

By Qasim
Posted on May 08, 2025 | 13 min read
In this article, we will explain what a man-in-the-middle attack is and look at the different types of these attacks, including those employed by various MITM attackers. We’ll also talk about why these attacks are dangerous and give you some examples. By the end, you will understand how a man-in-the-middle attack happens and learn how to spot and stop it.
A man-in-the-middle (MITM) attack is a type of cyber-attack that poses significant challenges to cyber security. In this attack, a threat actor gets between a user and an app. They do this to intercept messages and data. The cybercriminal can change the information to do bad things, like making unauthorized purchases or hacking.
These attacks often target sensitive data, like login credentials and financial info, as they aim to collect personal data. The user thinks they are using a trusted system, like a secure website. But the hacker is secretly in the middle.
The hacker can also use website spoofing to trick the user. This allows them to take control of the user's account. Once they have control, the hacker can steal money, commit identity theft, or break into a network. MITM attacks can be risky. Users often don't know their data is being stolen. This gives the attacker full control over important personal and financial information, putting everyone at risk.
A MITM attack generally consists of two phases: interception and decryption.
A MITM attack starts when cybercriminals target a network. They often use an open Wi-Fi router or a poorly secured domain name system (DNS). These attackers look for weaknesses and points of entry. They often exploit weak passwords, use IP spoofing, or do cache poisoning by sending fake arp messages. After finding a target, the attackers use tools to capture data. This allows them to control and change the user’s web experience, like redirecting traffic.
In the second phase, the stolen data is decoded. The cybercriminals can now read it clearly. This decrypted data is used for bad activities like identity theft, making unauthorized purchases, or stealing money from bank accounts. Sometimes, MITM attacks are done just to cause trouble for businesses and victims. The attackers disrupt normal operations, creating chaos while stealing sensitive information.

Email hijacking occurs when cybercriminals gain access to email accounts from trusted organizations, such as banks or financial institutions. Once the attackers take control, they can monitor ongoing transactions and communication between the bank and its customers. In more malicious cases, the hacker spoofs the bank’s email address, sending fake emails that instruct customers to resend their login credentials or transfer money to an account controlled by the attacker. This type of attack relies heavily on social engineering, where the attackers build trust with the victim by mimicking the official email style, increasing the likelihood that victims will follow the attacker’s instructions without realizing it’s a scam.
Wi-Fi eavesdropping is a type of attack in which cybercriminals set up a fake Wi-Fi network, usually near a public hotspot or business, with a name that looks legitimate. It may appear to be a public Wi-Fi network or a nearby café’s network, such as "Free Public Wi-Fi Network." Once a victim connects to the fake network, the attacker can silently observe the user’s online activity. They can capture sensitive information such as login credentials, credit card numbers, or even personal messages. To prevent this, users should always double-check the network they are connected to, ensuring it is a secure connection avoid using public Wi-Fi for sensitive transactions, and disable the automatic connection to Wi-Fi networks when on the go.
DNS spoofing, also known as DNS cache poisoning, is a type of attack where the hacker manipulates the DNS system to redirect users to a fake website. DNS is used to translate website names into IP addresses. In a DNS spoofing attack, the attacker alters the DNS records so that when the victim tries to visit a legitimate website, they are instead sent to a fraudulent, look-alike website. This fake site may prompt users to enter personal information, such as passwords or payment details, under the impression that they are interacting with a trusted service. DNS spoofing is particularly dangerous because it involves redirecting users without their knowledge, allowing the hacker to steal sensitive data like login credentials, bank account information, or personal identification numbers.
Session hijacking happens when a hacker steals a valid session cookie from a victim who has logged into a website or an application, such as online banking or email services, especially if multi factor authentication is not implemented. A session cookie is a piece of data stored by the web browser that helps identify the user during their session. Once the attacker obtains this cookie, they can impersonate the victim and gain access to the same account without needing to log in. This type of attack is particularly effective because it bypasses the need for usernames or passwords, making it harder for victims to detect. Session hijacking attacks are time-sensitive, as session cookies typically expire after a short period, so attackers must act quickly to steal and use the session before it expires.
