

Posted on April 08, 2025 | 21 min read
Cybersecurity is more important than ever before. As technology grows, so do cyberattacks. These attacks happen more often and are becoming harder to stop. Cybercriminals use tricks like ransomware, phishing, and malware to hurt people and businesses. These attacks can steal personal information, cause money problems, and disrupt business activities. One of the biggest dangers today is Distributed Denial-of-Service (DDoS) attacks. Unlike ransomware, which locks files, DDoS attacks make websites, and online services stop by sending too much traffic at once.
A DDoS attack is different from other attacks like ransomware. Instead of locking your files or stealing your data, a DDoS attack makes your online services crash by sending an overload of traffic. It’s like a huge crowd showing up to your website all at once, blocking others from accessing it. This causes your website or service to stop working, leaving customers unable to use it. These attacks can last for hours, days, or even longer, hurting your business.
To stop DDoS attacks, it’s important to understand how they work and how to protect your business. We’ll explain what DDoS attacks are, how they happen, and the best ways to stop them. Whether you want to improve your protection or just learn more, this guide will help you. You’ll learn how to keep your business running smoothly, even if an attack happens, and protect your important data from being targeted. With the right steps, you can defend your online services and prevent downtime, so your business stays safe and efficient.

A DDoS attack is a harmful attempt to shut down a server, network, or service by overwhelming it with too much traffic, making it stop working. These attacks can stop services like banking, gaming, and government websites, causing big problems.
As the DDoS attacks continue to grow more complex, companies need strong cybersecurity strategies. These strategies help prevent downtime and keep services up. Using advanced DDoS prevention techniques, businesses can protect their server and network security. By taking proactive steps, they can reduce the impact of these attacks and keep operations running smoothly.
DDoS (Distributed Denial-of-Service) attacks don’t happen by chance. They are planned with clear goals. Some attackers want money, while others aim to make a statement. Knowing why these attacks happen helps businesses stay prepared.
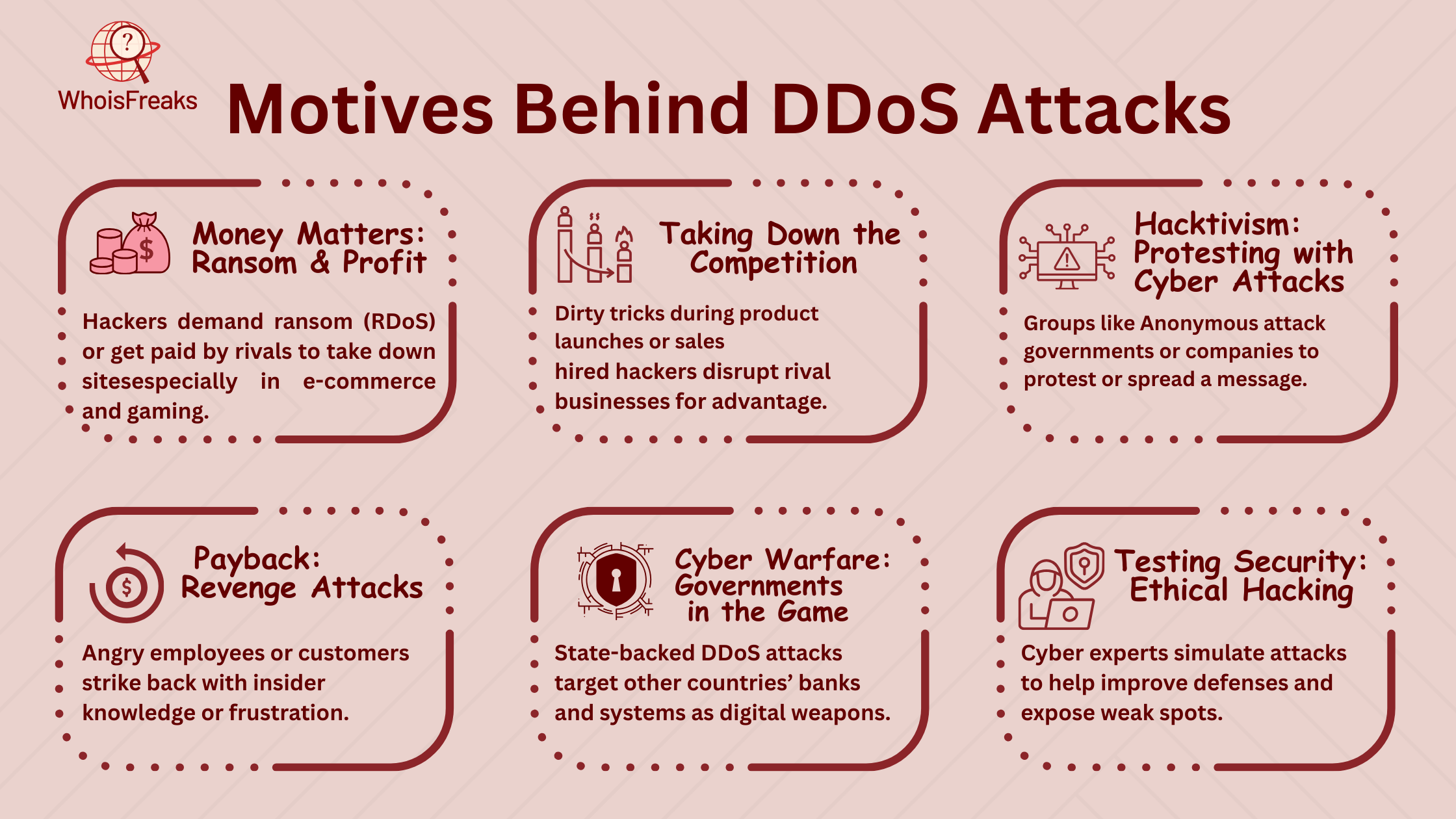
Many hackers launch DDoS attacks to make money. Some demand a ransom to stop the attack—this is called ransom DDoS (RDoS). Others get paid by a company’s rival to bring their site down. This is common in online shopping and gaming, where downtime means lost sales.
Businesses sometimes play dirty. They hire hackers to attack competitors. This slows down websites and causes lost customers. It often happens during big sales, new product launches, or major gaming events. A few minutes of downtime can cost companies a fortune.
Some groups use DDoS attacks to make a statement. Hacktivists, like Anonymous, attack governments, banks, and big companies. They do this to protest, raise awareness, or push for change. These attacks are not about money—they are about making noise.
DDoS attacks are sometimes personal. Angry employees, unhappy customers, or rival hackers may want revenge. A fired worker who knows company secrets might strike back. A frustrated customer might try to shut down a business's site. These attacks can be very damaging.
Countries use DDoS attacks too. State-sponsored hackers attack other nations to weaken them. These attacks target banks, government websites, and security agencies. Some countries use them to test cybersecurity defenses or even spy.
