

By Qasim
Posted on May 07, 2025 | 12 min read
In today’s world, where cybersecurity threats are growing every day, session hijacking is one of the most dangerous and hard-to-detect attacks. This type of attack lets cybercriminals take over a user’s active session without the user knowing. Once they have control, attackers can gain unauthorized access and pretend to be the user, access private data, and even take over accounts.
For businesses, especially those that manage user logins and access, understanding session hijacking is very important for ensuring online security. In this blog, we’ll explain what session hijacking is, how it works, and the different types of attacks. We’ll also discuss how to prevent these attacks and share some real-life examples. Finally, we’ll highlight the best ways to defend against this threat. By the end, you’ll have a better understanding of how to protect your applications and users from this serious risk.
Session hijacking is a harmful act where a bad actor takes over a user's web session. This happens by stealing a session token. A valid session token is a unique ID that keeps communication safe between two endpoints. The attacker uses this token to pretend to be the real user and gain access to sensitive info and services.
This attack can happen in many ways, like by listening in on network traffic or using tricky phishing methods. Once the attacker has control, they can do a lot of damage. They can steal identities, commit fraud, and break into private messages. As more people use the internet for things like banking, shopping, and chatting, the impact of session hijacking grows.
The damage from session hijacking can be serious. It affects both personal and business online safety. Protecting against this type of attack is important for data security to keep our information safe and secure online.
A session ID, or session token, is a unique ID given to every session on a website. This ID helps track what the user does during their session. It is usually stored in a cookie or added to the URL as a query parameter that the web server recognizes. This way, the server can remember the user and keep the session running smoothly, even as the user moves between different pages.