SSL hijacking is an attack in which a hacker intercepts data between a user’s device and a secure server. SSL (Secure Sockets Layer) is a protocol used to secure internet communications by encrypting the data being sent between the server and the user. However, older versions of SSL, such as version 3.0, have security flaws that attackers can exploit. The attacker intercepts the SSL connection and decrypts the data being transferred, allowing them to access sensitive information such as login credentials, personal details, or payment information. SSL hijacking is particularly concerning because SSL is a widely trusted security protocol, and users assume their data is safe when connected to a website with "HTTPS" in the URL. The vulnerability in SSL is a reason why it was replaced by TLS (Transport Layer Security), which is now considered more secure.
ARP (Address Resolution Protocol) cache poisoning involves deceiving a victim’s device into thinking that the attacker’s computer is the network gateway. ARP is used to map the IP address to the MAC address of devices within a local network. In this attack, the hacker sends false ARP messages, causing the victim’s computer to route its network traffic to the attacker’s device. Once the attacker intercepts the traffic, they can access any sensitive data being transmitted, such as personal identification information (PII), login credentials, or private communications. This attack is particularly dangerous on local area networks (LANs) and can be difficult to detect since the victim’s device continues to function normally but with traffic flowing through the attacker’s device.
IP spoofing is a technique used to make the attacker’s computer appear as though it is a trusted source by changing its IP address to match that of a legitimate website. This form of attack is similar to DNS spoofing, but instead of tampering with DNS records, the attacker alters the IP address to make the malicious site appear to be a trusted site. When users visit the fake website, believing it to be real, they may unknowingly enter personal data or engage in harmful activities like transferring money or submitting sensitive documents. IP spoofing can be difficult to detect because it appears as if the traffic is coming from a trusted source, allowing attackers to steal data or launch more complex attacks.
Stealing browser cookies involves hackers gaining access to the cookies stored in a victim’s web browser. Browser cookies contain important information such as saved login details, passwords, credit card numbers, and other sensitive data. Attackers often use other MITM techniques like Wi-Fi eavesdropping or session hijacking to gain access to the victim’s device and steal these cookies. Once the hacker has the cookies, they can impersonate the victim on various websites and access their accounts without needing to know the login credentials. This attack is dangerous because it gives attackers access to all the personal and financial data stored in the victim’s browser, making it an effective method for identity theft and financial fraud.
Both consumers and businesses can be at risk of MITM attacks. Customers are most at risk when they are tricked into using a fake Wi-Fi network, visiting a fake website, or using a hijacked email account. This can lead to their personal information being tracked, stolen, and misused. Users of websites or apps that need login details or store financial data are easy targets for these attacks, as cybercriminals want to steal valuable personal and financial information.
Businesses also face serious risks. Companies with websites and apps that store customer details are big targets. A successful MITM attack can slow down business operations, forcing companies to spend resources fixing the attack. After the attack, businesses also have to deal with legal issues and work hard to regain trust. For this reason, businesses must focus on finding and stopping MITM attacks to protect their operations and their reputation.
MitM attacks are a big threat to businesses today, especially with more people working from home, using mobile devices, and connecting to different networks. The increase in IoT device use and the reliance on unsecured Wi-Fi connections make things worse. The 2022 Cybersecurity Almanac reported that cybercrime caused $6 trillion in damage in 2021, and this could reach $10 trillion a year by 2025, according to Cybercrime Magazine.
Businesses are at high risk from MitM attacks, which can lead to stolen login info and personal credentials. Attackers can also install harmful software updates, which contain malware, during an attack. Unencrypted messages, especially those sent over weak network connections on mobile devices, are easy to intercept. Business News Daily says that cyber-attacks on small businesses cost an average of $55,000 in losses, showing just how much these attacks can hurt businesses financially.
Detecting a Man-in-the-middle (MITM) attack requires taking the right steps to look for signs that your communications have been intercepted. Without checking, these attacks can go unnoticed until it's too late. One of the main ways to find a MITM attack is by checking if the page is properly authenticated and setting up tamper detection. These methods may require extra work, like forensic analysis, to confirm if an attack happened.
