

By Qasim
Posted on May 10, 2025 | 11 min read
Whaling attacks are a type of cyberattack that focuses on the most important people in a company, like top executives and key decision-makers, highlighting the dangers of whaling phishing attacks. These attacks are a form of phishing, where attackers create convincing emails, messages, or even phone calls to trick these senior individuals into giving away sensitive information.
Unlike regular phishing attacks that target many people, whaling attacks are much more precise. It's like using a sharp spear instead of a wide net. The attackers often use tactics that build trust, make things seem urgent, and appear very legitimate to catch their targets off guard.
The consequences of a successful whaling attack can be serious. It’s not just about losing money, including the risk of unauthorized access to your bank account, although that’s a big risk but also damaging the company’s reputation, losing customer trust, and facing potential legal issues.
In this guide, we’ll explain how whaling attacks work, who they typically target, and offer tips on how to protect yourself and your company from falling victim to them.
Whaling attacks are a special type of phishing. They focus on big targets like CEOs, CFOs, and top executives. Unlike regular phishing, which casts a wide net, whaling attacks are aimed at specific people. These attacks are designed using lots of details about the victims.
The attackers gather information from social media, websites, and other public sources. They then use this info to send emails that look real. These emails might ask for wire transfers, private data, or urgent decisions. These actions, especially spear phishing attacks, can hurt a company. Whaling attacks target people with power and access to important company info. This makes them a big threat to businesses.
Whaling attacks use information from different sources like public websites, social media, and even the dark web. Cybercriminals collect this data to send personalized phishing emails to executives. These emails look real and often have links or attachments with harmful software, similar to spear phishing and whaling. But whaling attacks are more focused and often pretend to be the executive themselves.
When a whaling attack works, cybercriminals can take over the executive’s email and move through the company. They might steal sensitive data or tell employees to share company resources or send money. Whaling attacks can also be part of a bigger plan. For example, a threat actor might send a follow-up email or even make a phone call to pressure the executive into clicking a dangerous link. This mix of methods makes whaling attacks especially risky and effective.

Cybercriminals use a range of clever tricks to deceive high-profile targets. While the methods can vary, here are some common techniques:
Attackers gather detailed information about their targets from social media, company websites, and other public sources. They then use this information to create messages that are very personalized and seem highly relevant to the target.
Attackers might send emails from addresses that look almost identical to legitimate ones. They usually change just a few characters in the email address, hoping the victim won't notice the small difference.
In whaling attacks, messages are carefully crafted to fit the role, interests, or ongoing projects of the individual being targeted. The attacker might pretend to be a CEO, CFO, or another senior official, which makes their request seem more legitimate.
Sometimes, attackers actually hack into a high-ranking executive's email account, making their fraudulent messages appear even more believable. For phone-based attacks, techniques like caller ID spoofing can make it seem like the call is coming from a trusted number.
Attackers may create fake documents, such as fake subpoenas or contracts, that demand urgent action. In some cases, they might direct the target to a fake website that looks identical to a real one, asking them to enter sensitive information.
Whaling attacks are a big cybersecurity threat. They can target top-level bosses and lower-level workers, putting the company’s data at risk. To stop these attacks, businesses need a mix of smart practices, security awareness training employee training, and good security rules. Here’s how to protect against whaling attacks:

Employee awareness is key to stopping whaling attacks. All employees, not just top bosses, need to understand how to protect the company’s data. Even lower-level workers can accidentally let attacks happen by making mistakes with email security. Workers should learn to spot tricks, like fake email addresses that look like trusted ones. For example, a hacker might send an email asking for employee payroll information from to "[email protected]" trick someone who usually gets emails from "[email protected]". Employees should also watch out for emails asking for money or secret data.
A great way to protect against whaling attacks is using multistep checks. Before giving away sensitive data or money, make sure to check the request in multiple steps. Emails and attachments from outside the company should be checked for harmful software, like malware or viruses. This helps catch threats before they cause any damage.
Good data protection rules are important to keep emails and files safe. These rules help protect against whaling and other types of phishing scams. For example, companies should check emails for signs of phishing, like strange domain names or money requests. They can also block suspicious emails from reaching employees to add more protection.
Social media can help hackers in whaling attacks. Top executives should know how their social media activity can give hackers useful info for scams. By setting privacy settings and limiting what they share, executives can reduce the chance of being targeted. Hackers can use data shared on social media to create fake emails that look real, tricking victims into trusting them.