The session ID helps the server store important data, like user preferences, shopping cart contents, and temporary login details. This information is safely kept on the server and linked to the user’s session ID. However, if a bad actor steals the session ID, they could pretend to be the user and steal sensitive data, accessing their information and performing actions the user is allowed to do.
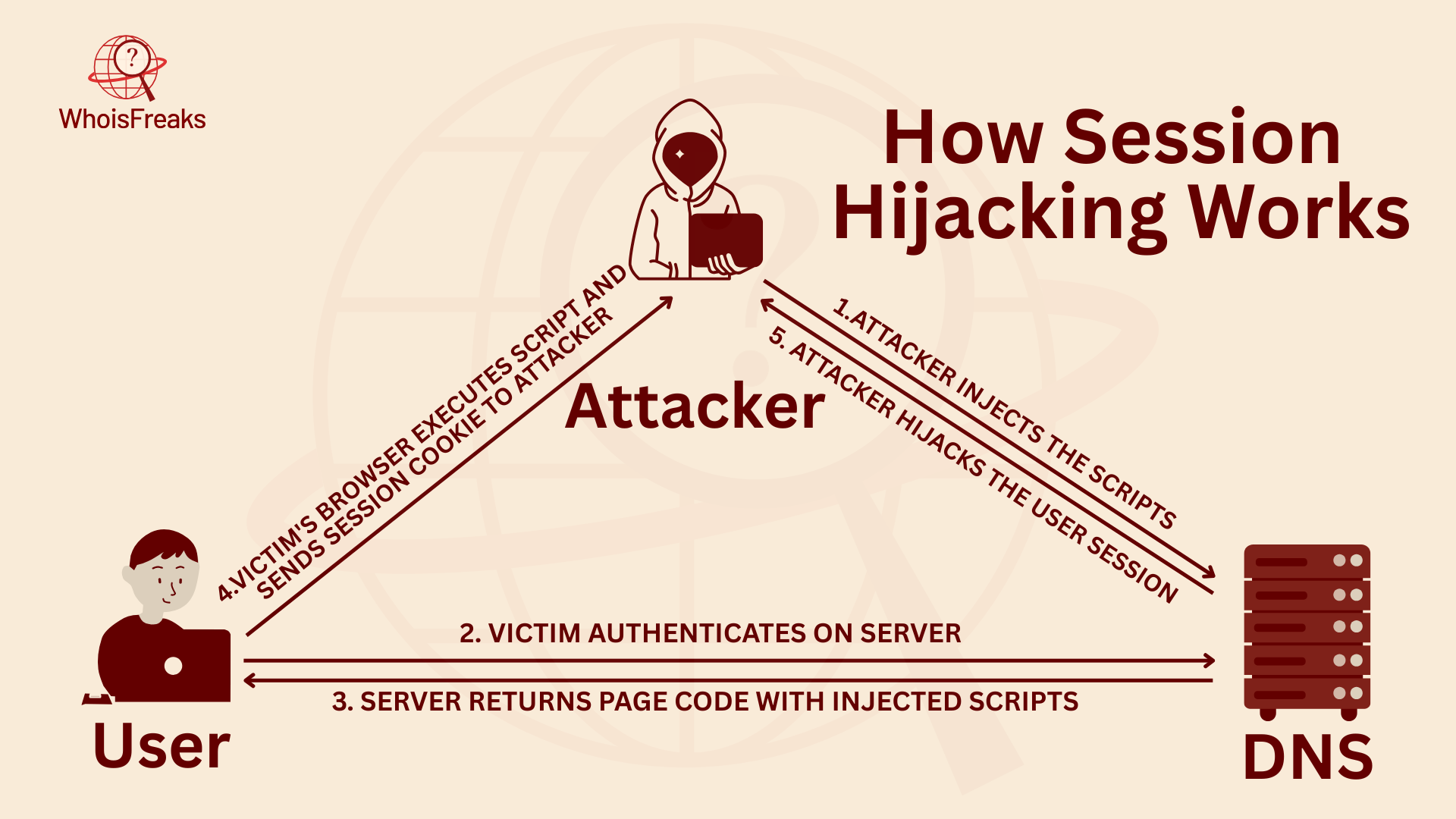
When a user logs in, a session key is created. This key helps the server know who the user is and keeps them logged in. It acts like a special security token that the client sends whenever needed during the session. The main goal of an attacker is to take over this session. While there are different ways to do this, a typical session hijacking attack usually follows these steps:
Session hijacking is very dangerous for website security. It can cause huge harm to both users and websites. A hacker can steal sensitive user info, like account details, login passwords, personal data, and transaction history. This stolen data can lead to bad activities like identity theft and financial fraud.
Losing sensitive data, such as credit card info and business secrets, can damage the website's reputation. It can also bring legal and financial problems. Session hijacking lets attackers make fake purchases or transactions for the user. These fake actions can cause financial losses and hurt both the user and the website.
The danger of session hijacking is that it’s hard to spot, making it especially dangerous in active attacks. The hacker can control the user’s account without leaving a trace. This makes it tough to know when the session is hijacked. The user might stay unaware, which makes it harder to stop the attack.
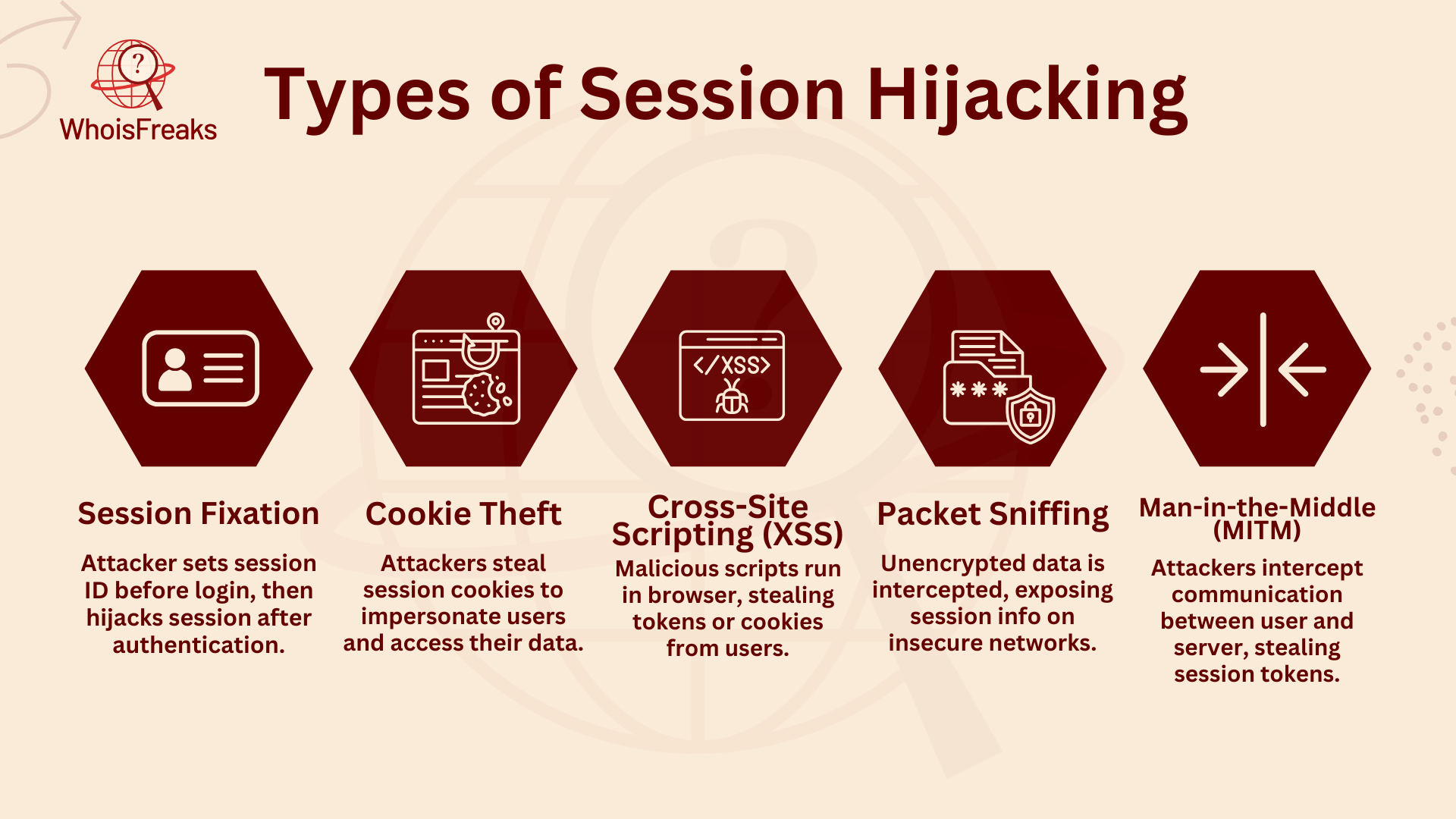
Session hijacking can occur in various forms, with attackers utilizing different techniques to intercept or steal session tokens. Let’s explore the most common types of session hijacking:
Session fixation happens when an attacker sets a session ID for the victim before they log in. The attacker tricks the victim into using this ID. Once the victim logs in, the attacker can take over the session. This is risky if session IDs are not properly reset after login. Proper token regeneration and security are key to protecting against this attack.
Cookie theft is when attackers steal session cookies. These cookies store session info in apps. If cookies are not secured with HttpOnly or Secure flags, attackers can use Cross-Site Scripting (XSS) to steal them. Once they have the cookies, they can act like the user. To avoid this, websites must secure cookies and use strong app security practices.