Not all DDoS attacks are bad. Cybersecurity experts test systems by simulating real attacks. This helps businesses find weak spots before criminals do. These tests help improve online security and prevent future attacks.
DDoS attacks have many motives. Whether for money, revenge, or protest, these attacks cause real damage. Understanding them is the first step in staying safe.
Some industries face DDoS attacks more than others. Businesses that rely on the internet are at the highest risk. Hackers attack them for money, competition, or just to cause chaos.
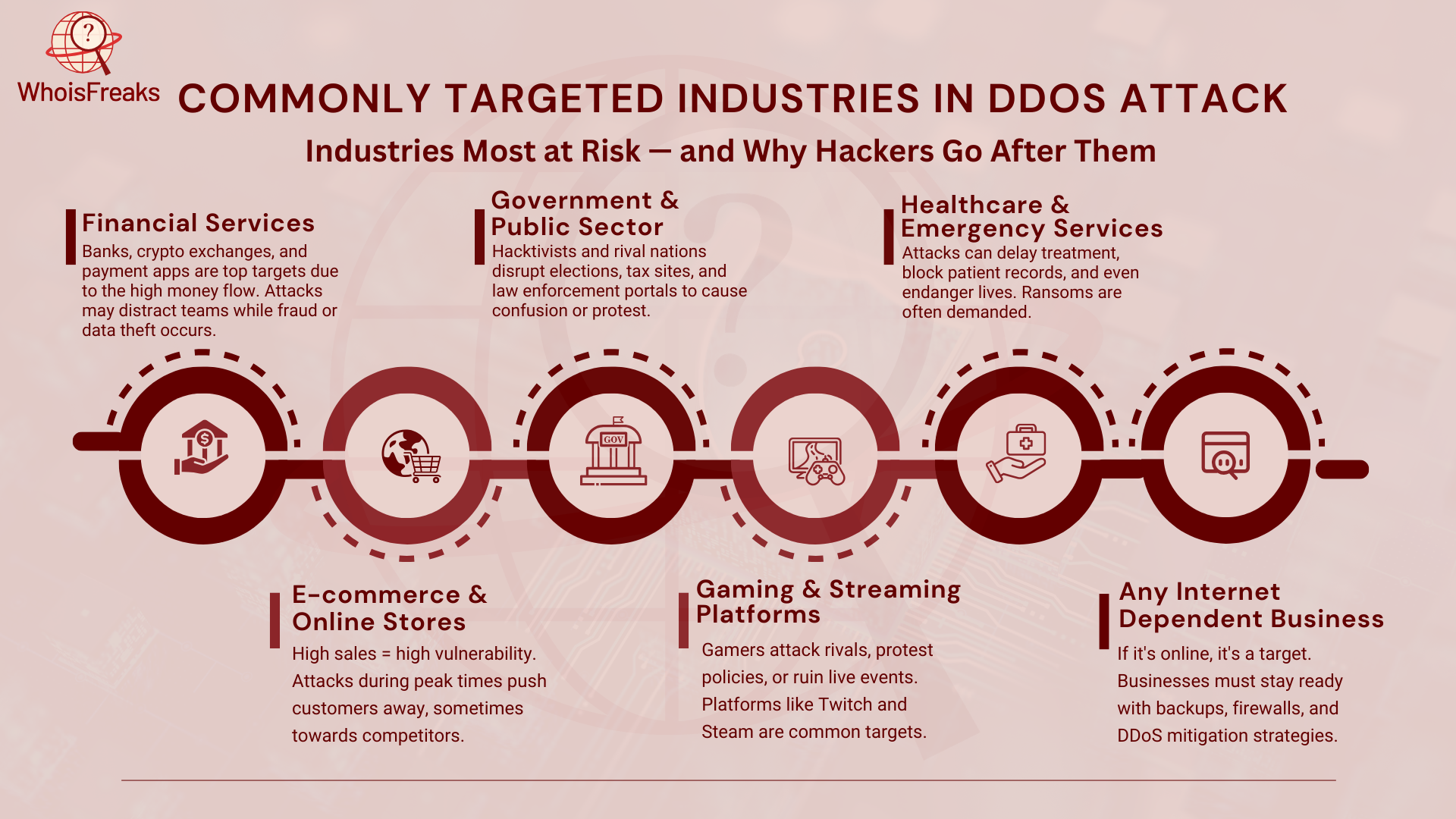
Financial services get hit the hardest. Banks, payment systems, and crypto exchanges handle huge amounts of money. A single attack can cause millions in losses. Hackers often use these attacks to distract security teams while they steal data or commit fraud. Some attackers even demand ransom to stop the attack.
E-commerce and online stores are also prime targets. These platforms get heavy traffic during sales and holidays. Attackers flood websites with fake requests, making it impossible for real customers to shop. This leads to major losses. Some attacks are done by competitors who want to push customers toward their own businesses.
Government and public sector websites are high on the list. Hacktivists and rival nations use DDoS attacks to disrupt important services. They may target tax portals, voting systems, or law enforcement sites. These attacks can spread misinformation, delay elections, or even impact national security.
Gaming and streaming platforms face attacks often. Services like Twitch, Steam, and Netflix are favorite targets. Some hackers overload gaming servers to get an unfair advantage in matches. Others attack platforms to protest policies or take down popular streamers. DDoS attacks can also ruin big gaming events, causing frustration for players and companies alike.
Healthcare and emergency services are at risk too. They use online systems for patient records, ambulances, and remote care. A DDoS attack can block doctors from records, delay urgent care, and risk lives. Hackers may also demand ransom from hospitals.
Hackers target industries where disruptions cause big problems. These businesses must stay ready, improve security, and react fast to attacks.