It’s also important to take steps to stop MITM attacks before they happen, instead of trying to find them while they are going on. Being careful about your browsing habits and knowing the weak spots in your network can help keep your system safe and stop hackers from accessing sensitive data.
Man-in-the-Middle (MitM) attacks are a big risk to your privacy and security. They happen when hackers secretly intercept and change messages between two people. To protect your data, it’s important to take steps to prevent these attacks. Here are some ways to keep your online activity safe.
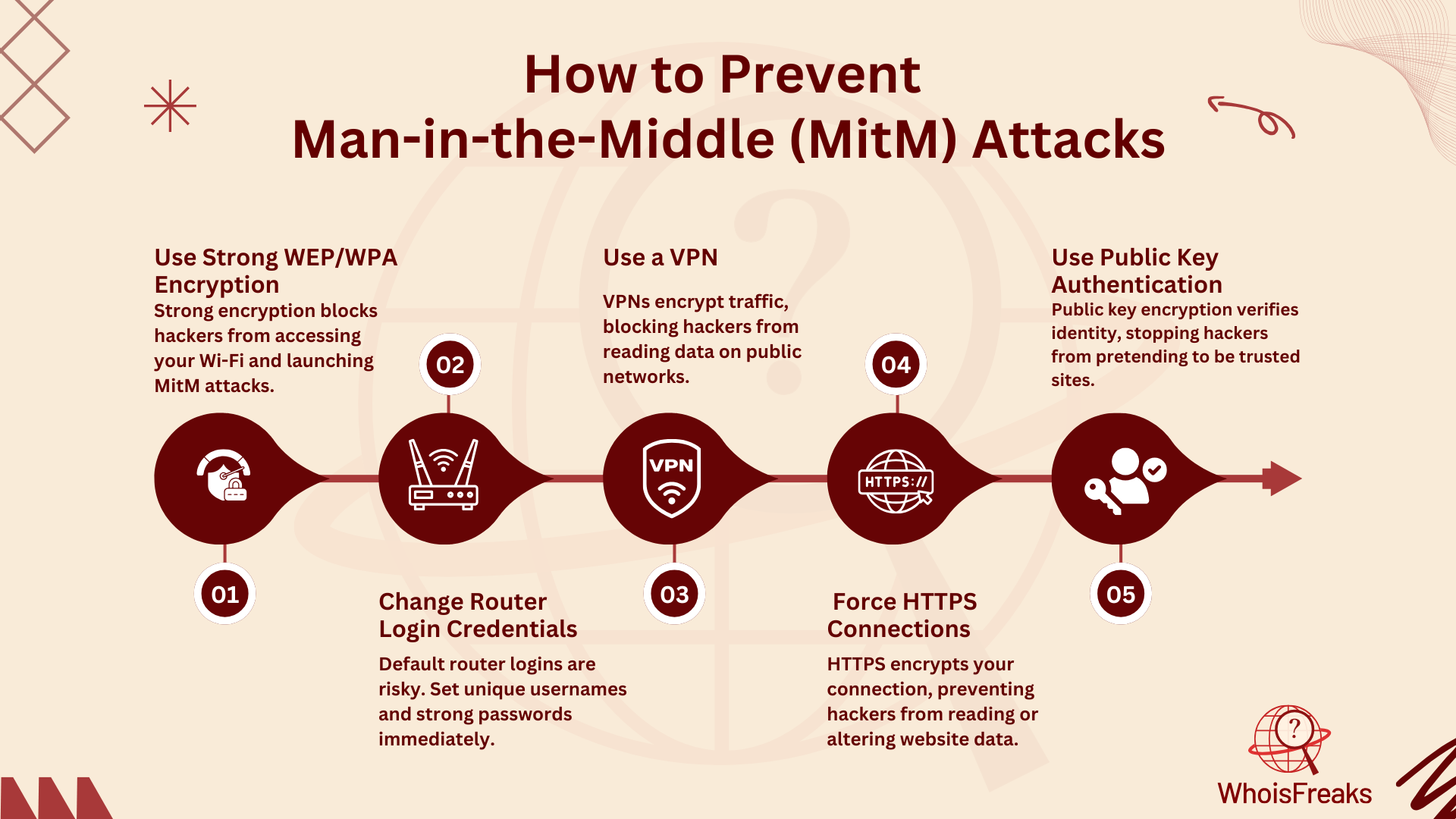
Using strong encryption on your wireless access points helps keep unwanted users from joining your network, even if they are nearby. A weak encryption method can let an attacker easily break in and start a Man-in-the-Middle (MitM) attack. The stronger the encryption, the harder it is for attackers to hack into your network. Using hypertext transfer protocol secure (HTTPS) keeps your information safe from being stolen or tampered with.