Cross-Site Scripting (XSS) is when attackers put harmful scripts on trusted websites or apps. These scripts run in the user's browser and steal session tokens or cookies. Attackers often trick users with social engineering, making them visit fake sites or click bad links. Strong website security and user awareness are the best ways to stop XSS.
Packet sniffing is when attackers capture unencrypted data between the user and the server. They use network tools to get session tokens sent over unprotected HTTP connections. This is common on public Wi-Fi. To prevent it, use HTTPS and encryption to protect session data.
A Man-in-the-Middle (MITM) attack happens when an attacker secretly listens to and changes messages between the user’s browser and the server. They can steal session tokens in the process. MITM attacks are dangerous on unsecured networks or if the website doesn’t use encryption. Using HTTPS and encryption helps reduce MITM risks, while also allowing systems to monitor network traffic for any suspicious activities.
Session hijacking can cause big problems for both people and companies. For individuals, it means someone could get into their accounts. This puts personal info at risk and may lead to money loss. For companies, the damage can be worse. If private data is stolen, it can hurt customer trust. This could lead to big money losses and harm to the company’s name.
For companies, the risks go beyond quick losses. A breach of trust can make customers leave. It can also damage the company’s brand. Companies may also face fines and legal issues, making things worse. The effects of session hijacking can last for a long time. Both the company’s money and reputation could be hurt for a long while.
Spotting a session hijacking can be hard because attackers try to stay hidden. But there are signs that something might be wrong, like strange activity on the account or unusual patterns in the session.
The good news is there are tools and techniques that help detect session hijacking. For example, Intrusion Detection Systems (IDS) can watch network traffic and look for signs that session tokens are being misused. Also, systems that detect unusual behavior can warn admins about strange session activity that might mean someone is trying to hijack a session.