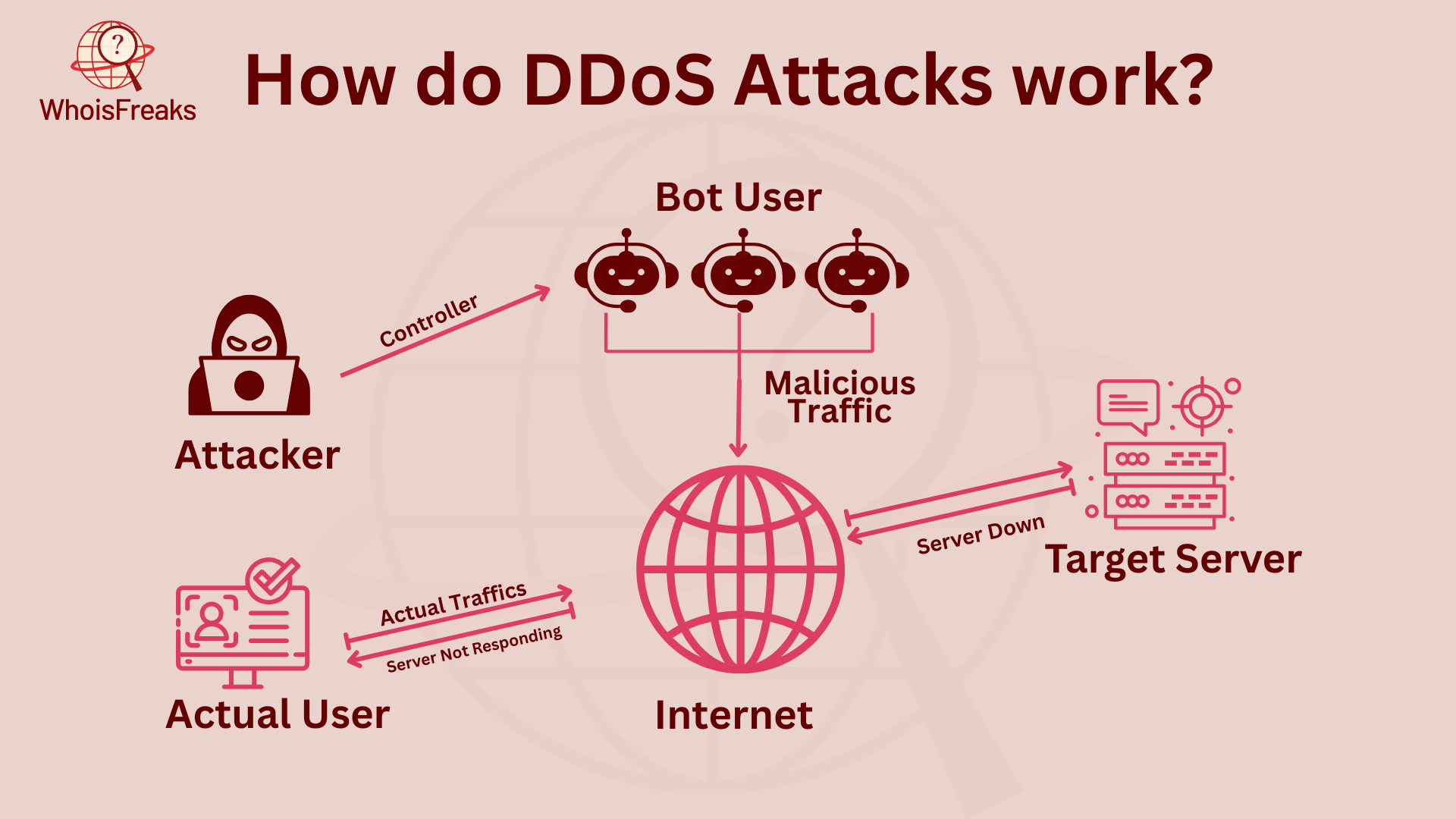
DDoS attacks are carefully planned to cause the most damage. Attackers often use cloud services or rent botnets to grow their attacks fast, making it hard for businesses to detect and stop them in time. Here’s how they work:
A DDoS attack begins by creating a botnet, a group of hacked devices controlled by the attacker. These devices can be personal computers, smartphones, IoT gadgets, or servers. Attackers use malware, often through phishing emails or risky downloads, to take advantage of software flaws.
Once the devices are infected, they become bots that follow the attacker’s commands. The botnet sends massive malicious traffic toward the target. The attack is stronger because it uses a lot of devices, often from places that are harder to detect.
Once the botnet is set up, the attacker picks a target, usually a business, website, or online service that relies on its system to work. The attacker’s motive may be to harm a competitor, demand ransom, disrupt services with fake traffic, or make a political statement.
Before the attack, the attacker carefully studies the target’s network to find weaknesses. They look for weaknesses like unpatched servers, not enough redundancy, or limited bandwidth. These vulnerabilities help the attacker make the attack more effective.
Once the target is chosen, the attacker uses a botnet to send huge amounts of traffic to overwhelm the target. The goal is to block real traffic by using up the target’s network, computing power, or server space.
Attackers often use multiple attack vectors to make mitigation more difficult. They may launch the attack during peak business hours for maximum impact. To hide from detection, attackers may change traffic patterns, fake IP addresses, or use encrypted data to bypass security.
A DDoS attack doesn’t stop after one burst of traffic. The attacker keeps sending traffic, sometimes in waves, to keep the target down. The ongoing attack also can last for a long time, forcing the target to deal with constant downtime.