Using anti-phishing tools is another way to stop whaling attacks. Many companies offer software and security services to help block phishing threats. But since whaling often relies on human mistakes, especially responding to fraudulent requests no tool can fully stop the risk. Businesses can also use help from the Anti-Phishing Working Group (APWG). APWG works on phishing research, gives useful resources, and helps companies report and study phishing threats.
By using these strategies, businesses can reduce the risk of falling for whaling attacks and keep their data, employees, and overall security safe.
The fallout from a whaling attack can be serious and have wide-reaching effects on both businesses and individuals, affecting many areas of their operations or personal life, such as the effectiveness of social engineering tactics:

Here are the key signs to look out for when recognizing a whaling cyber security attack:

Emails that mention personal details about you, even if they seem to come from trusted sources like senior executives or business partners, should raise suspicion. These messages are designed to look familiar but may contain too many details.
If an email asks you to take immediate action, such as authorizing a wire transfer or sharing sensitive data quickly, it could be a phishing attempt. Attackers use urgency to bypass normal security checks.
Be cautious of emails from addresses that closely resemble legitimate ones, with slight spelling differences or similar domain names. Always check the email address carefully to spot any small changes.
Watch out for emails requesting wire transfers, changes to payment details, or sensitive information like login credentials or payroll data. These requests are often not part of regular business procedures.
Emails received outside of regular business hours or unexpected requests from executives who don’t usually handle certain tasks could signal a whaling attack. These odd patterns suggest something may be off.
If an email contains confidential company information or projects that only a few people know about, it may be a phishing attempt. Attackers use insider knowledge to trick you into trusting the email, but if the information is not widely shared, be cautious.
By recognizing these signs, you can protect yourself from falling victim to a whaling cyber security attack.
