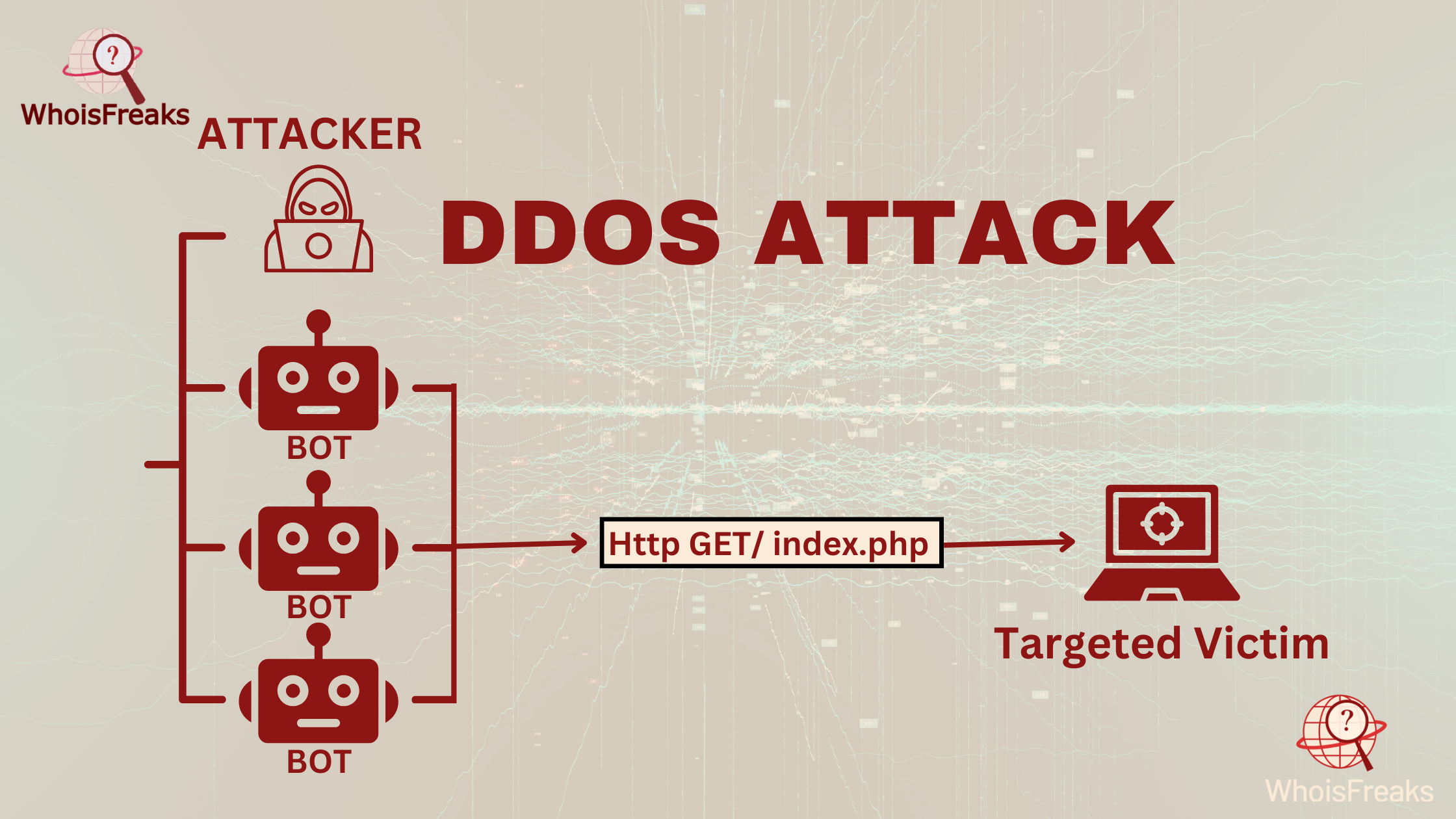
IP spoofing can lead to severe consequences for organizations and individuals alike. It disrupts networks, exposes sensitive data, and allows attackers to bypass security systems. These attacks can damage reputations, increase costs, and even result in legal issues. Effective protection against IP spoofing is essential to prevent these risks and minimize the potential harm.
IP spoofing is hard for end-users to spot. It works at the network layers, specifically Layer 3 of the Open System Interconnection model. Spoofed connection requests often look legitimate, making detection tricky. However, organizations can use network monitoring tools to analyze incoming traffic at endpoints and spot suspicious activity.