The attacker may use adaptive methods like changing traffic sources or switching attack types to make it harder to stop. These tricks help keep the attack going for as long as possible.
The goal of a DDoS attack is to make the target’s services unavailable. This causes:
Recovery from a successful DDoS attack, can take days or even weeks. The target needs time to fix systems, patch vulnerabilities, and regain the trust of users.
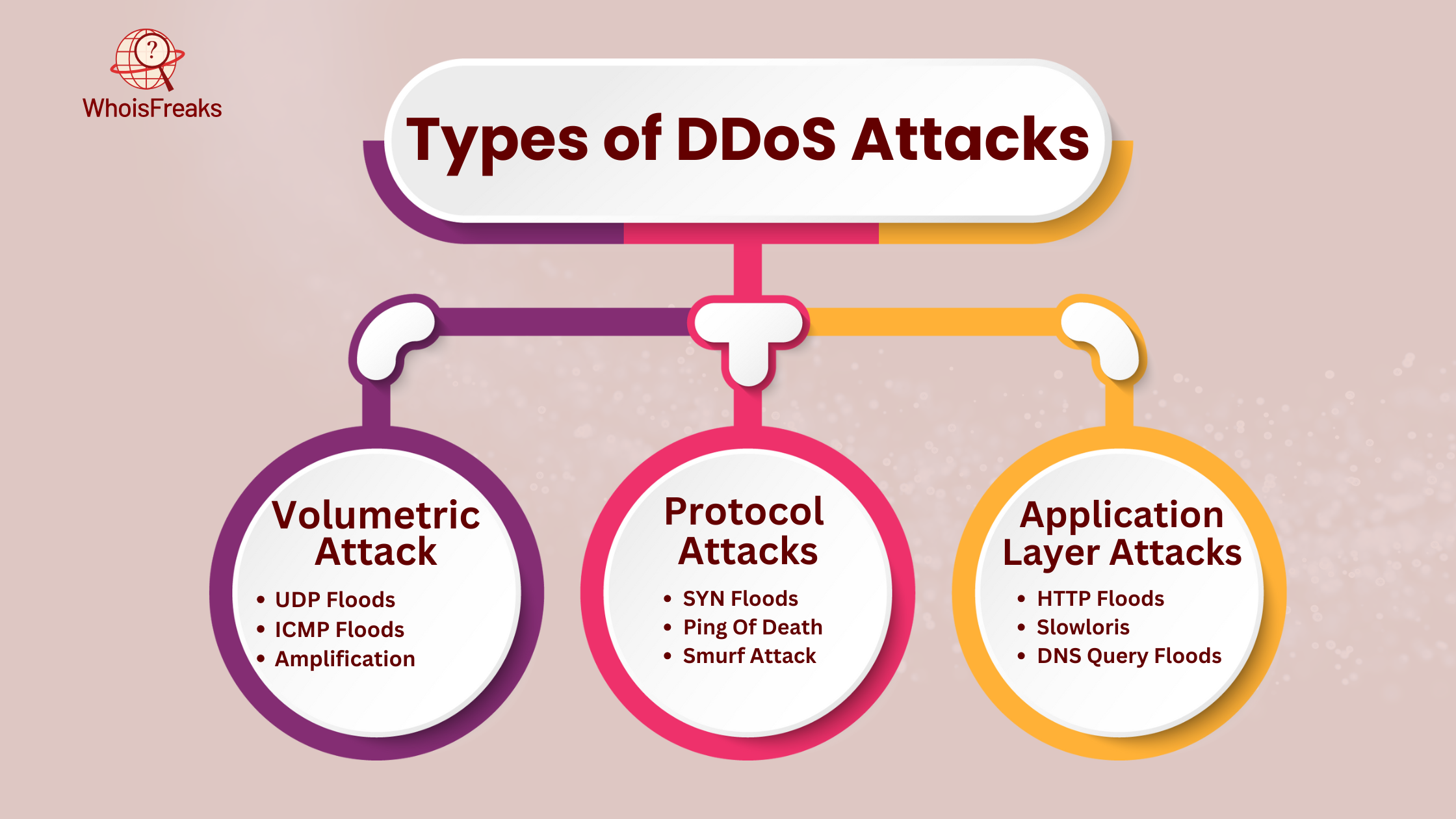
DDoS attacks are of three main types: volumetric attacks, protocol attacks, and application-layer attacks. Let’s take a closer look at each type of volumetric DDoS attack:
Volumetric attacks are a type of cyberattack that flood a network with too much data. This can slow down or stop services, making them unavailable to real users. These attacks overload a company's servers or network in different ways, causing delays or shutdowns.
Here are the common ways volumetric attacks work:
Protocol attacks are a type of DDoS attack. They take advantage of weaknesses in a network. These attacks drain resources like network connections, tables, firewalls, load balancers, and servers. This makes the system slow or stop working, causing problems for users.
Here are the common types of protocol attacks:
Application-layer attacks, or Layer 7 attacks, target the top part of the OSI model. This is where internet services like HTTP, DNS, and SMTP work. These attacks are smart and look like real user actions, so they are harder to catch. Their goal is to use up the target server's resources, causing problems while using less data than other attacks.
Common types of application-layer attacks are:
DDoS attacks are a serious threat to businesses. These attacks can cause both quick and long-term damage. They can hurt a business's finances, reputation, and operations in many ways.
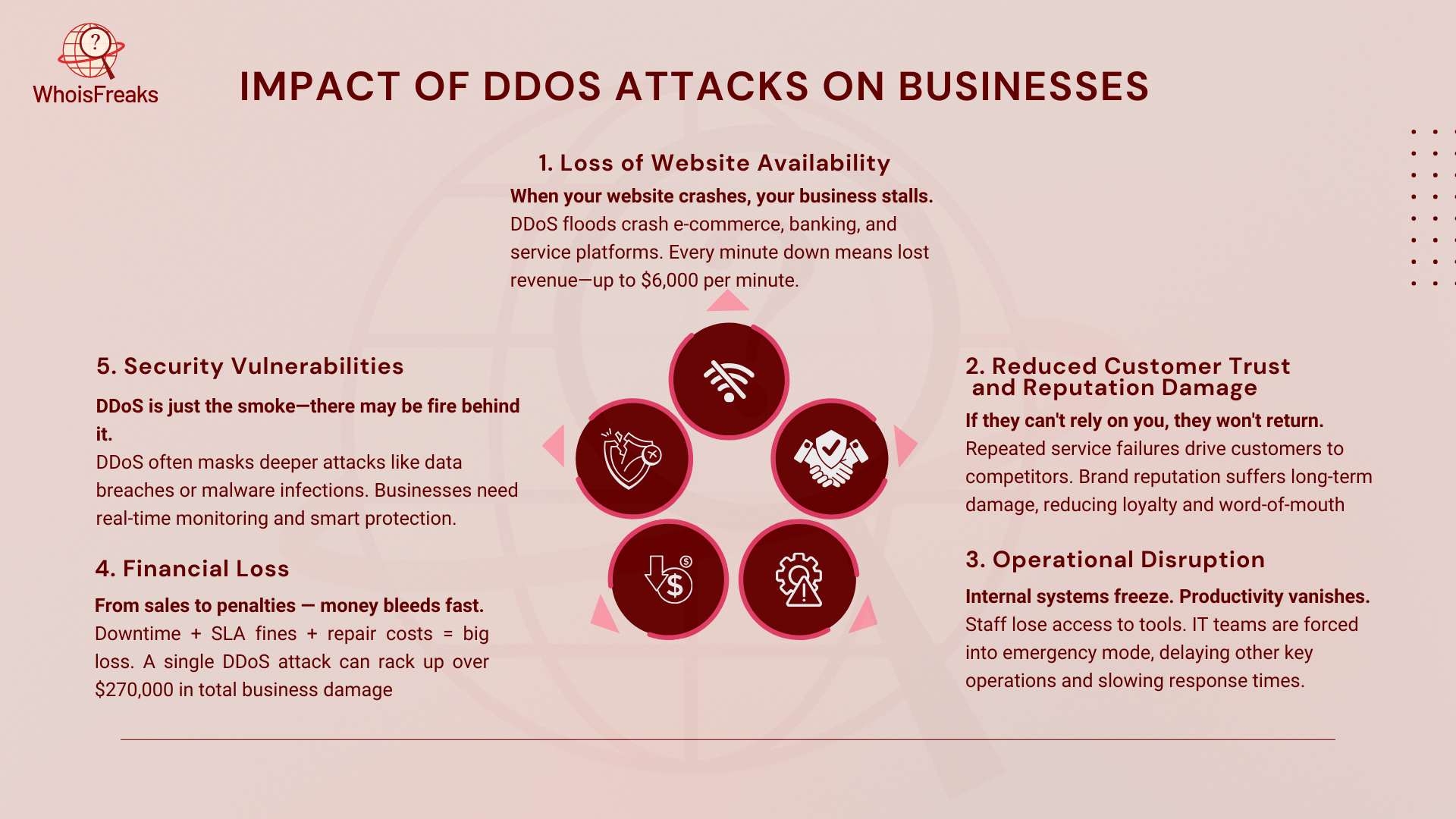
A DDoS attack can stop a website from working. For businesses with e-commerce platforms, financial services, and online services, this is a big problem. Customers can’t access the site, leading to missed sales. The downtime also wastes resources and costs businesses around $6,000 per minute. The total cost can reach $270,000 per attack.