Just having detection systems in place isn’t enough. It's important to keep an eye on things all the time and do regular security checks to find security vulnerabilities a weakness before attackers can use them. Security teams should be on the lookout for things like:
Organizations need strong security to stop session hijacking. A key step is managing how long sessions last. Different apps have different rules for session length. For example, social media apps may keep users logged in for weeks. However, banking or healthcare apps should log users out quickly due to the higher risk of session hijacking from inactivity.
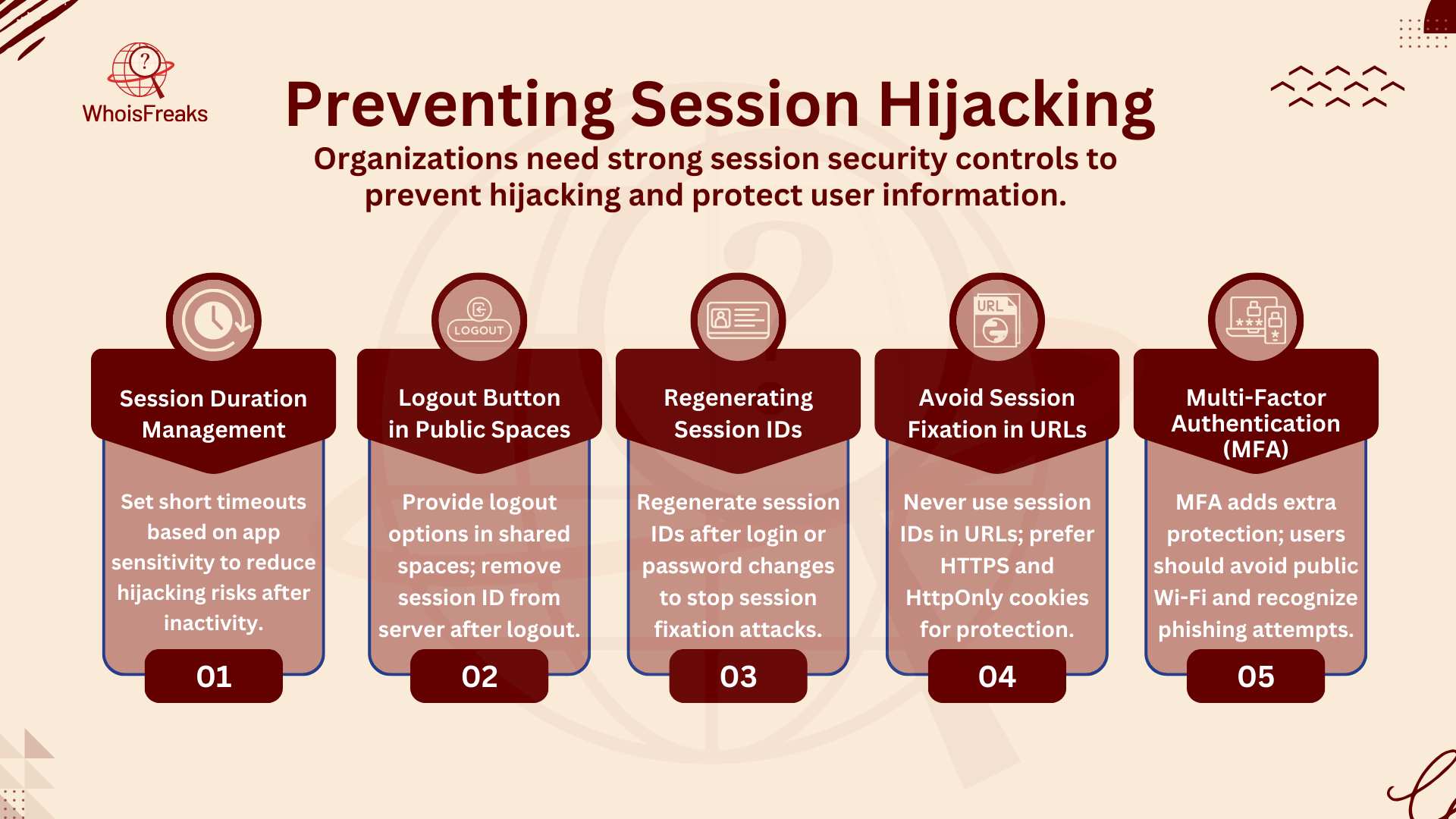
Developers must set session times based on how sensitive the app is. Shorter session timeouts make it harder for attackers. If a session ID is stolen, it only works for a short time. Automatically logging users out after inactivity or detecting suspicious actions, like a change in IP address, can also help.