According to the Verizon DBIR 2023, social engineering attacks, like phishing and whaling, are on the rise. This is mostly due to pretexting, a common tactic in Business Email Compromise (BEC). The amount stolen from these attacks has also gone up to $50,000. Cybercriminals often target executives, especially those in the C-suite and board of directors, using tactics that differ from standard phishing attacks. These executives have digital access and special rights to sensitive data, which makes them key targets.
Executives also have the authority to make big decisions, like adding new vendors or wiring money. This gives attackers a reason to focus on them. On top of that, executives mix business and personal activities. They sometimes use personal emails to access company files and systems. This can bypass security controls and increase risk. They also stay connected a lot, often using home networks or public Wi-Fi, which makes them vulnerable to man-in-the-middle attacks.
Because of these risks, security teams often worry about executives' ability to protect their devices, systems, and networks. Even though cyber threats are a top concern for boards, executives are still big targets because of their access, power, and work habits.
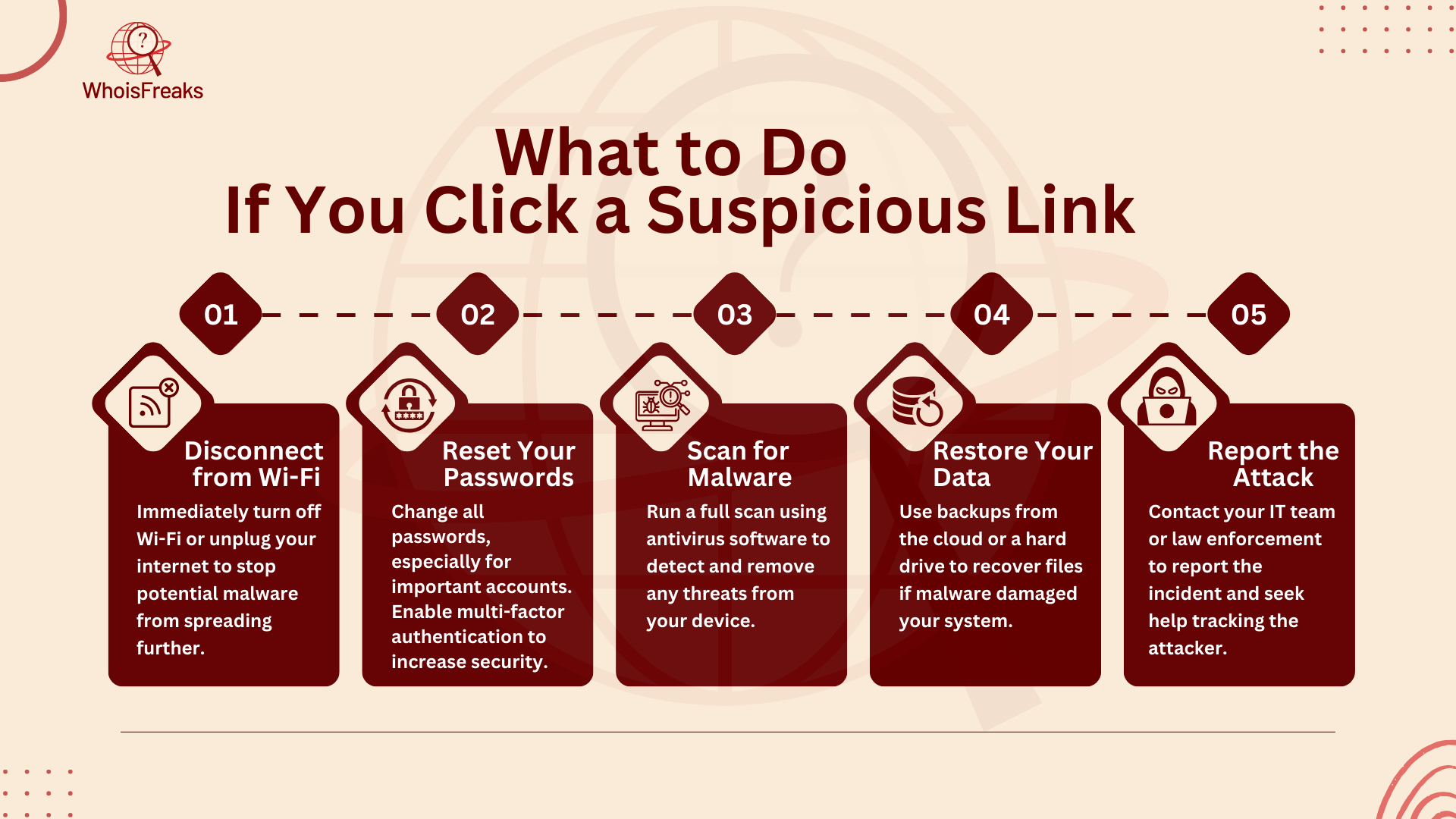
If you click a suspicious link and suspect a whaling attack, quickly disconnect your Wi-Fi or unplug your Ethernet cable to help block whaling attacks. This helps stop any harmful malware from spreading.
Reset the passwords for all your online accounts, especially if you think a hacker gained access to them. It's also a good idea to set up multi-factor authentication for extra protection.
Use cybersecurity software to scan your device for malware. The software will help find and remove any threats. If it can't remove the malware, share the security report with your IT person for help.
If you have backed up your data to the cloud or an external hard drive, restore your data to avoid losing important files. If you don’t have a backup, talk to an IT specialist for recovery options.
If the malware can't be removed or if you need to make a formal report, contact your local law enforcement. They can escalate the case, find a solution, and track down the scammer behind the attack.
By following these steps, you can help limit the damage from a suspicious link and stay protected.
| Aspect | Phishing | Whaling |
|---|---|---|
| Target Audience | General public, employees in organizations | High-ranking individuals (executives, senior managers) |
| Message Type | Generic messages sent to many recipients | Personalized and targeted messages aimed at specific individuals |
| Example | Fake prize messages, emails from fake banks | CEO asking CFO for money transfer, trusted partners asking for sensitive info |
| Complexity of Attack | Simple, easy to spot | Sophisticated, with detailed info making it harder to recognize |