When a business has too many service issues, customers lose trust. If an organization is seen as unreliable, customers may go to competitors. The business’s reputation suffers, which makes it harder to keep clients. This hurts the company in the long run.
DDoS attacks disrupt business operations. Employee productivity goes down when internal systems are affected. IT teams need to focus on stopping the attack. This takes away time and resources from other important work.
DDoS attacks cause financial loss in several ways. Businesses lose money from downtime and recovery costs. There may also be fines for breaching service level agreements (SLA). Big attacks can cost millions of dollars, adding to the losses.
Sometimes, DDoS attacks are just a cover for worse things. They may hide data breaches or the deployment of malware. These attacks expose security risks. To stop them, businesses need DDoS protection with live monitoring and quick automatic actions. This helps keep services running and protects the company's reputation.
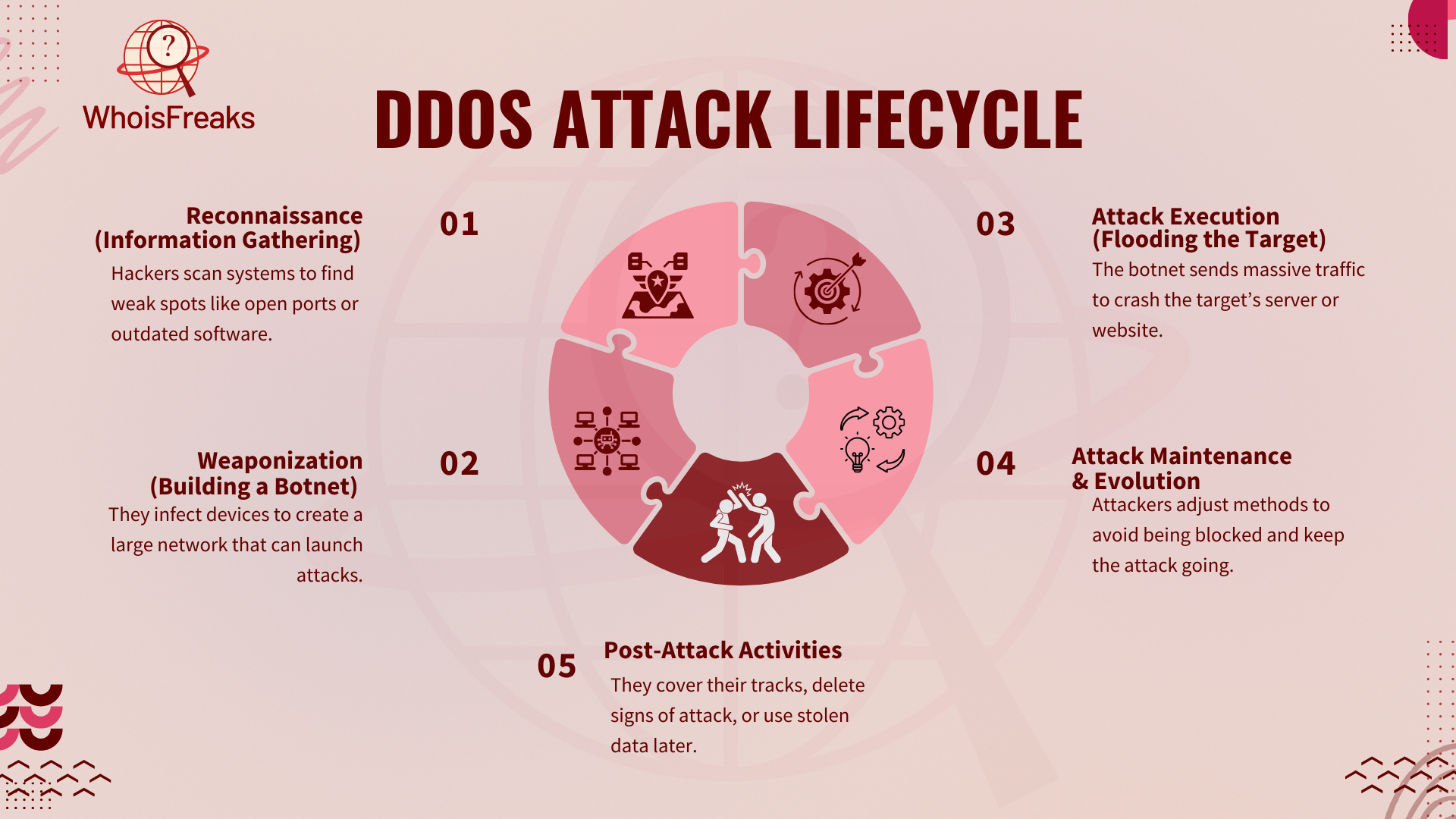
Before an attack, hackers study the target to find weak points. They check server locations, bandwidth limits, and security rules to plan their move. One key step is scanning for misconfigured devices, like open ports, outdated software, or exposed APIs.
To gather this data, they use Open-Source Intelligence (OSINT) tools like Shodan and Nmap. These tools help them map networks, find security gaps, and collect key data. The more they know about a system, the easier it is to attack.
Hackers create botnets by infecting many devices with malware. They use threats like Mirai and Mozi to target IoT gadgets, cloud systems, and weak servers. Once infected, these devices work together to launch attacks.
Botnets grow by spreading through weak passwords, outdated software, and phishing scams. Some hackers sell botnets as DDoS-for-hire services on the dark web. This makes it easy for others to cause large cyberattacks.
Once a botnet is active, hackers send huge traffic to the target. This floods servers, making it hard for real users to connect.
Attackers use different tricks to crash systems. SYN Floods fill up server requests, while UDP Reflection fakes IPs to increase traffic. Application-layer attacks hit web servers, making them slow or stop working. These attacks harm businesses and lead to big financial losses.
Hackers keep attacks going by changing their tactics. They watch security systems and adjust their moves to stay ahead.
Many use multi-vector attacks, switching between methods. For example, they may mix SYN Floods with DNS amplification to cause more harm. Some botnets update themselves, helping them avoid detection and stay active even when blocked.
Once the attack is over, hackers cover their tracks to avoid getting caught. They delete logs, wipe malware traces, and sometimes sell hacked systems on underground sites.
Stolen data can lead to ransomware, identity theft, or spying. By staying hidden, cybercriminals protect themselves while setting up future attacks.
DDoS attacks are sneaky and tricky. Many businesses don’t notice them until their website crashes or customers complain. Catching them early helps stop damage and keeps your site running.