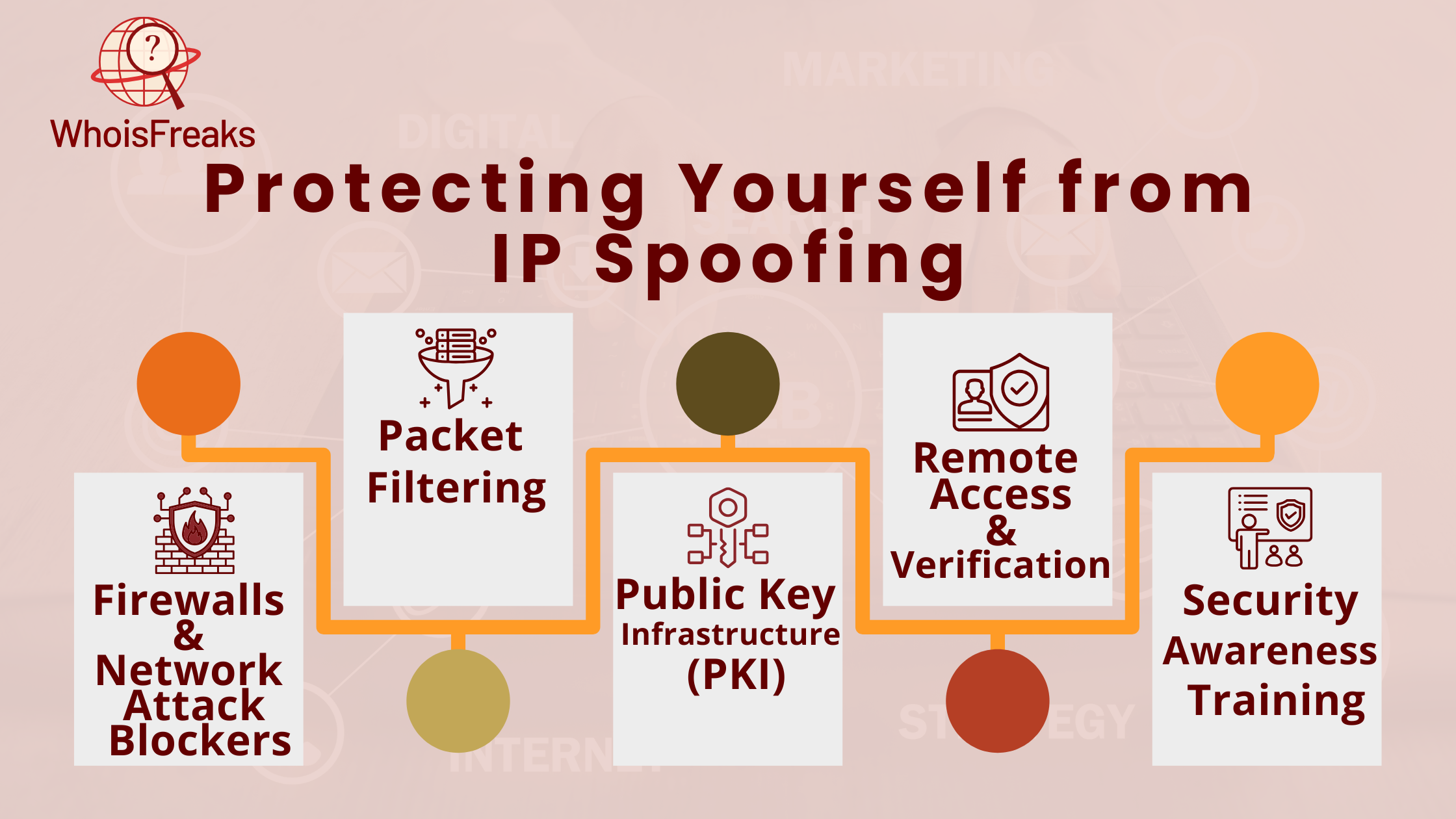
Packet filtering is the most common way to detect and prevent IP spoofing. It is found in routers and firewalls. This method checks for mismatches between the packet's IP address and the IP addresses in access control lists (ACLs). It also helps detect fraudulent packets.
There are two main types of packet filtering: ingress filtering and egress filtering.
An insecure or untrusted DNS resolver can be exploited in spoofing attacks, as attackers might manipulate DNS queries to send you to malicious websites, thereby compromising your system.
By using these methods, organizations can improve protection against DDoS, botnet, and man-in-the-middle attacks, ensuring safer internal network operations.
Protecting yourself from IP spoofing is key to avoiding DDoS attacks, botnet, and man-in-the-middle attacks. Network monitoring is important for tracking network activity. It helps find suspicious or harmful activity from attackers.
IP spoofing attacks have caused major issues in the real world. In 2018, GitHub faced a huge DDoS attack. Cybercriminals spoofed GitHub IP addresses and flooded its database servers with packets. The attack caused the server response rate to jump 50 times higher than normal, leading to a 10-minute outage. This shows how disruptive different IP address spoofing can be.
In 2020 same network, Google was hit by a severe spoofing attack. Chinese attackers used a UDP amplification method to generate 2.5Tbps of traffic aimed at Google servers. The traffic spike reached four times the previous record, showing how fast spoofing attacks can grow. These incidents highlight the growing strength and frequency of DDoS attacks, with IP spoofing playing a big role.
Cybersecurity stats show DDoS attacks are getting worse. Companies must adopt strong protection to detect and against malicious traffic and prevent spoofing attacks.
IP spoofing is a major threat to networks, databases, devices, and even home computers. As long as we send packets for communication between network devices and message senders and recipients, the risk of IP spoofing will stay. Spoofing tools are easy to find, and even amateur cybercriminals can use them. They can bypass security scripts and launch DDoS or MITM attacks.
Though it’s impossible to stop these tools completely, countermeasures can help. Packet filtering, network monitoring, and secure encryption protocols can lower the risk of attacker spoofing. To fight IP spoofing, combining multiple anti-spoofing techniques works best. Awareness training is also key. It helps users understand the threat and supports technical defenses.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Learn how to prevent subdomain takeover with essential strategies and best practices. Protect your online assets—read the full guide now!
8 min read