| Common Indicators | Generic greetings ("Dear User/Customer"), poor grammar, suspicious links | Custom details that make the email seem legitimate, using names and positions of familiar people |
| Success Rate | Lower, since it’s easy to spot | Higher, due to the personalized and credible approach |
Whaling attacks are not a new thing, but there have been some high-profile cases in recent years that caught a lot of attention. Let’s look at a few examples to understand how they work and what they have in common:
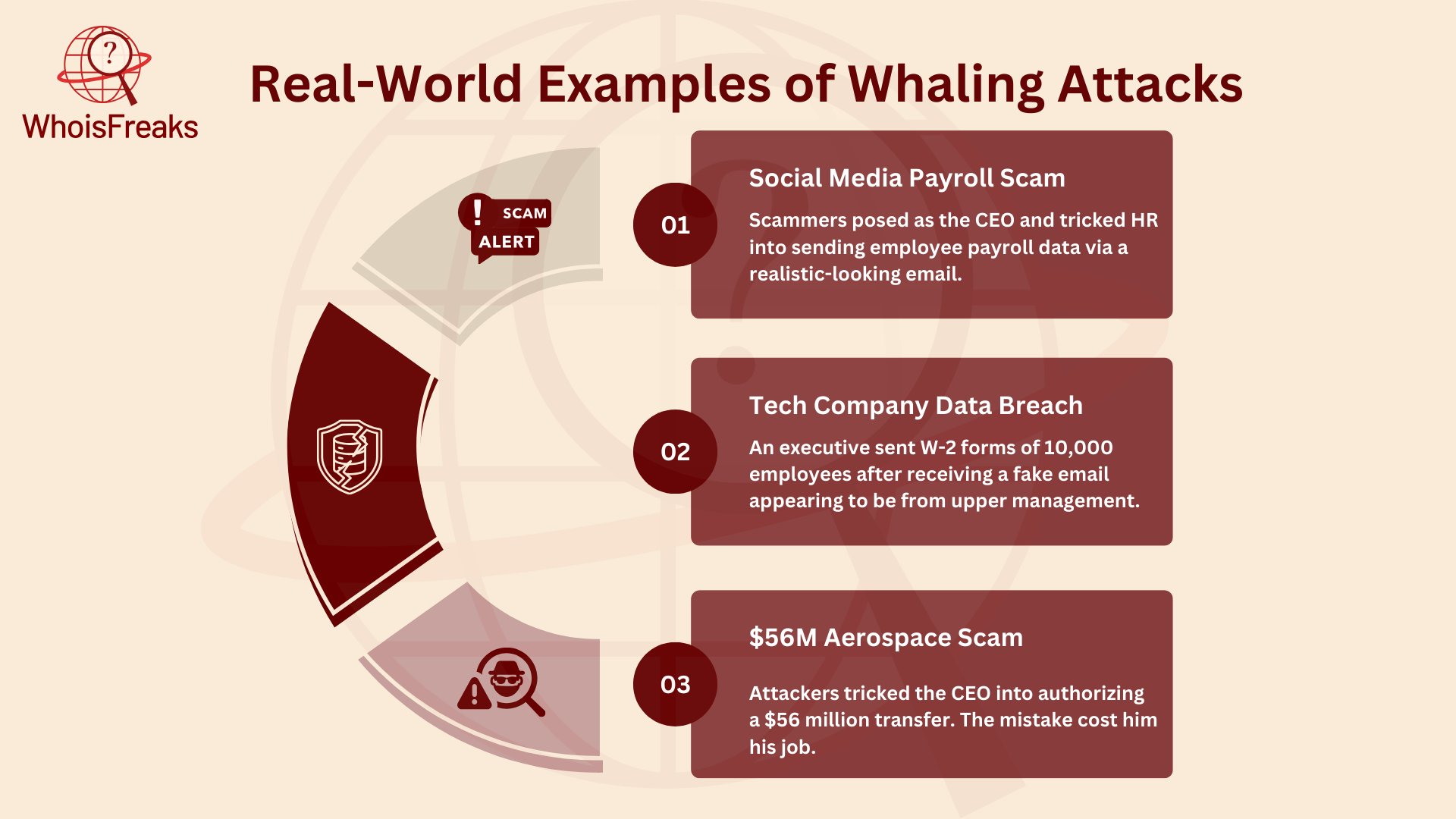
A famous social media company had a high-ranking employee in its HR department targeted by scammers. The fraudsters sent a very convincing email to someone in the payroll department, pretending to be the company’s CEO. The email asked for payroll details, and since it looked so real, the employee sent over sensitive payroll information, thinking it was a legitimate request.
In another case, scammers went after a top finance executive at a well-known tech company. They sent an email that was made to look like it came from the company’s top management. The email asked for W-2 forms from all current and former employees. The executive thought it was a real internal request and sent the information. This breach exposed the tax details of almost 10,000 employees, putting them at risk for fraud and identity theft.
One of the most talked-about whaling attacks happened when the CEO of a well-known aerospace company was tricked into falling for a scam. The attackers sent a series of emails pretending to be senior executives, making it seem like a legitimate business transaction. Believing it to be real, the company’s finance team transferred $56 million to the fraudsters’ account. This led to the CEO losing his job.
Whaling attacks are a serious cyber threat that target high-level executives and organizations. These attacks can steal sensitive data and cause major harm. However, by staying aware and following some simple steps, like being cautious of suspicious emails, using strong passwords, and securing your accounts with multi-factor authentication, you can protect yourself and your organization. Always be ready to act fast if you think you’ve been targeted, and don’t hesitate to contact experts if needed. Taking these precautions can help reduce the risks and keep you safe from whaling attacks.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Learn how to prevent subdomain takeover with essential strategies and best practices. Protect your online assets—read the full guide now!
8 min read