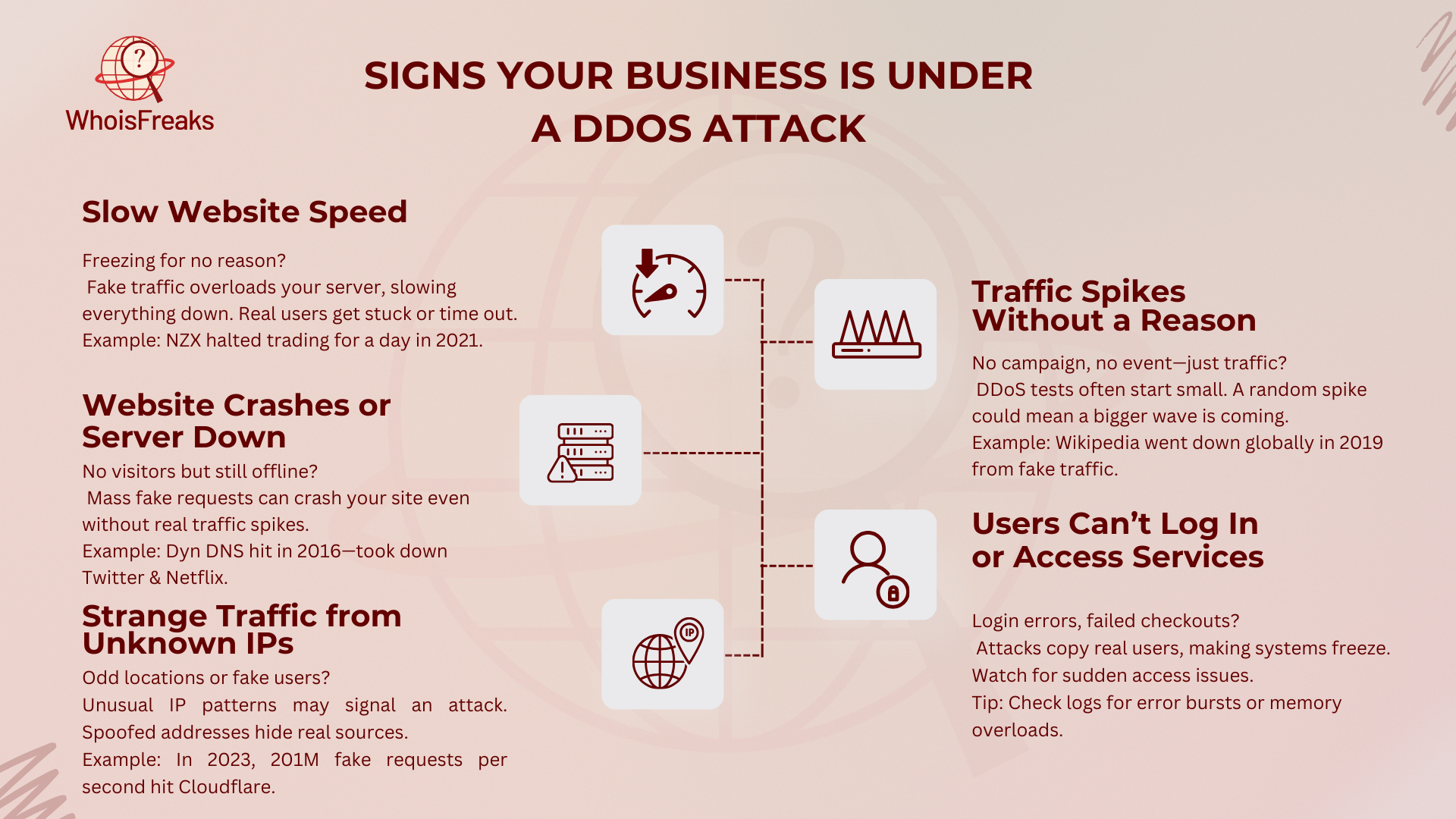
Websites slow down sometimes, but if yours freezes for no reason, it may be a DDoS attack. Attackers send fake traffic to overload your server. This blocks real users from reaching your site. In 2021, the New Zealand Stock Exchange (NZX) had to stop trading for a full day because of an attack like this.
If your site suddenly stops working, but there’s no big spike in visitors, an attack could be the cause. Attackers send fake requests to shut down servers. In 2016, the Mirai botnet attacked Dyn, a big DNS provider. This took down Twitter, Netflix, and PayPal for hours.
Your business may be under attack if you see lots of traffic from odd locations or unknown IPs. Attackers often fake IPs to hide who they are. In 2023, a Cloudflare attack sent over 201 million fake requests per second using hacked IoT devices.
A sudden jump in visitors with no ads, news, or events could mean trouble. Attackers test security with small attacks first, then hit hard later. In 2019, an attack on Wikipedia flooded the site with fake traffic, making it unreachable worldwide.
If customers can’t log in or complete purchases, but your system looks fine, an attack may be blocking them. TCP SYN Flood attacks send half-open connections to fill server memory. Layer 7 attacks copy real users, making them hard to spot. If users report errors often, check logs and traffic reports for attack signs.
Detecting DDoS attacks is important to stop them from hurting a business. Quickly finding these attacks helps companies fix the problem and keep everything running. Here are some ways to detect DDoS attacks and protect your network.