It is very important to change the default router login credentials. This means not just your Wi-Fi password but also the login information for your router itself. If attackers get access to your router login, they can change your DNS settings to their malicious servers, or even worse, install harmful software on your router. By changing the default credentials, you make it much harder for attackers to break in and mess with your network.
A VPN is a tool that helps protect your sensitive information while it travels through a network. It creates a secure "tunnel" that encrypts your data so that even if an attacker gets on the same network, they won’t be able to read or steal your information. VPNs are especially useful for protecting your data when you use public Wi-Fi or shared networks, as they help analyze network traffic. They provide an extra layer of security that makes it much harder for hackers to track your activity.
Using HTTPS instead of HTTP makes online communication much safer. HTTPS uses encryption between your browser and the website, so hackers can't read or change the data being sent back and forth. Websites should only allow HTTPS connections and avoid using the less secure HTTP. You can also use browser plugins to make sure your browser always uses HTTPS when visiting websites, ensuring your data stays safe from hackers.
In MitM attacks, hackers often pretend to be someone else, like a trusted website. To prevent this, public key pair-based authentication, such as RSA, can be used to confirm the identity of the systems you are communicating with over the internet protocol. This method ensures that you are talking to the right server and not a fake one set up by an attacker. Using public key authentication adds another level of protection, making it harder for hackers to trick you into giving them your data.
In 2013, Edward Snowden leaked documents that showed the National Security Administration (NSA) was using a MitM attack. They did this by pretending to be Google, which is how a MITM attacker intercepts traffic. This allowed the NSA to collect search records from Google users, including Americans, as part of illegal spying on U.S. citizens. A similar attack happened when Comcast used JavaScript to insert its ads into web traffic, replacing third-party ads. This is called code injection, another type of MitM attack.
One well-known MitM attack happened in 2017 with Equifax, a major credit history company. The attack exposed over 100 million customers' financial data to criminals for several months. Another attack targeted banking apps used by banks like HSBC, NatWest, Co-op, Santander, and Allied Irish Bank. This flaw let criminals steal personal information, including passwords, pin codes, and other credentials.
These MitM attacks led to some of the biggest data breaches. For example, Cognate’s breach exposed five billion records, while Twitch also had five billion records leaked. LinkedIn had 700 million records compromised, and Facebook’s breach affected 553 million records. These incidents highlight the serious impact of MitM attacks on both personal and business data security.