In shared or public spaces, it’s important to have a logout button. This lets users end their session safely. The session ID should be deleted on the server once the user logs out. This way, even if an attacker gets the session ID, it can't be used again.
Changing session IDs at key points, like after login or password change, helps stop session fixation. This means attackers can’t use a stolen session ID to hijack the session. All session tokens should be removed when the session ends.
To avoid session fixation, don’t accept session IDs in URLs or GET/POST variables. Always use HTTPS to protect the whole app, not just the login page. HTTPS stops attackers from sniffing session IDs. Also, make session ID cookies HttpOnly to lower the risk of cross-site scripting attacks, which can be a vector for phishing attacks.
Multi-factor authentication (MFA) adds extra protection. Even if an attacker hijacks a session, they’ll still need another way in. Users should use secure devices and avoid public Wi-Fi. Public Wi-Fi is often unsafe and lets attackers steal session IDs. Teaching users about phishing and how to spot fake emails, links, or websites can help stop session hijacking that often involves malicious code.
| Type of Attack | What It Is | How the Attacker Does It |
|---|---|---|
| Session Hijacking | Stealing a session ID to pretend to be the user. | The attacker grabs an existing session ID and uses it to access the victim's account. |
| Session Spoofing | Creating a fake session to trick the server. | The attacker makes a fake session ID and tries to get the server to accept it as valid. |
| Session Fixation | Forcing the user to use a set session ID. | The attacker sets up a session ID and tricks the user into logging in using that specific ID. |
If a session hijacking attack happens, a fast response and recovery plan are key. The organization must quickly end all active sessions to stop any compromised sessions. This ensures that attackers cannot keep using stolen sessions and that any access to the user's web browser is secured. After that, the organization should reset session tokens and ask users to log in again. This helps create new, secure session IDs for future sessions.
Next, the organization should ask users to change their passwords. This will stop attackers from using stolen passwords to access accounts. A full investigation is needed to find the cause of the attack and how bad it is. Internal and external security teams should look at logs, network traffic, and system settings to understand how the attack happened. This helps the organization learn and get better at stopping future attacks.
Based on what is found in the investigation, the organization should update security rules and fix any weak spots. These fixes may include using stronger encryption, better network separation, and patching any vulnerabilities. This will help the organization stay safe and ready for future threats.