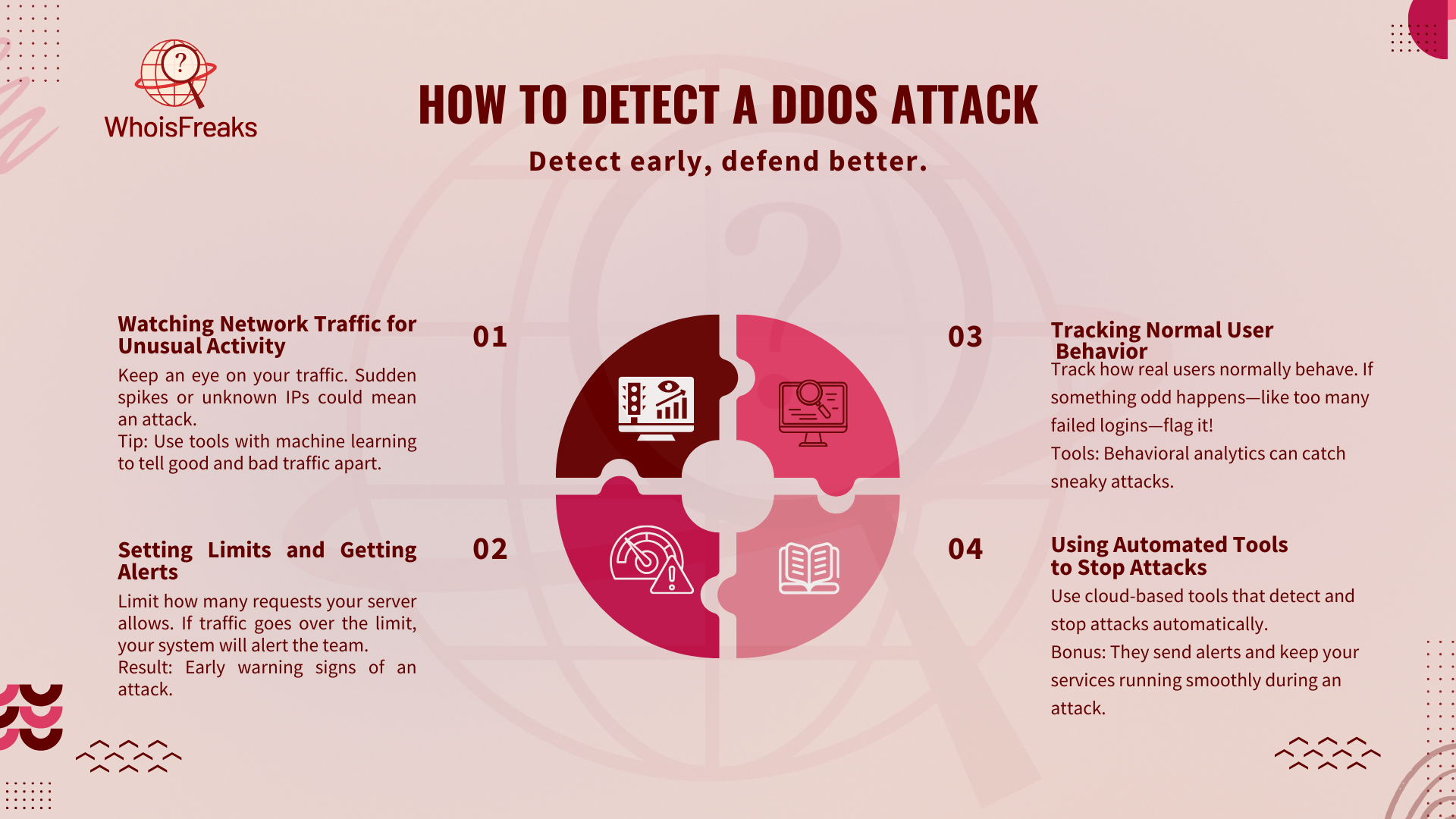
Traffic monitoring is needed to find DDoS attacks. Security teams check network traffic for sudden spikes or unknown IPs to find problems fast. Machine learning helps find the difference between normal internet traffic and bad activity.
Rate limiting controls how many requests a server can handle. This helps spot strange traffic that might be a DDoS attack. If the traffic is too high, alerts warn the security team to check what’s going on.
Behavioral analytics tools watch how users normally act. If something changes, these threat intelligence tools flag it as a possible attack. These tools are good at finding small or hidden attacks that might not be caught by regular systems.
Cloud-based systems can find and exploit vulnerabilities to stop attacks quickly. They help keep services running even when such an attack happens. These tools send alerts and help teams recover fast, reducing the damage from the attack.
Cyber laws help stop hackers and protect online systems. Different countries have strict laws to fight cybercrime and punish criminals.
The CFAA makes hacking and cyber-attacks a federal crime. Anyone who accesses a system without permission or disrupts online services can face up to 10 years in prison and fines over $250,000.
The FBI actively tracks cybercriminals, including those behind DDoS-for-hire services. These services let people pay for attacks to take down websites. Law enforcement works to shut them down and arrest operators before they cause more harm.
The CMA law makes it illegal to launch DDoS attacks, create botnets, or disrupt networks. Offenders can face up to 10 years in prison or unlimited fines.
The NIS Regulations require businesses to improve cybersecurity. Companies must follow strict rules to protect systems and prevent attacks. If they fail to do so, they risk huge penalties and legal action.
Pakistan’s PECA 2016 law fights hacking, denial-of-service attacks, and data theft. Cybercriminals caught under PECA can face up to 7 years in prison and heavy fines.
Government agencies monitor online threats and track local hackers. Authorities try to catch cybercriminals and stop illegal activities before they cause big damage.
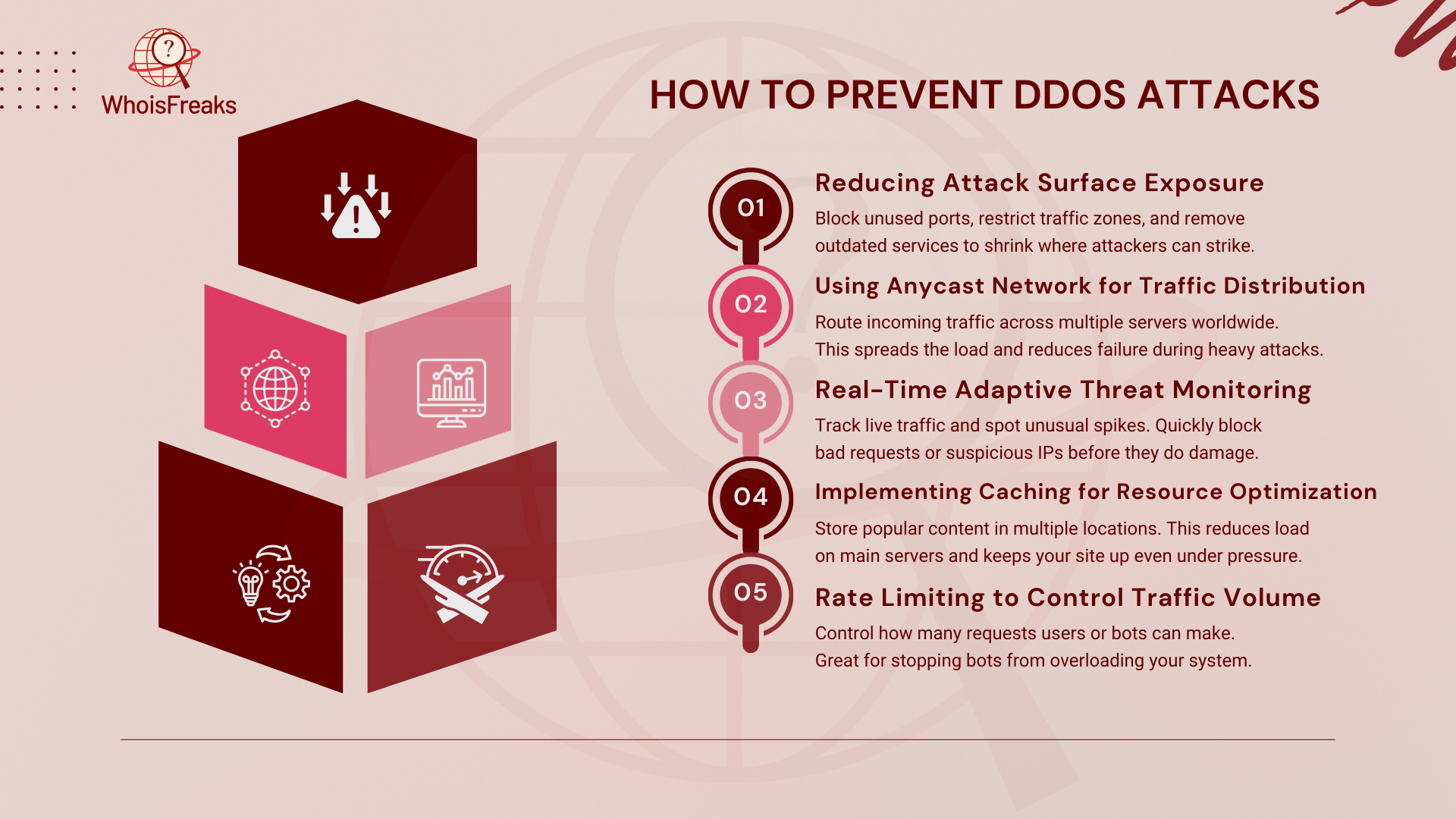
Stopping many DDoS attacks at once can be hard, especially during busy times or in large networks. A strong defense needs three key things: reducing attack risks, watching for threats, and using powerful tools to stop attacks.