Cybercriminals, researchers, and IT professionals often use a range of tools to test security in IT environments. These tools simulate attacks to check if systems are secure, especially against Man-in-the-Middle (MITM) attacks, and can be complemented by security software. Some of the most popular MITM tools are:
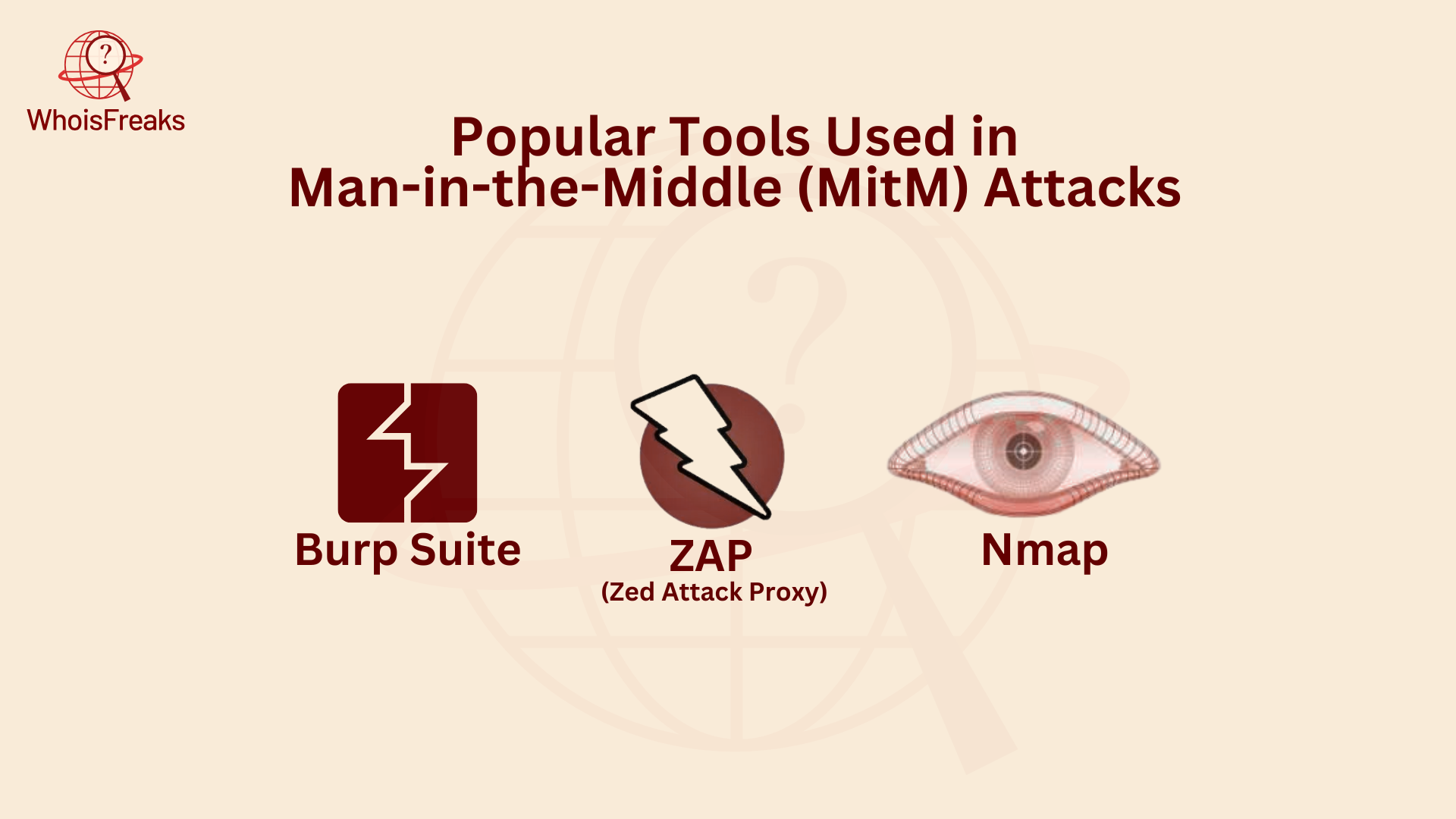
These tools are essential for intercepting, analyzing, and manipulating network traffic to detect security flaws. By using them, professionals can better understand the risks and protect against MITM attacks.
In conclusion, Man-in-the-Middle (MitM) attacks can be harmful and put your personal information at risk. However, by taking simple steps like using strong encryption, changing router login details, using a VPN, enforcing HTTPS, and using public key authentication, you can greatly reduce the chances of falling victim to these attacks. Staying aware of your network's security and making these changes can help protect your data and ensure a safer online experience.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Learn how to prevent subdomain takeover with essential strategies and best practices. Protect your online assets—read the full guide now!
8 min read