Session hijacking is not just a risk it has happened in real cyberattacks. These examples show how harmful it can be for users, businesses, and governments.
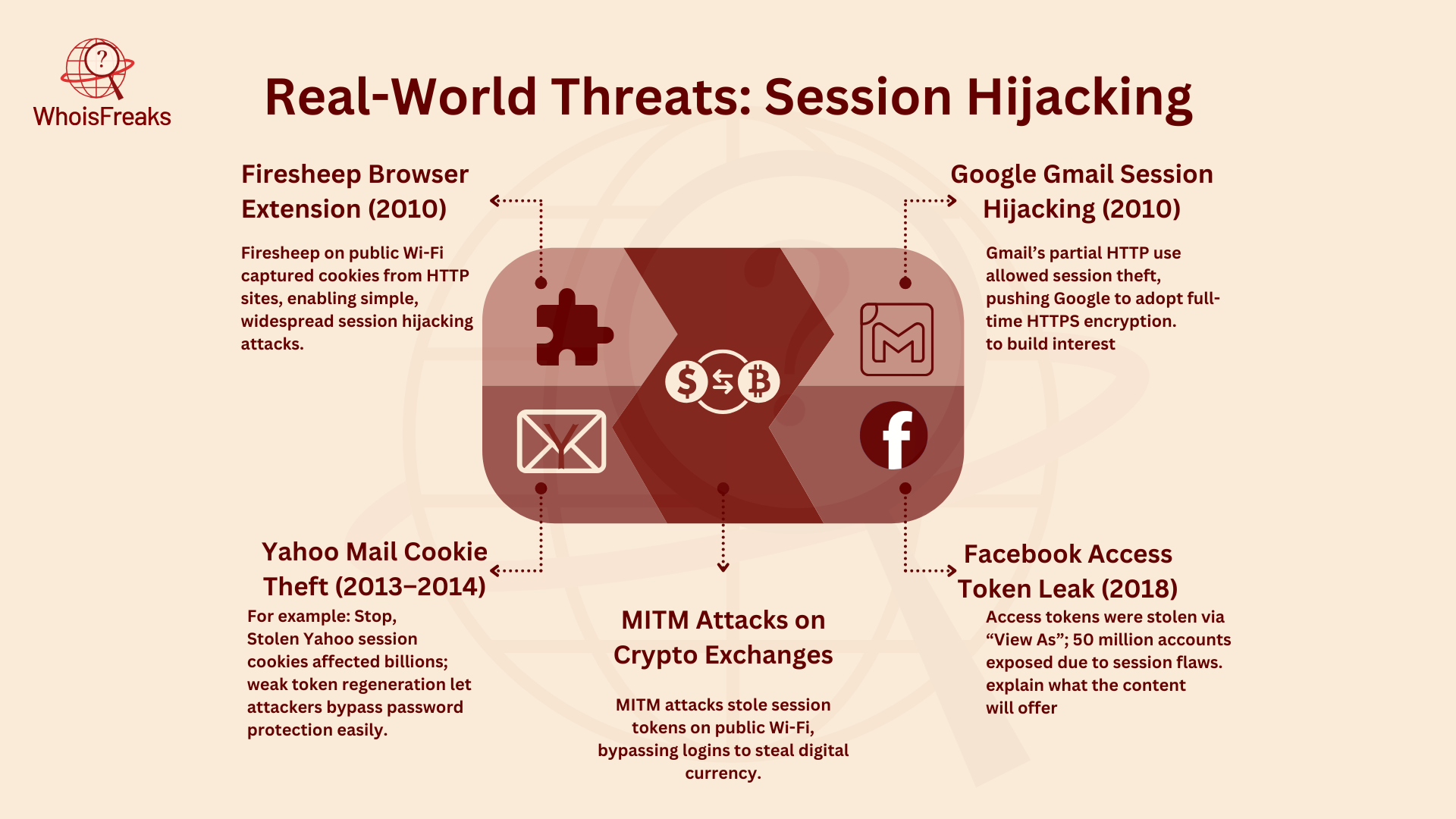
In 2010, the Firesheep browser extension made it easy for attackers to hijack sessions on public Wi-Fi. Firesheep allowed anyone on the same network to capture session cookies from users on websites like Facebook and Twitter. The problem was that many websites still used HTTP instead of HTTPS. This made it easy for attackers to take over sessions. The attention this incident got led to more websites using HTTPS to improve security.
In 2010, researchers found that Gmail was vulnerable to session hijacking. While Gmail used HTTPS, some parts of the site still used HTTP. This flaw let attackers steal session cookies and access users’ email accounts. This made Google and other companies switch to "always-on HTTPS," which made all data encrypted and reduced the risk of session hijacking.
From 2013 to 2014, Yahoo faced a huge cyberattack where attackers stole session cookies. They used these cookies to log into users’ accounts without needing passwords. The attack affected 3 billion accounts. Yahoo had a problem because it didn’t regenerate session tokens. This attack showed why it’s important for companies to change session IDs and disable old ones to stop hijacking.
Cryptocurrency exchanges were also targeted by Man-in-the-Middle (MITM) attacks. In these attacks, attackers intercepted web traffic to steal session tokens. They used these tokens to impersonate users and steal cryptocurrency. These attacks mostly happened on public Wi-Fi networks. Without multi-factor authentication (MFA), attackers could use a man in the browser technique to pretend to be users and make unauthorized transactions. This showed the need for MFA and secure VPNs to protect valuable assets like cryptocurrency.
In 2018, Facebook had a security issue where attackers stole access tokens. These tokens act like session tokens. The leak affected 50 million Facebook accounts. The issue was in the "View As" feature, which showed users how their profiles looked to others. Attackers exploited this flaw to hijack user sessions. Facebook responded by logging users out and making them log back in. This breach showed how important it is to manage tokens well and watch for unusual session behavior.
In conclusion, session hijacking happens when an attacker takes control of a real user’s session ID. They use it to pretend to be the user and do things without permission. There are many ways attackers can do this, like session sniffing, cross-site scripting, session prediction, and session fixation. To stop these attacks, it's key to follow good tips to keep sessions safe. By using best practices, companies can lower the chances of session hijacking and keep user sessions secure.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Learn how to prevent subdomain takeover with essential strategies and best practices. Protect your online assets—read the full guide now!
8 min read