DDoS attacks have hurt many industries, causing businesses, banks, and even national systems to shut down. Here are some of the most famous cases in history:
In October 2016, a massive DDoS attack hit the Dyn DNS provider. This attack made major websites like Twitter, Netflix, Reddit, GitHub, and PayPal stop working. People across North America and Europe could not access these sites for hours.
The attack was carried out using the Mirai botnet. This botnet took control of smart cameras, DVRs, and routers. These devices flooded Dyn’s servers with 1.2 terabits per second (Tbps) of traffic. The huge number of requests overwhelmed Dyn’s system and stopped websites from loading.
The impact was serious. Millions of users lost access to online services. Businesses suffered major downtime. Later, hackers leaked the Mirai botnet code. This caused a rise in IoT-based DDoS attacks worldwide. Experts warned that unsecured IoT devices were a big risk. They urged companies to use strong passwords and update device software to prevent future attacks.
On 28-February-2018, GitHub, a major code hosting platform, was hit by a huge DDoS attack. The attack peaked at 1.35 terabits per second (Tbps), making it one of the biggest cyberattacks ever. For 10 minutes, GitHub’s website was down, causing problems for developers and businesses worldwide.
Hackers used Memcached reflection, a trick that boosts attack traffic by up to 51,000 times the original request. Memcached servers, built to store common data, were not secured and left open online. Attackers faked GitHub’s IP address and sent small requests to these unprotected servers. The servers then sent huge data floods back to GitHub, overloading its systems.
GitHub reacted fast. Within 10 minutes, they switched to Akamai’s DDoS protection, which blocked the attack. This event warned the world about the risks of open Memcached servers, pushing businesses to improve security. Cybersecurity experts urged companies to secure their servers to stop future attacks.
In August 2023, Google was hit by a huge DDoS attack. It reached 398 million requests per second (rps), making it 7.5 times larger than the last record. This flood of traffic targeted Google’s servers, trying to shut down services on a scale never seen before.
Hackers used HTTP/2 Rapid Reset, a flaw that let them send and cancel requests fast. This trick overloaded Google’s systems before they could react. Unlike older attacks that used IoT botnets, this one ran on strong cloud-based servers. Since it was a Layer 7 attack, it hit web servers directly, making it harder to block.
Even with the attack’s size, Google’s Cloud Armor stopped it. This showed that AI-powered security can fight smart cyber threats. The HTTP/2 flaw was fixed, but experts say hackers will keep looking for new ways to break the internet.

The table below shows a clear difference between the DoS attack and the complex DDoS attacks' attack methods.
| DOS Attack | DDoS Attack |
|---|---|
| Stands for Denial of Service Attack. | Stands for Distributed Denial of Service Attack. |
| A single system targets the victim system. | Multiple systems attack the victim's system. |
| The victim's PC is overloaded from data sent from one location. | The victim's PC is overloaded from data sent from multiple locations. |
| DOS attack is slower compared to DDoS. | DDoS attack is faster than DOS. |
| It is easy to block as only one system is used. | It is hard to block as many systems are involved. |
| DOS attacks are easier to trace. | DDoS attacks are harder to trace. |
| The traffic volume in DOS is lower. | DDoS attacks allow sending huge amounts of traffic to the victim. |
| Types of DOS attacks: 1. Buffer overflow 2. Ping of Death 3. Teardrop Attack 4. Flooding Attack | Types of DDoS attacks: 1. Volumetric Attacks 2. Protocol Attack 3. Application Layer Attacks. |
AI is making DDoS attacks stronger and smarter. Attackers now use self-learning malware that changes tactics in real time. This makes it hard for security systems to stop attacks. AI-driven botnets can find and bypass firewalls without getting caught. They send fake traffic that looks real, making it harder to block. This can cause websites to crash for hours.
Deepfake traffic patterns add to the problem. These fake requests mix with real ones, making it tough to tell them apart. Security experts have seen AI-created traffic spikes that confuse DDoS defense tools. This shows why businesses need better protection to stop these advanced attacks.
Quantum computing could make online security weaker. These powerful computers can solve problems much faster than today's systems. Hackers may use them to launch DDoS attacks at 100 times the current speed. This could flood networks and shut down even strong security systems.
Encryption-based firewalls, which keep data safe, may not work against quantum attacks. Hackers could break encryption codes in seconds. To fight this risk, the U.S. and China are working on Post-Quantum Cryptography (PQC). This new encryption will help protect data from quantum threats. As technology grows, cybersecurity must evolve to stop these powerful new attacks.
DDoS attacks are a big problem for businesses. They can make websites stop working, cause money loss, and hurt a company’s name. As these attacks get stronger, businesses must use good security to stay safe.
To stop DDoS attacks, businesses must understand how they work. They can use tools to control website traffic, store data safely, and check for attacks in real time. Firewalls and security services can also help block attacks before they do damage.
By using these steps, businesses can stay safe from DDoS attacks. Good cybersecurity keeps data safe, makes websites work, and helps customers trust the business. In today’s online world, staying safe is very important.

Historical WHOIS data is the digital fingerprint of domain activity. WhoisFreaks tools help security teams trace attackers, rebuild attack timelines, preserve court-ready evidence, and detect threats early, strengthening incident response and proactive cybersecurity defenses.
10 min read

Explore the benefits and risks of domain fronting, its applications, and how it impacts online privacy. Read the article for a comprehensive overview.
9 min read

Learn how to prevent subdomain takeover with essential strategies and best practices. Protect your online assets—read the full guide now!
8 min read